The US driverless market has become a competitive – and crowded – arena, with big names like Google, Apple, Uber, and even Intel intent on leading the pack. Not to be outdone, the EU is also getting in on the automated car action with self-driving fleets launching in both the UK and the Netherlands within the next two years.
Usually, we think of vaccines as preventative, a shot we get to prevent the flu or some childhood disease like measles or mumps. But there are vaccines for other purposes, such as the ones studied by researchers from the Netherlands.

It's 2017 and finally ordering "fries with that" at McDonald's is an even easier prospect for all you lovers out there ball and chained to the fast food game. The great big golden arches are moving one step closer to making your order as golden as it ought to be through a mobile ordering app using geofencing technology to track your location.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

Most of us equate feeling cold with catching a virus—but we've also heard plenty of debunkers proselytizing that being cold isn't what gives you the flu.

With the Game Developers Conference (GDC) in San Fransisco just a few weeks away, Microsoft Senior Program Manager Vlad Kolesnikov has announced via Channel9 (Microsoft's developer news outlet) that not only will new low-cost virtual reality headsets be coming in March to developers, but that they will be at GDC, too.

In addition to trying to give Pokémon a life on the HoloLens, Sky Zhou, a founding member of mixed reality studio Matrix Inception, won Microsoft's Actiongram Fantasy Contest Quest last month for his video concept on slaying dragons. But fantastical creatures aren't the only thing Sky can whip up on the HoloLens.

If you just can't wait to see the Pixel and Pixel XL, the new Google-branded smartphones expected to be announced tomorrow, you're in luck. After weeks of rumors and blurry images, a smartphone sales company called Carphone Warehouse just accidentally dropped the entire ball. The UK business accidentally set the product pages for the Pixel and Pixel XL live a couple days early, and for just long enough for them to be archived before they were taken down.

Traditional root ad-blockers like AdAway and AdBlock Plus have no effect on YouTube anymore. Until now, if you wanted to get rid of the commercials that play before your favorite videos, there have only been two ways—either by paying for a YouTube Red subscription, or by using an Xposed module to modify the YouTube app itself and force it into not showing ads.

Finding Pokémon in the wild isn't the only way to add to your collection in Pokémon GO—you're also able to hatch your own from eggs that you've gotten from PokéStops.

We used to saunter into the grocery store and gaze longingly at the pre-made roasted chickens, wistfully thinking of things we could do with the golden fowl if only we didn't already have dinner plans.

You're only as smart as your communication skills allow you to be, as other people will simply never know your inner genius if you can't effectively express yourself. Regardless of the medium—be it a Facebook post or even a simple text message—this fact remains true.
Hi, I am Robel, I am here to let you know about how to hack windows admin password with out Sam files, this requires physical access and any boot operating system...I used Kali 1.8 , if it doesn't work make sure you have shuted it down properlyor use backtrack.

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

This article is to all the newbies on here wanting to become a hacker. Since I have seen many newbie questions on here, I need to address this.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

Hello, my fellow hackers. My name is cl0ck. I am a senior majoring in Computer Engineering with an emphasis is Security. I have been lurking the site for a while now reading and learning from the great minds that reside here. I, too, have some knowledge that I would like to share with all of you. This post actually comes from a personal problem I faced and had to find a solution for. Without further ado, here it is:

Do you have a file (or many files) that, in the wrong hands, may cause you trouble? Don't worry about it, because I'll show you how to wipe it (or them) from your computer in order to leave no trace behind.

!!!WARNING!!! !!!Because of misleading informations please wait for the new post about this same argument instead of reading this post!!!

Whether you choose the sassy face of someone like your inner Disgust from Inside Out, or you're the happy-go-lucky Joy, chances are you're well-versed in expressing your inner "ew." So for this Halloween, take pride in your judgmental self by donning a DIY Disgust mask.

In the second part of this tutorial, we are going to crack the hashes that we've captured previously. I'm going to explain how to do it with the powerful John the Ripper. It comes with Kali by default, so no need to install!

Taking care of your car requires effort, whether you take it to the pros for washes, waxes, and detailing, or you spend time to make it shine yourself—and it often seems that, right after your car is sparkling again, rain or midnight moisture appears to cover its surface in water spots. With a small tweak to your typical car care routine, you may be able to keep your car's surface and windows shining longer and better: you just need to add a little hair conditioning liquid.

Security researcher Samy Kamkar, best known for his MySpace Worm, and most recently for his online calculator that can help you crack any Master Lock combination, is at it again. This time he's figured out how to break into security doors that have a motion-sensing egress system.

The next time you're out camping, whether it's outdoors in the wilderness or right outside in your own backyard, try this hack out for an effortless campfire all night long. While there is definitely some prep work involved, it's well worth it if you don't need a huge bonfire, and more so if you plan on cooking meals over the flames.

Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.

Saying that I was obsessed with Pokémon as a child would be a serious understatement, and even though I'm not the Pokémon fanatic I once was doesn't mean I don't love playing still. However, I do often find myself dumbfounded by all of the new features and characters in each generation.

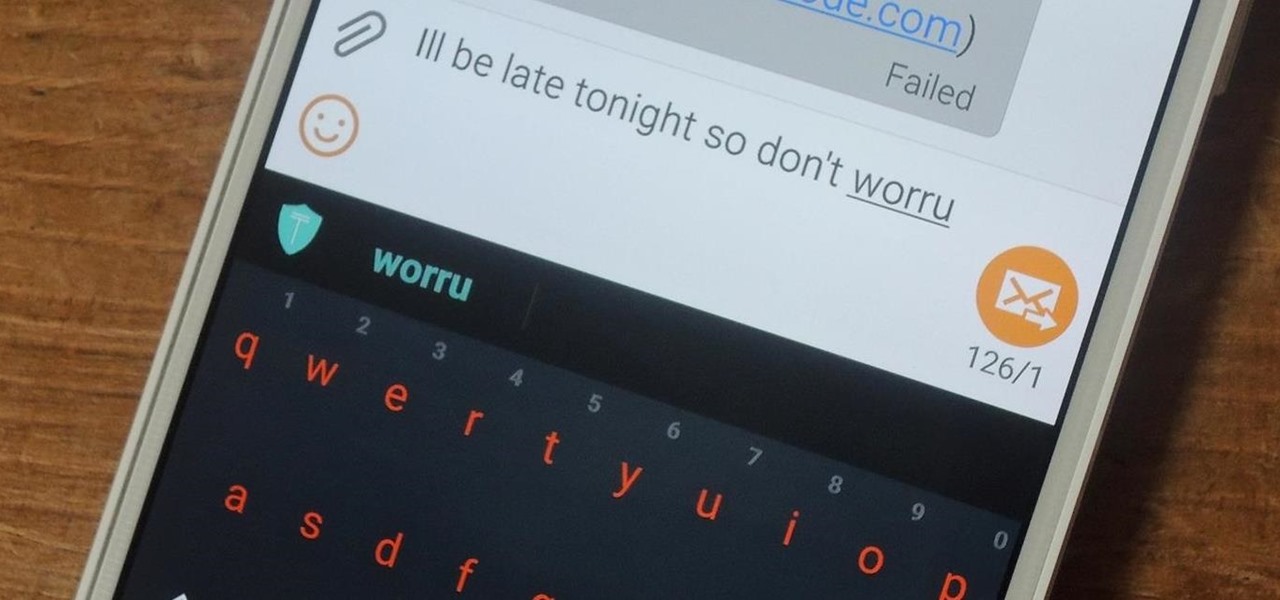
My reliance on autocorrect has made me a horrible speller. I take it for granted that it'll catch all my mistakes, but it only ends up making matters worse (especially when it inadvertently makes correct words wrong). So instead of relying on autocorrect to fix typos, why not try to completely prevent mistakes from happening in the first place?

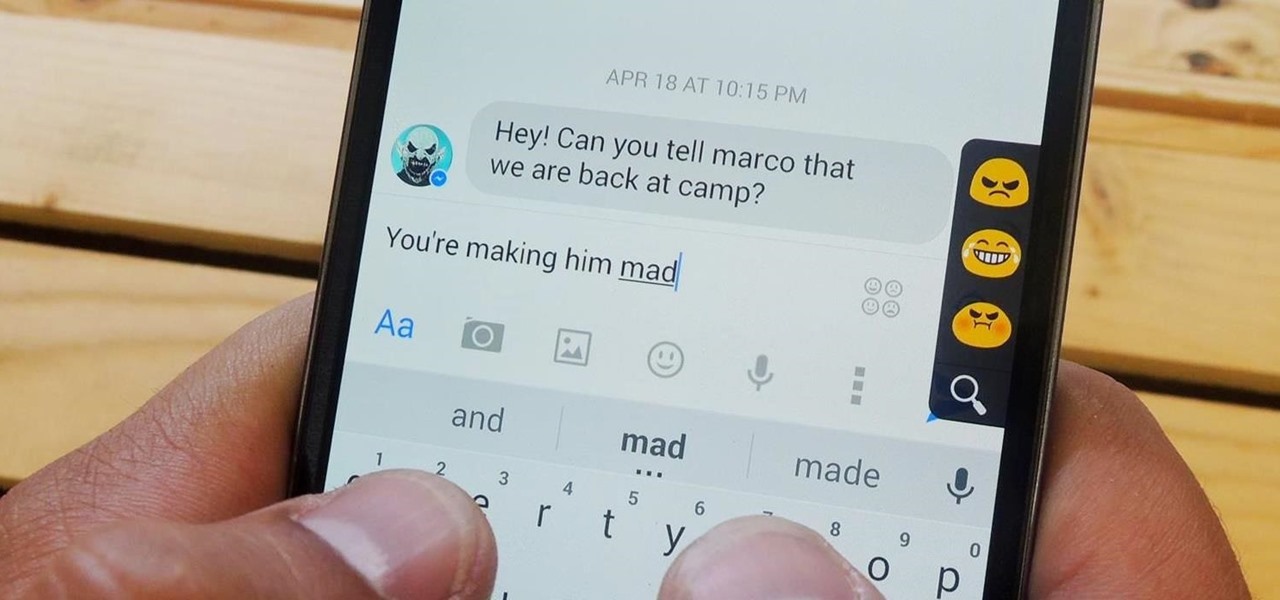
Some third-party keyboards, like SwiftKey for example, include a convenient feature that suggests emojis as your type based on the content of what you're saying. Unfortunately, many keyboards, including most stock ones, don't include this function.

OTW's great Tutorial Hack Like a Pro: How to Save the World from Nuclear Annihilation gives me the inspiration to try this on Win7 sp1.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Today marked the official unveiling of the HTC One M9 at Mobile World Congress in Barcelona. The newest HTC flagship will be released by the middle of March globally, and come in gold, gunmetal, pink, and silver. And if you were wondering, yes all of the leaks were pretty much spot on.

Step 1: Introduction: Hello! Hackers

You don't need a study to tell you how beneficial music is to helping you fall asleep. Most of you probably have your soothing playlist and SleepPhones queued up and ready to go before you get into bed and count those Zs.

Many Nexus 6 owners, myself included, have already started to experience the dreaded burn-in issues that often come with AMOLED display technology. These displays are different than your typical LCD screen in that each pixel emits its own light instead of using a backlight, so this leaves AMOLED screens more susceptible to issues with dim or unresponsive pixels.

Our workdays are typically filled with one thought: get as much completed as possible. Whether you face an inbox filled with tasks or just a project or two, both our bosses and our inner workhorses encourage us to knock out as many tasks as we can each day. But is being super-productive the best course of action for our minds and our employers?

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

Creativity and well thought-out planning are qualities to be admired when choosing a costume for Halloween. Going out in hordes to purchase the same 'ol outfits from a local costume warehouse means you're probably wearing the same thing as thousands of other people.

Welcome back, my hacker novitiates! Every so often, a MAJOR vulnerability appears that makes millions of systems vulnerable to attack. The most recent, named Shellshock, basically leaves every Mac OS X, Linux, and UNIX system on the planet vulnerable. As nearly two-thirds of all web servers on planet Earth run one of these operating systems (primarily Linux), that's a whole lot of systems out there waiting to be harvested.

There really isn't any custom manufacturer skin, like Sense, that can match the clean look and fluidity that comes with stock Android. HTC knows this, and they, just like Samsung, include a Google Play Edition version in their flagship lineup.