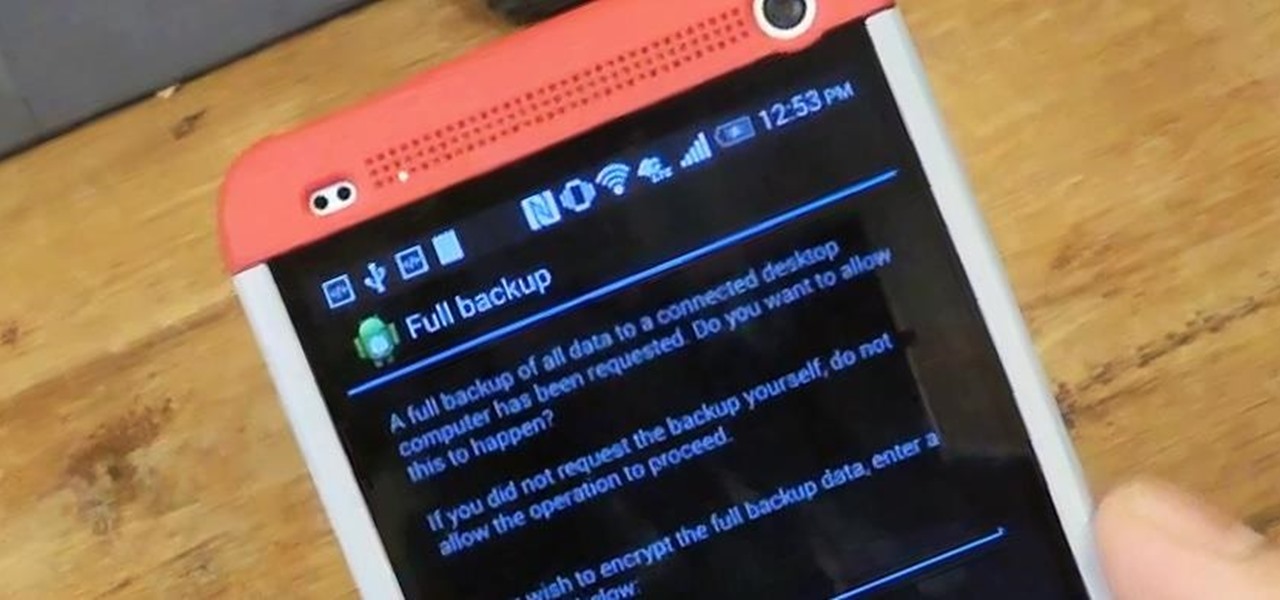
Today, I'm going show you how to back up all of your apps and their data using Android Debug Bridge (ADB)—an essential function for all softModders. These commands will be especially useful when you are updating your version of Android, since they don't require a third-party program to run on your device.

You've probably used Google to search for recipes, or to find out what the heck that mystery food on the ingredients list is. But with all its built-in features, there are plenty of other ways the search engine can help you out in the kitchen.

It's always the snack you're most looking forward to that ends up being moldy when you open the fridge to grab it. Always. That slice of leftover pizza or chunk of cheese you've been thinking about all day? We've all been there. What separates us is how we choose to deal with it. Personally, I toss anything that has even the slightest hint of mold, but not everyone errs on the side of caution. Some people don't mind the risk and just cut off the green or fuzzy parts and eat the rest.

Most recipes don't specify what type they mean when they call for onions. While using whatever kind you already have won't necessarily ruin a dish, using the best one for what you're cooking will definitely make your food taste better.

"Enter your email address. Confirm your email address." I absolutely hate seeing those two sentences when I'm signing up for something online, especially on my Samsung Galaxy S3. The less keyboard work I have to do on my mobile the better. Luckily, there is a way to enter your email address without having to type it all out, and I'm going to show you how it's done.

No matter how much of a gamer you are, typing with your PS4 controller is a bitch. Let's just be real. Having to move left, then right, then down, for every single letter can make writing a message very time consuming; so much so that I usually avoid messaging altogether.

Ways to Blocking a Website on a PC Open the “Control Panel” by click “My Computer” on your PC

Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun. Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to get a bit of revenge and keep him or her off your back!

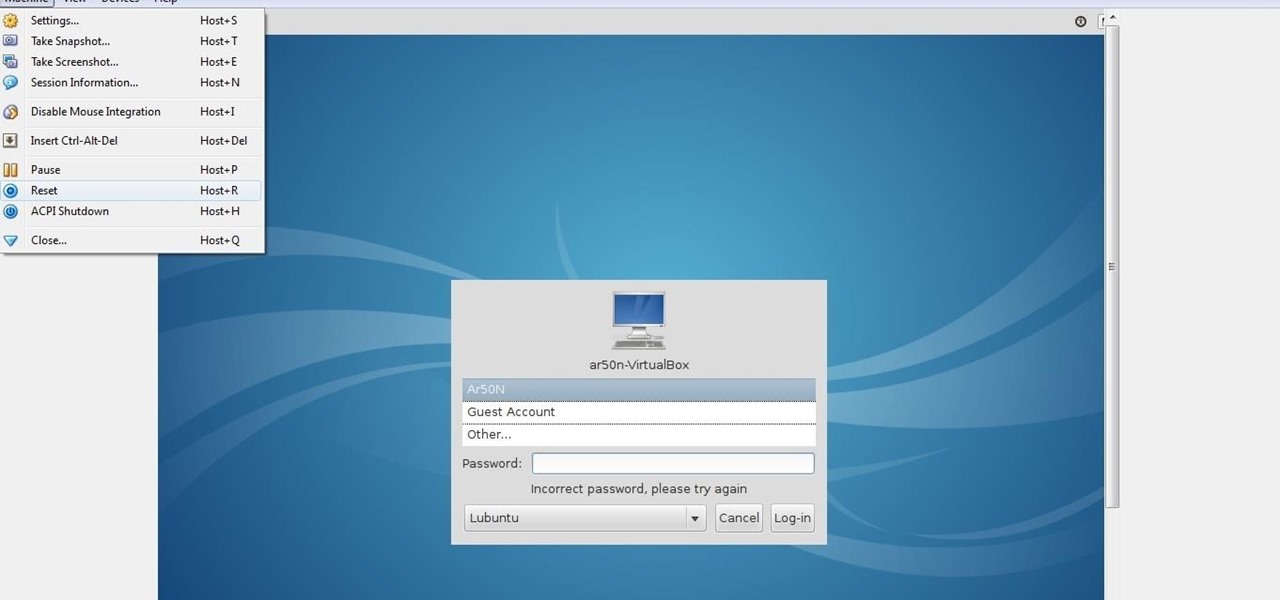
lubuntu is a is a lightweight Linux/Ubuntu that makes it suitable to virtual environments, that you run with VirtualBox to add a secondary machine to your computer or laptop. With this program you can run a number of operating systems upon the same platform.

Just because you wanted a stable, stock Android version on your HTC One doesn't mean you have to miss out on Sense because you bought or softModded to a Google Play Edition. As long as you have the Android SDK tools and you've unlocked your bootloader, you can turn your HTC One into the Developer Edition, a Sense version free of carrier bloat.

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

Previously, if you missed a call or text on your old Samsung Galaxy S3, there was a white LED notification to let you know. It's a nice feature that most smartphones have, but wouldn't it have be nice to know what kind of notification it was before picking up the phone?

Welcome back, my hacker wannabees! Most of my recent posts have addressed using Metasploit’s Meterpreter and what we can do once we have embedded it on the victim’s system. This includes remotely installing a keylogger, enabling the webcam, enabling the microphone and recording, disabling the antivirus software, among many other things. The list is almost unlimited.

Welcome back, my tenderfoot hackers! So many of you responded positively to my post about using the keylogger, as well as my post regarding turning on the webcam, that I decided that you might enjoy another similar hack. In this article, we will enable the audio recording capability on the remote system of your roommate.

This is a very fun and happy cat nail design that I wanted to show how to create through the following nail art video :

We've all had that awful, sinking feeling when something you've been typing away at is suddenly gone. Maybe you accidentally hit the Back button, lost your internet connection, or your computer crashed, but whatever the reason, losing your work totally sucks. A lot of word processing programs have a built-in auto-save feature to prevent you from losing everything, but most websites and blogs haven't gotten there yet. An extension for Chrome and Firefox called Lazarus: Form Recovery can help y...

This is a very cute and simple gradient or ombre sequinned nail art with hearts nail polish design that a did a few days back and just wanted to share with all you girls here.

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

Whether you're making a poster, drawing a logo or designing a website, the font you use can make a huge difference in any visual design, and the ones available in most word processors can get pretty boring. There are thousands of sites online where you can download free fonts, and even a few that let you design your own. Here are some of the best.

Bugle cords are used as elaborate ornamental leashes on bugles and trumpets, but they are also used as snazzy ornamentation, called aiguillettes (a type of fourragère), on uniforms worn by certain members of the military. While you could buy one pre-made, you could also make one yourself. But this should not be confused with the infantry blue cord of the U.S. Army, which is another type of fourragère only with more elaborate knotting.

Attention jewelry makers! When making your own unique jewelry designs, one must learn how to secure the end crimp beads with crimping or chain-nose pliers. Crimp beads can be used for finishing off your strung jewelry or as "stoppers". In this tutorial, learn how to hone your jewelry-making skills!

Excel is great, and if you're a Mac user, Excel 2008 for Mac has a lot of new and useful great features you can use to maximize efficiency in your spreadsheets. Excel doesn't have to be the boss anymore, you can! The Microsoft Office for Mac team shows you all the great features in this how-to video.

Excel 2008 for Mac makes it easy to create formulas for cells. You could always do it before, but now with the new Formula Builder feature, building formulas just got one step closer to simple. The Microsoft Office for Mac team shows you just how to build formulas by using the new Formula Builder in this how-to video.

There are plenty of options and shortcuts available on the iPhone, and one notable feature is the ability to copy, cut and paste text or images, just like you would on a normal computer. So how do you do it? Best Buy has answers. The Best Buy Mobile team explains how simple it is to cut, copy and paste text with your Apple iPhone.

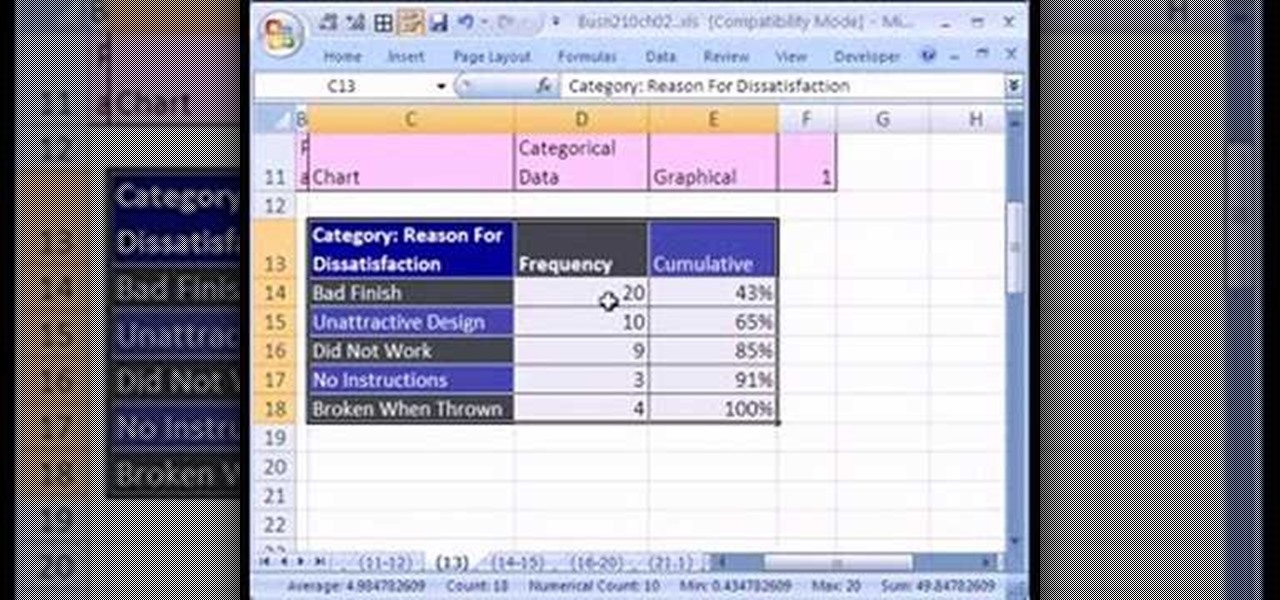
If you want to create a Pareto Chart for categorical data in MS Excel you should first have your data input into Excel already. From your data, you should highlight the cells that you want to count the frequency for and in the frequency box you should type in =COUNTIF and highlight the data you want the frequency for and put in F4 and then press , click on cell to the left and click enter. Now this will work all the way down. If you have not sorted it, you can right click and then click sort....

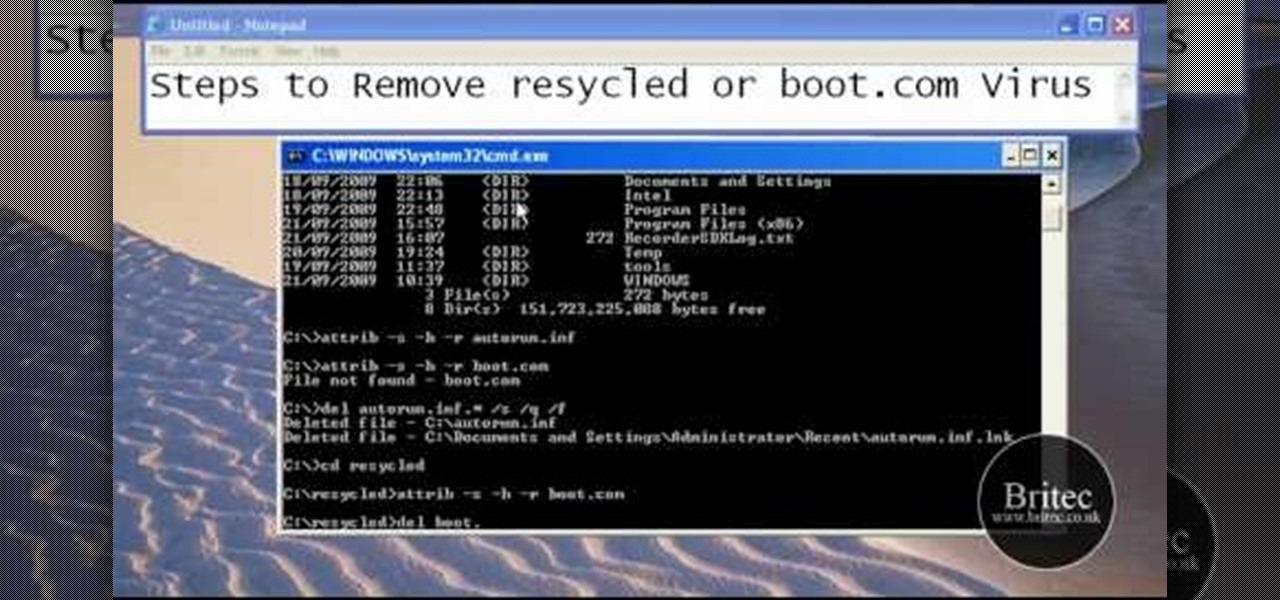
This tutorial describes the procedure to remove autorun.inf and boot.com virus. This virus is commonly called as resycled/boot.com virus, which could damage the system files and may steal important information from the system.This can be removed by any malware / spyware remover like Malewarebytes.

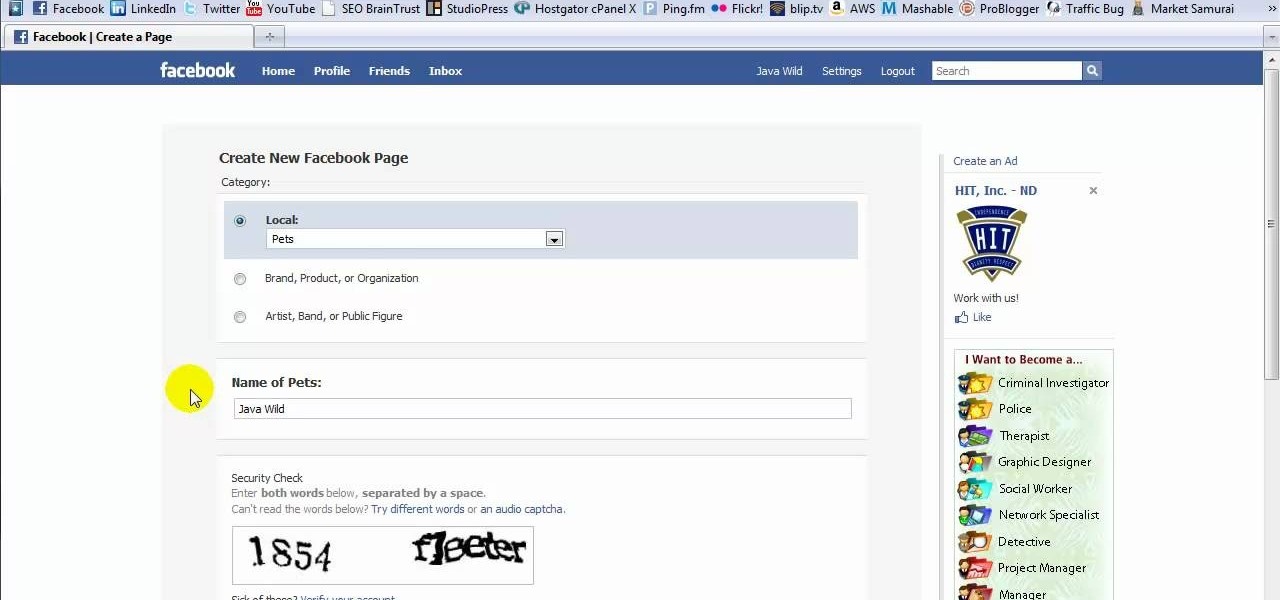
This tutorial is in response to mail to Facebook. Scott Wilde leads you through the process. You can start by creating a brand new profile page. In this case, Mr. Wilde created a profile page for his dog Java Wilde so he could have a fresh new page without having to alter his initial profile page. Fan pages are different than your base profile. Your base profile is not indexed, it is not public, it is private and limited to 5000 friends. A fan page is unlimited up to millions of fans and it c...

It was bound to happen with all those numbers floating around in your brain – you've forgotten your Windows password. Here's how to recover it.

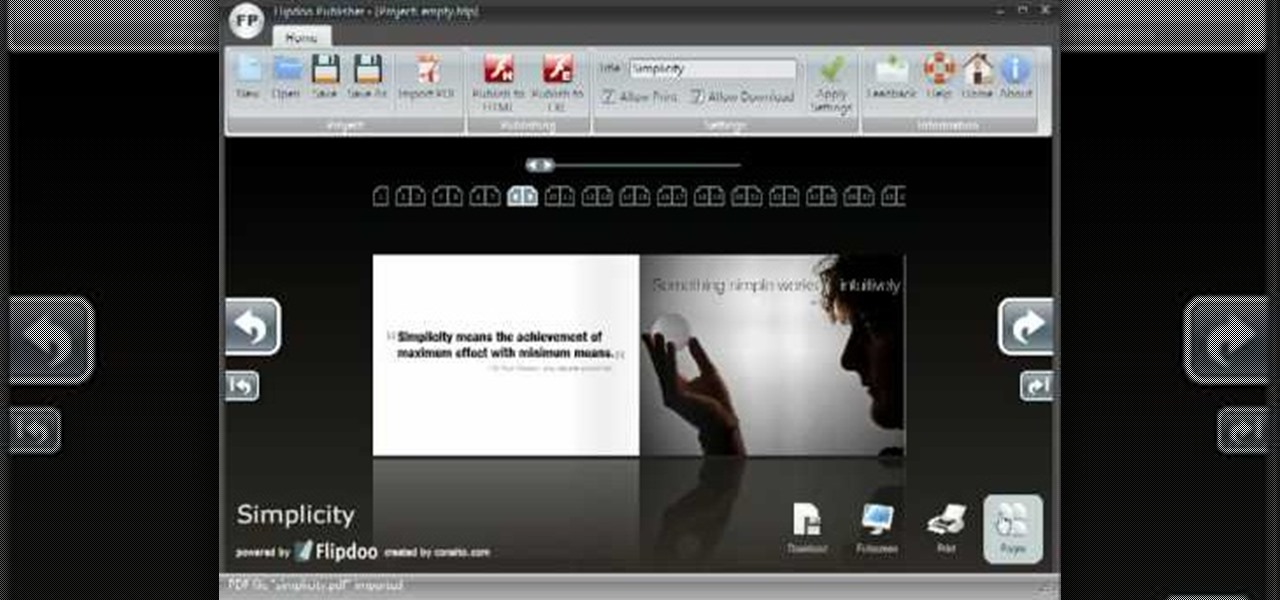
If you'd like to create a cool presentation with Flash, check out this video and the Flash plug-in flipdoo. Flipdoo allows you to build stunning flash flip books for both online and offline use in minutes. You don't need any additional software. Import your PDFs, configure book look & feel and publish. This is the best way to create digital ( electronic ) editions such as any type of publications, magazines, brochures and catalogues. Flipdoo Publisher is a Windows desktop application that hel...

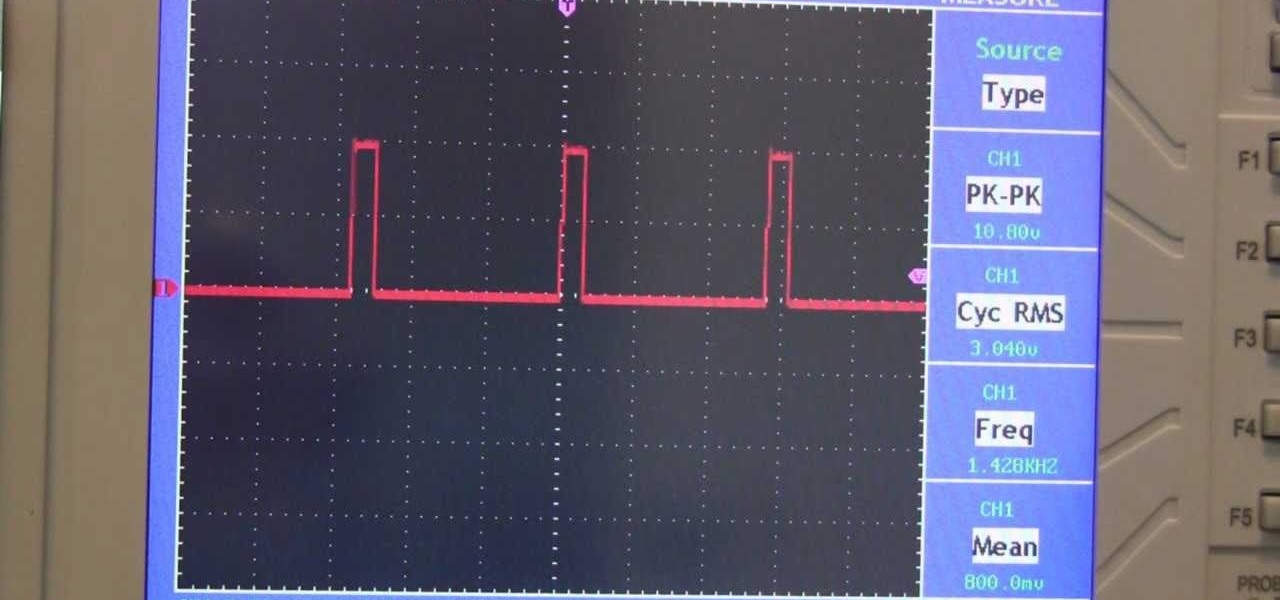
Many types of circuits are useless and less useful if you cannot control the amount of power going through them. For that, you need a PWN (pulse with modulation) switch. This electronic component will let your control the power going through the circuit, enabling you to dim LED lights, control the speed of a motor, and other useful tasks. This video will teach you all PWN switches and how tom make your own.

The top-down twin-stick shooter has become a fixture of low-budget gaming since Geometry Wars showed the world what the genre could be. LittleBigPlanet 2 contains all the tools to make one, as it does with most types of games, and this three-part video series will take you step-by-step through the creation process for an awesome zombie TDTSS (top-down twin-stick shooter).

The side-scrolling space shooter (Think R-Type) is one of the oldest and most basic of video game genres, which makes it a great place to start for novice game designers. This video will show you how to make such a game, called "Schnoopter", in Unity3D, an excellent free online game design engine. If you've never used Unity before, you should watch this series for a guide to the absolute basics.

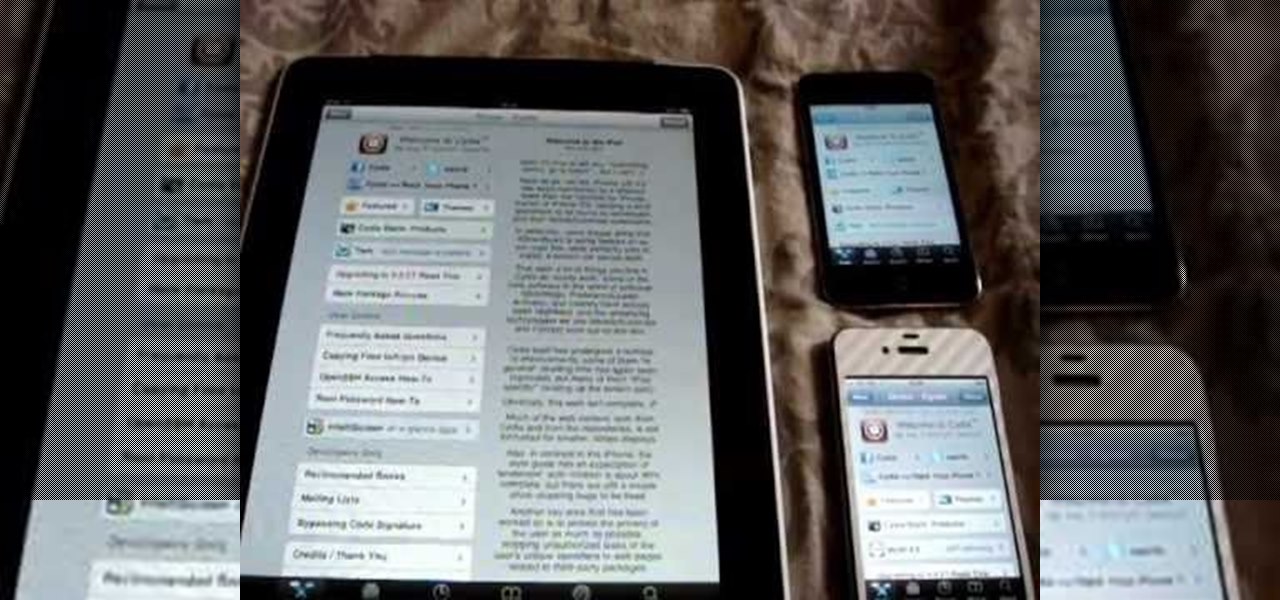
If your iPad, iPhone 4 or iPod Touch is already on a tethered jailbreak, this is the tutorial on the new Redsn0w release for all you experienced users. An untethered jailbreak is a type of jailbreak where the device does not require rebooting with a connection to an external jailbreak tool to power up the iDevice. Jailbreaking allows users to get root access to the command line of the operating system, to download otherwise unaccessible extensions and themes, or install non-Apple operating sy...

Kundan flowers are made from kundan gems, which are a type of Indian gem with very vibrant, jewel-like tones. Kundan flowers, then, can be made as exotic and brilliant decorations for your tabletop or even to adorn fanciful cakes.

Need a few cool moves to show off the next time you're trying to impress the ladies at a club? Then check out this helpful video to learn a sequence of tutting moves (a type of street dance that emphasizes right angles) and popping.

One way to improve your arm strength and work out your bicep muscles is with curl exercises. All you need are some dumbbells and some time. This video shows you an alternative curl routine called the side curl, which is a type of concentration curl. It begins at the side, then you curl the weights in toward your chest.