Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.
For most of us, the primary reason we capture videos on our iPhones is to post on one of the various social media platforms out there, like Facebook, Instagram, Snapchat, or Twitter, providing instant gratification by receiving a proverbial nod from our followers.

Heads up! We've done a new, more thorough review of the best Android file-sharing apps. You can check that out here. Our old file-sharing app roundup can still be viewed below for posterity.

Google made a huge splash this year in their annual Google I/O with an awesome announcement regarding their Photos app. Although I was primarily interested in the details surrounding Android M, my ears instantly perked up when Google announced that their Photos app will now offer free, unlimited, high-quality storage.

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

Big box stores love to sell gift cards, and as consumers, we snap them up almost as quickly as they can be printed. This industry has become rather profitable, though, because portions of the gift card balances often go unused.

Your iPhone's home screen is a tricky thing. You can sort your collection of apps in any order you'd like, but where you place those apps is a totally different story. App and folder placement follows a strict grid on iOS from left to right, top to bottom. No exceptions, and that's how Apple wants it. So you might think without a jailbreak you're stuck with this layout — but you're wrong.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

The Nexus Player is one of the most robust set-top streaming devices on the market. This is mainly due to the fact that the base software it runs is a direct fork of Android, which is a very powerful operating system itself.

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

The internet is forever. When you put something out there, it can easily be re-shared, floating from server to server indefinitely with no way of taking it back. It's a scary thought when you consider that a young adult's grandchildren will one day have access to their drunken party pics.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

If you've ever owned an HTC device or anything in the Nexus line, odds are, you have typed the word "fastboot" into your command line at one time or another. That said, odds are, you have only just barely scratched the surface of what this handy little Android tool can do. Let's take a deeper look.

Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requires an external wireless adapter (your wireless adapter is piped through the VM as a wired device, eth0), but it makes for a great place to test your hacks while honing your skills.

Climbing into bed and shutting your eyes each night is heavenly—but waking up the next morning isn't. We all hate dragging ourselves out of the comfort of sleep and into the groggy, exhausting work day. Yet starting your day doesn't have to be awful if you know how to hack your sleep cycles and get the most out of your shut-eye.

Fasting—or the practice of regularly abstaining from ingesting anything except water—is a pretty drastic move. I tried to fast for two days and made it to the 12-hour mark, which is when I broke down and ate a quart of ice cream.

When OS X Yosemite was first announced, there were a number of features that struck my attention, but one in particular that stood out above them all was the ability to make and receive texts and phone calls from your Mac, which Apple calls Continuity.

Boozing it up at work might have been okay back in the days of Mad Men, but today, employers prefer that their workers stay sober. What you and your bosses probably don't know is that a little drinking on the job can actually increase your creative capacity and problem-solving skills. Alcohol Can Enhance Your Creativity at Work

Have you ever fallen victim to a clever Jedi mind trick? Don't worry. It happens. There are evolutionary reasons as to why our brains sometimes give into the oldest tricks in the book. Fortunately, the more you understand the tricks of a salesman, the easier it is to avoid their gripping psychological influence. Clue #1: Too Much Specificity

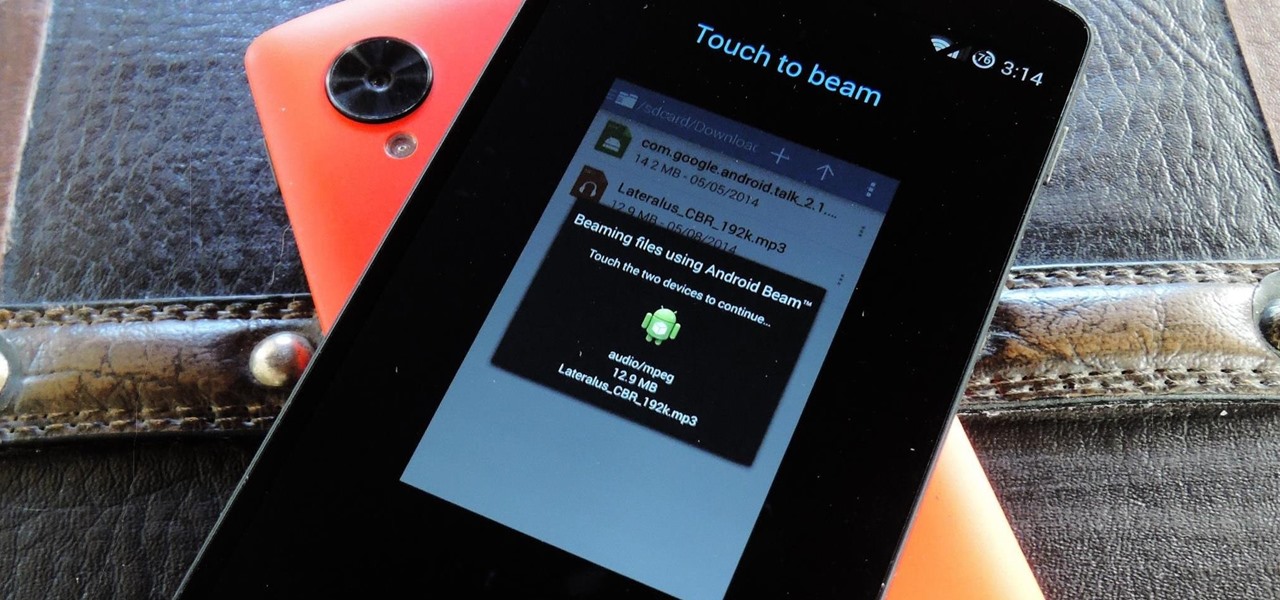
Your Nexus 5 comes with a pretty cool feature baked in called Android Beam. Using NFC, or Near Field Communication, this functionality allows you to send information to another compatible device by simply touching the two together. Most flagship devices have NFC built into them these days, so there is a broad range of devices that your Nexus 5 is capable of sharing information with wirelessly.

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers).

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

There are definitely some very cool things about the new iOS 7, but it's also got plenty of downsides, one being the updated look of stock app icons. Apple drastically changed their glossy skeuomorphic icons for a flat, modern squircle look using their golden ratio grid.

Mixing water and electricity is extremely risky and potentially lethal, yet that's exactly what I did with the Scariac. In its simplest form, the Scariac is just a glorified version of two wires in a bucket of water, but it's actually one of the cheapest power controllers you can make.

Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.

Building a DIY Alarm System: The Concept So, you want to protect your property, or maybe a room, car, or even your backyard. The concept of an alarm system is to notify the "alarm administrator" that there is an intruder entering the previously designated boundaries. The triggers for this boundary could be as simple as a pressure sensor, or as complicated as a laser network. They all do the same thing, but some work better than others.

Wrapping leather is the least of your worries when it comes to the meticulous and dexterous art of making jewelry. IIf you have the basic jewelry making skills down, doing this wire-wrap on leather should be a cinch.. This demonstration video will help walk you through the process of wire-wrapping leather.

Instead of just going for a walk through the outdoors, try adding in the rewarding hobby of bird watching. The song sparrow is a great bird to look for on perches and will vary in appearance across the US.

Dr. Aris Latham suggests setting standard plans for breaking a fast for most of people that he interacts with because the animal body has been programmed to eat in a certain way. This is necessary to train your body well so as to survive and be healthy. Divide your day into 3 equal parts of 8 hours. Take the sleep part of the day where you deal with the waste in your body and create energy within the body. The next period when you get up is basically when you break your fast when your were sl...

There’s so much you can do with a shoe. Be it the house in a fairy tale or just on the foot of a man, you will want to know how to sketch a good shoe. Keep on practicing and try giving your shoes a little wear-and-tear character.

For furniture or wood projects, adding an aged wood look can give real character and interest to an otherwise ordinary object. With a little sanding, stain and lacquer to finish you can transform any wood object.

Crossword puzzles are great way to exercise you mind and have something fun to do with breakfast. Don’t just do a puzzle, but make one yourself. You can do it by hand or try out the help of a crossword building software.

If you want to shake up your style or pay tribute to the 90s, then bust out that crimping iron. You will bring the party with this fun and funky style that can worn down, up or added to bring a little flare to more traditional styles.

Bennett's fracture takes place at the base of the thumb. It typically occurs when an individual falls on an outstretch hand. The force is directed this way; the fracture occurs here. Learn how to diagnose and treat a Bennett's fracture in this medical how-to video.

For all intents and purposes, Google could have called its 2023 developer conference A/I instead of I/O. Capitalizing on the artificial intelligence hype, Google devoted most of its keynote address to AI research, experiments, and developments. But there's some substance behind the hype in the form of new features in the Google services you already use on Android, iOS, and desktop.

Customization has always been the main draw of Android for me, but Apple has an impressive feature on iOS 16 that lets iPhone users create customized emoji wallpapers for their home and lock screens. While Android doesn't have something like that built-in by default, it's easy enough to make emoji wallpapers for your Android phone.

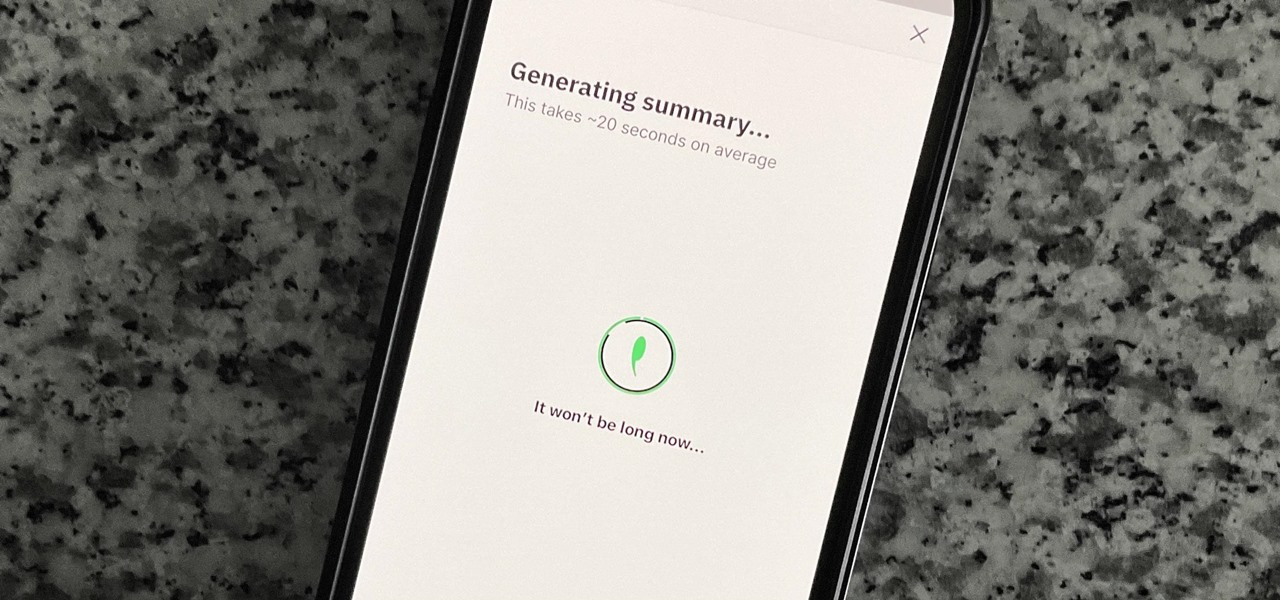
If you're like me, you don't have time to sit down and leisurely read an entire article from start to finish — but you still want to be informed throughout the day. Instead of just browsing the daily headlines, there's a free service that will summarize any article you throw at it, giving you a better idea of what's going on without committing to reading an entire article.

For a long time, digital creators have had to make do with clumsy mice that don't capture the minute movements they need to do their best work. Unless you were willing to spend potentially over $600 for a drawing tablet with a high-resolution screen, you were stuck with a mouse. Creators who work with audio or video were just out of luck, period.