Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.

Welcome back, my fledgling hackers! In the first part of my series on Wi-Fi hacking, we discussed the basic terms and technologies associated with Wi-Fi. Now that you have a firm grip on what Wi-Fi is exactly and how it works, we can start diving into more advance topics on how to hack Wi-Fi.

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

Can't decide between the Galaxy S4 or the Galaxy Note 2? There are advantages to both the Galaxy S4 or the Note 2, it all boils down to what your needs are such as screen size, battery life, and more.

We'll show you how to use an attachment for a power washer called a "Foamer" - you'll never hand wash a car or boat again!

Welcome back, my newbie hackers! Hackers often are associated with clandestine and illegal activity, but that is not necessarily always the case. Hackers are increasingly being used and employed for law enforcement, national security, and other legitimate purposes. In this installment, we will look at how a single hacker could save the world from nuclear annihilation.

In this Windows 8 Tutorial you will learn how to search for application in the Windows 8 store. I know it can be a bit confusing for those who have just moved to the Windows 8 store on how to search for store applications in fact it took me like an hour to figure out how to search because all the visual cues were hidden away. However when you finish watching this Windows 8 tutorial you will see it is as easy as being able type on your keyboard to find applications in the Windows 8 store.

This Windows 8 tutorial, I will show you how to change the name of groups, and rearrange groups and applications in the Windows 8 start menu metro interface.

PRL, or Preferred Roaming List, basically tells your phone which towers to connect to first. Changing PRLs can improve reception and data speeds, and in some cases even give you access to corporate/test towers.

Welcome back , my fledgling hackers! Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look at inserting a listener (rootkit) inside a PDF file, exploiting a vulnerability in Adobe's Reader.

In my last hack blog on crashing your roommates Win7 system, we started looking at client- side attacks. As promised, we will be looking at some more client-side attacks.

Automator is a built-in Mac utility found in Mac 10.4+ and can be used to convert a PDF file to text format.

Programs that run automatically every time you start your computer can slow down your boot time—or just be plain annoying. Many of these programs are rarely used and don't even need to be running for your computer to function properly. So, if you want to disable these auto-run programs and increase your computer's startup speed, here are a few ways you can do it in the new Windows 8.

Here's a video on how to deal with pedestrian crossings in England. It's to help all of you taking driving lessons in Nottingham and the surrounding area, and can be used before or in-between your training.

Gardening school is in session and Shirley is teaching the absolute basics, such as: what to wear, what tools to use, what is the difference between an annual, perennial, and biennial? What is a garden zone, and which one is yours? Class is in session, so spit out your gum and listen up. Time to learn Gardening 101.

In my first few articles, we focused on operating system hacks. These hacks have been primarily on older operating systems such as Windows XP, Windows Vista, and Windows Server 2003.

Until recently, brainwave-reading devices have pretty much only existed in science fiction. Sure, electroencephalography (EEG), the technology that powers these devices, has been used in medicine and psychiatry since the late 1800s, but diagnosing people's brains and reading their minds are two totally different things. The first EEG headsets available to the public were used mostly in gaming and even in fashion, but in the last few years, they've gotten a little more sophisticated.

As an adult you will come a cross a point in time when you need to make the right impression by writing a formal letter. Follow the format and you will be able to be most effective at conveying the information in your letter.

Water is an important resource and it needs preservation. Older toilets suck up way more water than necessary, causing both high water bills and pain for the environment. Follow this tutorial, and learn how turn your old toilet into a newer low-flow model.

Crossword puzzles are great way to exercise you mind and have something fun to do with breakfast. Don’t just do a puzzle, but make one yourself. You can do it by hand or try out the help of a crossword building software.

Everybody has a blood type. There are four types of blood in the ABO system: A, B, AB, and O. In this medical how-to video, learn how easy and important it is to find out what your blood type is. The procedure is very watch and find out.

Drummers have their choice of drum stick styles and grips and unless they know about them it is hard to know what is best for each. Learn about several of both from an expert drummer in this free video clip series.

There are entertaining card tricks performed by our expert that are easy to learn and fun for everyone. Learn the typical cup trick or the more complicated magic Mentalism Trick. Make sure you have the needed props for the rope trick or the floating ball trick.

In these swim lessons on video, learn some basic synchronized swimming techniques, including strokes, kicks, body jumps, sculls, figures and hybrids. Our expert Ymajahi Brooks swim instructor will walk you through all of the elements of a typical synchronized swimming routine, from the stretches and warm-ups, to tricks like an alligator scull or a split walkout.

In these instructional videos you’ll learn what to expect during typical Lomi Lomi massage session. Expert massage therapist Kelley Welch offers tips and advice on the benefits of Lomilomi treatment, where to find a qualified practitioner and how to prepare for your session. She also explains the philosophy of Lomi Lomi, the importance of breathing exercises and demonstrates massage techniques for different regions of the body.

There are a lot of things on your computer that can reveal information about you when you are surfing the Internet. If you are like me, then you will do anything to maintain your privacy and prevent those little leaks of information from happening. Here's a list of a few of the "threats" that can reveal information about you:

Update: this article is referring to the 1.9 pre-release beta version, which is now commonly referred to as 0.1.9, released in October of 2011.

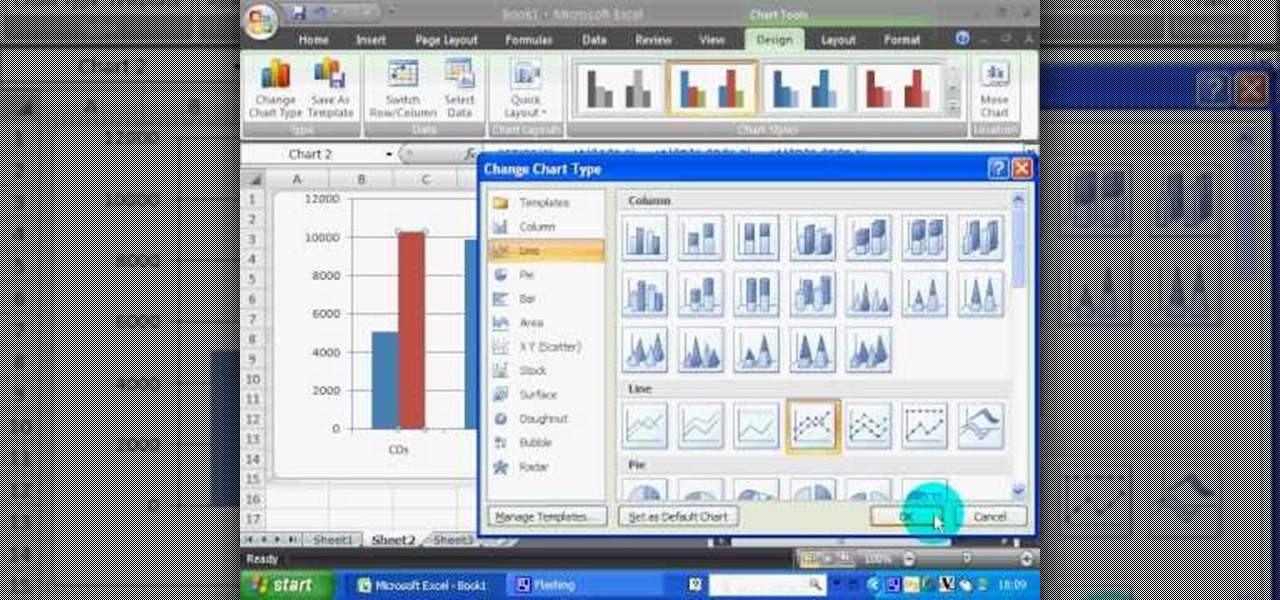
In this software video tutorial you will learn how to create a column line graph in Microsoft Excel 2007. First you type in the data in to the work sheet. Then highlight the data and click 'insert' on the menu bar. Here you select the 'column' option and go down and click on the type of column that you want. And the graph is automatically presented. Now click on 'move chart' and select a sheet where you want the graph to be moved to and click OK. To change any field in the chart in to a line ...

mIQ? What is it exactly? It's a handy web service that helps you manage your mobile life, with free and easy online access to all of the content and information stored on your mobile device. How does it work? Best Buy has answers. The Best Buy Mobile team explains how simple it is to use mIQ to backup all the data on your cell phone, including messages, photos and contacts.

Learn how to set up Internet on iPhone clones with this video. *First thing you need to do is to make an AT&T GPRS data account.

Check out this video to learn the fundamentals of woodsball, a mission or scenario oriented type of paint ball. Positions are meticulously explained to help in deciding which player type best suits an individual.

While Apple has included a vibration motor in the iPhone since the beginning, it's never let us use it for haptic feedback on its default keyboard — until now.

Apple's stock keyboard for iPhone has gone through many changes over the years. Some have been significant, and others more subtle. Overall, most of these updates have been fairly obvious, so you're probably already using them — but there are more than a few interesting features that were slipped in under the radar that you may not know about.

The average business person likely recognizes Epson for its printers or even its projectors, not the futuristic AR wearables.

The act of typing on a smartphone has come a long way since the days of tiny physical keys at the bottom of a BlackBerry, but there are still quirks that can make it frustrating. Luckily, if you know a few hidden tricks, things do get easier.