Welcome to my very first tutorial ever. Today I will be teaching you how you can use Arachni to scan vulnerabilities of web applications. I welcome all criticism good or bad as a teaching method for myself.

When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Welcome back! In our last training session, we covered some advanced list topics. We'll be going deeper into the advanced list rabbit hole today with lambda and lambda operators! (And I'm not talking about Gordan Freeman)
In the wake of Apple Music making its debut on Android devices, Google has finally released its highly anticipated YouTube Music app. With these two tech heavyweights throwing their hats into the ring, the streaming music world is about to get rocked.

It might be difficult to admit, but a lot of us are probably guilty of lurking on Instagram profiles, whether it be an ex you've been keeping tabs on or someone cute you literally just met.

In this article, we will explore the basics of radare2, a powerful package that comes with Kali. We are going to write a simple program, and then disassemble it, to see what is really doing in the processor.

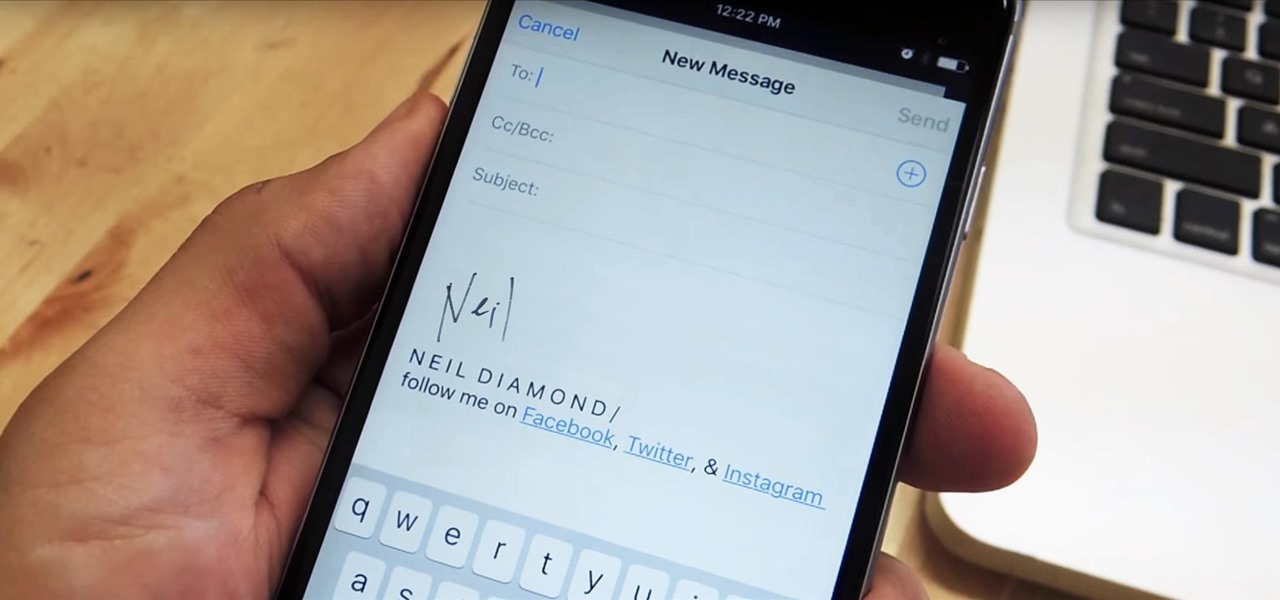
Emails sent from an iPhone, by default, are signed "Sent from my iPhone," which almost seems like a disclaimer in case the email has spelling or formatting errors. If your goal is to look professional while corresponding with coworkers or potential employers, then you're better off removing the signature completely and just typing your name out.

If you couldn't wait to test drive iOS 9 before its official release this fall, you probably have the beta software on your iPhone right now. However, if you're not a fan of all the bugs and glitches that accompanies it, it's not too late—you can still downgrade back to the latest version of iOS 8.

The options for finding random or specific music to listen to are vast. Spotify is excellent for streaming popular music and new releases, while SoundCloud provides a healthy dose of user-generated remixes and originals. And then there's YouTube for everything else.

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"

Using breadcrumbs in the kitchen is the perfect way to add crisp and crunch to the usual salad, entrée, or dessert. As chef and media personality Mario Batali once said, "There's almost nothing I wouldn't put homemade breadcrumbs on."

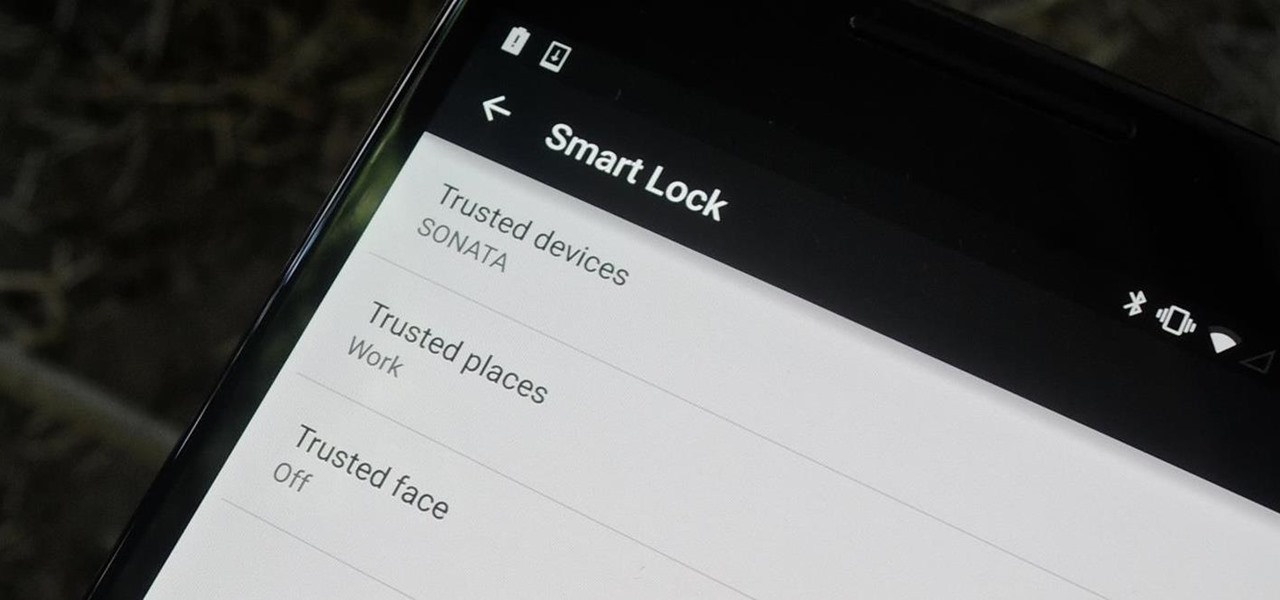
Keeping expensive mobile devices safe and secure is a priority for most of us, but the process of repeatedly unlocking a phone or tablet can seem like a pointless task. This leads to disabling the lock screen altogether, especially when in a safe place (e.g., home, office, car, etc.).

We all fall sleep in different ways. Some may require absolute silence, others need white noise, and some enjoy listening to a song or two to help bring on the sleep. If you're in the latter group, like I am, there's a problem. Fall asleep before the music stops, and a loud song may jolt you awake in the middle of the night. With an iPhone, however, that issue can be avoided with a little setup.

Today, I want to share a tutorial on one of the most useful but old methods which you could use to hack websites, that is using the Dot net nuke (DNN) vulnerability . I know some of you already know about this method.

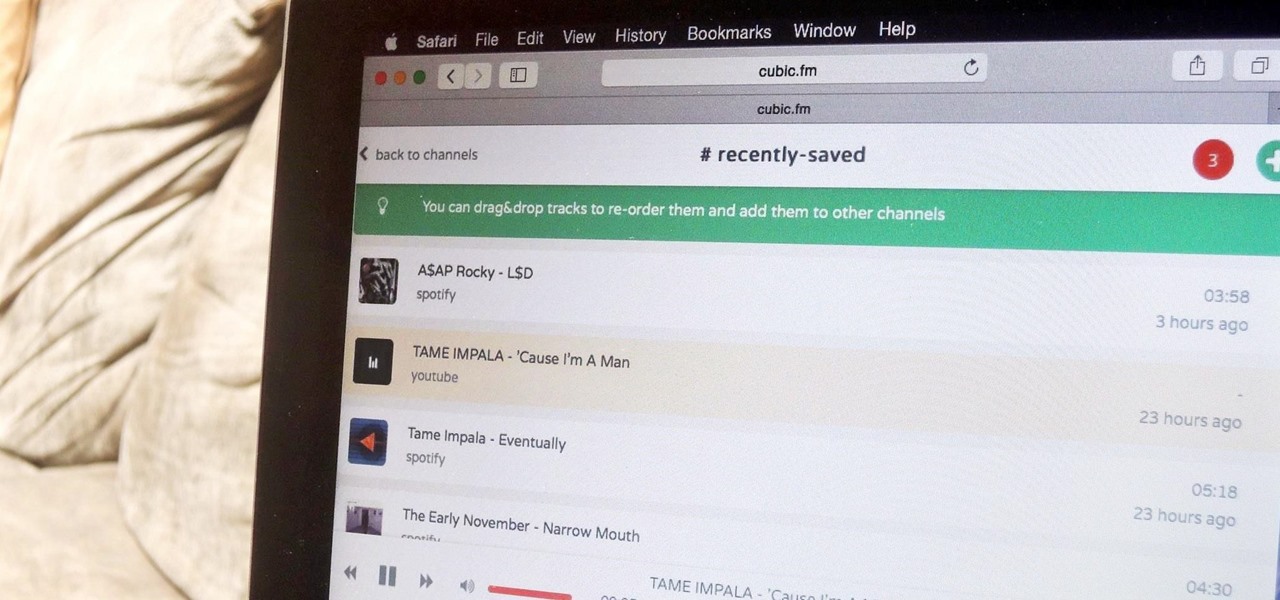
When streaming services like Spotify or Pandora compete for customers, the main differentiating factor is the size of their libraries. While these and comparable services usually run somewhere around $10 per month, a completely free alternative may actually have the most expansive library out there.

When Google Play Music launched a few years ago, I ditched iTunes and began using the service as my one and only source for listening to my personal music library. While All Access is great, I still prefer the radio feature on Spotify, so I still use that to discover new music.

As far as wallets go, mine is as full as they come; think something like George Castanza's overstuffed wallet on Seinfeld. I've got receipts, pictures, and tickets jammed inside, but what takes up the bulk of the space are all of the cards—credit, debit, gift, rewards, customer loyalty... I've got pretty much any card you can think of squeezed in. While it is a strain on my rear end, there's nothing I can do besides keep some of the cards elsewhere. However, looking for them when I need them ...

Are you a follower or a leader? No matter how you respond, we all know that leader is a more desirable position to hold. Great leaders typically share a few qualities—confidence, intelligence, and strength, to name a few—but one of the most intriguing is their appearance. With the right facial structure, and some well-rehearsed expressions, you can trick others into thinking you're leader material.

Finding the motivation to make a change can be tricky. It's difficult to resist the urge to procrastinate, or even give up when goals seem distant and difficult. If you wish you could stick to your New Year's resolutions, or maybe even just commit to pursuing smaller goals, you might want to consider making a small change to start: just create a new password.

Whether you choose to hang an authentic or artificial pine Christmas wreath on your door — or an entirely different type, like ones made of paper waste or even food — chances are you've spent a year or two struggling with how to keep your decor hanging. With one easy to apply, quick to remove trick, you can skip the shiny wreath holder and any further damage to your front door.

Our workdays are typically filled with one thought: get as much completed as possible. Whether you face an inbox filled with tasks or just a project or two, both our bosses and our inner workhorses encourage us to knock out as many tasks as we can each day. But is being super-productive the best course of action for our minds and our employers?

Holidays are a time for good food and good drink, but more often than not, we substitute good drink for, well, cheap drink. However, cheap wine doesn't have to be bad.

While CNN, FOX News, and MSNBC are valuable sources of information for what's going on in the world today, they may not be the best news stations to watch if you actually want to learn something. They, along with local news stations, are great at grabbing your attention, but if you truly want to learn something about recent events, you're tuning into the wrong channel.

Investing is like exercise—we all know we should be doing more of it, but we often just can't find the time. I mean, really, who's got the hours, inclination, and skill to pour through volumes of data and put together a balanced yet sophisticated portfolio of investment vehicles tailored specifically to optimize their returns while mitigating potential risks. Not me, that's for sure.

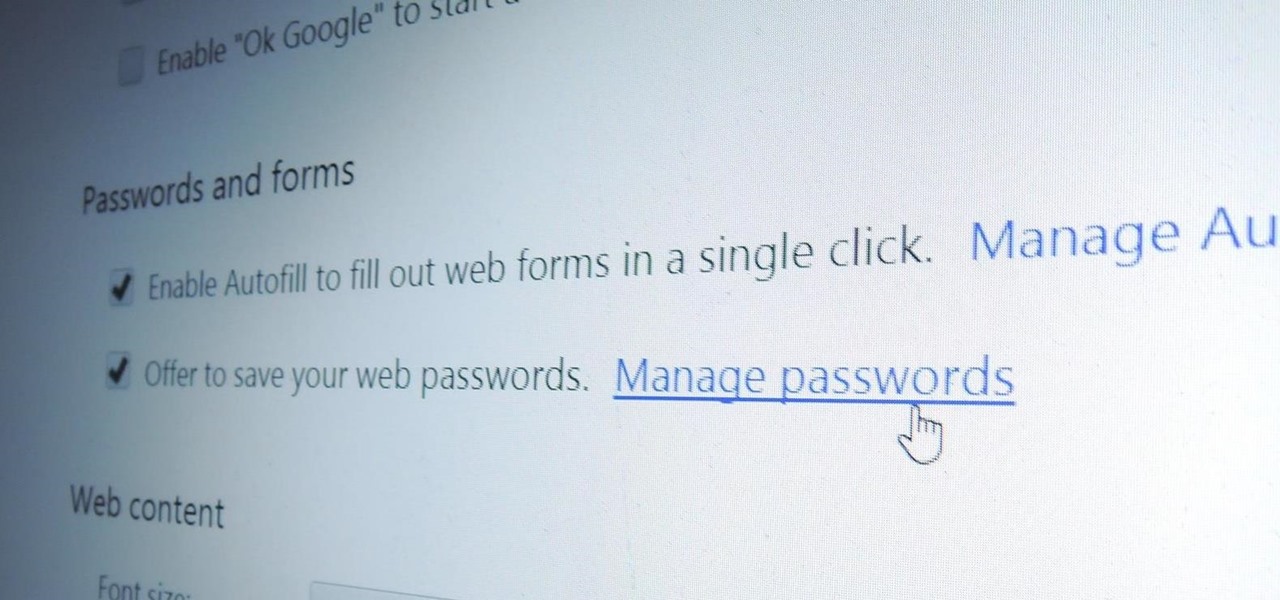
Chrome, Firefox, and Safari all provide built-in features that allow you to save your username and password for your favorite sites, making the process for entering your credentials a breeze when you revisit them.

When it comes to squeezing as much battery life as possible out of our smartphones, most people aim for software solutions, or ones that can otherwise be easily managed right from the touchscreen.

Tequila is a hard liquor that's often been misunderstood. Produced from the agave plant, this aged spirit has complex flavors that bloom the longer it's aged and can rival the finest scotch.

While you may look ridiculous doing the potty dance and crossing your legs back and forth, holding it in can be worth the discomfort when you've got an important decision to make.

Known for its easily recognizable filters—and coining the hashtag #nofilter—Instagram has long been an app that focused more on photo posting rather than photo editing. Yet today, Instagram released an upgrade for both Android and iOS users that edges the app towards becoming a full-fledged photo editor.

Apple announced the successor to Mac OS X Mavericks at their Worldwide Developer's Conference 2014, and it's called Yosemite. Named after California's Yosemite National Park, it will be available as a free upgrade from the Mac App Store for everyone this fall.

Most days, getting through an eight-hour work shift is a struggle. There are a million places you'd rather be, and none of them include your desk. It's difficult to find the motivation to tackle the growing number of emails in your inbox when your mind is back at home, comfortable in front of your gaming system.

Welcome back, my aspiring hackers! In previous tutorials, I have shown you how to scan the globe for vulnerable servers and write simple scripts in BASH and Perl to perform other reconnaissance tasks. In a very recent guide, I taught how to scan vulnerable servers for Heartbleed.

It can be a pretty exasperating ordeal to hunt for one image on your tablet when you have hundreds and hundreds of photos in your gallery. Luckily, there are ways to make this a pain-free process on your Nexus 7, as well as make sure it's never a problem in the future.

Online gaming is nothing new, and with live YouTube streams becoming ever more popular, there always seems to be a way to watch people play video games. Twitch TV offers the same spectator experience you've come to know and love, but the people over at TwitchPlaysPokémon have gone a step further and made it so that the spectators are the ones playing the game.

If you've seen ParaNorman or Fantastic Mr. Fox, then you have some kind of idea of what stop-motion animation is. Basically, these artists make objects, or small figures, appear to be moving on their own by manipulating and repositioning them in the smallest increments, then capturing each frame after doing so. When all the frames are compiled together, the final product is something spectacular like The Nightmare Before Christmas, which took roughly 109,440 frames in all.

Sometimes it's the little things that make our days better, like finding a dollar in our recently washed jeans or a box of donuts in the lunch room. But your Nexus 7 tablet's lock screen isn't typically one of those things—it's just a lock screen after all.

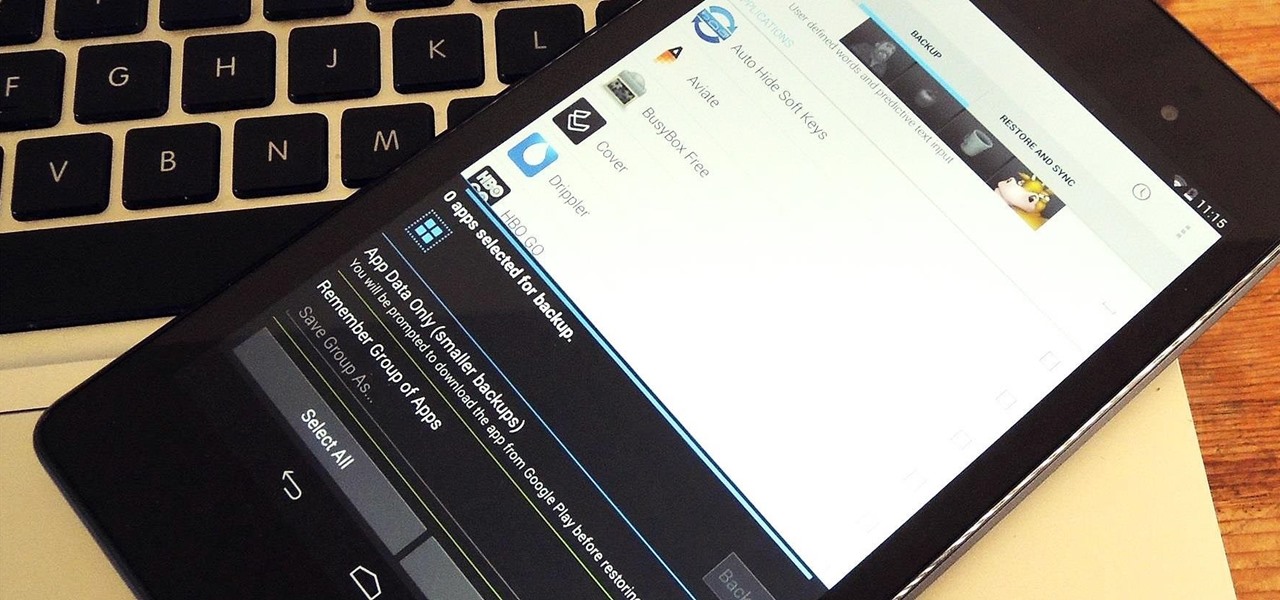
At some point, we all need to back up our device. Maybe it's time to take it in for repairs or maybe you're just cautious and paranoid. Maybe you're trying out a new ROM on your Nexus 7—then you definitely need to back up. The most secure way would be to use a custom recovery like ClockworkMod or TWRP, but if you're not rooted or planning to root, then you'll need an easy alternative.

Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.

If you've had the pleasure of owning both an iOS and Android device, you may have noticed one subtle difference on each one's PIN unlock screen. Android's lock screen requires you to press "OK" after entering the PIN, whereas iOS's simply unlocks the screen right after the last digit.