A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

In this überbrief video tutorial, you'll find instructions for adding a CNAME record to tinydns. The steps, demonstrated in the video, are as follows: Open up the data file, type a capital C, the domain you'd like to use, or subdomain, the IP address of the machine or destination you'd like that hostname to route to and the TTL or time to live. Save the changes, type make, and test it out!
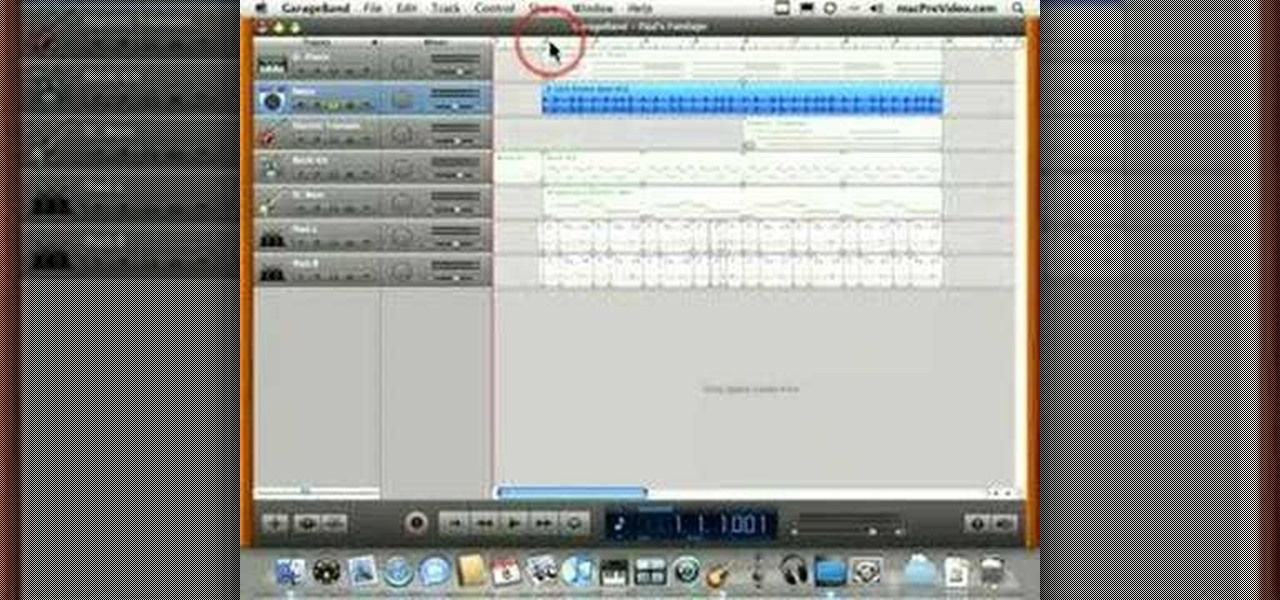
This GarageBand tutorial teaches you about track types. Learn the difference between audio tracks, instrument tracks, and Apple Loop tracks in GarageBand.
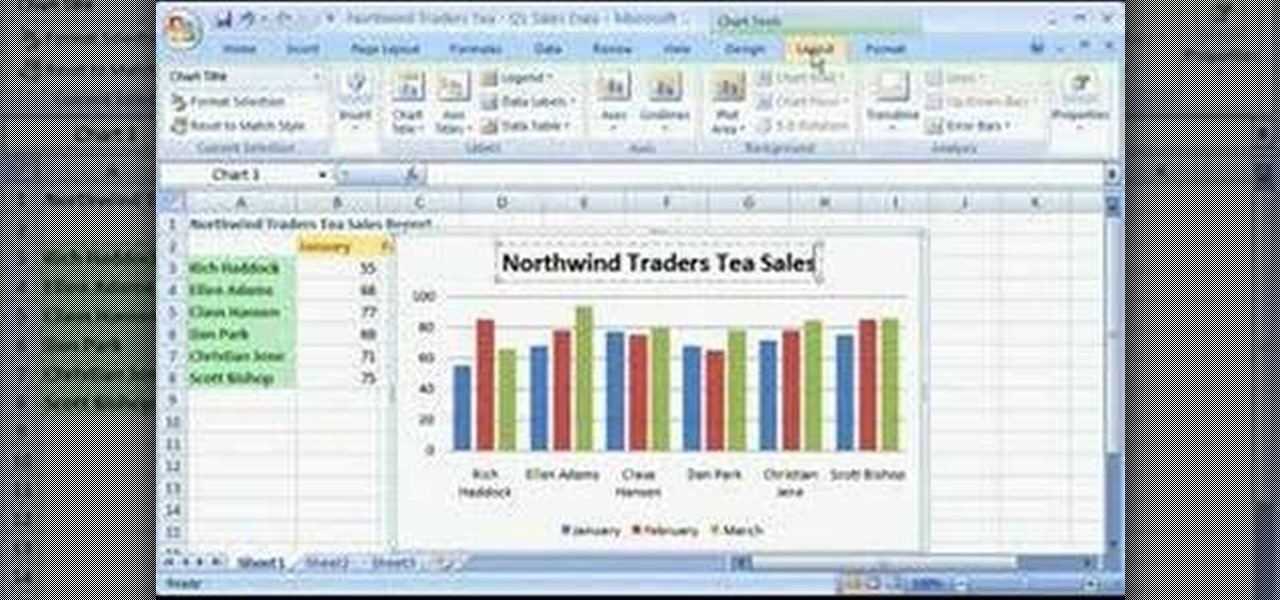
Check out this tutorial and learn how to create chars in Excel 2007. In Office Excel 2007, you just select data in your worksheet, choose a chart type that best suits your purpose, and click. Want to try a different chart type? Just click again and select a new chart type from a huge range of possibilities. Then work with the new Chart Tools to customize the design, layout, and formatting of your chart. You can see how various options would look just by pointing at them.

Wedging two types of clay can give you a new color, which you can then use to further decorate your pieces. Make sure that the two kind of clay require the same firing temperature. You can mix your own personal clay to work with simply by selecting qualities in standard clays and kneading them together.
In this video tutorial, Chris Pels will show how to persist and restore information in the ViewState of a custom user control. First, learn how to persist simple values containing .NET primitive types such as String, Int32, Boolean, etc. Then see how to persist complex types such as Class which contain properties storing information. The sequence of processing View State information during the lifecycle of an ASP.NET page is also discussed.

Long and lean, or full and curvy, there's a party dress out there for you. Follow these fashion tips to find the right dress for your body type.

This video shows you how to make 2 types of tension wrenches 2 types of picks and a demonstration on how to pick a lock. All materials used, are materials one can found around his/her house.

A short tutorial on how to setup mime types using cPanel. This video is provided to you by Scandicsoft.

Kitchen lighting is vital to having a beautiful and functional kitchen, but even knowing where to start when choosing the type of lights for your kitchen can be confusing. To find kitchen lighting ideas, Meghan Carter visited Kichler Lighting where she discovered the three different types of kitchen lighting you need to make the most of your kitchen.

From the depths of the gaming abyss, a classic returns to melt the heart of shoot 'em up gamers. Here's some tips from G4TV on beating the first two bosses in R-Type for the Wii Virtual Console.

Surfline TV presents Mick Fanning on how to go fast in all types of surf.

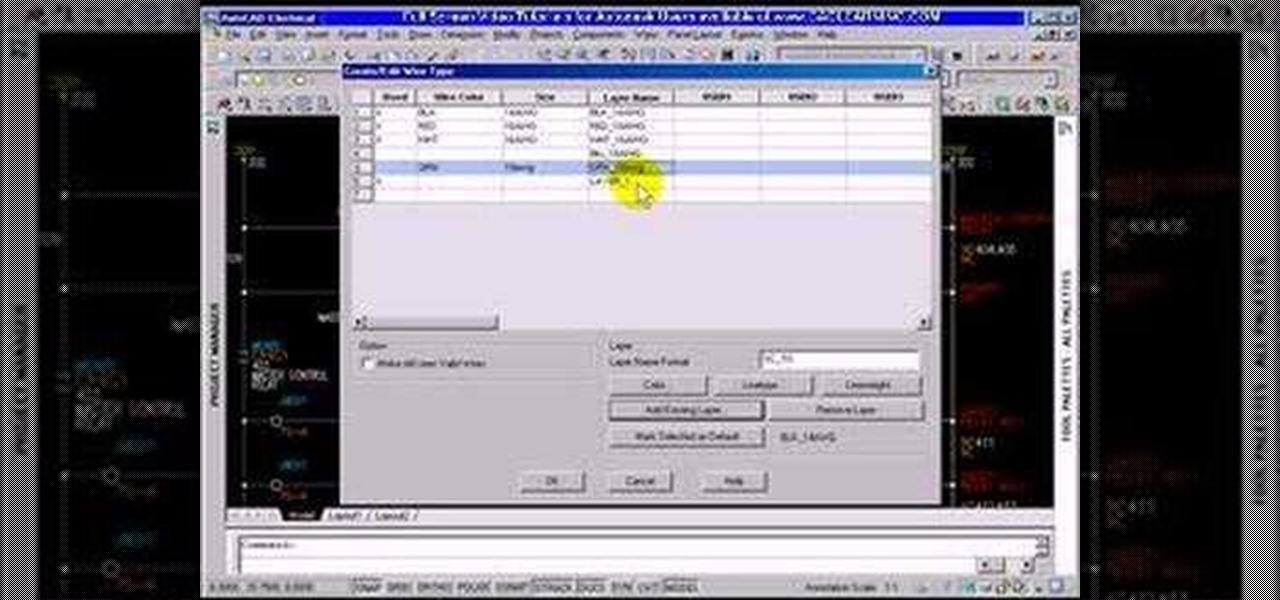
This tutorial shows you how to create wire types in AutoCAD Electrical 2008.

Issac explains what different shot types are: from the establishing shot to the extreme close up, and how they can be used to enhance your videos.

Watch as a jewelry designer demonstrates the basics of earring construction. She will show you the main types of earrings and how to create them.

This video explains the "player" type at the office and gives tips on how you can handle this type of boss.

Do your videos lack emotional impact? Do you wonder about the framing options that could be use to produce a better video image? This episode of Izzy Video covers the Framing Terms for different types of shots and how to use them.

Have your ever wanted to build a bird feeder? Do you want to know what types of birds live in your neighborhood? If the answer to one of these questions is yes, then this video is for you. Bre Pettis will teach you how to make two different types of bird feeders and then how to attach a webcam to the feeders so you can watch the birds.

Making text look old and weathered, or rusty and corroded is a long standing effect but it's a good one to know. In this episode, Bert will show you how to do a nice, detailed weathered type from scratch. You may want to download his example files or full rez version to see a detailed view.

In this tutorial you'll learn how to use Illustrator to make cool and dramatic headlines. The main step, is changing the type into an outline, which is just a vector based image of the type. This allows you to easily manipulate the text as an object and do some cool things to your headline.

Does your dog like to jump in mud puddles and play in dirt? Learn how to give your dog a bath at home so you can save the cost of frequent trips to the dog groomer. In this case we are going to use a bath tub, but you can also bathe your dog in outdoor showers, indoor showers, or just use a hose. Now that we have the place to bathe the dog, we have to decide what type of shampoo to use. Remember, dogs have different types of fur, so you will want to select the appropriate shampoo for the type...

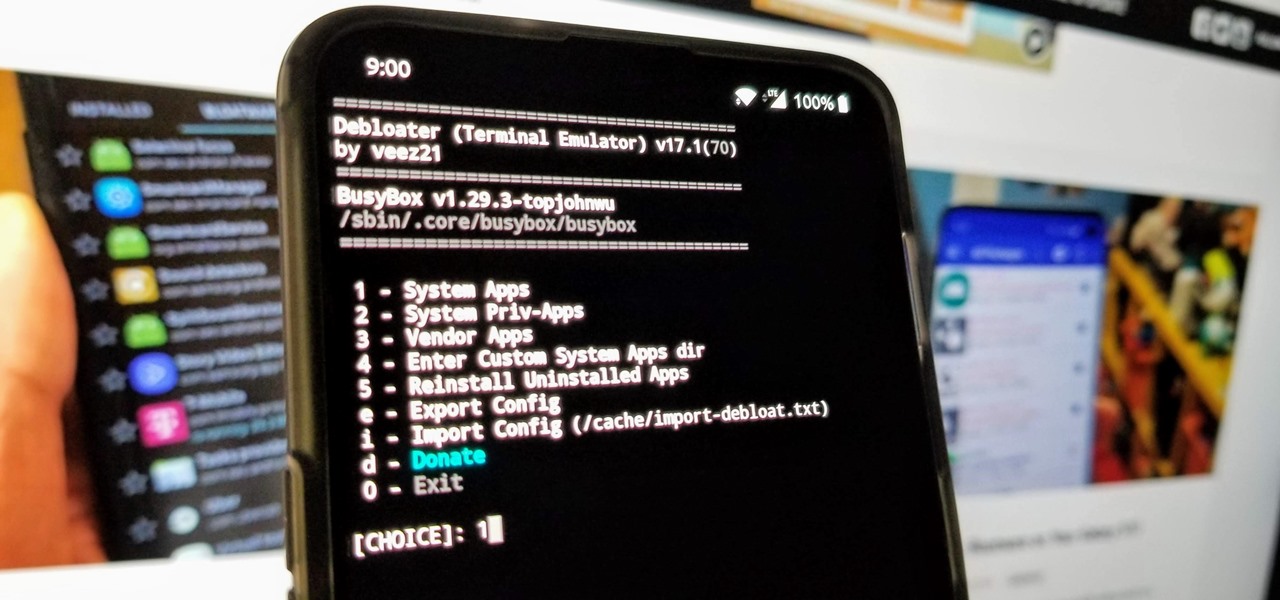
When you get a new phone, the last thing you want to deal with is a ton of preinstalled programs staring back at you. They not only clutter your home screen with apps you'll probably never use, but they're also wasting space on your internal storage and potentially draining battery. To truly uninstall them, you'll need root — but even then, it can be hard to pin down all the apps that should be removed.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

The number of households in the US that go hungry because they lack money for food hit a high of almost 15% in 2011. While that number continues to decline, nearly 13% of American households still go hungry.

Brace yourselves, because Siri has a trick up its sleeve that iPhone users have wanted for some time. Yep, that's right, I'm talking about the ability to use Siri without having to talk out loud for the whole world to hear. It's great for privacy, Siri-ing on the down-low when you're not supposed to, or ... you know ... if you have a speech disorder.

Google Now, Siri, and Cortana aside, the main way you interact with your smartphone is through the keyboard. Every app you use, every search you perform, every message you send—the most fundamental interface between you and your device is that handful of characters and those 26 letters on the bottom half of your screen.

Hello Friends … My name is Suresh Senarathna and this is my first “How-To” post,

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the victim portion of the shell. Today, we'll be building the attacker portion. This script will initialize interaction with the victim portion of the shell, send commands, and receive the output.

So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - bypassing antivirus.

OK, In my last Tutorial we made a Server for sending Instructions to a Client. This time we will build the Client. Fire up your favourite Python environment and get the Code here.

Ready or not, the USB-C cable is about to take over your electronics. The new industry standard is fully reversible and packed with enough power to serve as a laptop charger or an HDMI cable, so it actually has the potential to replace every cord, wire, and connector in your house. In fact, the conversion has already started: The latest MacBook, Chromebook Pixel, and Nexus phones are sporting USB-C connectors out of the box.

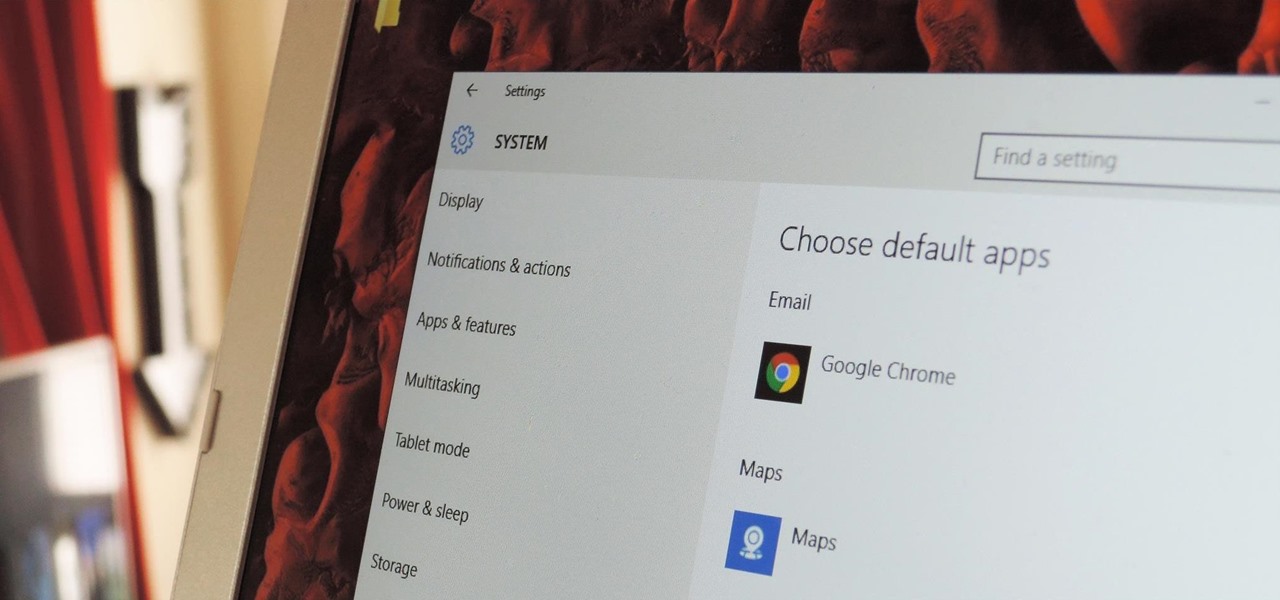
The first time you launch any type of file, Windows 10 will usually prompt you to select an app to open it with. Occasionally, though, this "Open with..." screen doesn't show up, and instead Windows will use a pre-installed system app to launch the file without ever giving you a choice in the matter.

What's up guys! It's time to discuss strings in more detail. Review

Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post.

In this article, we will explore the basics of radare2, a powerful package that comes with Kali. We are going to write a simple program, and then disassemble it, to see what is really doing in the processor.

Welcome, in this tutorial we shall we looking at creating a safe(r) way to back up your important files. The contents we will be covering are as follows;

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

Hello you sexy, savage, surreptitiously tech-savvy penetrators (Pun intended)!