By connecting the dots between theory and real-life effect, two new studies offer more proof that neonicotinoid insecticides are causing extensive damage to honeybee colonies.

There is a reason the Amanita phalloides mushroom is called the "Death Cap." It can kill you. Mushrooms are a type of fungi, an organism that produces thread-like mycelia that often produce spores. Spores allow the fungi to reproduce. Molds, lichens, and yeast are all fungi, but the most visible fungi are mushrooms. Some fungi are delicious, but others can cause disease or, and still others, like Penicillium, can cure it.

We can add one more health effect of our gut bacteria to the growing list. Researchers from the UK have just reported that the gut microbiota plays a role, both directly and indirectly, on the toxicity and efficacy of chemotherapy. Their findings are published online in the journal Nature Reviews Gastroenterology & Hepatology.

With new diet and health claims coming at you everyday, it's sometimes hard to know what to believe. Well, here's a bright spot: A pair of studies confirm that whole grains are healthy for you, and for the diversity of microbes living in your gut.

If the rumors are right, Microsoft has decided to cancel the second version of the HoloLens, and they will instead move onto version three of their mixed reality headset. In the latest report, Thurrott's Brad Sams states that the expected release date of this new Windows Holographic device wouldn't be until 2019, a long two years away for those of us putting full effort into HoloLens app development.

As a former repair tech, I've heard the same reasons over and over as to why people opt not to purchase phone insurance. Some cite the cost—why pay extra every month for insurance when you're careful with your phone? Deductibles are expensive, so why not just spend that money on a repair instead of getting a refurbished phone as a replacement?

Whenever I went to the grocery store on a mission for blueberries, I'd inevitably find myself staring at these weird little tomato-looking berries... and wondering what the hell they really were. Tomatoes? Berries? A weird science experiment? Then, I'd set a pint of blueberries in my cart and carry on, forgetting about them for the time being.

Fresh, homemade pasta definitely beats the dried stuff from the store. However, most of us aren't usually in the mood to knead dough for 10 minutes... or to clean up a sticky, doughy, floury mess afterward.

Welcome aboard my inquisitive comrades. I am starting a new series that nobody expected coming. It may not seem very exciting at first, but await the last few parts as many startling discoveries will be made. This is a series which I plan to continue after the completion of Nmap, unless you have major objections.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

Nothing gets me functioning in the morning better than strong coffee. And if I'm going to start my day with a dreaded workout, that steaming cup of caffeine is the exact motivation I need to get going. Although coffee might not seem like the best beverage to drink before hitting the gym, it actually has a few hidden benefits over water that may surprise you.

It seems like whenever someone sees my phone, they ask me two questions right off the bat; "What phone is that?" and "How did you get your Android to look like that?"

Are you someone who always struggles to wake up in the morning, no matter how much you've slept? For most, the thought of getting out of bed any earlier sounds horrific. Yet dragging yourself out of bed and towards the coffee maker a few hours earlier each day can have benefits you've never realized. Here are six reasons that make a compelling case for ending our bad habit of sleeping a little too long.

If you've ever searched for a new job online, chances are you've been completely overwhelmed by the process. Clicking through pages and pages of semi-relevant job postings, sending out hundreds of emailed résumés, and filling out applications is tiresome and dull.

Apple is widely known for keeping a tight grip on iOS, disallowing open-source and third-party downloads. While there are many reasons for this, the three most frequently referenced are quality control, malware prevention, and of course—money.

What I'm going to do in this tutorial is, as the title implies, teach you how to make nearly anything look like metal. This can especially come in handy in Steampunk, as most of us don't have the ability to machine brass. We do, however, have access to wood, PVC, and spray paint. Not to mention that, as a costumer, I can speak from personal experience when I say that things made of brass are really, really, really heavy!

In response to Apple's implementation of LiDAR sensors in iPad Pro and iPhone 12 Pro models, Google is looking to leverage the dual-camera setups in recent flagship devices as depth-sensing components.

When Treasury Wine Estates released 19 Crimes Snoop Cali Red this summer, named for its new partner in wine, rapper Snoop Dogg, it already came with the brand's signature AR-enhanced label.

Whenever you're browsing a grid of photos and videos in the Photos app, whether you're in the Photos, Albums, or Search tab, all media is cropped within the confines of tiny square thumbnails. But it doesn't have to be that way.

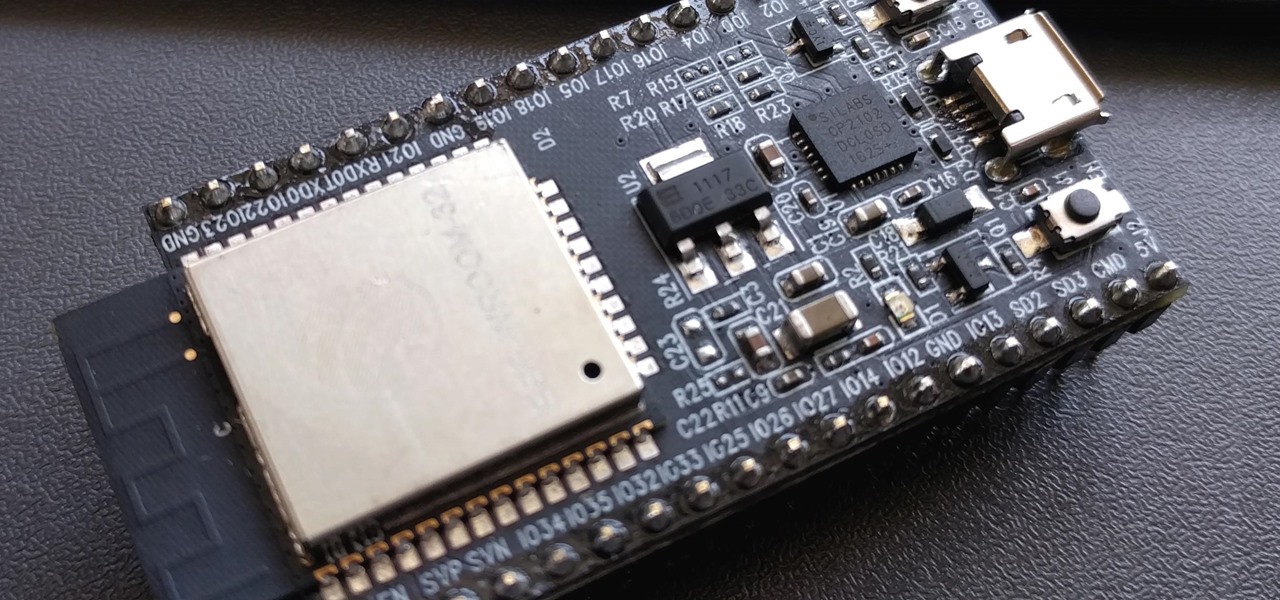
PirateBox is a great way to communicate with others nearby when cellular and Wi-Fi networks aren't available. With it, you can anonymously share any kind of media or document and even talk to one another by voice — without being online. However, it needs a Raspberry Pi, which is more expensive than ESP32 boards, and if you only need a text-based chat, there's a much simpler option.

We are now in the age of 5G. Carriers worldwide are upgrading their networks to the newest standard for mobile, which will dramatically improve your phone experience. How? By giving it download speeds and latency that surpass Wi-Fi. But before you upgrade, there are few things you should know first.

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

There's something extremely satisfying about hunting down your online adversaries and knocking them out with a well-placed shot, which probably explains why shooting games are still one some of the most popular time killers for iOS and Android.

Here at Next Reality, our typical approach to all things augmented reality involves vision combined with remote control, either via a handheld device, gaze control, or hand/finger tracking.

One of the more competitive aspects to chat apps these days is customizability. It seems every messenger wants to offer the largest number of options for users to make the app feel like a truly personal experience. Telegram is no stranger to this customizability, offering tools where you can select backgrounds and chat bubble colors.

During the Google I/O 2019 keynote, the latest Android Q Beta was released to the public for Pixel smartphones along with 15 other non-Pixel devices. It's the third Developer Preview for Android 10, but it's the first official public beta outside of Google's Pixel smartphones. A new public beta means good things are on the way as the future of Android continues to evolve.

In just a few weeks, on May 29, the annual AWE (Augmented World Expo) conference will take place once again in Silicon Valley (Santa Clara, California, to be exact).

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

Streaming movies and TV shows on phones is more popular today than ever, but what about when you're on a plane, have a limited data plan, or will be in a no-service area? You'll want to download your movies and TV shows instead. While Netflix is excellent, you can't rent or download most of the latest movies and TV series. What you need is an app that lets you do just that.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

When you want to post a breathtaking landscape or picture-perfect portrait that you just took with your DSLR camera to Instagram, Facebook, or some other social platform, there's an easy way to do so — even if you don't have a computer handy, which is typical when you're out and about.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

An incorrectly scaled object in your HoloLens app can make or break your project, so it's important to get scaling in Unity down, such as working with uniform and non-uniform factors, before moving onto to other aspects of your app.

With Virtual Network Computing, you don't need to carry a spare keyboard, mouse, or monitor to use your headless computer's full graphical user interface (GUI). Instead, you can connect remotely to it through any available computer or smartphone.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

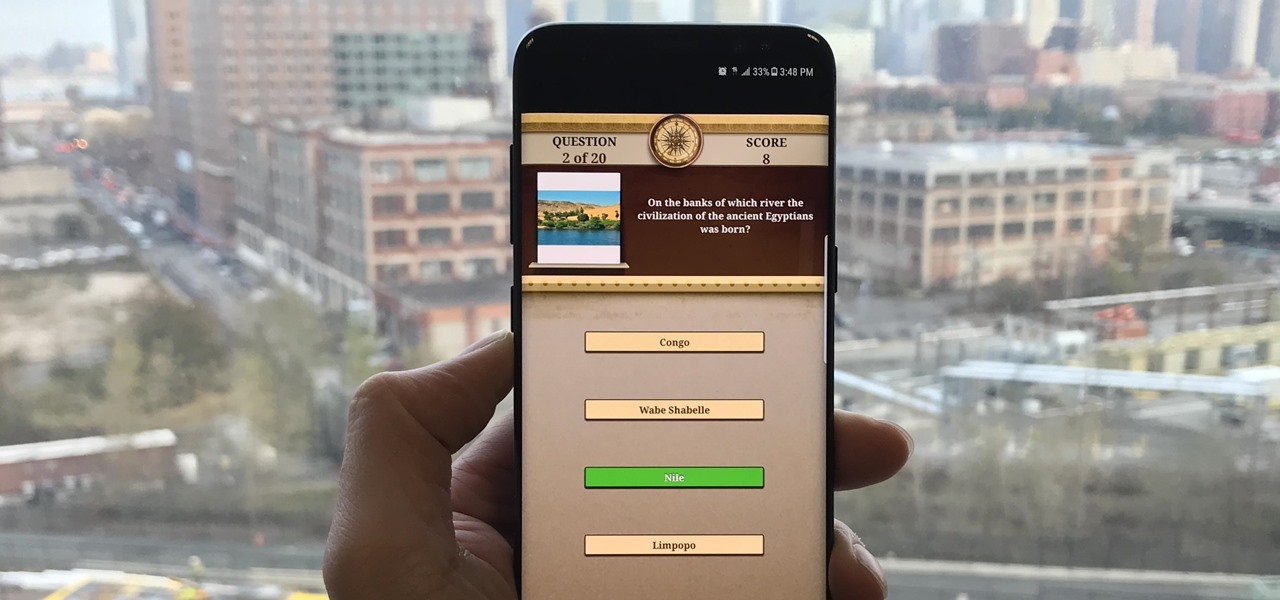
Trivia games are among the most entertaining ways to learn factoids and interesting info you may have never known about before. They're also the perfect genre to enjoy with friends and family, as they're particularly great at breaking the ice to make for a more memorable time together.

Aircraft equipped with ADS-B are constantly shouting their location into the radio void, along with other useful unauthenticated and unencrypted data. In this guide, we will make an ADS-B receiver using a Raspberry Pi with a software-defined radio (SDR) dongle, which we can use to track aircraft anywhere in real time.

Quanergy CEO and founder Louay Eldada is, by any standard of measure, a pioneer in the development of LiDARs for driverless vehicles.

Architects are natural candidates to be early adopters of mixed reality. Their trade consists of not only designing buildings and spaces, but also presenting those designs to clients, who then decide that their vision is worth spending thousands (if not millions or billions) of dollars to build in reality.

Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.