Over the past two product cycles, Apple has been rumored to be preparing to reveal its Apple AirTags tracking devices that can help iPhone owners find their possessions with augmented reality.
Apple released iOS 14.3 public beta 3 today, Wednesday, Dec. 2. The update comes three hours after Apple released 14.3 developer beta 3, and 15 days after Apple released iOS 14.3 beta 2 for developers and public beta testers. The latter introduced a change that bypasses the Shortcuts app when using a custom icon on the home screen.

Apple released iOS 14.3 developer beta 3 today, Wednesday, Dec. 2. The update comes 15 days after Apple released iOS 14.3 beta 2 for developers and public beta testers, which introduced a change that bypasses the Shortcuts app when using a custom icon on the home screen.

Android updates don't have as many headlining features as they once did, but that's the point. If you keep updating software to add features and fix bugs, you'll eventually reach a point where the main focus is polish. That doesn't mean you can't get excited about a fresh coat of wax.

Apple just released the fourth developer beta for iOS 14.2 today, Tuesday, Oct. 20. The new update introduces eight new dynamic wallpapers, including four real-life landscapes, and four digital landscapes.
The Memories feature in Photos is meant to help you rediscover old or forgotten experiences by creating a short slideshow of photos and videos based on locations, dates, and events. It's a fun feature to relive exciting times, but it isn't always perfect because it's generated automatically. It might include incorrect content, but in iOS 14, you can now create your own Memory Movies.

One of the underrated components of the Galaxy Note 20 series is its usage of Gorilla Glass Victus. Think of this as Gorilla Glass 7, the latest innovation from Corning. And this release is a big deal, delivering protection without sacrifices.

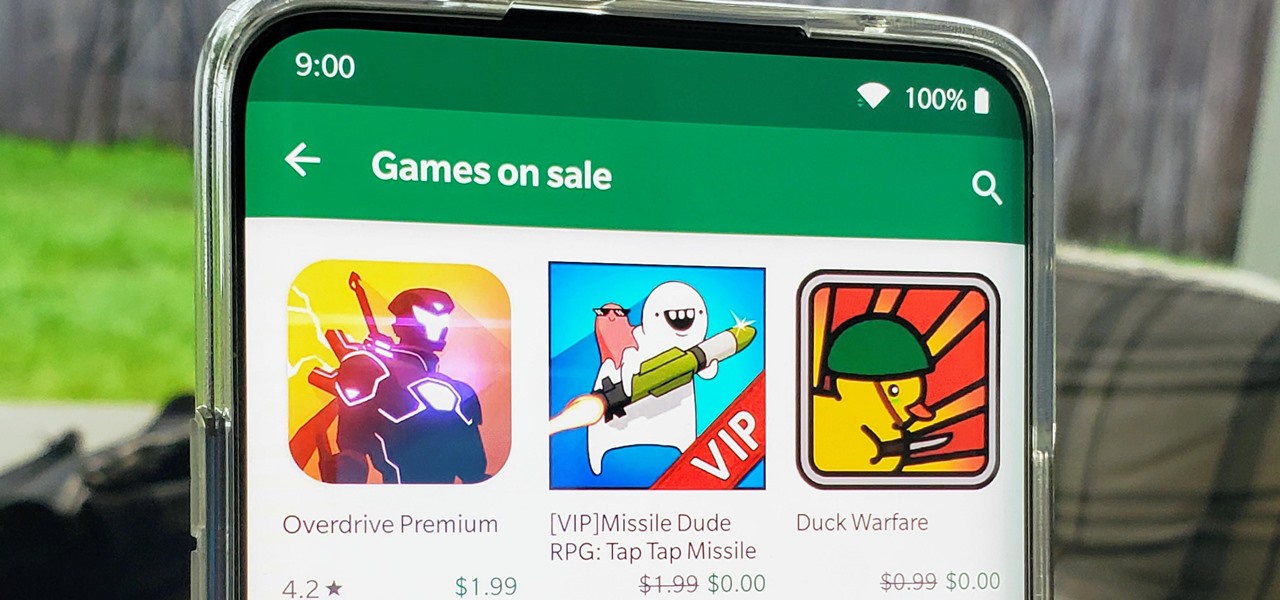
Software takes time to create, and time is money, so a lot of great apps aren't free. But to generate interest, some developers will make their paid apps free for a limited time. The potential for a long-term increase in daily active users more than offsets the short-term lost revenue. So for us end users, the trick is knowing when these sales are going on.

A stager is a small piece of software that's typically used by malware to hide what's happening in the early stages of infection and to download a larger payload later.

The Home button on an iPhone does a lot. That's not necessarily news for anyone who's ever owned an iPhone with a Home button, but what you might not know is that it's capable of so much beyond the standard everyday functions. So if you have an iPhone 7, 8, or the new SE model running iOS 13 or later, keep reading to learn about 17 secret Home button tricks you're missing out on.

One of the benefits of Blu-ray and DVD is the ability to share discs with friends and family without any hassle. Want to show off your favorite movie? Just lend them your copy. A digital movie isn't so kind, as it's typically locked to the account that purchased it. But now there is a way to share your digitally purchased movies with friends and family — and it won't cost you or them a dime.

Does TikTok scare you? Trust me, I get it. It's a strange, unfamiliar place to those of us not accustomed to its ways, populated by teenagers and college students with their own subcultures, memes, and humor. But here's the thing: TikTok has something for everyone, you included.

For anyone interested in using cheap, Wi-Fi-connected microcontrollers like the ESP8266, the Arduino programming language can be a barrier to entry. Based on C++, Arduino requires knowledge of more computer science than languages like Python. Fortunately for beginners, setting up MicroPython on an ESP8266 allows anyone to write Python on affordable microcontrollers in a matter of minutes.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

Android 10 is officially out, but a lot of phones didn't get it in 2019, and others may not get it at all. With this page, you'll at least know when or if.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

In a bold move, Samsung has decided to forgo the Galaxy S11 moniker and jump straight to the S20. Perhaps it's marketing for the new 20:9 aspect ratio and 120 Hz display, or maybe it's just the fact that it's releasing in 2020.

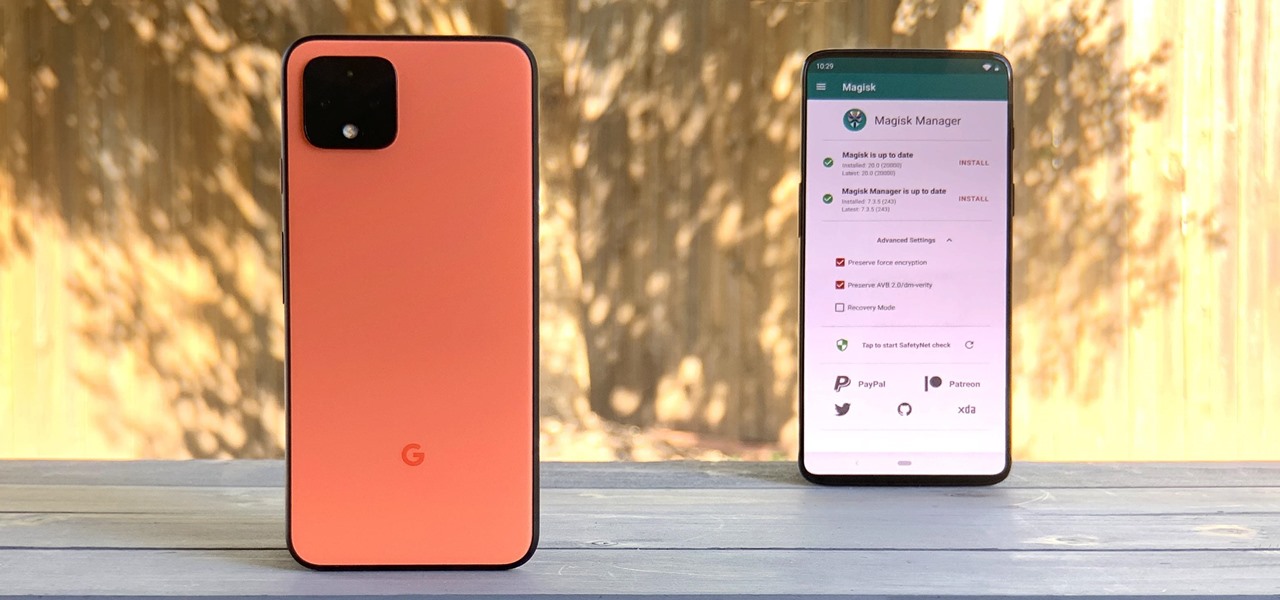
According to a study done by Kaspersky, 7.6% of Android users root their phones. That may not sound like a lot, but with over 2 billion Android devices out there, the math works out to over 150 million rooted phones — more than the total population of Russia, Mexico, or Japan — so root nation is an important demographic that deserves being catered to.

To be honest, the Mail app for iPhone had always been somewhat forgettable. It lacked many of the features that made third-party clients like Spark and Edison better, but with iOS 13, the gap between Mail and its competitors is much smaller. Apple updated the layout and added many new features to its native emailing app, and that may be just enough to get you to switch back.

You may have recently seen a plethora of Instagram users, including celebrities and politicians, sharing a screenshot declaring that the platform will implement a new "rule" where it would own and could use your photos and videos however it wishes. The screenshots are part of an internet hoax, one that's been around in one way or another since 2012, but what can Instagram actually do with your media?

Emoji are, without a doubt, an integral part of messaging on smartphones. Whether you're team iPhone or Android, chances are you send emoji daily. However, years after their introduction, emoji remain static in most cases, even with animated stickers and GIFs supported on almost every major chat app. That said, one of those chat apps, Telegram, makes things more lively.

I think we all like the idea of getting paid games for free with minimal effort. Typically, though, anything claiming to help you do that is either illegal or a scam. But there are actually quite a few no-fuss methods that can get you paid games without going too far out of your way. From checking notifications to discovering hidden offers, you might have something waiting for you.

There's something extremely satisfying about hunting down your online adversaries and knocking them out with a well-placed shot, which probably explains why shooting games are still one some of the most popular time killers for iOS and Android.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

When new Android versions come out, the modding community has to find new ways to root the OS. It's a fun cat and mouse game to follow, but it also means the process of rooting isn't exactly the same as it was the last time you did it. Android 10 changes how root works on a system level for some devices, but luckily, the developers are already on top of things.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

Metadata contained in images and other files can give away a lot more information than the average user might think. By tricking a target into sending a photo containing GPS coordinates and additional information, a hacker can learn where a mark lives or works simply by extracting the Exif data hidden inside the image file.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

OnePlus always seems to offer affordable yet powerful tools for videographers of all kinds. The camera hardware itself is crucial, but what's hardware without good software to highlight its real potential? It doesn't matter which version of the smartphone you have, they're all powered by the very same OnePlus camera app.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

When you want to install a new tool or game on your iPhone, you go straight to the App Store to do so — but it's not the only place you can get apps from. Some developers use back alleys to get their apps to you, while others can trick you into installing them without giving it much thought. This can lead to malicious software running on your iPhone, software you'll want to get rid of asap.

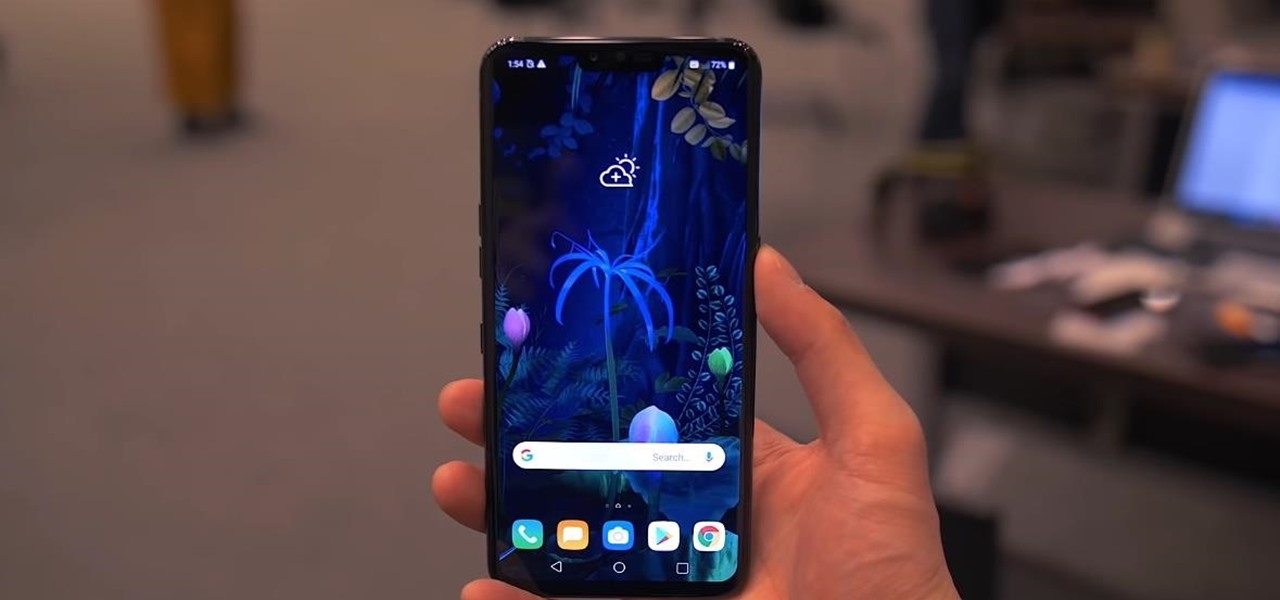
Similar to last year, LG is mixing up its releases. Instead of the G series in the first half of the year and the V series in the second half, LG is releasing both heavy hitters together. However, unlike last year, this is a true upgrade from its predecessor, the LG V50 ThinQ 5G.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

Whether you've celebrated multiple cake days or you're just now getting your feet wet with Reddit, it's a rite of passage to choose your preferred smartphone client. Quick spoiler: Your best option most certainly is not the official Reddit app.

The rise and fall of Meta, the Silicon Valley-based augmented reality startup that looked to challenge the likes of Microsoft's HoloLens, and others, took just six years.

While keeping your iPhone out of the bedroom might help to avoid unnecessary distractions before bedtime, it could be better served right by your side to help diagnose sleeping issues you may be experiencing each night.

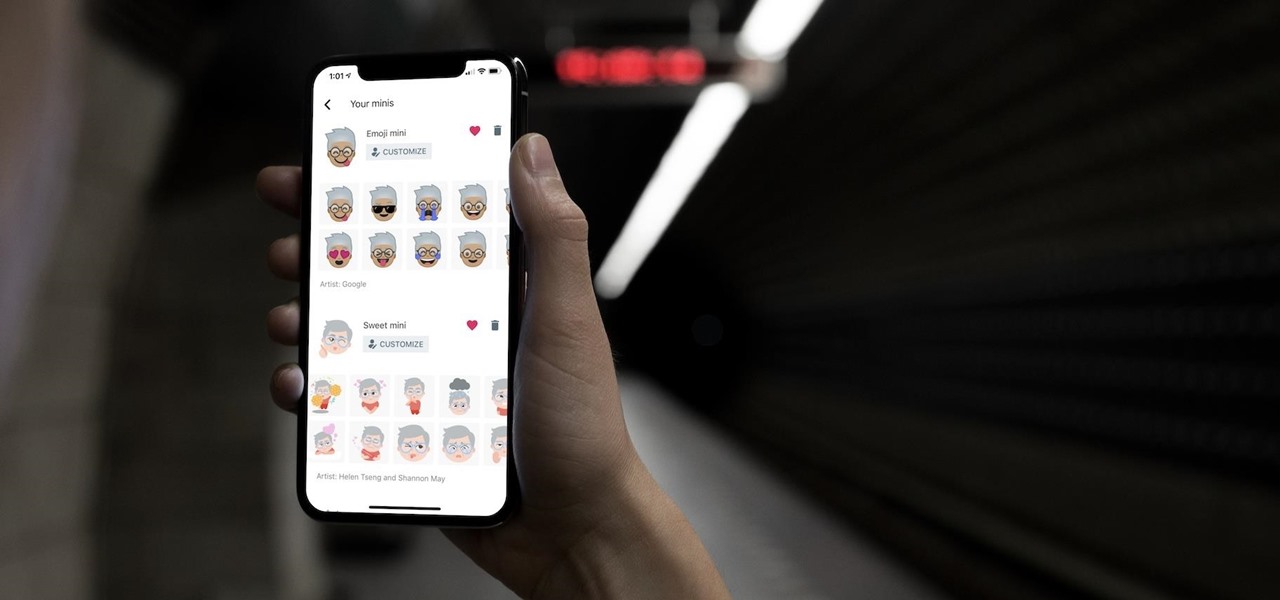
Expressing yourself during chats is much easier these days thanks to the steady rise of emoji. Now, products like emoji Minis for Gboard are taking the craft to an interesting yet familiar new level. With emoji Minis, you can automatically create stickers based off your own face. From there, you can further customize the stickers by adding key features such as glasses, earrings, and facial hair.

These days, it's easy to cut the cord. Thanks to a new crop of streaming TV apps, you can get the same service offered by a traditional cable subscription at a fraction of the price. After some extensive testing, we believe we've found the absolute best apps for cord cutting.