
How To: Make your own track dolly
Build a track dolly for about £80. This is great for getting professional dolly shots when making your own films.


Build a track dolly for about £80. This is great for getting professional dolly shots when making your own films.

You won't believe its vegan, a creamy rich sponge cake that everyone will love. Serves: 12 approx

Learn how to use 17 warm up stretching drills for your feet, legs and knees. These types of exercises are important for atheletes and high impact, explosive activities.

Learn some terminology and topics that will help you be better prepared for your next trip to the lumber yard. Just a few of the topics covered include identifying different types of cuts, estimating board feet, and finding a good hardwood supplier.

Add storage space to your computer by either adding an additional drive or swapping out your old one. Note: This is for Parallel ATA type drives only.

For beginning DJs. Learn how to use and fine tune the pitch control. This method applies to all types of turntables, not just the Technics sl1200!

Dave shows us some unusual types of clematis with striking flower colors and shapes and resistance to disease. Any plants that are resistance to disease are a good choice.

In this video Chef Sanjay shows you how to make three different types of Indian fish pakoda. Sanjay is using mahi but you can substitute for your favorite fish or market availability.

This video is all about creating dolly shots. If you have ever wondered about how to use and control this type of shot, then let Israel Hyman show you. This is a great alternative to zooming in and out which is unnatural for our eyes.
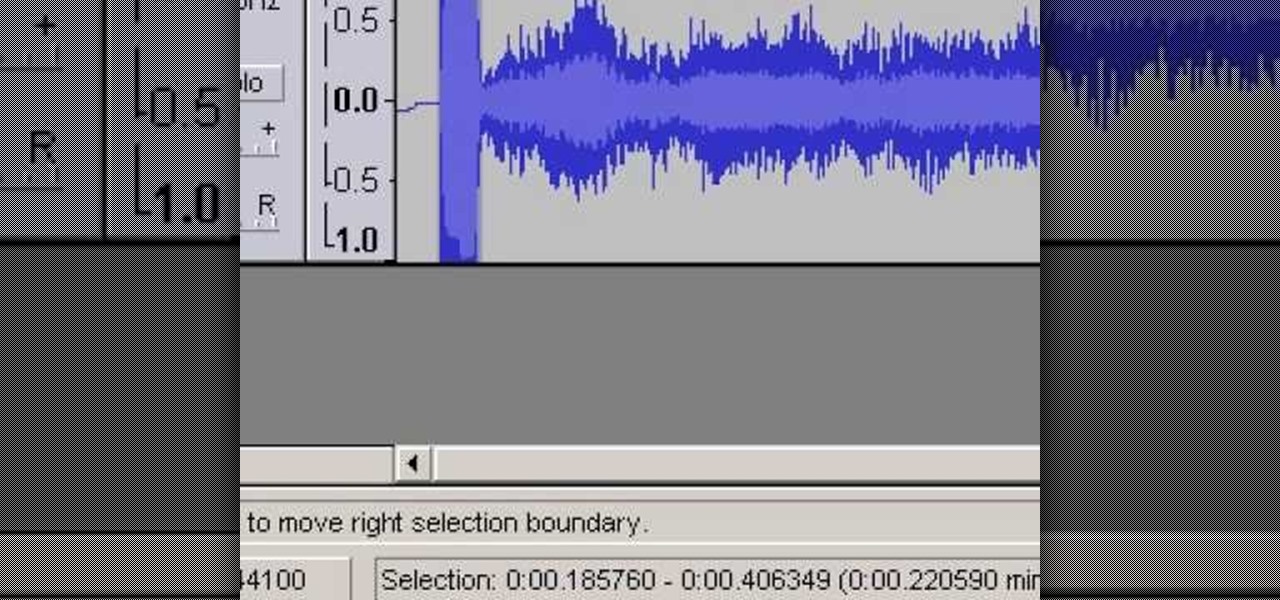
Learn how to change the default action that the Firefox web browser takes when opening a type of file including .mp3, .midi, and others.

Learn the steps for making an easy shrimp fried rice, including a trick for frying the egg in the middle of the ingredients. You will need cooked rice, frozen cooked shrimp, frozen baby peas, green onion, olive oil eggs and low sodium soy sauce. Fried rice can be made with any type of protein - enjoy making this Asian dish for your family!

Your video footage does not need to come from a camcorder or iMovie HD. In this tutorial you will learn how to import other types of video into iMovie '08.

In this episode, The Shirtless Apprentice gives us some tips and information on how to use one of the most versatile and under appreciated tools in a videographer"s arsenal, the sungun! Matt compares two types of sunguns, incandescent and L.E.D., and weighs the benefits of each.

Jeff Schell shows you how to create a spinning headline or front page of a newspaper. You'll see how easy it is to build this special effect for any type of image or clip using a pair of rotation keyframes and scale keyframes, and by specifying your keyframes in reverse order.

Sample different types of threads and sewing machine settings to learn the best combinations for varying sewing projects and effects.

Unfortunately not everyone goes through the effort of making form fields on their forms. So rather than print the form out and fill it out by hand, use the Acrobat Typewriter Tool to click right onto the form and type right onto it without the need for form fields. In this video you’ll learn how.

Been trying for those 6-pack abs without much success? According to oodelboxTV fitness guru Wes Cole, odds are you aren’t working out the correct type of muscle fibers. What? Watch and learn what that means AND how to get a brick belly.

This video demonstrates how to work out your quadricep muscles using a leg extension machine. The video walks you through adjusting the machine to your body type and explains how to perform the exercises correctly.

This video demonstrates how to use a leg press to work out your quads and glutes. The video walks you through setting up the machine to your body type and performing the exercises correctly to avoid injuries.

Ironing can be a bit tricky, with so many different designers and clothing materials to choose from. This video shows you how to iron a blouse and skirt so each looks perfect every time.

It doesn't matter what type of cuisine you're cooking - more likely than not, you're tossing the ingredients in a pan and smearing oil all over it for extra succulence (as well as to coat the pan). While a healthy dose of oil every day is vital for absorbing vitamins and nutrients, getting too much oil will land you in heart attack town.

Chef Chris Smith makes two different types of smoothies including a chocolate peanut butter and a berry smoothie usng berries, soy milk, tofu, banana extract and fiber fruit smoothie. Both demonstrations are low carb smoothies.
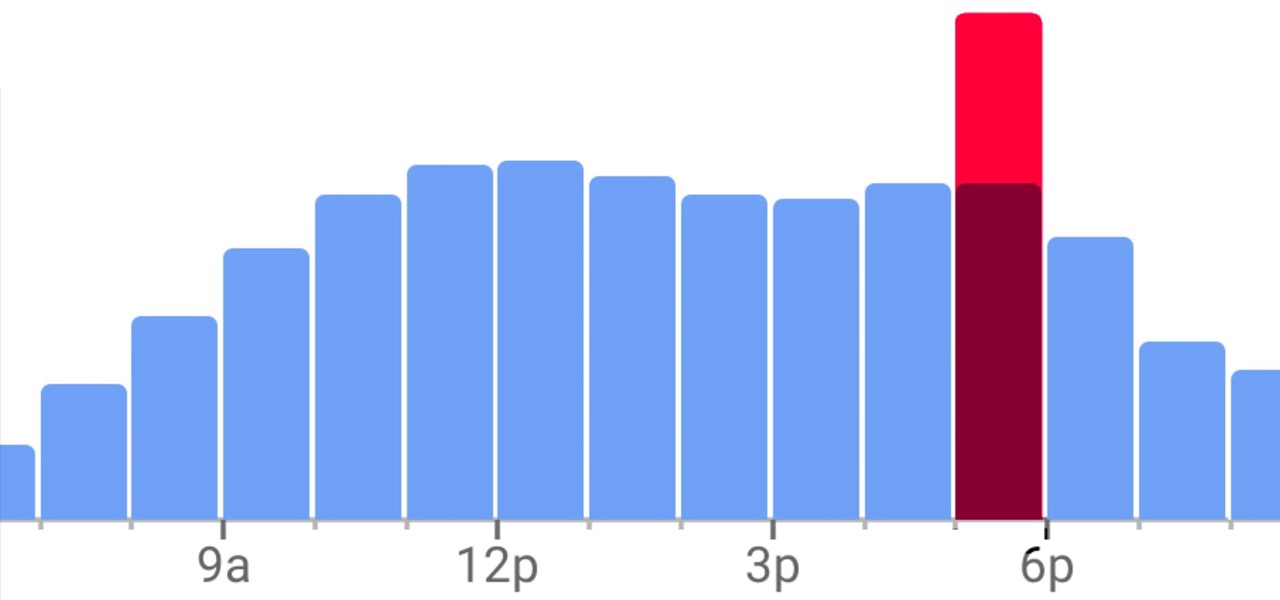
Unlike Apple Maps, Google Maps can tell you when a restaurant, bar, club, or other business you're thinking of visiting is busy. It's extremely helpful if you want to avoid peak times or wait for the place to be empty. If you can't pry yourself away from using Apple Maps, there's an easy alternative to see the popular times of most businesses.

Whenever you need to type out a fraction on your iPhone, whether in a message, word document, presentation, math problem, recipe, or wherever else you need it, it's easy to use numbers and slashes. But there's a way to make fractions look more professional and easier to read straight from your keyboard.

If you do a lot of typing every day — writing reports, essays, emails, and whatnot — we can guarantee your day would be improved by taking less time to do it. Thankfully, we've found a super-smart AI-powered tool that will do just that, and right now, you can get an amazing 52% off a Lightkey Pro Text Prediction Software: Lifetime Subscription for the sale price of just $79.99 (regular price $169).

Let's say you're using your iPhone's Calculator app, and you're knee-deep into a complicated calculation with many steps. You type in a large number, for example, "123,466,789," but mess up. You meant to type "5" midway through but accidentally typed "6" instead. The only thing to do now is start over, no matter how far along you are, right? Wrong.

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.
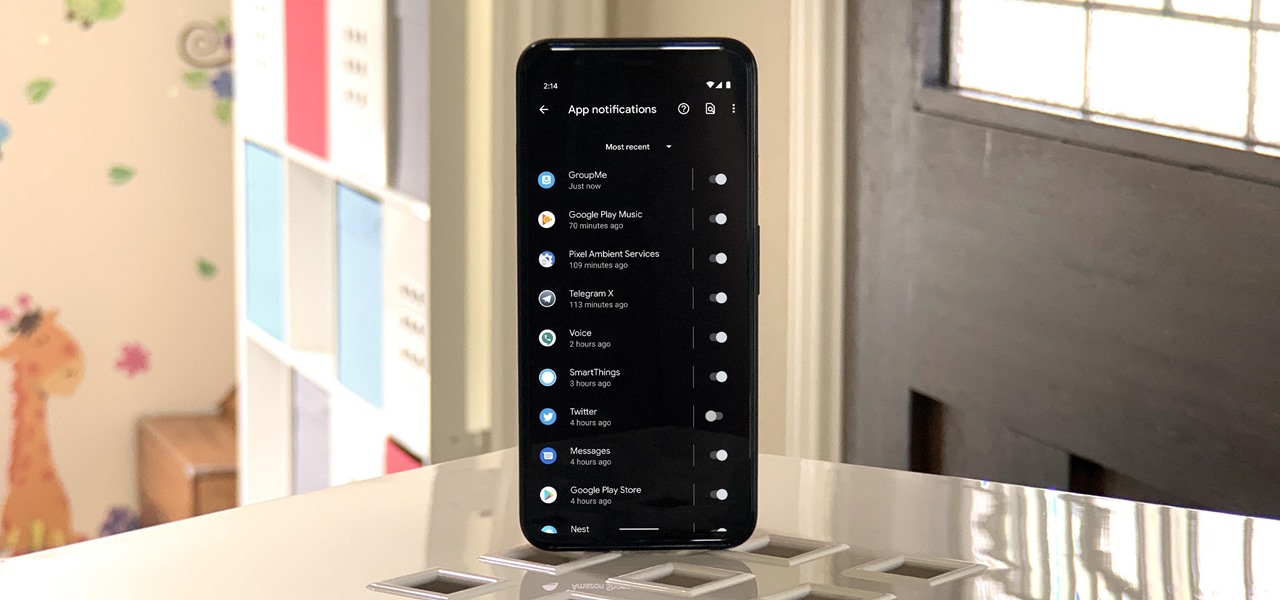
Sometimes you might find that a certain app keeps sending you notifications. What are you to do? There are plenty of useful apps that might send one too many push notifications, but that doesn't mean you should dump them. Luckily, Android gives you complete control over how each installed app handles notifications.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

You can easily deck out your favorite phone with great wallpapers, ringtones, and icons, but what about fonts? Not all Android skins let you change the system font, and even when they do, the options are often limited to a few choices. Certain root apps can open up the system font to customization, but some of these can cause problems now that Google introduced a security measure called SafetyNet.
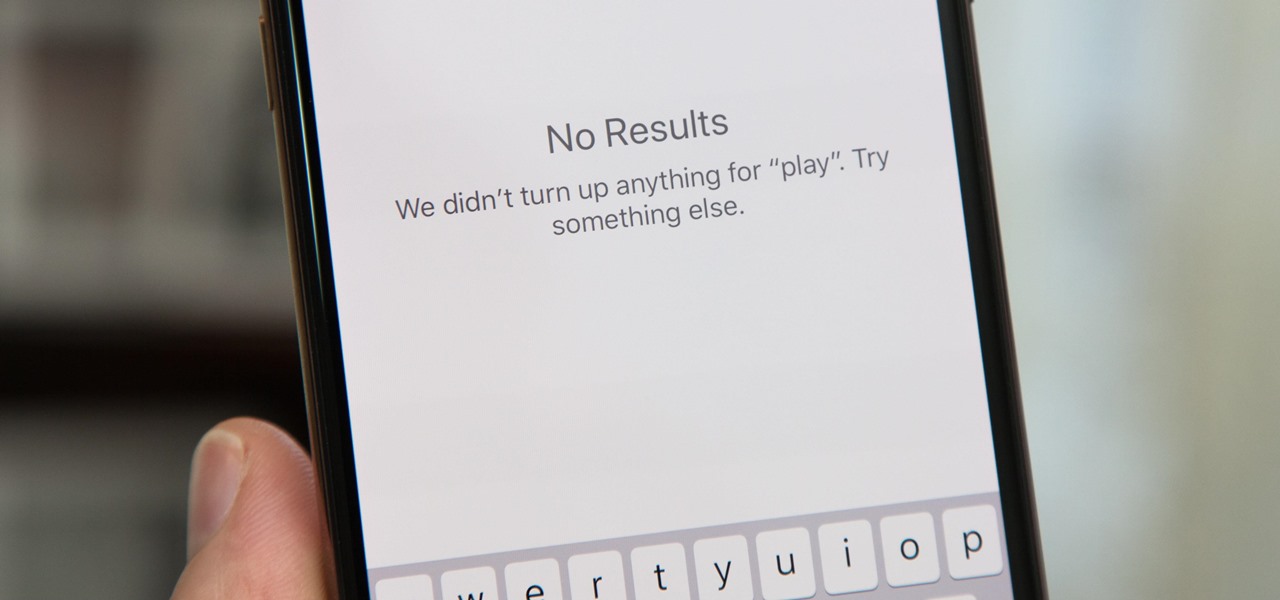
There's something seriously wrong with Apple's new Shortcuts app, and it's severely limiting the number of shortcuts users can install on their iPhones.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line. We'll use aliasing to set some simple commands for easy native packet capture on a macOS system.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

Long admired for their active and cooperative community behavior, some types of ants also wear a gardening hat. Nurturing underground fungus gardens, these ants have a win-win relationship that provides food for both ants and fungi. If we humans understand it better, it may just help us out, too.

As fun as it is to see Fido's face light up when you feed him table scraps, American dogs are getting fat. The good news is that research is homing in on nutritional strategies to boost canine capabilities to maintain a healthy weight.