
News: Google Glass Engineer's Patent Application Points to Potential Google AR Headset
If you thought Google was sitting on the sidelines of the growing race toward mainstreaming augmented reality, think again.


If you thought Google was sitting on the sidelines of the growing race toward mainstreaming augmented reality, think again.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.
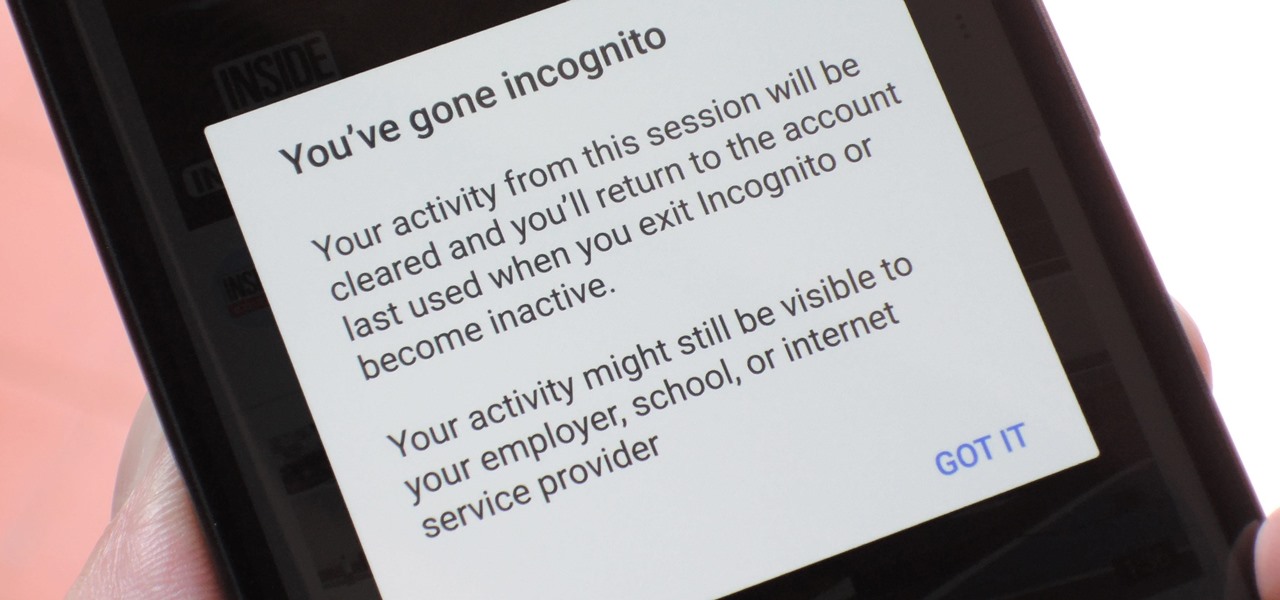
Incognito Mode is a privacy feature that was popularized by Google Chrome, and it recently made its way to GBoard. Now it's coming to the YouTube app to help make your video watching experience truly private.
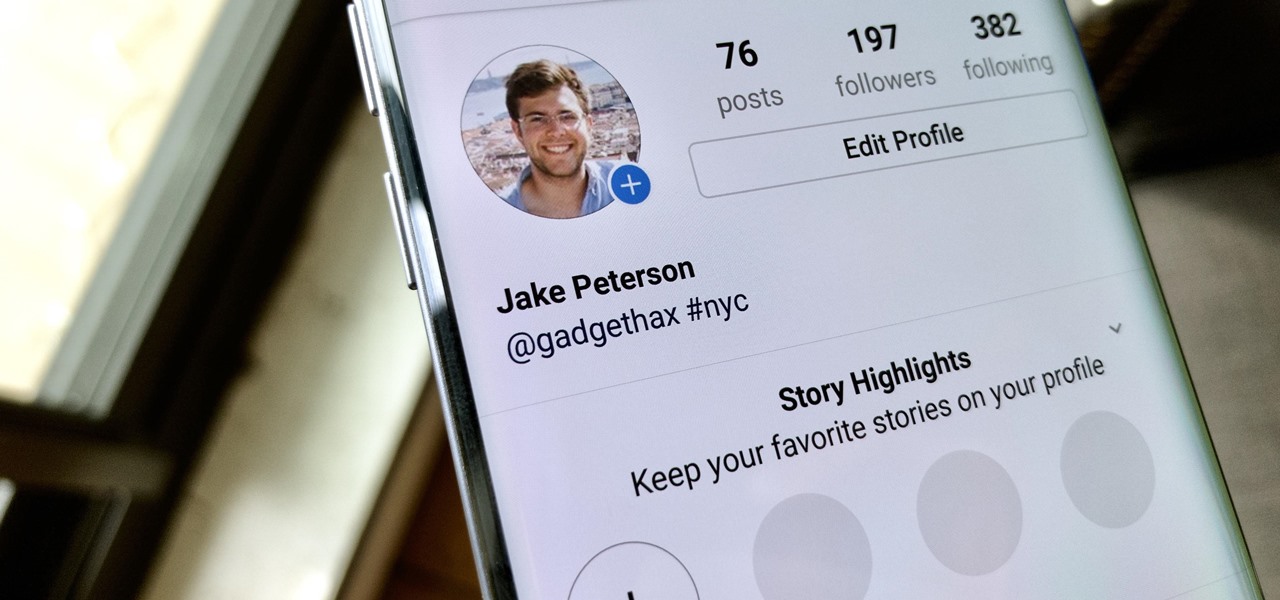
Your Instagram bio could always be used to link to other websites or profiles or just to show off your witty personality. Now, you also have the ability to use this section to tag other Instagram accounts as well as add tappable hashtags. Whether you want to link out to your best friend, company, or the latest trend in your city — if it has a profile name or tag, it can be in your bio.

With Virtual Network Computing, you don't need to carry a spare keyboard, mouse, or monitor to use your headless computer's full graphical user interface (GUI). Instead, you can connect remotely to it through any available computer or smartphone.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

As interest in augmented and virtual reality continues to grow, so does the need to bring objects from the real world into virtual space. With that, there's also now an increased need for solutions that bypass the time-consuming process of producing handmade 3D models.

Another day brings another Apple ARKit demo, this time for a first-person role playing game that inserts villagers, vendors, and villains into real world locations.

It's fitting that students at the University of Washington can catch a glimpse of the new, 135,000 square-foot computer science building in augmented reality before construction is completed.
Within the last week, there have been at least three times when someone asked me to play a good playlist. This is always a tough call. What if I play something that nobody likes? I probably will.
Snapchat is rolling out some awesome new features in their update today. The major update comes just two weeks after the company's premiere of backdrop, snap shopping, and voice clip features. They rolled out two new features this time, Multi-Snaps and the Tint Brush.

Russian phone customizer Caviar — you might have heard of the blinged-out iPhone 6s Pokemon GO phone they released a few months back — is taking on international relations with their newest product.

Typing out thirty hashtags on Instagram is always such an annoying process. Figuring out the best hashtags to use to get more likes is also tricky. You can't just keep copying and pasting the same hashtags on every post — that's like attacking the same tribe every time. You got to diversify, which takes a lot of conscious effort to be on top of the current best hashtags to use.

Driverless transportation is definitely coming closer to the mainstream, but most companies developing the technology have said it will be another couple of years before we see autonomous vehicles being used as an alternative for typical transportation.

There is a reason the Amanita phalloides mushroom is called the "Death Cap." It can kill you. Mushrooms are a type of fungi, an organism that produces thread-like mycelia that often produce spores. Spores allow the fungi to reproduce. Molds, lichens, and yeast are all fungi, but the most visible fungi are mushrooms. Some fungi are delicious, but others can cause disease or, and still others, like Penicillium, can cure it.

With the US Department of Homeland Security (DHS) banning laptops and tablets on flights originating from 10 international airports, and the United Kingdom taking similar precautions, international travelers are faced with hours of non-productive — or far less entertaining — flight time.

Dramatic new research may change the fate of the hundreds of people who wait for a kidney transplant every year. The study hinged on the ability to cure hepatitis C infections, a possibility that became a reality in 2014.
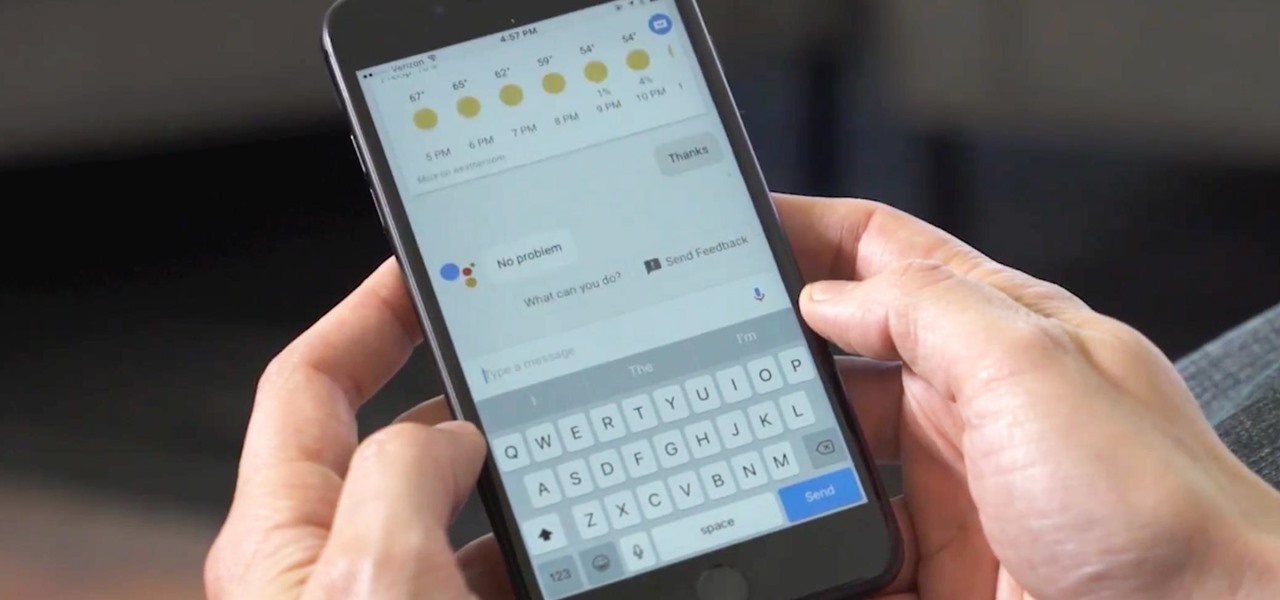
As we've said before, Siri has some major competition moving into its own playground, and Google just announced at its I/O event that Google Assistant is available on the iPhone, starting today.

Kik is an extremely popular messaging app, but it has a few annoying features that we all just sort of put up with. You can't turn off read receipts, nor can you hide when you're typing, and the photos you take with Kik's camera show up differently than ones you send from your gallery app. At least a couple of these features should be subject to change, but they aren't — well, not without some tinkering.

As many as 700 species of bacteria live on our teeth and in our mouth, and just like the microbiomes inhabiting other parts of our bodies, they change in response to diseases and other health conditions.
Android is a highly customizable operating system. Sometimes, we use these capabilities to add core functionality or streamline the user experience, but there are other times when customization is just about having fun and making your smartphone's interface more enjoyable.

Merge VR, a company mostly known for its virtual reality experiences, is moving into and creating an augmented reality experience that combines an iPhone or Android smartphone, a set of goggles to put your phone in, and a box about the size of a Rubik's Cube which looks more akin to the Lament Configuration seen in the Hellraiser film series. When used in concert with the smartphone and goggles, the toy cube, called Holo Cube, becomes one of many AR experiences.

Origami is the Japanese art of folding paper, which has been around since the 1600s. The word origami comes from the two Japanese words ori, meaning "folding," and kami, meaning "paper."
Google has added a number of new features in the latest update to Google Keyboard including a one-handed mode and a setting that lets you adjust the height of the keys. The update hasn't gone live on the Play Store yet, but you can download the APK right now for both 32-bit and 64-bit phones.

Google Now, Siri, and Cortana aside, the main way you interact with your smartphone is through the keyboard. Every app you use, every search you perform, every message you send—the most fundamental interface between you and your device is that handful of characters and those 26 letters on the bottom half of your screen.

In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

Hello Everyone! I wanted to share a free and open source note taking tool that I've been using for quite some time now.

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them

From laptops to tablets, technology is taking over classrooms. Elementary schools offer kids tablets, and college students are bringing laptops into lecture halls, leaving their notebooks behind. Today, many students prefer putting their fingers to a keyboard rather than pen to paper, but are these helpful devices truly beneficial?
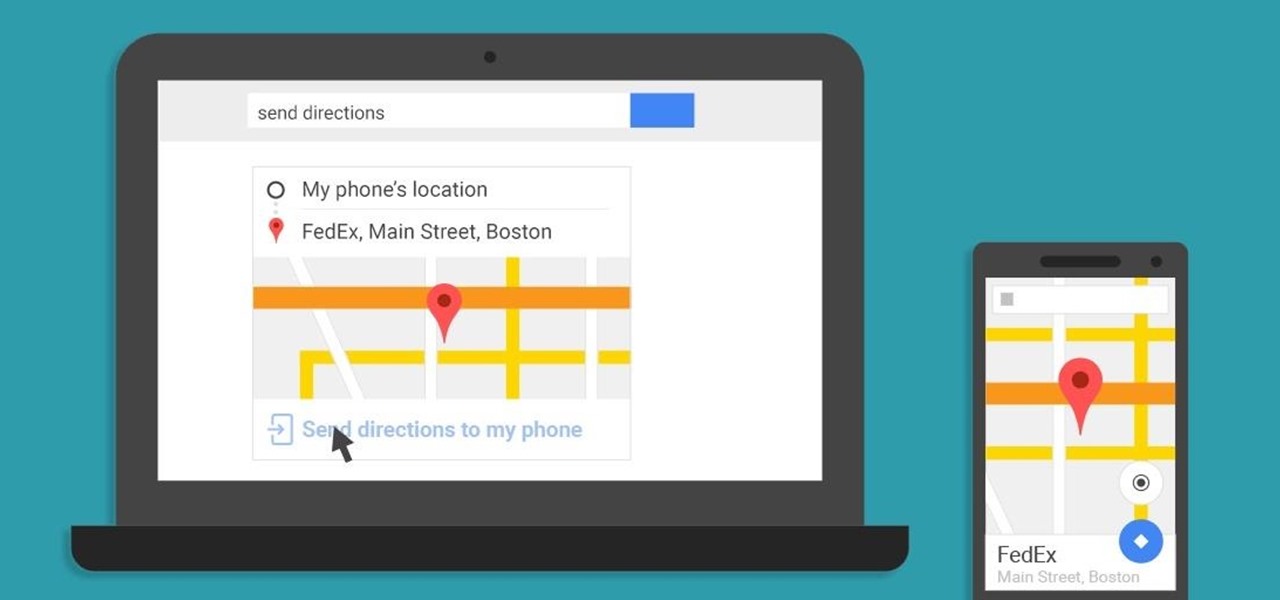
A set of cool new Android-related Google Search functions made their debut this week, which will allow you to locate your phone, send directions to your mobile device, set alarms and reminders, and send notes from any web browser.

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

What Is IPython? IPython is a richly featured replacement for the standard python interpreter. It offers a wider range of functionality, that the standard

Hello Elite Hackers! Welcome to my 3rd Post, which explains how to hack any account like G-mail, Facebook, etc.

The Nexus 6 is one of the few devices on the market that sports a 1440p "QHD" display. This means that the amount of pixels displayed is higher than almost any other smartphone, which sounds great on the surface, but is not without its drawbacks.
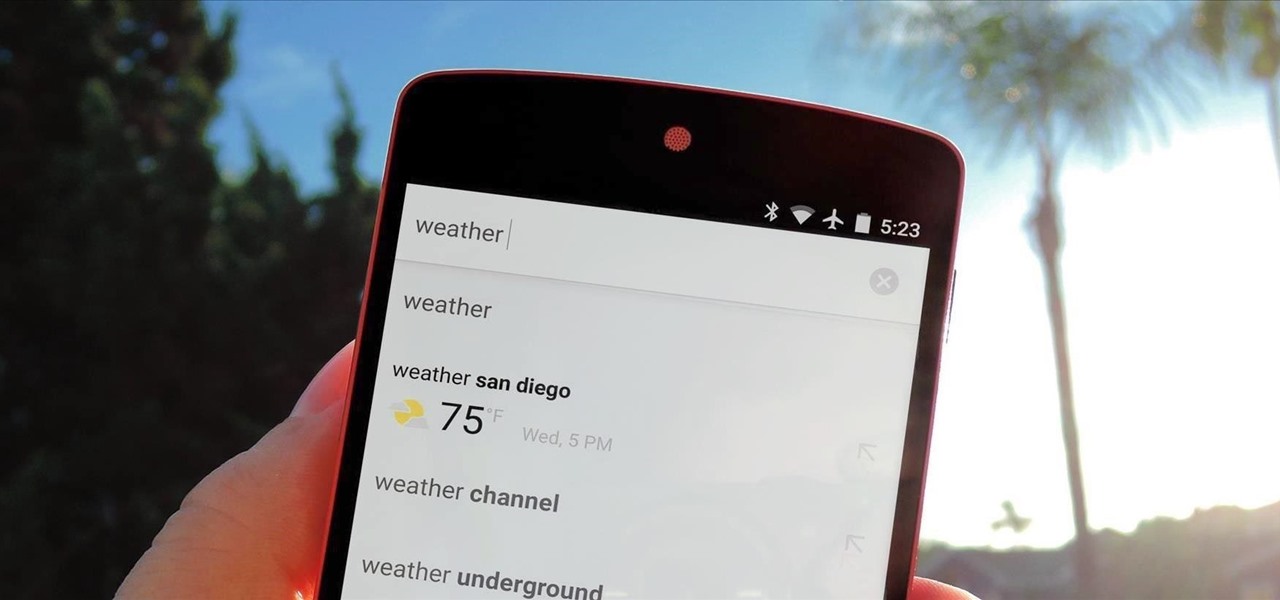
Google continues to be the most commonly-used search engine for a reason. While continuing to stay ahead of the pack with advanced semantic search functions, Google even introduced Knowledge Graph results that offer key information without ever having to click a search result.

When exercising at a high intensity, you know to expect some level of pain. That can make it difficult to identify when your body gives you a warning sign of injury. If you pay close attention, however, you can tell the good hurt from the bad. I talked to Dr. Brian Parr again, professor at the Dept. of Exercise and Sports Science at the University of South Carolina Aiken, who explained which symptoms of exercise are normal and which are bad:
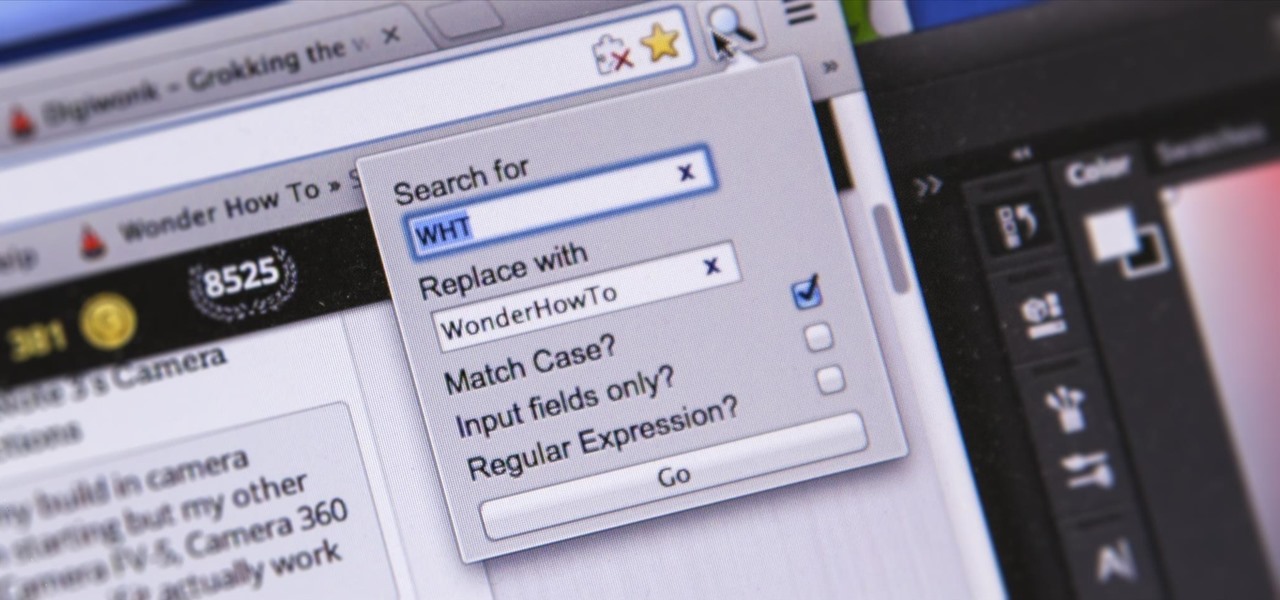
I'm sure you've been there—halfway through typing something out, you realize that one word you've been using more than any other has been misspelled. Perhaps it's a single word, acronym, or line of code that you find yourself typing quite often at work, but this one requires complicated hand gymnastics that you'd simply rather not perform over and over again.

There are so many mods we can apply using a custom recovery. From themes to bug fixes and feature ports, a typical rooted user spends a decent chunk of time in TWRP Recovery.