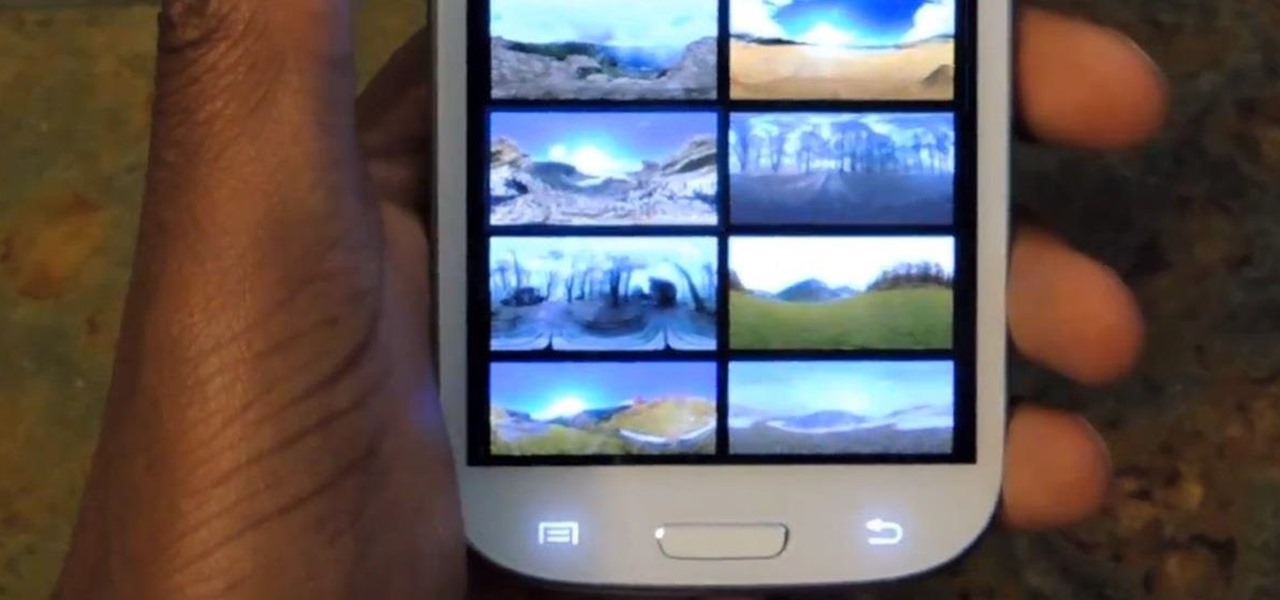
How To: Get Photo Sphere Live Wallpapers on Your Samsung Galaxy S3 (Without Rooting)
For the first time ever, iPhones will be getting live panoramic wallpapers in iOS 7, but it's something Android devices have always embraced.


For the first time ever, iPhones will be getting live panoramic wallpapers in iOS 7, but it's something Android devices have always embraced.

You can find a ton of live wallpapers for your Android device on Google Play, but the more alluring interactive ones are a harder to come by, which can bring your home screen to life using a few finger swipes and taps.
A wave of shock and anger swept across the country after Edward Snowden released private documents recounting the U.S. government's secretive mass surveillance programs. Although some of the fear was unwarranted (they don't read your emails or listen to your calls), many scrambled to find privacy of new heights for protection from the all-watchful eye. While the government may not be tracking you down, there are a myriad of other candidates that fill that Big Brother role—and I'm not talking ...

Food can smell great before, during, and after cooking. A pot of stew simmering away on the stove will tantalize you all afternoon, and there's nothing better than the smell of fresh-baked cookies lingering in the house for hours.

The art of persuasion is a very crucial characteristic that anyone can learn, and it has countless benefits. Whether it's at work, home, or in social situations, the ability to be veritably persuasive can have an unheralded impact on your daily life.
We don't spend much time thinking about bicycles today, do we? Sure, they're a "green" alternative to driving everywhere in cars, but the vast majority of America has dismissed them as simply being too much work, or more importantly—too slow. That wasn't always the case, though, I assure you!

Let me start out by saying that Steampunk isn't about being historically accurate, and that everything I'm about to tell you is entirely optional. That said, let's take a look at the history of screws! What many people don't realize is that before we had metal screws, wooden screws were in wide use for things like wine and oil presses. Generally, the invention of the screw is attributed to Archimedes in the 3rd century BC. That was a long, long time ago. Metal screws and even screwdrivers hav...

Cross-dressing and gender-bending are nothing new, but the realm of Steampunk seems to be especially accepting of role-reversal in dress.

As a kid, I was always interested in what was beyond our world. I remember lying down on the top of my dad's car and watching the stars for hour, gleefully excited whenever a shooting star streaked across the night sky.

Clearing the cache on your computer is (usually) a quick and easy way to help speed it up. Deleting those temporary files frees up space, helping you computer run smoother, especially if you have not cleared the cache for a extended period. However, finding the different caches in Windows 8 is a little trickier than in previous Windows systems.

You've probably noticed how we like to stress the importance of a strong password. After all, there are still people out there who continue to use passwords like 123456 and even just "password". But passwords aren't the only barriers that protect your information.

It's no secret that there's a lot of surveillance going on these days. It's easier than ever to end up in a database, and even former government agents are speaking out about the atrocious amount of spying being done against our own citizens. They've targeted our laptops, cars, IP addresses, and now they're coming for our iPhones. AntiSec hackers managed to get their hands on a list of over 12 million Apple UDIDs (Universal Device IDs) from an FBI computer, and they published 1,000,001 of the...

Every once in a while, Minecrafters want to create a simple hidden piston door to secretly hide all their valuable items. Now, it's possible with only 18 redstone, 2 repeaters, 12 sticky pistons, and ONLY 20 blocks of any kind!

It's summer, which means vacations, barbeques, and, most importantly, no school. But that doesn't mean you can't learn something while you lounge by the pool. Schools and organizations all over the country are offering online courses taught by real professors—for free.

One thing that's always important to have in your home office is a bulletin board, because they let you quickly display papers that you need to see every day, such as schedules, notes and memos.

Builds in Minecraft aren't usually for your own personal enjoyment; most people want to show them off to others. So to some extent, builds need to be user-friendly. That is, they should automatically guide people to areas of interest or importance. One particularly stylish way to do that is by using guide lights. I have two different designs included here, which you can either use or adapt to your own purposes.

Hello! This tutorial is made for all who like to sunbath, but also do not want to get those tiny first wrinkles too soon. Or even skin cancer.

Brushing your teeth is a necessity. You don't want to walk around with yellow teeth and stinky breath, and it's common courtesy to those around you to care about your personal hygiene at least that much.

This Hello Kitty drawing is a sketch of an image from the "Hello Kitty" website. It's adorable and isn't the typical image you see on a Hello Kitty character. DragoArt has this video tutorial on how to draw Hello Kitty. Get more detailed instructions on the step-by-step cartoon drawing here.

Unlike typical waxing, which strips your skin of vital moisture, causing inflamed, dry, and itchy skin as well as ingrown hairs, sugaring is a slightly gentler way of removing hair. Because it's all-natural, made generally of sugar, water, and lemon juice, it irritates the skin less because there are no artificial ingredients or harsh chemicals.

In this video series on scrapbooking you will learn many tips and techniques that will help your scrap book come alive and push your creativity to become more personal which will, in turn, create a more personal scrap book.

Gmail uses TLS, or Transport Layer Security, by default for all email communications, so all of your emails will use the standard encryption as long as the recipients also support TLS. But there's a way to add even more security to your Gmail emails, and you can use your iPhone's Mail app to do it.

If you're living or staying out in the middle of nowhere or a rural area outside of a big city or town — where there are no reliable cable, fiber, or wireless networks available — how can you get an internet connection? There are several possibilities, but they all come with tradeoffs, which we'll go over in detail.

As protests surge in the wake of George Floyd's murder by a Minneapolis police officer, powerful photographs and videos from the demonstrations have gripped the world, putting our nation's very real and very justifiable widespread civil unrest out into the digital world. Unfortunately, these pictures could put you or others in danger if precautions aren't taken before uploading them online.

The original iPhone SE was, for some, the perfect iPhone. It brought back the popular one-handed form factor of the iPhone 5 but packed in the internals of the then-new iPhone 6S. Now, the second-generation iPhone SE is here for 2020, but can it live up to what made the first-generation iPhone SE so popular?

You're a busy, on-the-go professional, so you deserve an email client that keeps up with you. "Mail" on iPhone wasn't always the best option, but thanks to iOS 13, it feels like a completely different app. That said, there are plenty of alternatives that offer a different experience. Better yet, these apps are free. You won't need to spend a dime to try them out for yourself.

For many of us, our work phone and our personal phone are one and the same. Just any old phone isn't going to cut it when you need to meet a deadline — a phone with built-in features that make it easier to get things done is almost a must.

When it comes to platform games on mobile, endless runners are some of the hardest to play since they can go on seemingly forever. There's always room for improvement since your goal is to beat your previous score (or someone else's high score). But which endless running games are worth your time?

Over the years, we've seen security breach after security breach, as well as high-profile data scandals where collected personal information was misused by companies. Apple makes customer privacy a priority, so there have been few issues to worry about when it comes to its services on your iPhone. However, there are still plenty of privacy settings to explore and change, especially within Safari.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

While there aren't as many ways to customize your iPhone like there is on Android, there are still a lot of apps out there that can help streamline and enhance your experience beyond Apple's own default options — and we've hand-picked over 100 essentials.

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

A new technological movement without the technology itself is just an idea sitting and waiting. Once the technology is present in the equation, movement forward can begin. This is how many of us see the head-mounted displays (HMDs) and smartglasses that have recently entered the augmented and mixed reality market — or are coming out in the next few months. This is a movement that will sweep over the world, changing everything in its path, and these are some of the people behind it.

As an adult you will come a cross a point in time when you need to make the right impression by writing a formal letter. Follow the format and you will be able to be most effective at conveying the information in your letter.

How much time have you wasted, wandering around your home trying to find one particular book? Without a good system of organization, finding the book you're looking for can become a hopeless task. Organize your book collection at home by following this tutorial.

In this online video series learn aerobics from personal trainer Ricketta Butler, who holds a Health Science Education Degree from the University of Florida. In this series of video clips she teaches aerobics exercises such as : the a step, hop turn, knee straddle, alternating knees, L step, basic left, over the top, basic right, safety for step exercises, straddle, turn steps, v step left, v step right, and the v step right and left.

While there's an art to surviving the all-nighter, there's also an art to staying awake throughout the day when you're operating on little to no sleep. In 1964, the record for sleep deprivation was set by 17-year-old Randy Gardner, who stayed awake for an incredible 264 hours and 12 minutes. Now while we're not out to challenge Randy for his title, we can certainly look to him for inspiration in beating back our own fatigue.