We are most certainly not machines. We all need some downtime every once in a while to set our sanity scales back in balance, which in turn, makes us more productive workers. This is a premise that several forward-thinking employers fully understand, but these types of companies are few and far between in corporate America.

In case you didn't know, Android has an awesome hidden settings menu called "Developer options" that contains a lot of advanced and unique features. If you've ever come across this menu before, chances are you just dipped in for a minute so that you could enable USB debugging and use ADB features.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

Ironing is a serious chore: hot, unpleasant, and frustrating all in one, but necessary if you don't want to look like you crawled out of bed just before work. While you might only turn to your flatiron when faced with wrinkled clothing, this little appliance packs the power to tackle even greater challenges—and here are our 10 favorites.

Climbing into bed and shutting your eyes each night is heavenly—but waking up the next morning isn't. We all hate dragging ourselves out of the comfort of sleep and into the groggy, exhausting work day. Yet starting your day doesn't have to be awful if you know how to hack your sleep cycles and get the most out of your shut-eye.
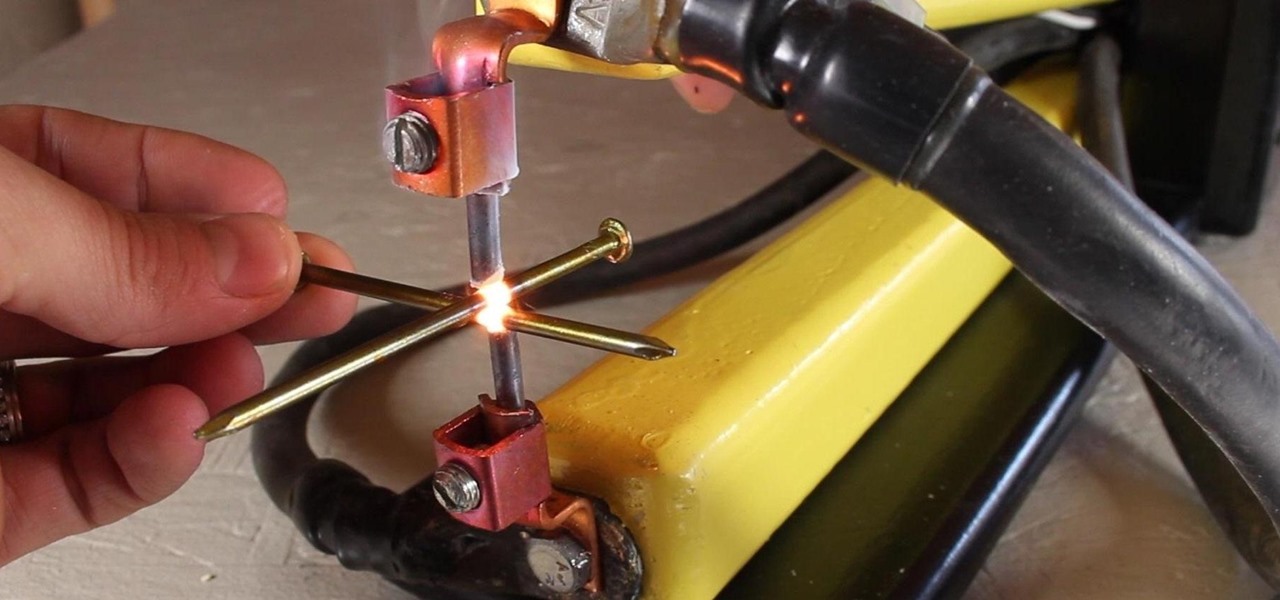
A typical resistance spot welder can range in price from about $200-$800, but with a little resourcefulness and a bit of free time, you can make one like this for about $10 or less.

If you upgrade to an iPhone 12, 12 mini, 12 Pro, or 12 Pro Max, you can take advantage of super-fast 5G speeds, but which 5G network are you actually getting and is it better than the others? Depending on your carrier, you may see 5G, 5G+, 5G UW, or 5G E in the status bar next to the signal strength, and there's a pretty big difference between them.

With the new Samsung Galaxy S22 Ultra release, the first thing you may be wondering is how its battery life compares to the iPhone 13 Pro Max, Apple's biggest model from 2021. We've rounded up some of the most popular Galaxy S22 Ultra and iPhone 13 Pro Max battery tests from across the internet to bring you answers.

If you're living or staying out in the middle of nowhere or a rural area outside of a big city or town — where there are no reliable cable, fiber, or wireless networks available — how can you get an internet connection? There are several possibilities, but they all come with tradeoffs, which we'll go over in detail.

Excited about experiencing blazing-fast 5G speeds on your iPhone 12, 12 mini, 12 Pro, or 12 Pro Max? Well, that brand new iPhone you just bought might not actually be using 5G, even when you see that 5G symbol in the top right. Unless you follow these instructions, your iPhone will use regular old 4G LTE more often.

Apple just pushed out iOS 14 to everyone on Sept. 16, but you may not want to jump right into updating your iPhone. If you have Automatic Updates turned on, you may want to turn it off real quick before it tries to download and install iOS 14 before you're ready.

Late last year, Snapchat introduced Cameos, deep fake-ish stickers animated from your own selfies. Now, Cameos have evolved as a sticker option to use in photos and videos captured with the app's camera.

Apple's iOS 13 for iPhone includes new features in Safari that make browsing the web a little bit better when compared to iOS 12. Some changes are small while others add functionality that just wasn't there before. Plus, there are more security enhancements.

Smartphone videos get better and better each year. Seven or eight years ago, who would have thought iPhone and Android phones could support 4K video recording. Some phones can even shoot slow-motion at 960 fps. But no matter the resolution or frame rate, a phone's rolling shutter can make quick movements in front of the camera appear wobbly, distorted, or with artifacts.

I noticed the neon yellow sign at the new location of Pho Bar in Chinatown right away. The sweeping cursive yellow letters spell out "Crazy Rich Broth"; the same phrase printed on the back of servers' shirts. It's the kind of minimalist but colorful design feature that is especially popular on Instagram at the moment — shots of patrons in front of a glowing sign.

After years of rumors and waiting, Samsung's first foldable smartphone is finally a reality. The phone itself is a bit wild, but with Samsung going so far out of their comfort zone with this one, there were some bumps in the road that caused a delayed release. The launch has been pushed back yet again, but when it does hit stores, it could end up being one of the most influential devices in years.

OnePlus will be releasing a new phone in the second half of 2018, specifically, an upgrade to their T-series. Over the past two years, #T versions have come out about five months after their predecessors and have included small updates that fix any problems from the previous OnePlus device. While we do know a bit about OnePlus 6T, what it could be is much more exciting.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

While you may not have loads of secret files hiding on your computer, there might be one or two items that need a little extra security, like a file of website logins or a folder of risqué photos.

The camera situation on the all new HTC One is a little daunting. The M8 has not one, not two, but three camera lenses built in. First, there's the 5 megapixel selfie machine up front, then around back, there's the new Duo Camera with a refined UltraPixel sensor. HTC has done things differently here, and the UltraPixels and dual lenses means that the M8 doesn't necessarily take pictures like you'd expect—and that's not a bad thing. With a little guidance and some easy tricks, you can use all ...

Hello again, faithful readers. For today's lesson, we will be learning the correct way to restring and tune an electric guitar. I almost wasn't going to post this because it is so basic. But, as with many basic tasks, there are a lot of people who know how to do it, but can't really do it right. If you are a new guitarist, this is an essential piece of maintenance work, because guitar shops usually charge way too much for this task. Of course, I'm kinda cheap, so even 5 bucks is too much for ...

If you use Goals in Google Calendar, you've probably already received the notification that Google, in typical executioner fashion, has marked the feature for death. As of November 2022, you can't create new goals, and your current goals won't repeat anymore. Google suggests switching to repeating events or tasks, but there's a better option to use on your Android and iOS device.

Microsoft believes its Mesh platform can help developers build immersive AR apps more easily. We spoke with a member of the Microsoft team to learn more about the platform.

Compared to Apple's products like the iPhone and iPad, Android phones and tablets are very flexible devices. For instance, you can set a new home screen, replace the lock screen, or even beam files using NFC — but that's just the software side of things, and the flexibility goes well beyond that.

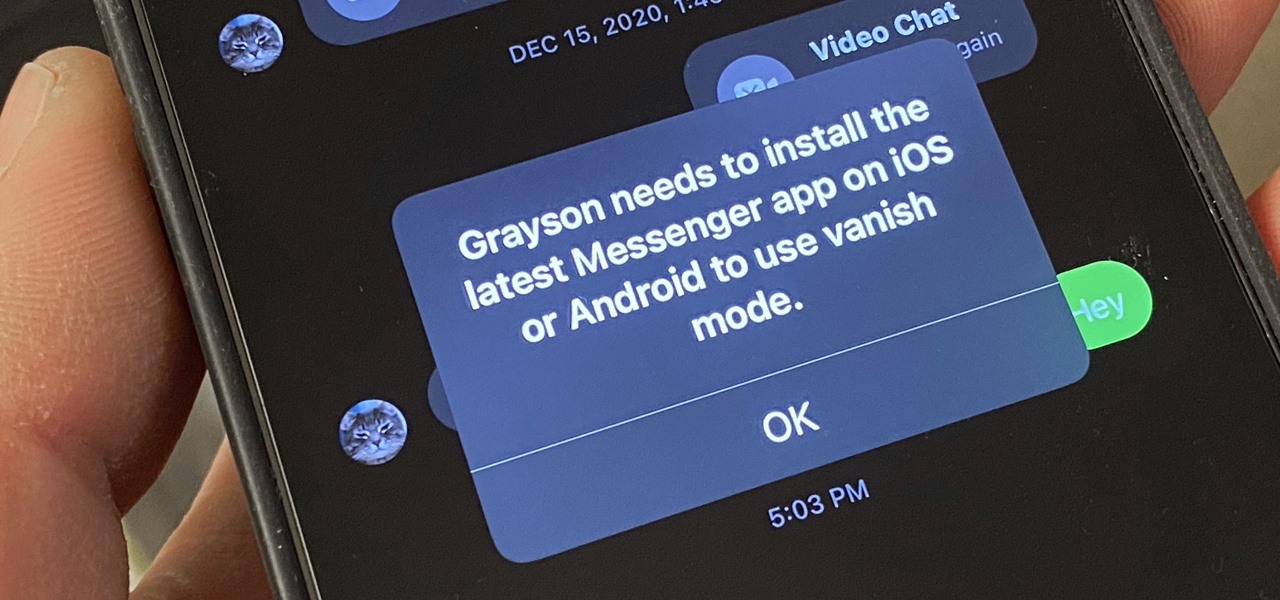
Facebook recently implemented "Vanish Mode" into Messenger and Instagram, which lets you have an end-to-end encrypted conversation in a chat that will disappear as soon as you leave the thread. As cool as it sounds, it's easy to enable accidentally, and a friend could force you into using it. In some cases, that may not be ideal since everything you or the recipient said will disappear.

In a similar vein to Facebook's colorful backgrounds for text posts, Instagram has a way to add vivid text-only status updates for your stories. That way, you can conjure up colorful stories that make a statement without even needing to take a photo or video in the first place. And now there are even more fonts to choose from.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

The Home button on an iPhone does a lot. That's not necessarily news for anyone who's ever owned an iPhone with a Home button, but what you might not know is that it's capable of so much beyond the standard everyday functions. So if you have an iPhone 7, 8, or the new SE model running iOS 13 or later, keep reading to learn about 17 secret Home button tricks you're missing out on.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

The $35 Raspberry Pi is an amazingly useful single-board computer (SBC) with a good balance of price, performance, and connectivity options. But for some projects, it just isn't enough. Whether you need more computing power, a smaller size, or better machine-learning capabilities, there are other options available.

There have been concerns with how much personal information Google tracks and all the things they know about us. Of course, that's what makes Google services so useful, they can use that information to cater to each of us individually. So yes, it serves a purpose, but it's not great for personal data security.

You might think you need to buy a thousand dollar phone to get a great experience while streaming movies and TV shows from services like Netflix, Hulu, and YouTube, but that's just not true anymore. While phone prices keep rising and the midrange segment now ranges from $300–$500, there are still cost-effective options that come with top-notch displays and media features.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

In this jam-packed October, the Huawei Mate 20 Pro has flown under the radar in the US. Due to Huawei's lack of presence in the States, many are unfamiliar with the second largest OEM in the world. Huawei has continuously put out amazing mobile devices, and this year they released a phone that's nearly perfect on paper.

The calendar app is one of the unsung heroes found within your iPhone. It's the ultimate personal assistant that you've come to rely on to keep track of your schedule and ensure you never miss a class or meeting, all while reminding you of upcoming birthdays and deadlines to help maintain good relationships with loved ones and colleagues.

One of the most popular usages of modern-day smartphones is listening to music. It doesn't matter if you download or stream your tunes, you are part of a massive group of users who do exactly the same. While statistics are a bit foggy on how many smartphones users download music, we do know that over 68% of American smartphone owners stream music on a daily basis.