
Quick Tip: iOS 7 Calendar
With the recent release of iOS 7 there is a world of easter eggs to discover within the new operating system.


With the recent release of iOS 7 there is a world of easter eggs to discover within the new operating system.

There are quite a few different types of headphones, and they all have their fair share of both pros and cons. Circumaural (full-size) headphones typically have better sound quality, but the in-ear kind are much more convenient to wear on the go.

Every time a major social media network changes its layout, people are pissed—especially when it's Facebook. Zuckerberg and company seem to have a knack for implementing changes that people hate, and then learn to love (Timeline, anyone?).
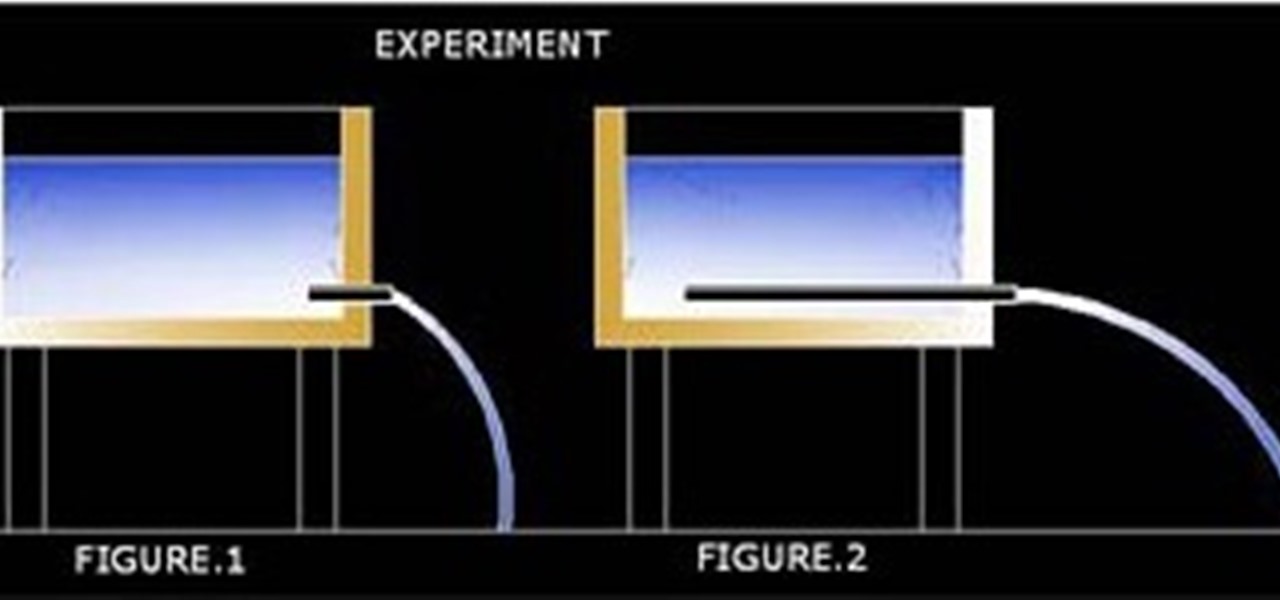
An experiment was carried out at our laborataries to investigate the flow through two pipes of same diameter fitted at the same height from water level inside of a water tank as shown. It is found the longer pipe line inside the water tank generates a higher speed resulting more powerfull flow. Flow in this pressure pipe develops due to gravitational accelaration on a horizontally flowing water column also, when it is an enclosed stream of flow. If this length is short it is not possible to d...

PDF is a convenient format for documents that can embed text and pictures and can be read by almost any device—personal computers, laptops, smartphones, etc. However, PDFs are mostly read-only files, so sometimes it's necessary to convert them to JPG images, a universal format for pictures. JPGs can be modified by software such as Adobe Photoshop or posted on Facebook.

Ever hear of Spokeo? No, it's not a city in Washington state. It's a website called Spokeo.com, and it marks the complete end of privacy on the internet. If your phone number and address has been posted in a phone book, it's on there. If you own a house, chances are there's a picture of it. If you have a Facebook profile, it's probably listed.
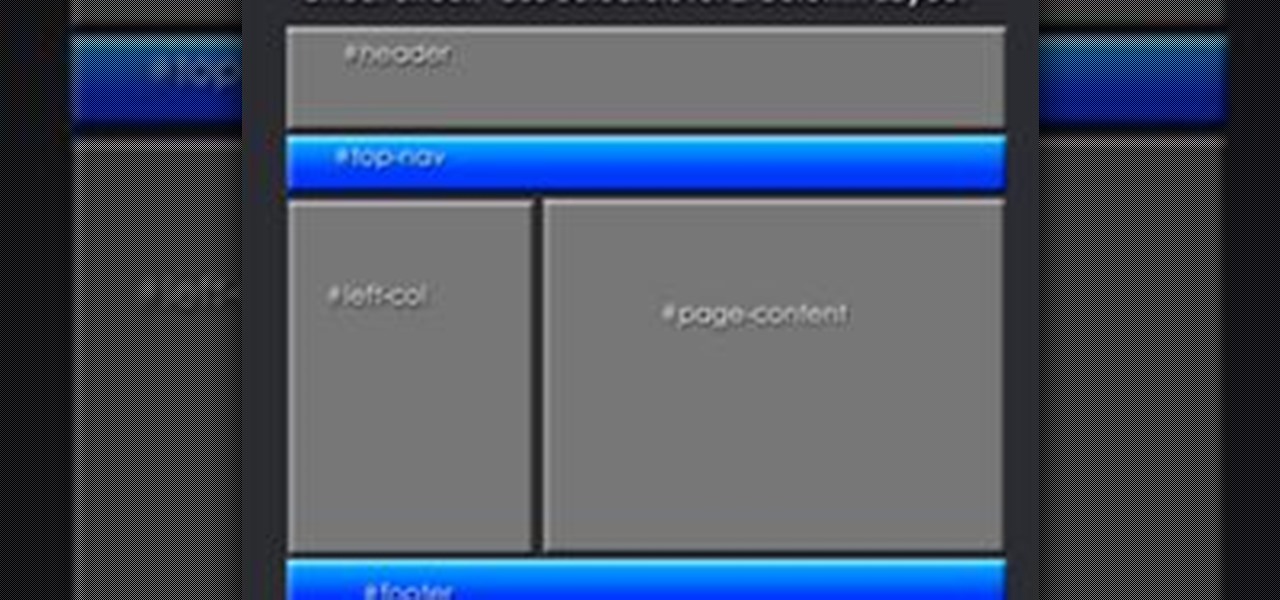
Getting Started Steps for Beginners If you are brand new to Expression Web 4, then read the following guide to quickly set up your web site and web pages.

This past spring, British TV show Fifth Gear aired stuntman Steve Truglia performing a Hot Wheels inspired feat. The daredevil completed the world's largest 360° loop-the-loop. Death was a definite risk.

Diego Stocco is back (previously, the incredible Music From a Tree). This time Stocco has created the experibass:

Whether you love Björk or you hate her, her Wanderlust music video is must-not-miss. Created by Encyclopedia Pictura, a California based production company, the video combines live action, puppets, scale models, and computer generated animation.

I like to grow vegetables all year round, and I couldn't afford the big gas bulbs, or the power to run them. The big gas bulbs:

The way you place your hands on the golf club will have a direct relationship to the flight of your ball, as demonstrated in this how-to video. If your grip is too weak, the clubface angle at impact will be off line, which will cause the ball to curve. The bottom edge of the clubface needs to be straight to the target line in order for the ball to fly straight toward the target. A good golf grip would be considered neutral, that is, neither weak nor strong. A neutral grip will allow your hand...

There’s a race on to see who'll be the Instagram of moving pictures. This makes sense, since many of our phones are clogged with video that, so far, no one is going to see. Wouldn’t it be great if there were a simple app that could take our video content, edit it for us, and then publish it to all of our networks?

I have had a lot of people ask me, "How does my neighbor keep getting into my wireless?!". Chances are, these people are all using WEP, a deprecated wireless encryption protocol. Either that, or you are using one weak WPA passphrase.

I just found out that I might be expected to tip all the vendors... on top of the exorbitant fee they charge! Sigh... Here is a great tipping cheat sheet courtesy of theknot.com.

Grey's Anatomy fans— you have just gotten a better viewing experience— an interactive viewing experience. But you need an Apple iPad to bask in the sweet delight of doctorly debauchery and do-goodery.

An effective warm up is essential for climbing: you will climb better and are less likely to sustain an injury. With no warm up, performance is compromised, fatigue comes quickly, and injuries are more likely. All together: Not Good!

Scrod sounds good, right? This fish will satisfy your seafood craving. But wait… is scrod even a fish? No. If you're not from the New England-area, you probably would never know this, but scrod is not a fish at all. It's often misconceived as being a type of fish. However, scrod is a New England term that refers to any white fish that has been split and boned before sale, typically cod or haddock.

Large, sweaty men are usually the first thing that comes to mind when you hear the word football, but for this video, we're not talking about the guys on the playing field, we're talking about the guys in the fishing boat, the kind of guys who like to use a "football jig".

My name is Noah Hornberger. I'm a former Pixar artist (Wall-E, 2008) and Professor of Animation (DePaul University, Chicago), and I have recently invented a motion-activated musical toy called the Dub Cadet. One Substance TV blogger has called my light-up sphere that transforms motion into music, "Daft Punk [the electronic music duo] meets Simon [the handheld toy] in a ball."
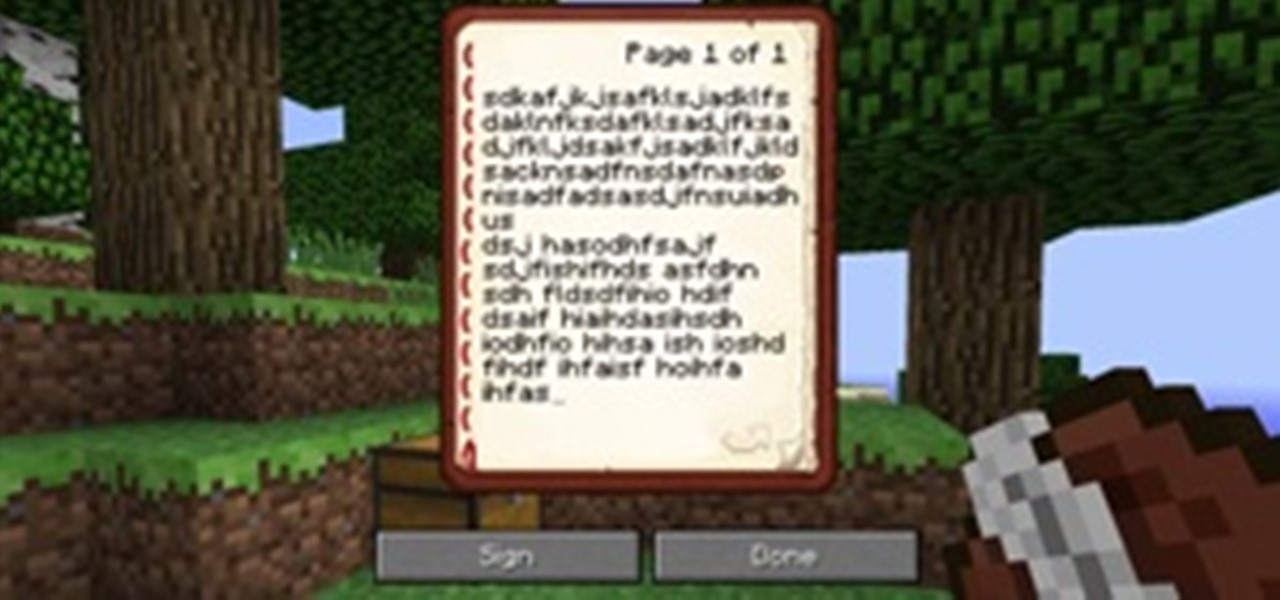
Looks like Minecraft is getting some cool new features, including editable books and colorful wooden half slabs. Check out the video below to see the newest Minecraft Snapshot 12w17a in action. Warning: This release is for experienced users only! It may corrupt your world or mess up things badly otherwise. Only download and use this if you know what to do with a minecraft.jar file!

So, you scratched up your $500 Adobe CD and now it's unreadable. You could go buy a new one, but you already purchased it! Searching The Pirate Bay and downloading some Adobe software can usually be easy enough, but what should you watch out for?

As some of you Mad Science readers will remember, we recently covered the separation of water into hydrogen and oxygen using electrolysis. Passing a current through water can rend it apart, but we can also recombine that oxygen and hydrogen to make electricity! This is the principle behind those vehicles run by hydrogen fuel cell engines.

You might already know a little bit about what the National Ignition Facility has been up to lately, or what they could possibly achieve. But last week, even the scientists at the Livermore, California station couldn't predict the awesome power that their humongous laser was capable of. NIF's laser is already the record holder for the world's largest laser, and now it can also claim to be the first ever 2 megajoule ultraviolet laser after it generated nearly 100 times more energy than any oth...

Ever wondered how other players can get so much awesome enchanted gear in such little time? Struggling to gain experience orbs and need an efficient way to do so with very few casualties? In this tutorial, we will be going over how to build a quick XP farm with a zombie spawner (though any spawner will do). Setup

As you progress in the world of information security, you'll find yourself in situations where data protection is paramount. No doubt you will have files to hide and secrets to share, so I'm going to show you how to use the GNU Privacy Guard (GnuPG or GPG for short) to encrypt and decrypt as you need. GPG is a great open-source version of Pretty Good Privacy (PGP), a similar application used for encryption, but licensing and patent problems led to the development of GPG in its wake.

In this article, I'll be showing you how to make a simple yet effective static electricity generator. Basically, this device allows you to carry a constant static charge on your body and discharge it on anything grounded or of opposite polarity. The electricity generated is around 8-10 kV, at a very low current. The shock is enough to startle your friends, just like a static shock from a trampoline or carpeted room. You'll need a little experience in soldering and circuit design to build the ...

This is the third part of my electromagnetic pulse series (see Part One and Part Two). By now, I've covered the hardware and general concept of electromagnetic pulse generators, but how exactly do they disable electronics? How can an invisible field of energy have such a catastrophic effect on computers, cell phones, and most any other electronics? I'll be answering all these questions in part three of Making Electromagnetic Weapons.

How many people use the big search engines here? I'm going to estimate 90% of everyone on WonderHowto uses one of the following on a regular basis: Google, Bing or Yahoo! Search. The question is: are you in that 10%? You should seriously consider dumping Google search for DuckDuckGo. Why? DuckDuckGo does not track you.

Nikola Tesla In my opinion, one of the most neglected inventors of all time. The names Edison and Marconi come to mind as familiar, but Tesla? Most think of a car. Few know that Tesla is responsible for alternating current, florescent lights, radar, remote control, generators that preform efficiently, the spark plug, and many others. The U.S Supreme Court declared in 1943 that Tesla, not Marconi, was the true inventor of the radio.

Skyrim is a time consuming game. I know I'm not alone in saying I constantly find myself looking for more time in the day. There is never enough time to read the books I want to read, or learn what I want to learn, or play the games that I want to play.

How to Crack Passwords Faster by Putting Your GPU to Work with HashcatSecurity on the internet is always changing. Not too long ago, having a 10 character password meant that you were safe from all forms of hash cracking. Hash cracking is when you take a string of characters that have been passed through a cryptographic hash and try to reverse them. The normal processors that are housed inside of our computer cases are general purpose. The processors are not meant for handling complex math an...

Yes, you read the title correctly. GameStop has problems, and if you're lax in morals, you can take advantage of them for free games and cash. I'm bringing you all yet another exclusive Null Byte that falls into the fascinating category of life hacking.

Bitcoin is a new currency built off "Satoshi Nakamoto's" (alias) 2008 Bitcoin white-paper. Bitcoin provides its users with a way to make peer-to-peer (P2P) transactions without having to use a bank as a mediator. There is no middle man, no corporation backing it, and no one has access to your money, except you. It's decentralized from government, run by the people, for the people.

Unfortunately, I'm a little behind schedule on my pizza dough making mission, but I promise - more experiments coming soon! In the meantime, here's a beautiful video about the nuance that goes into bread making, as demonstrated by famed San Francisco baker Chad Robertson of Tartine Bread. Bread and pizza dough go hand-in-hand, and I've been thinking about picking up the Tartine cookbook for some time now. As I mentioned above, the nuance that goes into the process is really pretty remarkable....

For as much money as they've made from North American video game audiences over the years, Japanese game developers don't seem to have very much faith in them. Dozens of great titles from their 40 years in the industry have appeared in Japan and across Europe, oftentimes even in English. But they never make it over to America, like Mother 3, Last Window: Midnight Promise, Dragon Force 2, and Tobal No. 2 (that one didn't even hit Europe).

It's only been ten years? Where has all of the time gone? When RuneScape came out in January of 2001, the world was a different place. There were no such thing as Xboxes, normal gamers didn't care about the number of cores on a processor, and the World Trade Center Towers dominated the Lower Manhattan skyline.

Many gamers see the film industry as the premier model that video games should follow, and it's no surprise. Movies are seen as the most legitimate and profitable of all artistic visual mediums, which is certainly qualities practitioners of any new medium would desire. Big budget games like Heavy Rain and L.A. Noire strive for the same level as film by aping its techniques, focusing on storytelling in a cinematic fashion, rather than creating compelling gameplay experiences.

Video games are the most prevalent type of interactive media, but certainly not the only one. The interactive music video for the song "3 Dreams of Black" by supergroup ROME and digital artist Chris Milk utilizes the latest web design technology, video game influenced art and interactivity, and large crowd-sourced elements to form a compelling work of art. ROME is composed of producer extraordinaire Danger Mouse, Italian film composer Daniele Luppi, Norah Jones, and Jack White. Their recent e...

With the globally rampant use of such social networking platforms as Facebook, Twitter, and Foursquare, the issue of privacy has become a prevalent concern for many. And for good reason—there's the violation of Facebook employing user names in ads, the Etsy slip-up, and of course, the everyman act of recklessly sharing too much information via common social media outlets: a night of drinking results in morning after embarrassment, or worst case scenario, sloppy Facebook posts and tweets resul...