
How To: Tie a Turk's head knot for sailing
This how to video tutorial demonstrates how to tie a Turk's knot for sailing. Follow along with the step by step process and the directions below to learn how to tie the Turk's knot.


This how to video tutorial demonstrates how to tie a Turk's knot for sailing. Follow along with the step by step process and the directions below to learn how to tie the Turk's knot.

Prepare this wonderful easy vegan meal for six. It only requires a 10 minute prep time and it cooks in 35-40 minutes.

If you have not used your eRecovery system in a long time and have forgotten the password, have no fear. This video is here to help you retrieve your details and use your program again. In this clip, learn how to recover any lost passwords with Acer's eRecovery Manager for Linux.

There's no default keyboard on the Apple Watch, but watchOS has another way to let you type text out for emails, messages, music searches, and more on the small display, and that's Scribble. With it, you simply draw letters and other characters on the screen with your finger, then your watch converts that into plain text. However, it's not perfect, and getting the nuances of regular typing can be tough.
Apple's iMessage is one of the main reasons to use an iPhone, and there's a lot you can do in chats without being overly complicated. But there's one issue that continues to drive people nuts, and that's the blue typing bubble indicator with the moving ellipsis (•••). Can you stop it? Not officially, but there are workarounds.
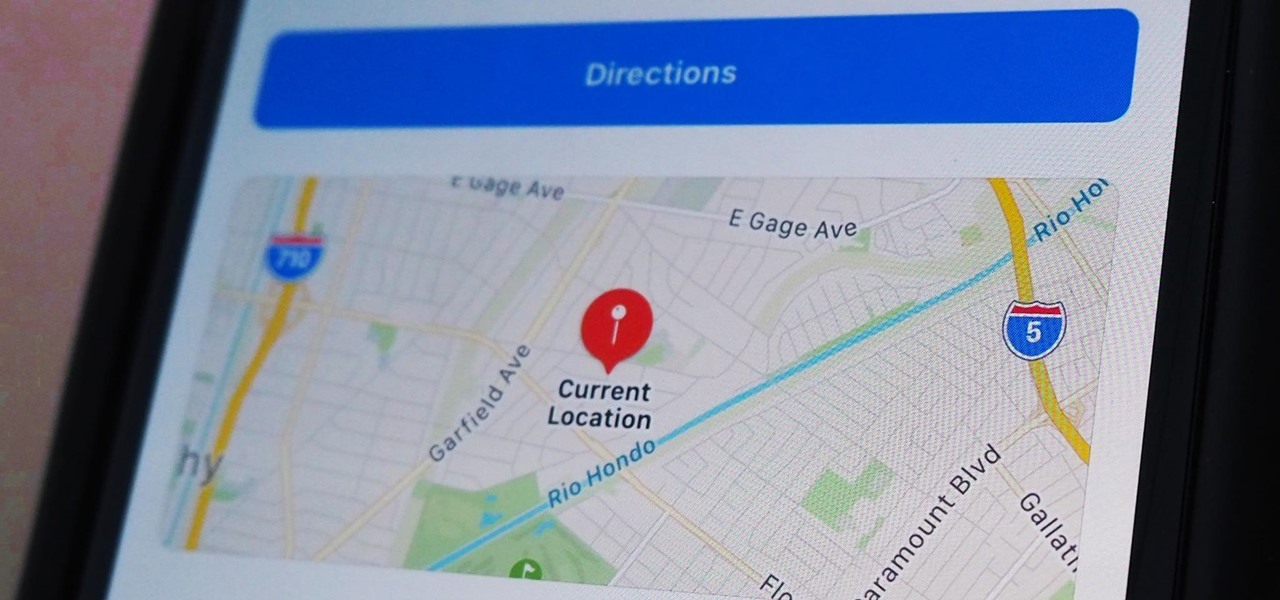
Apple makes it simple to share your location with your family and friends using tools built into the "info" page for each conversation thread in Messages. With those tools, you can send your current location or share trackable real-time coordinates. But iOS always has a few hidden tricks to make things easier than they seem, and that's precisely the case if all you need to do is share your current location.

If you're using the default Samsung Keyboard on a Samsung Galaxy smartphone or Gboard on a Google Pixel or any other Android device, here's a cool trick you should know about.

Undo. Redo. These two actions are forever intertwined, but they're missing from the standard keyboard on Android. Accidentally delete a word, and there is no Ctrl + Z to undo this mistake. But there is finally a solution available on Samsung Galaxy phones.

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.

Life is too chaotic to be organized all the time, but little steps in the right direction make things easier overall. File folders keep paperwork from spiraling out of control. Spice jars take the clutter out of cabinets. Storage totes keep basements neat and tidy. But to find what you're looking for faster, you need a label maker.

One of the hallmarks of augmented reality's coming of age is that the technology is starting to find a home in business categories that are less obvious compared to typical AR enterprise use cases.

Apple has packed a lot of new features into the iOS 13 update, and practically no core app has gone untouched. The Messages app, in particular, got plenty of love, including new ways to dress and use your Memojis.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.
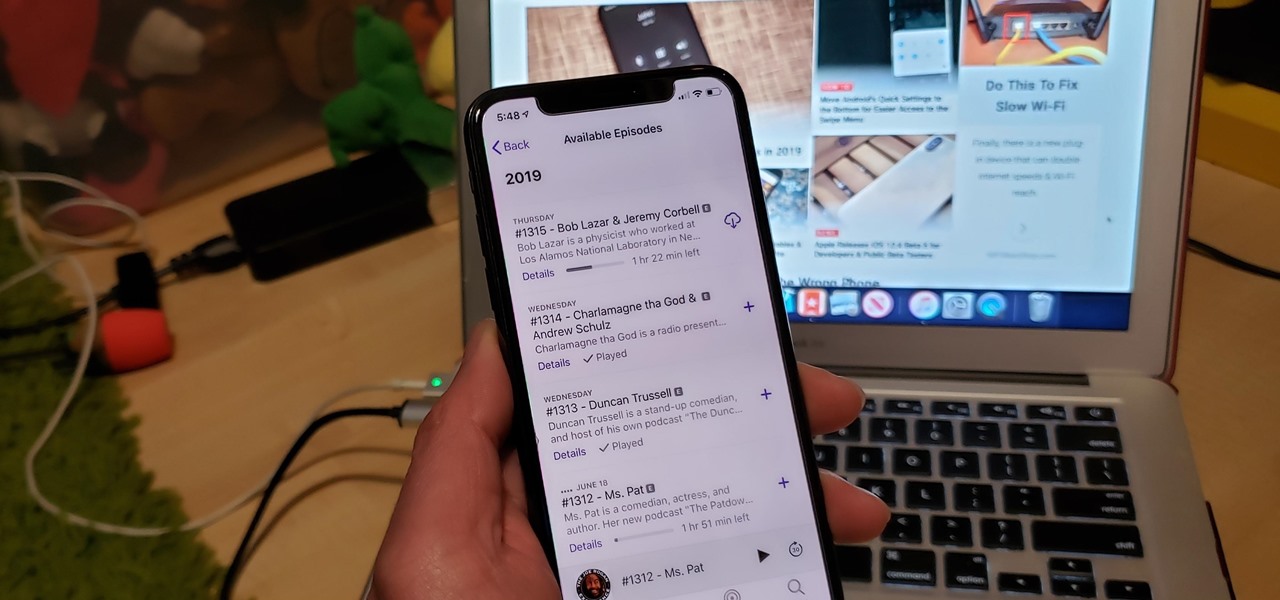
A typical hours-long podcast can cover a broad range of topics, and it's not uncommon to stop listening halfway through an episode or to skip through the parts you don't want to hear. Unfortunately, in the Apple Podcasts app, unfinished episodes remain within the app's My Episodes list and will play again automatically once you've finished a previous episode.

Sports technology company Form is testing the waters for augmented reality wearables with a product aimed at a very specific user group.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.
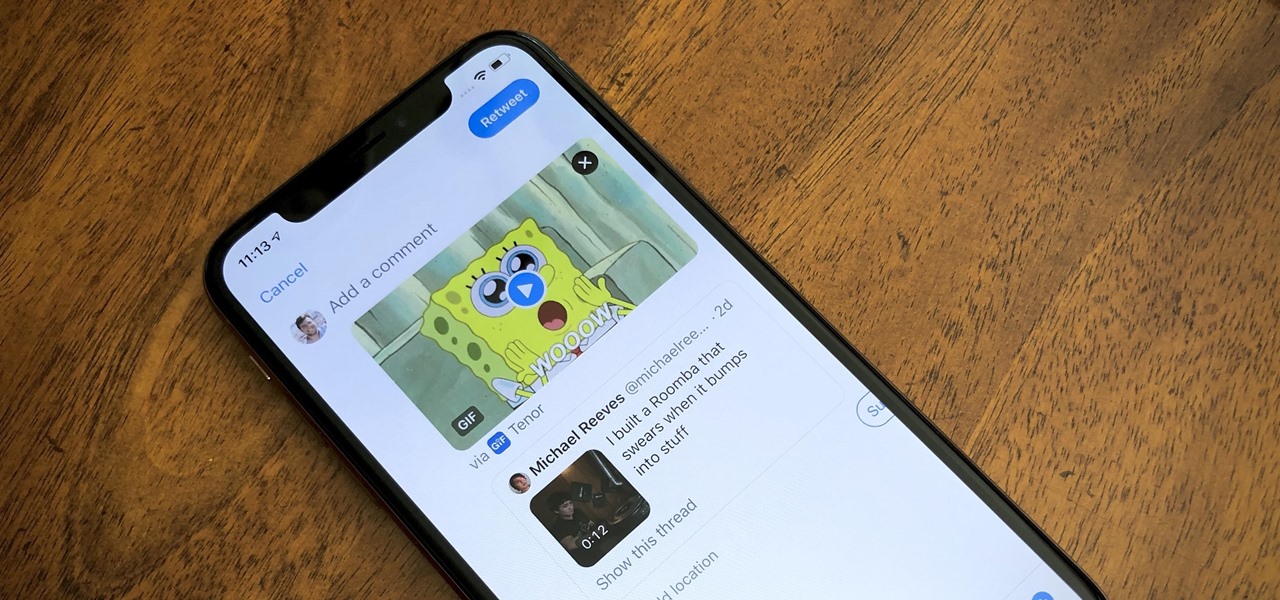
On Twitter, quote retweets are a great way to share someone else's tweet with your view of their message. Twitter has expanded on this idea by giving us the ability to attach images, video, and GIFs to quote retweets. With these extra options, you should have no problem adding your own unique perspective on that funny, serious, or professional tweet.

Until very recently, Apple apps were among the only ones that would play nicely with Siri on iPhones. If you wanted to take advantage of the digital assistant to, say, compose an email, you would need to go with Apple Mail instead of the email client you actually use. As of iOS 12, this is no longer the case.

Snapchat is joining the ranks of Netflix, Hulu, Amazon, YouTube, and Apple in the trend toward streaming original programming, but with a twist that rings true to its roots.

This year marks the first for Apple to exclude the Home button from any new iPhones. If you're going from a Home-button iPhone to a new XS, XS Max, or XR, you might be a bit stumped when trying to perform basic tasks, such as activating Siri. While you can't hold down the Home button any longer, there's a new method that's just as quick.

Automotive augmented reality company WayRay has set its destination for a $1 billion valuation with an estimated time of arrival of 2019, and it has just passed a major milestone towards that goal.

Sometimes we need to share screenshots, but don't want to reveal the entire screen. This usually requires some editing that isn't typically easy to do on a smartphone. BlackBerry recognized this issue and created a tool called Redactor that makes it easy to hide your data before sharing.

The current iPhone lineup inarguably features Apple's best displays to date, but the stock wallpapers don't really do the screens justice. There are plenty of third-party wallpapers you can use, as well as ones you create yourself. However, if you want that typical Apple feeling, you're better off sticking with Apple wallpapers, and the iPad Pro has some beautiful ones that look awesome on an iPhone.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

Augmented reality is expected to eventually change everything, and the prevailing view is that those changes will be for the better. The converse view, however, is that the technology will further erode privacy.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

With Gboard, Google created a keyboard with more functionality than just inputting words. The app includes features such as GIF search and live text translation, but it gets even better when you let it learn more about you. With this data, Gboard grows from a good keyboard to one that can complete your sentences.
If you installed Android 9.0 Pie, you might have enjoyed trying out some of the new features in the latest version of Google's OS. However, change isn't always a good thing, so you might be wishing you could downgrade back to Oreo right about now. Good news — you can.

Thanks to Samsung Experience 9.0 on the Galaxy S8 (AKA TouchWiz Oreo), we know the upcoming Galaxy S9 is going to enjoy some of the new keyboard changes coming to Samsung's iteration of Android 8.0. Those who preorder the device on March 2 or pick it up on March 16 can expect these changes out of the box, as the S9 will be running Samsung Experience 9.0 on day one.

In 2017, after purchasing a majority of the 600 MHz frequency, T-Mobile began a massive rollout of the new LTE Bands across the US. However, there are currently only two devices that support the frequency, also known as LTE Band 71. Thanks to a recent FCC listing, we've learned this number will double when the Galaxy S9 and S9+ debut next month.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

Razer, the company known for PC peripherals and laptops, is joining the smartphone industry with a new device. Rumors have been swirling since they announced an event on November 1 at 4 PM EDT, but now, we have our best look yet with a leaked promotional video before the actual announcement.

Apple introduced Portrait Mode with the iPhone 7 Plus, a feature which utilized the iPhone's dual cameras to create a shallow depth of field around a subject. This effect replicates the look of DSLR cameras, making your photos look more professional. Apple, of course, carries Portrait Mode to the iPhone X and iPhone 8 Plus in iOS 11, however, with it comes a twist — Portrait Lighting.

On June 11, 2016, an Arizona woman died from what appeared to be several infections, including pneumonia. She likely caught at least one of these from her dog.
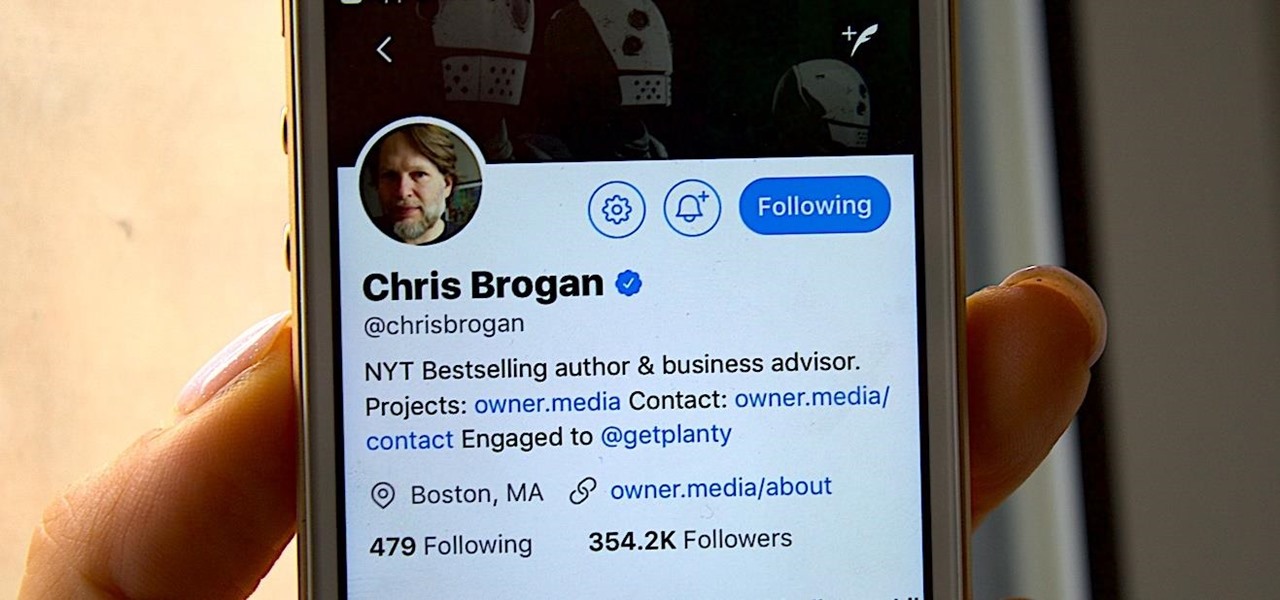
Chris Brogan is no stranger to using multiple social media platforms all from the comfort of his phone. In fact, not only does he have over 350,000 followers on Twitter, but he's also an avid YouTuber, Instagrammer, podcaster, and blogger.

Snapseed is an app that you should definitely be using not only if you're really serious about photography, but also if you want to ensure that your online work sets the standard for social media. It's a great companion app to Instagram and VSCO, and it will save your day many times over when you find yourself on your phone, on-the-go, needing to edit an image beyond the typical everyday filters.
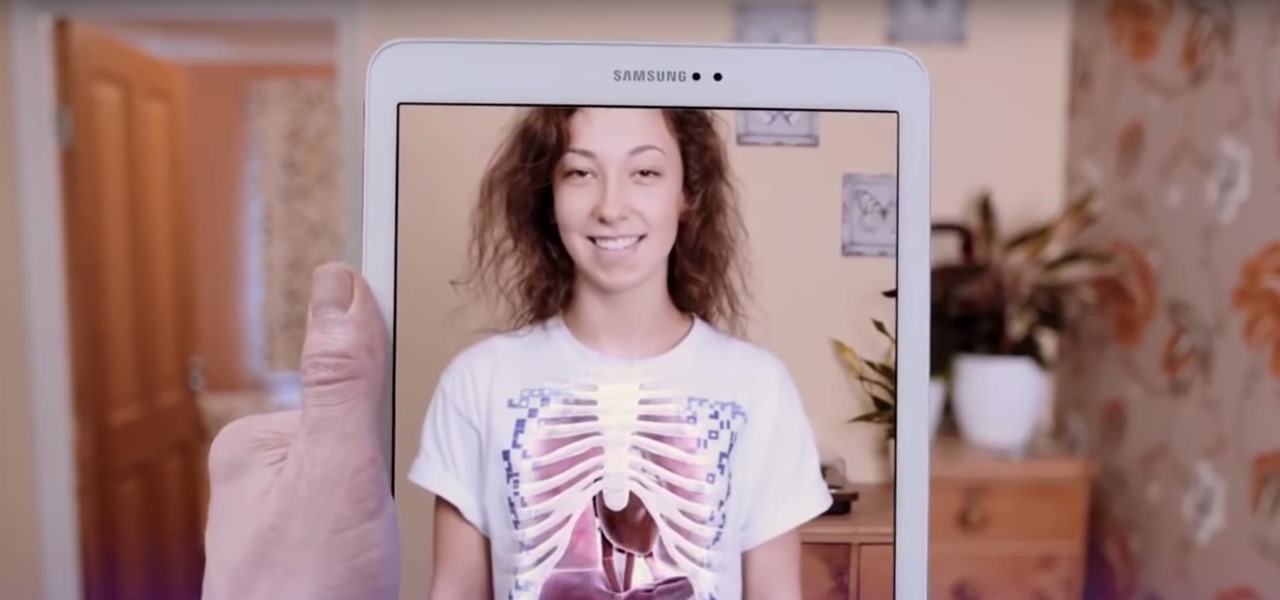
I have spent a good portion of this year traveling between cities and various emergent technology conferences and events. Most of these events have been really good, but in terms of augmented and mixed reality, the Augmented World Expo, in its eighth year running, definitely stood above the rest.
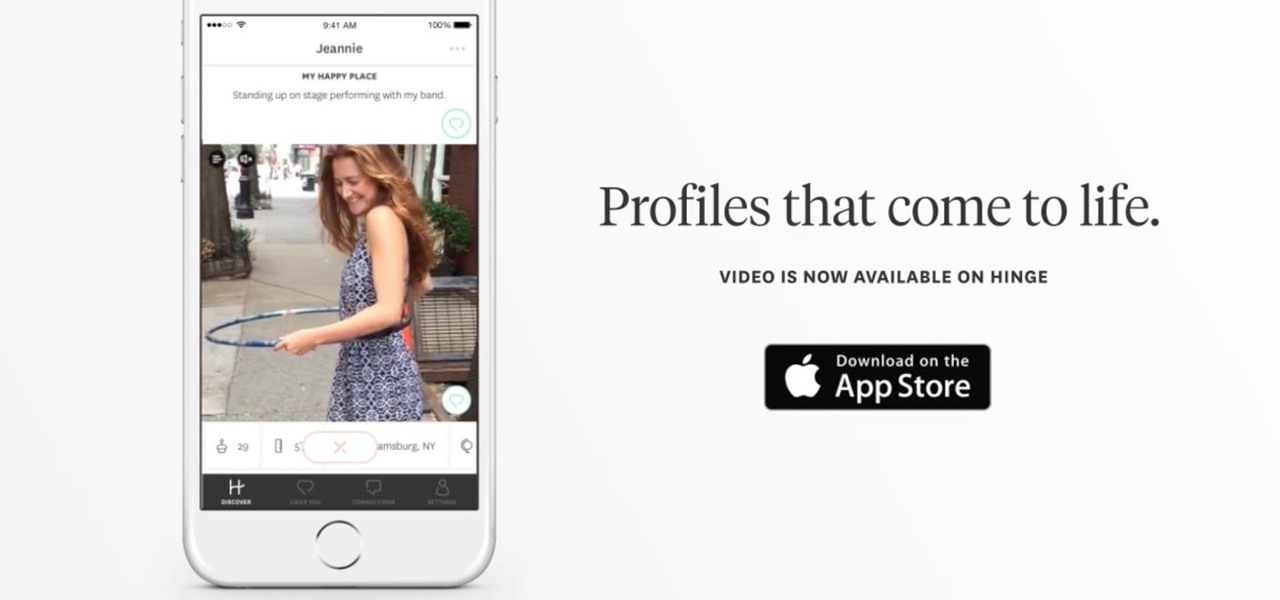
It seems we've come full circle in alternative dating routes. Just like a long time ago when people were able to go to matchmakers and watch videos of potential matches, the dating app 'Hinge' is now allowing you to add videos to your profile.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.
Today in Santa Clara, California, at the Augmented World Expo, Scope AR revealed a major new update that will add markerless tracking for their remote assistance application, Remote AR, on standard devices.