The iPhone can actually be annoying sometimes, especially those little sounds it likes to make when you click on anything. When you're typing, it can really be just too much for your ears. So how do you stop all the noise? Best Buy has answers. The Best Buy Mobile team explains how simple it is to eliminate the typing sounds on your Apple iPhone.

Shaking your cell phone is no longer a bad thing with the iPhone. Now, shaking is an actual feature, rather than a risky move. It really comes in handy when you're typing and you misspell a word. So how does shaking your iPhone work? Best Buy has answers. The Best Buy Mobile team explains how simple it is to shake to undo typing errors on your Apple iPhone.

The iPhone is great for a lot of reasons, but one fault it may have is the keyboard and the ability to type. It's hard enough to actually type emails and notes on the small keyboard, but when auto-correction thinks it knows more about what you're writing than you do, it could become frustrating. So how do you stop Auto-Correct? Best Buy has answers. The Best Buy Mobile team explains how simple it is to turn off Auto-Correction on the Apple iPhone 3G.

If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's ExcelsFun, the 92nd installment in his "Excel Statistics" series of free video lessons, you'll learn how to use the TINV and TDIST functions to test a hypothesis.
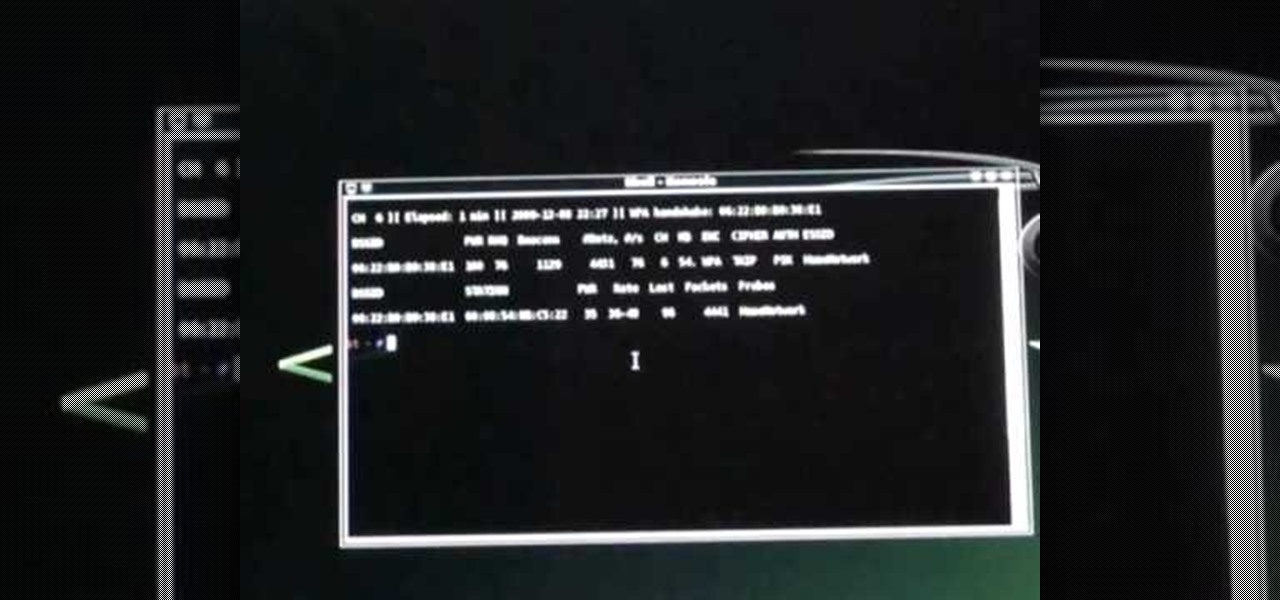
In this video we learn how to crack WPA using Back Track. The first step is the boot into Back Track using a VMware Virtual Machine Image. Next you need to open a shell console. In the console you will type "airmon-ng" and press enter. This does a check to find the wireless guard interface name. Next, type "airodump-ng wlan0" and press enter. This will tell it what wireless card to use and scan for wireless networks. You are looking for the one that comes up WPA. Copy the MAC address then typ...
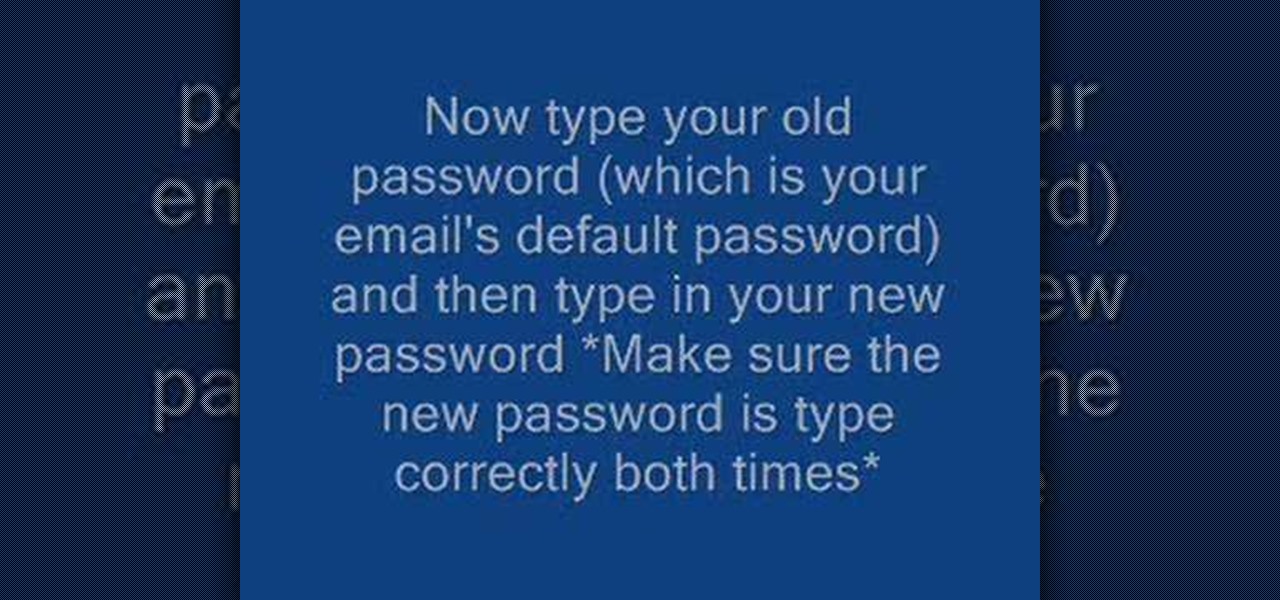
This video demonstrates how to set up a password for Microsoft Outlook. Begin by opening up Microsoft Outlook. Next, go to "GO" and scroll down the "Folder List." Click on this. Then right click on "Personal Folder" and then on "Properties." Next, you will need to click "Advanced" then "Change Password." You will then type your old password. This is your default password for your email. Next type in your new password. You will need type it in twice, so make sure you type it in correctly in bo...

In this how to video, you will learn how to create a diagonal sum in Microsoft Excel 2007. First, open the program and make a large selection. Type in =int(rand()*500) and then press control enter. This will create random numbers for the cells in the selection. From here, click conditional formatting and select new rule. From here, type in =column(A1)-row(A1)=$H$1. For the format, choose a contrasting look, such as a purple background and bold numbers. Click okay. If you type -1 or -2 in this...

To download the different types of screen saver using net, first to navigate in to "www.wallsaverapp.com". In this screen you have a "download" button that appears in the right of the screen. After download this program, run the program. Now you have to download different types of screen saver in website like "www.macupdate.com". In this site you can search different types of screen savers. Enter the website and type "matrix saver" in the search dialog box. Download the required screen saver....

In this Computers & Programming video tutorial you are going to learn how to add "Hide" & "Unhide File" to the right click menu. Go to reg.exe and type in ‘regedit’ and click ‘enter’. On the page that opens up, Navigate to ‘HKEY_CLASSES_ROOT’ > directory > shell. Right click on shell and select new > key. In the ‘key’ box type ‘Hide Folder’. Now right click on the right side box of the page and select new > string value. Type in ‘HasLUAShield’ in to the box that opens up. Now on the left side...

This video tutorial in Computers & Programming category will show you how to delete temporary files in Ubuntu, Linux Mint or Debian. For this you will need the program called bleachbit. You could get it from Bleachbit Sourceforge/ or from Synaptic package manager. For synaptic manager, click on ‘package manager’ in the ‘start’ menu and log into the program by typing your password. Then search for ‘bleachbit’, download and install it. Go to ‘terminal’, type in ‘su’ and enter, then type in your...

This video discusses how to find the right type of bike for you. There are four different types of bikes: road racing, multisport, comfort sport and flat bar road bikes. Road racing bikes typically have lighter weight frames. They have steeper angles for more aerodynamic positions and higher components. Multisports also have light weight frames and higher components. They also have more aerodynamic tubesets in the fork and airwires which allow for a more aggressive position for races. Comfort...

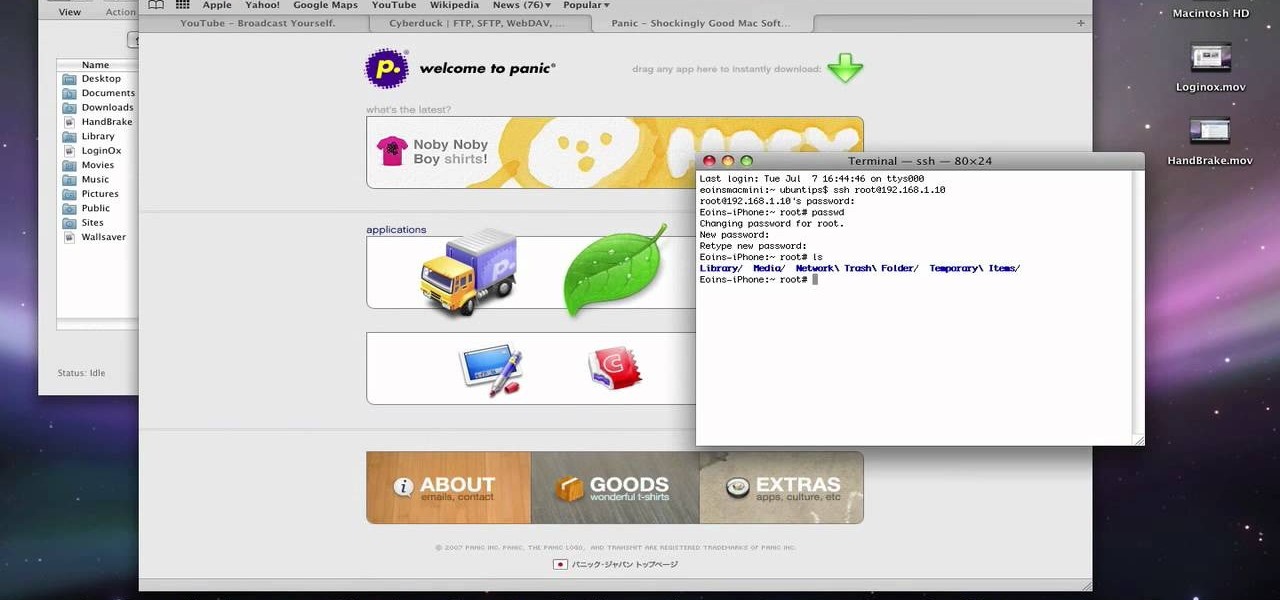
This video describes about accessing an iPhone in Ubuntu using open SSH, cyber-duck, Netatalk. For accessing using SSH, make sure your iPhone's Wi-Fi connectivity is on. Now open your terminal and type "SSH root@'address'". Here address refers to the IP address of your iPhone. You have to type a password to access the iPhone contents. Once you are authenticated type "ls" and you will be shown with the contents of the iPhone. The second method is using cyber-duck. In it, choose SFTP as the con...

This video teaches you how to change your computer's account password using the DOS command prompt. The first step is to get to the command prompt, you can do this simply by clicking run in the start menu and typing "cmd." You next type "net user" which will show you all of the user accounts on the computer. Choose the one you would like to change the password for and type "net user (account name)." It will then ask you for a new password, you may type anything you like here keeping in mind t...

The Facebook is one of many social community website with many features. To break into Facebook at school there are many ways. Some of them are listed below.

How to replace a fork seal on a motocross dirt bike. Cartridge type fork, fork seals are easy. Rocky Mountain ATV/MC] is the largest off-road retailer in the U.S. Check out their how-to videos on WonderHowTo. Search Rocky Mountain for more videos.

Check out this cool Tinkernut video on typing upside down. This will drive people nuts!

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

Some very cool features that you can do at Zamzar.com, and its all free. Check out Zamzar for some Great URL integration functions.

This AutoCAD 3D tutorial covers some fun with AutoCAD in making 3-D graphics using 3-D functions and rendering solid form.

This tutorial shows you how override functions inside UnrealScript for Unreal Tournament 3 (UT3). Specifically, create a customize trigger that plays a sound instead of triggering an event.

This video shows you how to use the basic functions of a Mini DV Camcorder and apply its various settings.

A spreadsheet software wouldn't be much good if you couldn't use formulas and functions on your data. This tutorial goes over how to use them in Numbers '08.

Phil Macdonald and Trent Munro discuss how you can identify wave types for surfing. There are two types of waves: rolling and clenching waves. Rolling waves break far from the shore while clenching waves are more dangerous.

One of my favorite iOS hacks is Type to Siri. This lets you type your queries to the iPhone digital assistant without needing to use your voice. Unfortunately, Type to Siri replaces the typical Siri voice prompt on the Home or Side button, meaning you need to choose between one or the other. That is, until iOS 13.

One core theme with each new iteration of iOS is the introduction of at least one or two features that fans have been hoping to see for years. With iOS 13, that feature is swipe typing, a first for the native iOS keyboard. While some of us have been getting our glide-typing fix with apps like Gboard for years, you might find swiping isn't quite your style. Luckily, the feature is easy to disable.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

In the previous section of this series on dynamic user interfaces for HoloLens, we learned about delegates and events. At the same time we used those delegates and events to not only attach our menu system to the users gaze, but also to enable and disable the menu based on certain conditions. Now let's take that knowledge and build on it to make our menu system a bit more comfortable.

If the all the fingerlike projections in our gut were flattened out, its surface area would be 100 times bigger than our skin's. It's so large that the actions of just a small part of it can impact our health. A new research study has found that enterochromaffin cells in the intestinal lining alert the nervous system to signs of trouble in the gut — trouble that ranges from bacterial products to inflammatory food molecules.

A young child becomes very thirsty very often and seems tired all the time. A visit to the pediatrician determines she has type 1 diabetes. The onset of type 1 diabetes may seem sudden, and it can be, but the disease may actually have been triggered by common childhood viruses years earlier.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.

In this article, we will build a parallel password cracker using the techniques explained in the previous part. As SHA-512 is the digest function that Kali (and most modern Linux distributions) use to store our passwords, we will make a SHA-512 password cracker.

Why did I write this when they're tons of scanning tools available.

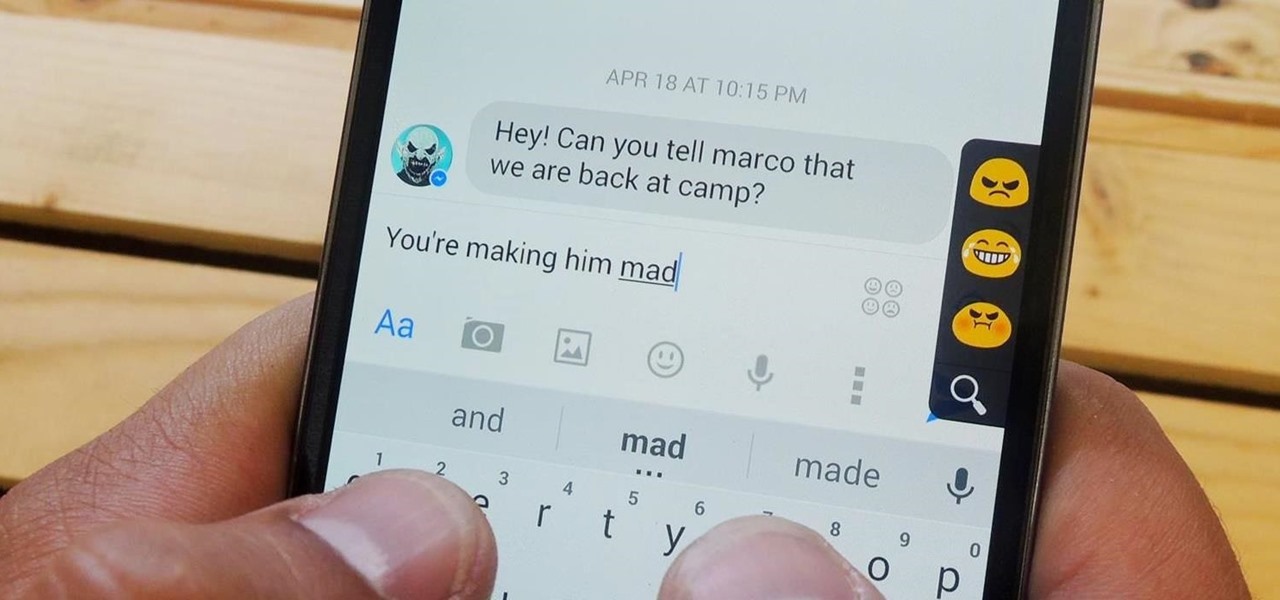
Some third-party keyboards, like SwiftKey for example, include a convenient feature that suggests emojis as your type based on the content of what you're saying. Unfortunately, many keyboards, including most stock ones, don't include this function.

Now that we have our vulnerable server, it's time to start up BeEF. Getting Started

OTW's great Tutorial Hack Like a Pro: How to Save the World from Nuclear Annihilation gives me the inspiration to try this on Win7 sp1.