Cats give us so much—companionship, loyalty, love... and now the bird flu. Several weeks ago, a veterinarian from the Animal Care Centers of New York City's Manhattan shelter caught H7N2 from a sick cat. According to a press release from the NYC Health Department on December 22, "The illness was mild, short-lived, and has resolved." This isn't the first time cats have passed infections on to humans, but it is the first time they passed on the bird flu—avian flu H7N2, to be exact.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

I've been a fan of potatoes ever since I can remember... but mainly because they weren't a big part of my daily diet (which usually consisted of rice). And because my experience with potatoes was so limited, I only knew of two varieties growing up: big, brown Russets and sinewy sweet potatoes. As for cooking with potatoes—well, I'm embarrassed to admit that the only time I cooked potatoes when I was a kid was with the instant kind.

Welcome back, reader! In this tutorial, we will be covering our first program! So let's get to it. We all know the unspoken tradition of the first program when learning a language and of course, here we will respect and complete it. Fire up your favorite text editor (be it vim, emacs, gedit, it's all the same to me, no h8) and try to keep up.
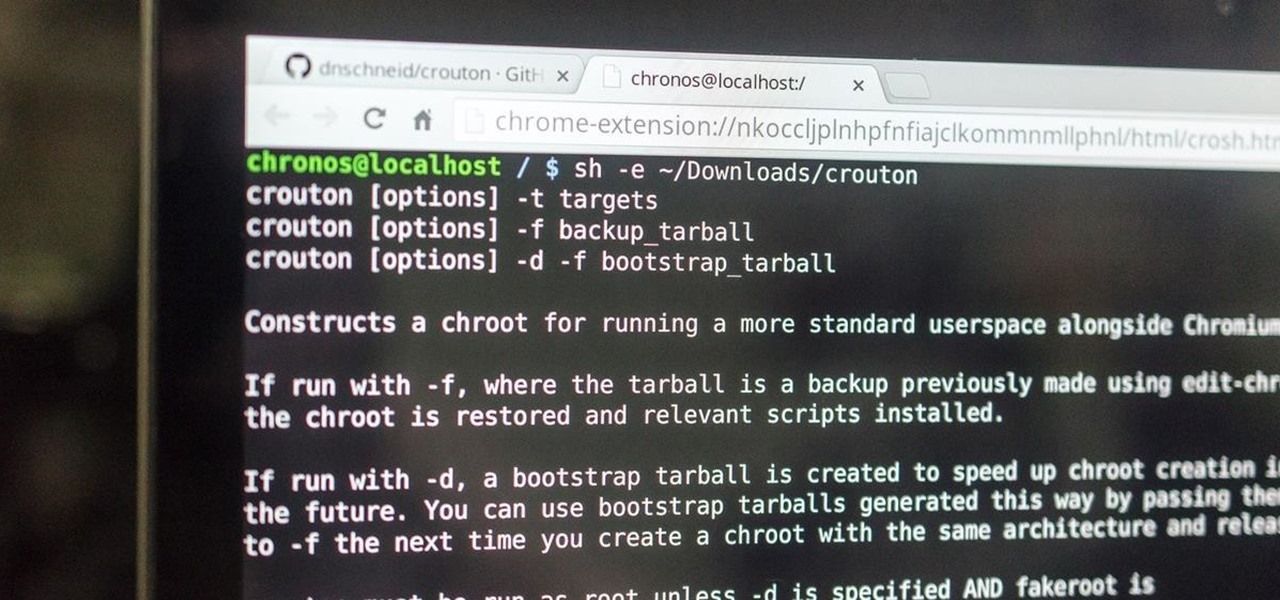
This is my first how-to for this site so feel free to let me know if I can somehow improve! Inspired by the great Jailbroken iDevice and Rooted Android PenTesting tutorials I decided to share how I use my Toshiba Chromebook 2 with Kali Sana.

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

Welcome back, my tenderfoot hackers! A number of you have written me telling me how much you enjoy the Mr. Robot series on USA Network. I am also a huge fan! If you haven't seen it yet, you should. It may be the best show on TV right now.

A video tutorial on how to do a four strand braid. Use this braid to make hemp necklaces, bracelets, anklets, and other types of jewelry.

A step by step video tutorial on how to tie a continuous half hitch spiral knot. You can use this knot to make various types of hemp macramé jewelry such as necklaces, bracelets, chokers, and anklets.

A video tutorial that shows how to tie a half square knot AKA spiral knot. You can use this knot to make various types of hemp jewelry.

Hi, dear co-apprentices and wise masters. I've been recently trying to learn the basics to hacking here, and I've read all guides on Wi-Fi hacking and noticed no word is dedicated to this awesome script that comes bundled with Kali!

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

If you struggle with deciding which wine you should buy for an intimate dinner, or the type of beer with the highest alcohol content that doesn't taste like tree bark, then check out some of these great alcohol-friendly apps to make better booze decisions.

This video shows the two types of necklaces. First one is in Egyptian style and the second one is in Christmas colors :) You can use your own colors if you wish..

Welcome back, my tenderfoot hackers! As you know, Metasploit is an exploitation framework that every hacker should be knowledgeable of and skilled at. It is one of my favorite hacking tools available.

This video will show you how to create a Twitter list for similar interest twits together. But if you want that twit from a special type of following or users will be bundled together then you have to create a list. You can isolate you favorite or useful twits from all twits coming by creating list in twitter. So please watch the video.

This pattern may look complicated, but here I used only the Square knot :) Pattern looks like the stars or birds in the sky. You can use this pattern for different types of goals, for example: clothing accessories, Handbags, purses, cases, wallets etc..

This video will show you how to set finger print scanner for phone unlocking in Samsung galaxy S5. The finger scanner option allows you to register your finger print for unlocking your phone. This method of unlocking your phone saves your time over typing password. This way no one can open your phone except you. Watch the video and employ the tricks in your Smartphone.

This video will show you how to change downloading location from Google Chrome. If you download a special type of file often then you have to visit default downloading folder and move them to your preferred location. But you could set the downloading location to your preferred folder from chrome. Watch the video and follow all the steps carefully.

As the title says, you'll learn how to set up a prank that will end up with your victims having eggs on their faces.

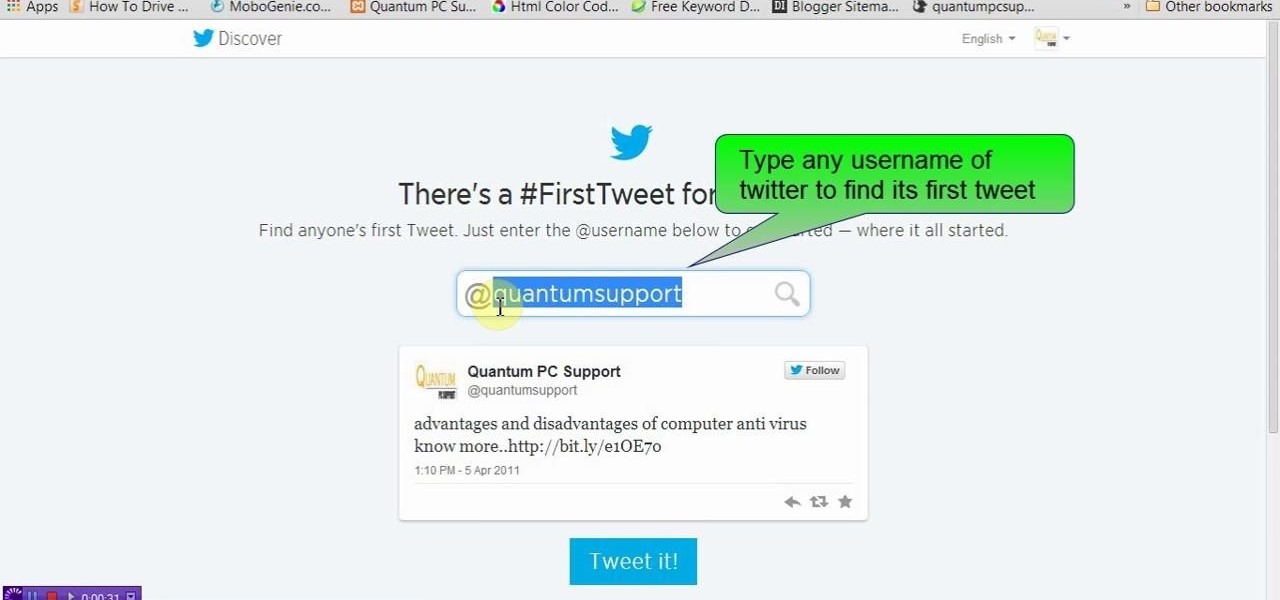
This video will show you how to see first twit of any user in twitter. You could type https://www.first-tweets.com in address bar and the site will be redirected to another place https://www.discover.twitter.com/first -tweet page. You have to enter the user name and twitter will fetch the first twit of that user. Watch the video and employ it yourself.

This is a video of how to use a can opener that's a safe can opener, which will not leave sharp edges. You can also reuse the lid to put back on top of the can if all of it's contents are not used.

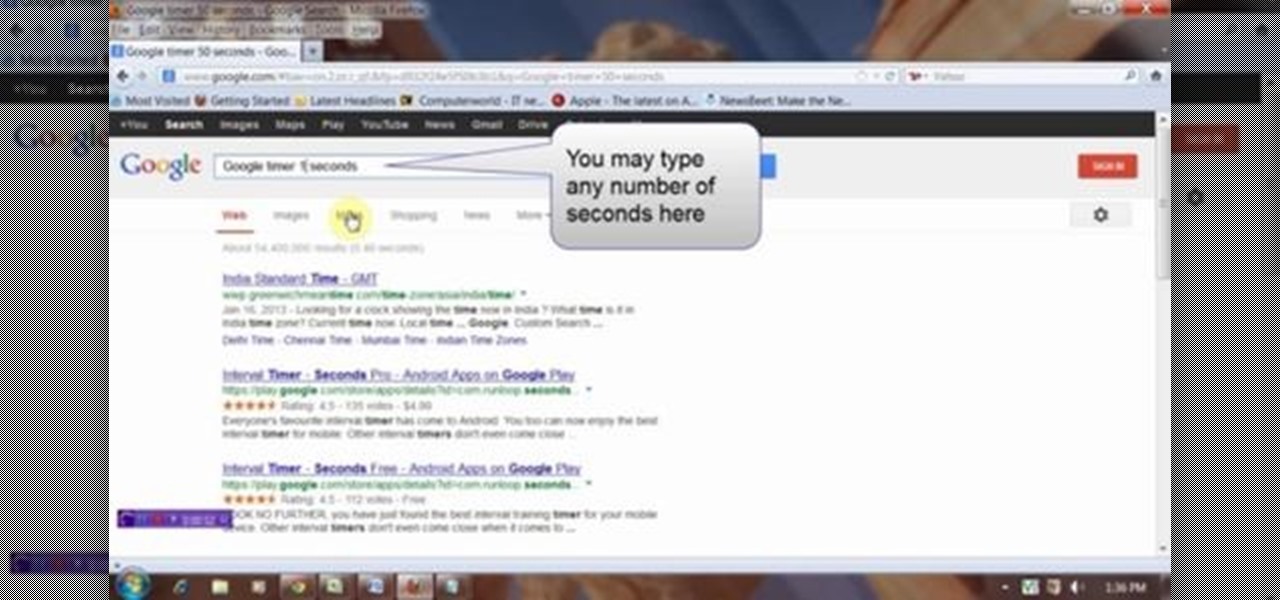
This video will describe you how to set Google online timer. Now you don't have to bother about the timer or stopwatch. You can bring a timer in your Google.com home page. You have to type a command "Google timer 50 seconds" and a timer will start automatically. You can stop and reset the timer whenever you want. Watch the video and employ it yourself.

This video tutorial shows How to make a Macrame Lizard, Nice accessory for the summer season! You can use this Lizard for different types of goals, for example: keyring, keychain, pendant for necklace, earrings, decor and accessory..

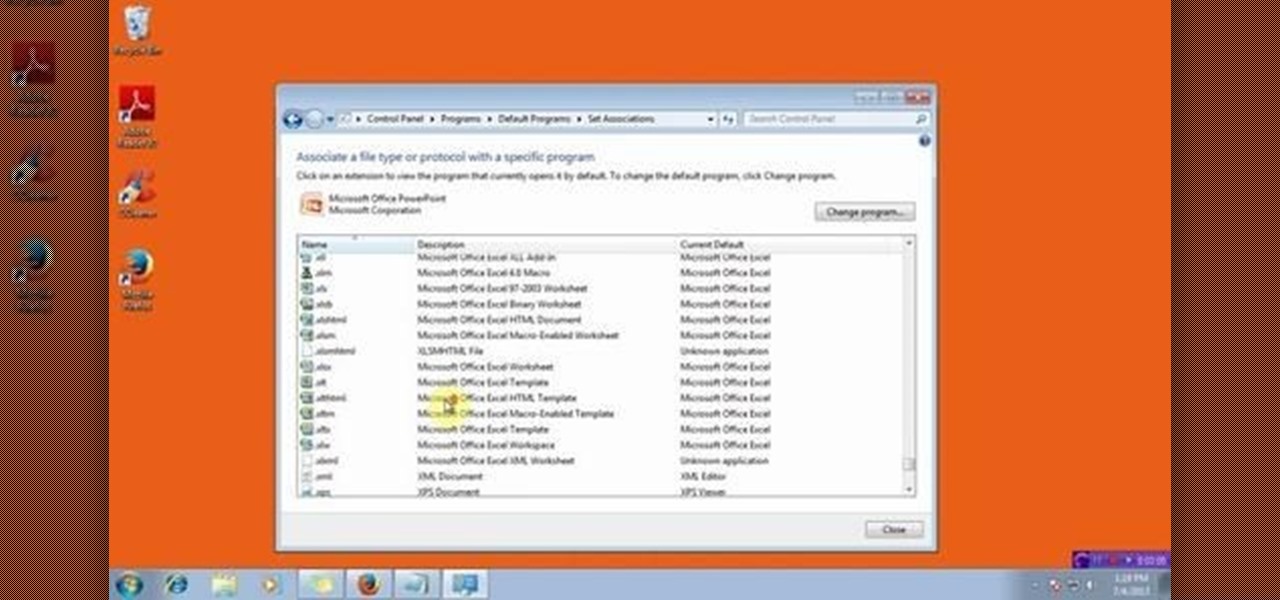
This video will show you how to change the default program for a Specific File Extension in Windows 7.

You can use this beautiful macrame pattern for different types of goals, for example: Handbags, cosmetic bags, clothing accessories, purses, cases, wallets, bracelets, etc..

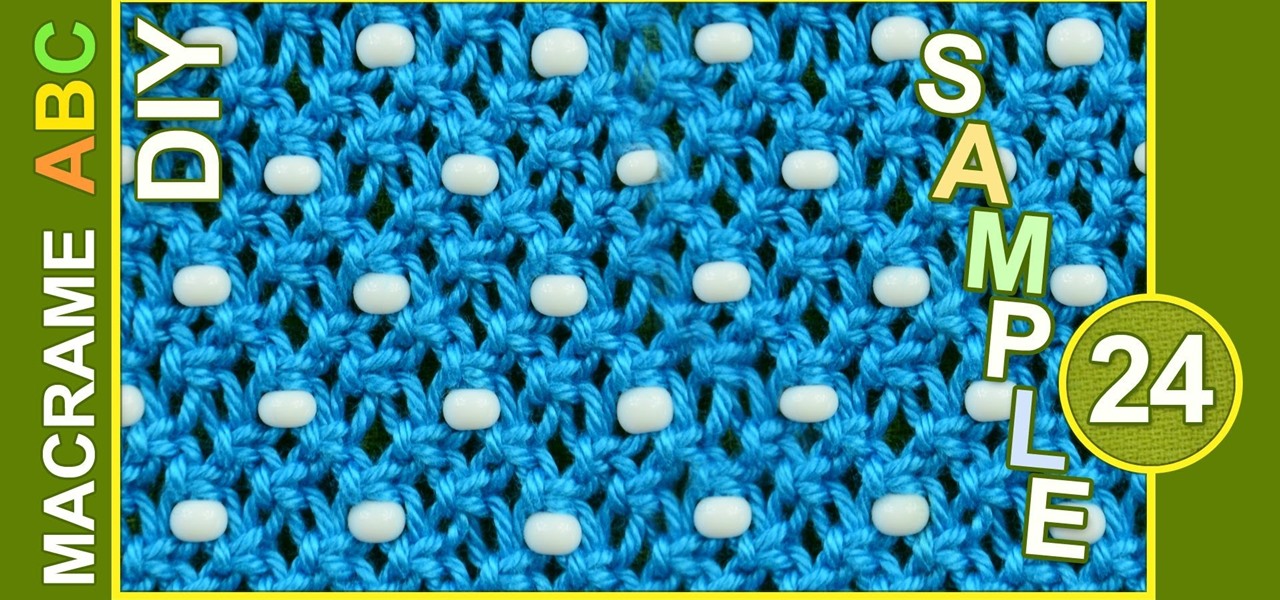
Easy Macrame pattern with beads. You only need to know Square knot and you can use this pattern for different types of goals, for example: clothing accessories, Handbags, purses, cases, wallets etc..

As softModders, the first thing we do after updating to the newest version of Android is to root, install a custom recovery, and install a superuser app. By doing this you open up your HTC One to a vast quantity of new apps and tweaks you can use to truly make your phone One of a kind.

You can use this pattern for different types of goals, for example: Clothing, handbags, tablecloths, coasters etc ...

Today we show you how to make horns for a costume. We specifically made horns for Maleficent, but you can shape and paint yours to like any type of thing.

Friendship Bracelet Tutorial for Beginners - Rag Rug, Easy Pattern One type - different bracelets - 3 samples...

This pattern with flower motifs looks very good! Maybe this tutorial is not for beginners, but you can use it for different types of goals, for example: Bags and Handbags, purses, tablecloths, coasters, clothing, wallets, phone bags and phone cases etc..

This is a tutorial how to make an easy ZigZag Macrame bracelet. You can use it as a friendship bracelet. Before you start you should know the basic macrame knots. There are 2 types of knots, the double half hitch and the reverse double half hitch. These knots are very easy to make. Don't worry and let's go make these Zigzagging waves :)

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.

This is for those people that want to create a fire in a camping situation, survival situation, flare type alert to other that you are lost, or simply for entertainment.

Henry shows you how to install a 3 tab asphalt shingle roof in this video. This video covers everything from the type of roofing felt to use, making the starter strips, layout with chalk lines right through to making and installing the ridge caps.

Depending on where you live, the type of skirting option you choose is important (Skirting is the base trim around the shed). Henry shows you three different ways to do this including the Drip Cap options for wetter climates.

Oysters are a bit of an acquired taste, you really need to try a few times to really begin appreciating them. Then once you get into it, you realise there are so many different types that you need to get to know them one by one.