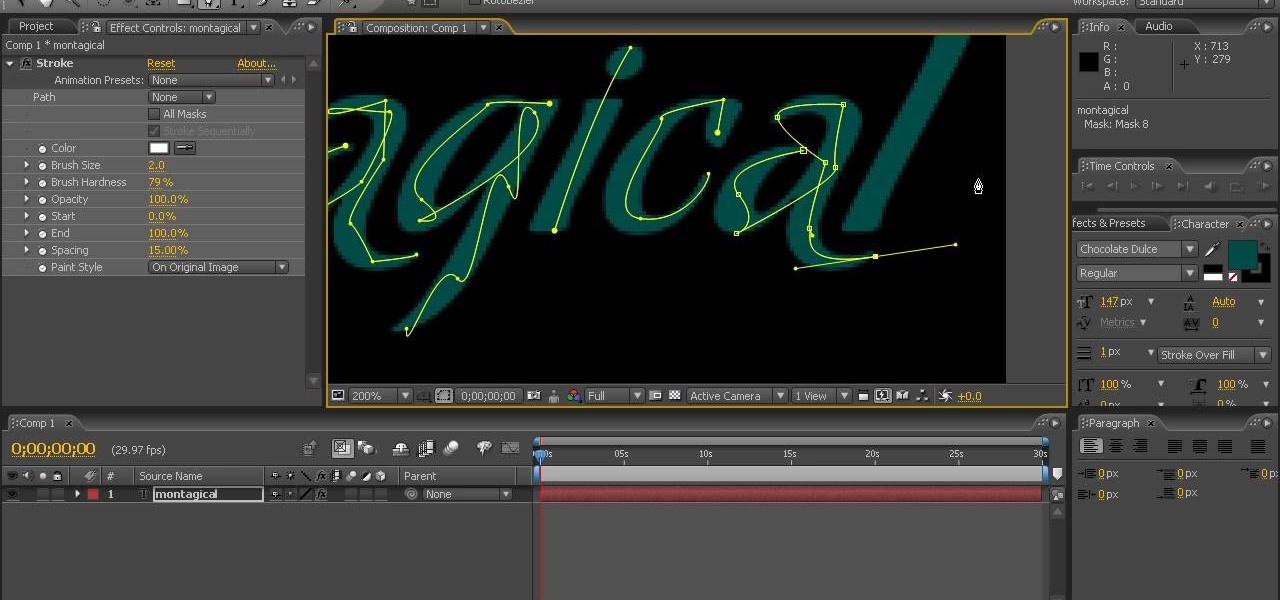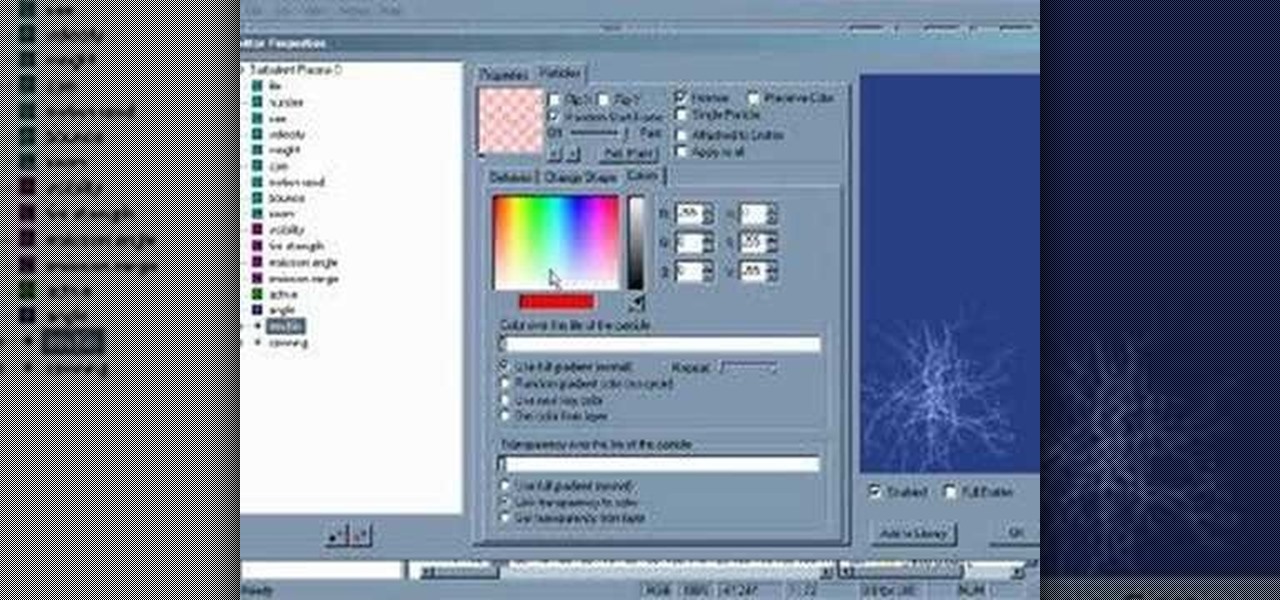
This tutorial is in the? tutorials map that comes with particleIllusion, but now available here! Check it out and learn the basics of how to use this particle generating plug-in software for After Effects, Sony Vegas and more.

Car + Hydrogen = Better Mileage? We're not quite ready to drop the cash on one of those under hood mileage boosters being sold all over the web...but using water electrolysis to produce Hydrogen sounded like a good first step!

Metacreations Bryce is a 3D terrain-generating application. You can build some beautiful landscapes, create animations, and even import 3D models from other programs.

Barrel distortion is a lens effect which causes images to be "inflated". Barrel distortion is associated with wide angle lenses and typically occurs at the wide end of a zoom lens. In this video tutorial you will learn how to correct the lens distortion in Photoshop.

Jeff Schell walks you through a few quick methods of making your titles appear less "computer-generated." This includes adding a linear gradient fill to the title as well as adding a soft Gaussian Blur to reduce the "computer crispness" of the text.

You can learn how to make the ice hockey side stop. Side stops is a side motion stop; not a snowplow stop. You need a strong knee bend to generate that scraping, stopping motion.

Former soccer star and current celebrity David Beckham has the augmented reality abilities of Facebook and Instagram as allies in the effort to eradicate malaria from the world.

A rainbow table can be thought of like a dictionary, except instead of words and their definitions, it holds combinations of characters on one side and their hashed form on the other. What is a hash and why would you want to know what random combinations of characters are hashed into?

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

In the perpetual search for a renewable and convenient energy source, our bacterial friends have once again stolen the limelight.

Video: . Nobody likes an RV or camper toilet that smells, this video will show you how to prevent your RV toilet from smelling.

As great as the Internet is, it is not without its dangers. Hackers at any time may be breaking into your online accounts and compromising your sensitive information. Last year, hackers broke into Facebook, Gmail, and Twitter and made off with 2 million stolen passwords.

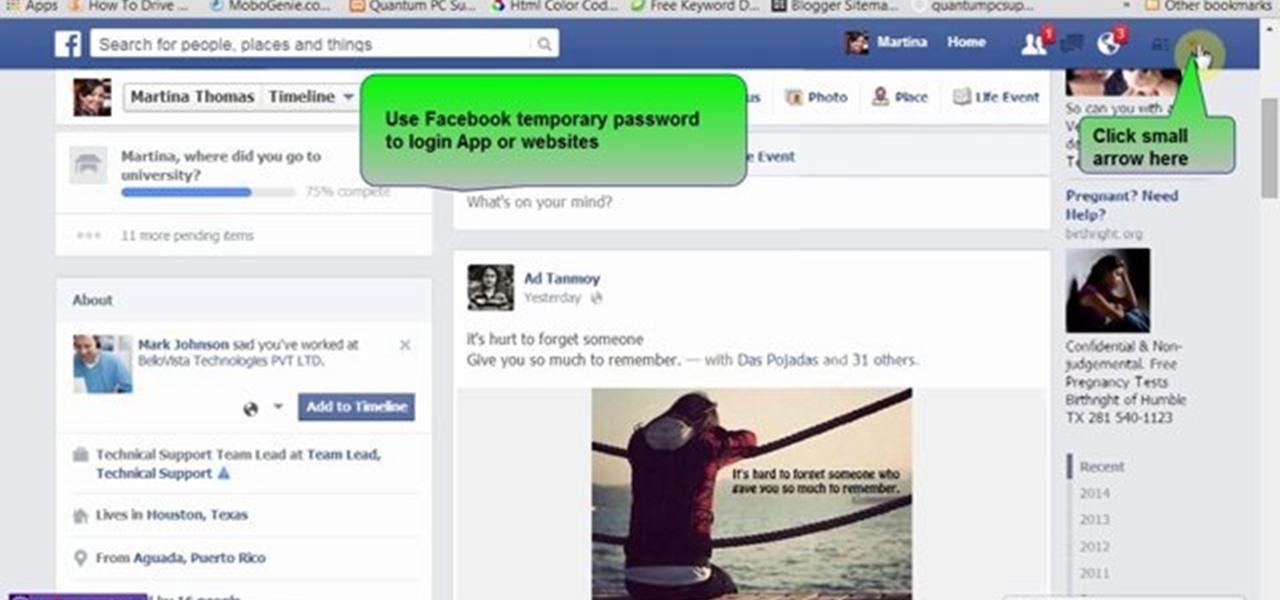
Many people use Facebook login detail to enter different apps or websites. This is somehow dangerous because unethical websites or apps may use your Facebook detail. So to avoid this warning Facebook is generating a temporary password for you. Now you could use this detail to login app or websites. You don't have to use your Facebook original login detail.

If you're looking for a fabulous gift, why not check out this tutorial with Martha Stewart and see what to do to create a beautiful fruit basket. Bananas, apples, peaches, grapes, cherries, oranges, pineapple, kiwi, tangerines - any fruit you want! Of course, make sure you're picking fresh, ripe and in season fruit so your gift can be enjoyed right away! And, you'll want a basket. Typically, these are made from wicker, but you could get creative and choose some other kind of basket as well!

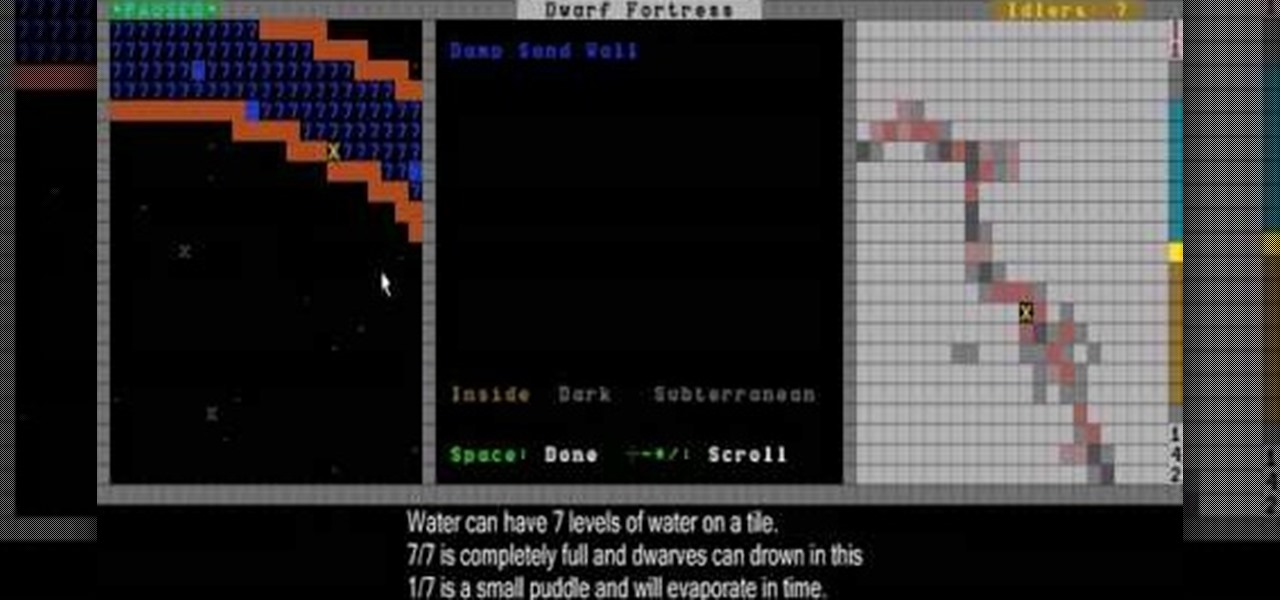
After you generate the world and choose a location for your fortress in Dwarf Fortress, it's time to prepare your party of seven dwarves to journey there. This video will show you how to assign their skill points and choose the right items to help you reach the fortress and succeed there.

This isn't your ordinary canoe. It might not be a canoe at all. But it's roughly shaped like one, only the ends have a small splash cover on the bow and stern decks not typically seen on canoes. But that's not the point, the point is you can recreate this cool paper boat with only one sheet of origami paper. If you know the name of this type of boat… speak up!

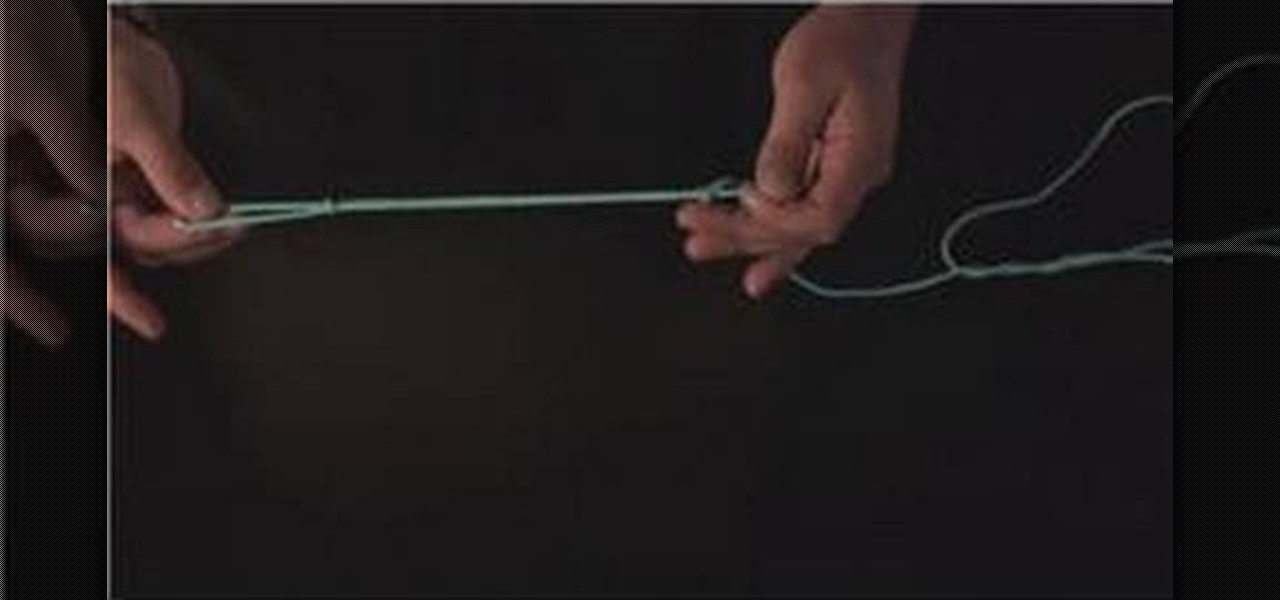
Know your knots! With this free video tutorial, you'll learn how to tie a Homer Rhode loop knot. Homer knots are typically used with heavy monofilament and work really well for fishing. The knot is easy to tie provided, of course, you know how to go about making it. For an easy-to-follow, step-by-step overview of how to tie this useful fisherman's knot in a minute's time or less, watch this free video knot tyer's guide.

Identity theft typically occurs when someone uses your personal information such as social security numbers, credit card numbers or account information to perform various misdeeds, and you are left to clean up the mess.

Changing your car's cabin filter and air filter is a really important part of its regular maintenance. Doing this simple maintenance task does not require a professional mechanic, so save your money and watch this video to start saving money today and changing your own cabin and air filters. This video specifically covers changing the cabin and air filter in a Honda Element. You can pick up the parts from your local Honda dealer. Typically, you should change your filters every two years.

Patching a bike’s tire inner tube is much easier and faster than it sounds. You Will Need:

Tim Brownson talks about how to tap into self-confidence during this video. This technique is called anchoring. An anchor is an idea or event that links to another event that is usually not related in some way but provides some kind of reminder of an emotion. This can also be called a conditional response. Tim gives a lot of real examples of anchors and conditional responses. First start by calming down as much as possible. Then think of some activity that you are confident you can do, and th...

In this Adobe After Effects tutorial, the instructor shows how to generate a hand writing effect. First, open Adobe After Effects. To do this effect, you need to use the Pen tool, which is a very good feature. Go to File menu, select new then create a new project. Go to composition and select a new composition. Right click and fit it to 100%. Go to the text tool and select a box on the composition and write something that you want. Apply a desired color and font to it. Select the text box, go...

In this Photoshop tutorial the instructor shows how to do retouching to produce undead skin makeup. This video shows how to make a convincing, undead like, vampire skin make up. First open a image of the face which you want to make it look like undead face. Go to the channels panel and make a selection of just the face with the skin and exclude the rest of the head which includes the hair and other stuff. Now open a new adjustment layer and open the color balance tool. Fist select the mid ton...

This video explains how to throw a football like a quarterback. With your elbows bent at a 90-degree angle, hold the ball in front of your chest with the fingers of your throwing hand across the laces of the football.

Learn how to do long stride runs across a floor. Presented by Real Jock Gay Fitness Health & Life. Benefits

Better known among consumers for its virtual reality apps, Jaunt is now pivoting toward solutions for augmented reality developers.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

Live theater doesn't typically benefit from the kind of computer-generated special effects that big-budget Hollywood blockbusters deploy, but that could change soon thanks to Microsoft's HoloLens.

Welcome, my hacker novitiates! As part of my series on hacking Wi-Fi, I want to demonstrate another excellent piece of hacking software for cracking WPA2-PSK passwords. In my last post, we cracked WPA2 using aircrack-ng. In this tutorial, we'll use a piece of software developed by wireless security researcher Joshua Wright called cowpatty (often stylized as coWPAtty). This app simplifies and speeds up the dictionary/hybrid attack against WPA2 passwords, so let's get to it!

Now that Thanksgiving is less than a week away, the holiday season is in full swing. And that means you're probably busier than ever, what with all the decorating, cookie baking, and present buying and wrapping.

Typically during the holiday season hostesses give very little attention to the plates that food is served on. Because the focus is on the food, the plate needs to be nothing more than a plain white backdrop, right? Wrong.

A sous-vide is an "under vacuum," a method of cooking food sealed in plastic bags and then dipped into a water bath that typically takes up to 72 hours to complete. Why cook your food in plastic baggies, you ask? To make sure all the ingredients come out pure and unadulterated.

Just because it's Halloween doesn't mean you have to dress up as something gory or creepy. Inject some pretty into the spooky holiday by donning a peacock costume, and check out this makeup video to learn how to create a lovely peacock makeup look.

During the age of silent film and film noir film was limited to only variations of black and white. While this aided greatly to produce scenes of dire intensity (a starkly lit shot of a man in an alleyway, for instance), this also meant that actors and actresses had to wear tons of makeup to make their makeup show up on screen.

Sea bream is a type of fish that lives in tropical climates, prefering to live in shallow waters and typically dwelling at the bottom. It's not nearly as easy to find at supermarkets as salmon or tilapia, but it's worth a try because it has such a unique flavor.

Once you've generated a world, picked a fortress location, and prepared seven dwarves, you're ready to start playing! This video will show you how the world map works and how to use it. It also covers how to rename your dwarves.

We've all seen origami frogs, as they are typically some of the easiest animals to make in origami. We've even seen jumping origami frogs that leap forward when you press down on the frog's back. But we bet you've never seen an origami frog that can do backflips.

The Solomon Bar is one of the most popular ways to incorporate paracord into a tie. The following video shows how to generate the banded bar, a dual-colored Solomon bar design. This video will show you how it's done! It's easy. So easy, in fact, that this clip can present a complete overview of the process in about 5 minutes' time. For more information, including detailed, step-by-step instructions, take a look.

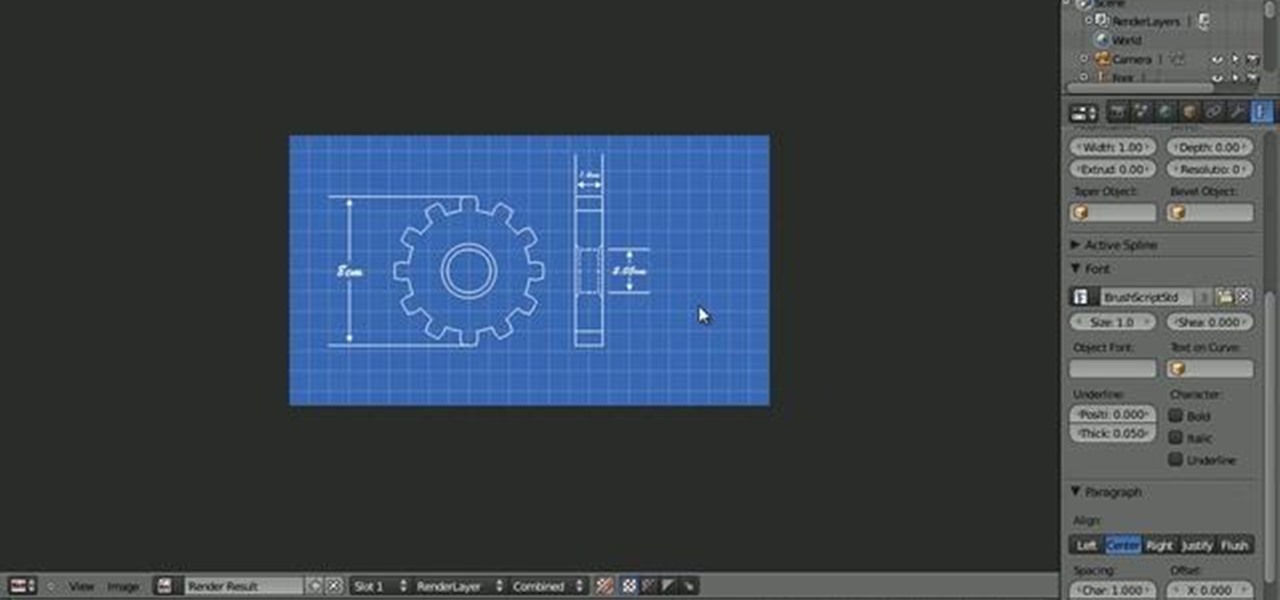
In this Blender 2.5 video tutorial, you'll see a method for generating neat-looking blueprint graphics. This tutorial includes using the Gears add-on, creating outline-only objects, setting up the World to look like a blueprint, and more. Whether you're new to the Blender Foundation's popular open-source 3D computer graphics application or are a seasoned digital artist merely on the lookout for new tips and tricks, you're sure to be well served by this free video software tutorial from the fo...