
How To: Do stability ball backbend holds
Learn how to do stability ball backbend holds. Presented by Real Jock Gay Fitness Health & Life. Benefits


Learn how to do stability ball backbend holds. Presented by Real Jock Gay Fitness Health & Life. Benefits

A demonstration of basic diabolo tricks.

Some card control techniques for beginner magicians.

A tutorial showing you some basic breakdancing footwork and floorwork.

We know that spring seems ions away, but if you're a gardener then it's time to begin thinking about what flowers you'll be planting to bloom during the spring. If you don't have much garden space but would love a very fragrant bloom, check out this video to learn how to grow lavendr provence in a container.

The most used and most washed articles of clothing are undergarments. Underwear, specifically bras and panties, are in desperate need of attention after each and every use. They're not like a pair of jeans, wearing them twice in a row is not a good idea, nor clean. Shabby’s not chic when it comes to lingerie. Use a little extra care to keep your lace and silk bras and panties looking good.

If you live in the US then you've probably already seen a crow if you recognized it or not. The common crow has a distinctive if not dramatic appearance and a less than melodic sound. With this information you'll be sure to spot one.

It's summer again and it's time to get out of the house and there's no better way than with a fun game like some improvised baseball. You don't need a whole team of people all you need is a bat, a ball and another person to play with.
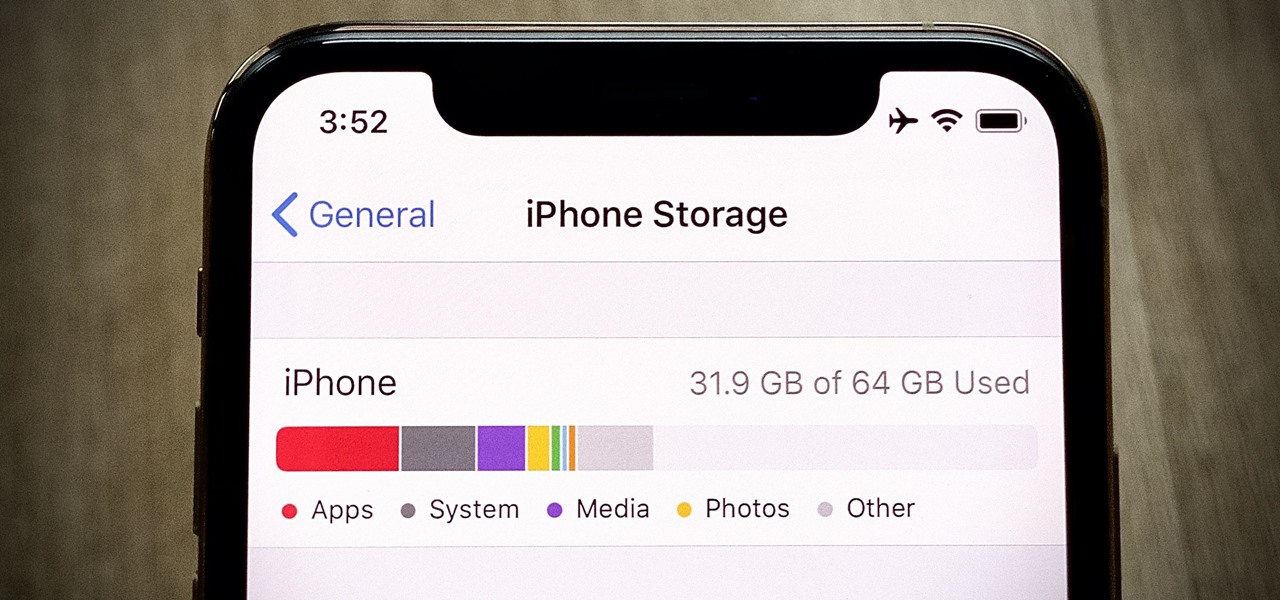
If you've ever run out of storage on your iPhone, you know how much work it can be to free up space. But all that work isn't necessary. Your iPhone can remove content automatically so you won't get any "storage full" warnings anymore — as long as you enable the option first.

You need a break from gloomy coronavirus updates. We all do. The unrelenting stream of doom and negative news is both helpful in terms of keeping ourselves and our families safe, but it also has the unfortunate effect of increasing our anxiety. When will this end? How bad will it get? Is there reason to be hopeful?
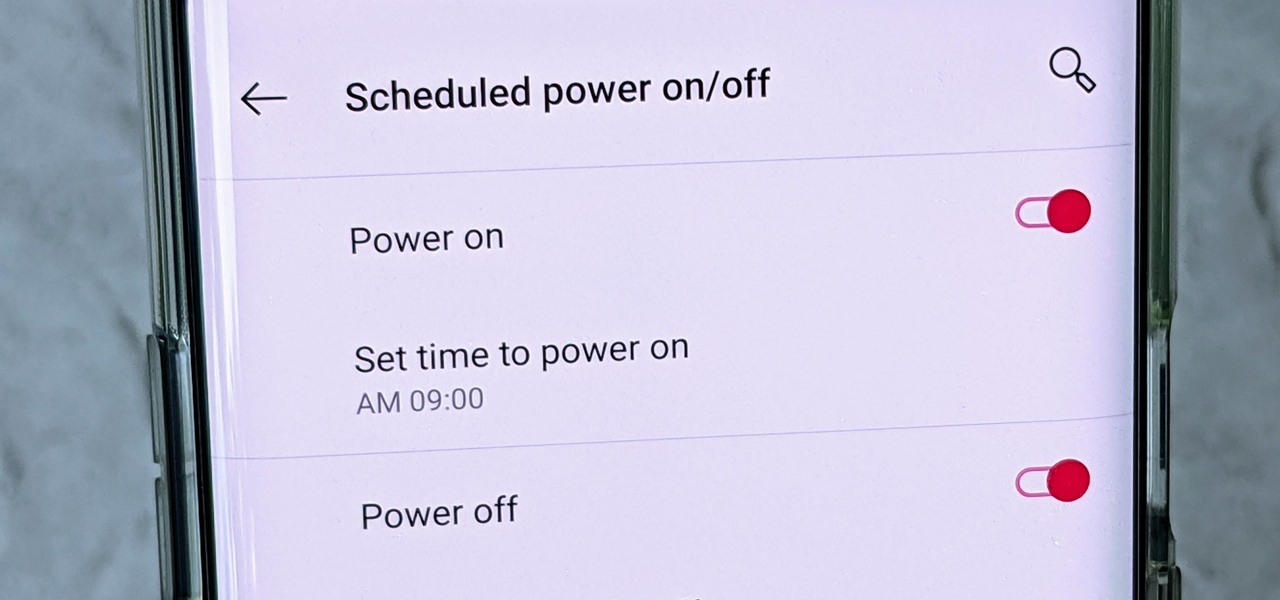
One of the more interesting power-related features for OnePlus phones is the ability to schedule a time to turn it, off then back on again. While OnePlus phones typically run blazingly fast, you can still benefit from the RAM clearing and process killing that a reboot provides. And since you can schedule this to happen overnight, you can wake up to a refreshed, restarted phone every morning.

All Kohl's wants for Christmas is Snapchat augmented reality. In conjunction with a holiday pop-up hosted in New York City from Nov. 7 through Nov. 10, Snapchat ran a sponsored portal lens available to targeted Snapchat users in the AR carousel. The experience gave users the ability to virtually transport themselves to the pop-up.

Android is moving away from navigation buttons. Even with the transparent navigation bar on the Galaxy Note 10+, it still takes up space on the screen that could otherwise be used to show content. What's great about the Galaxy Note 10+ is that you can remove it, without installing one app.
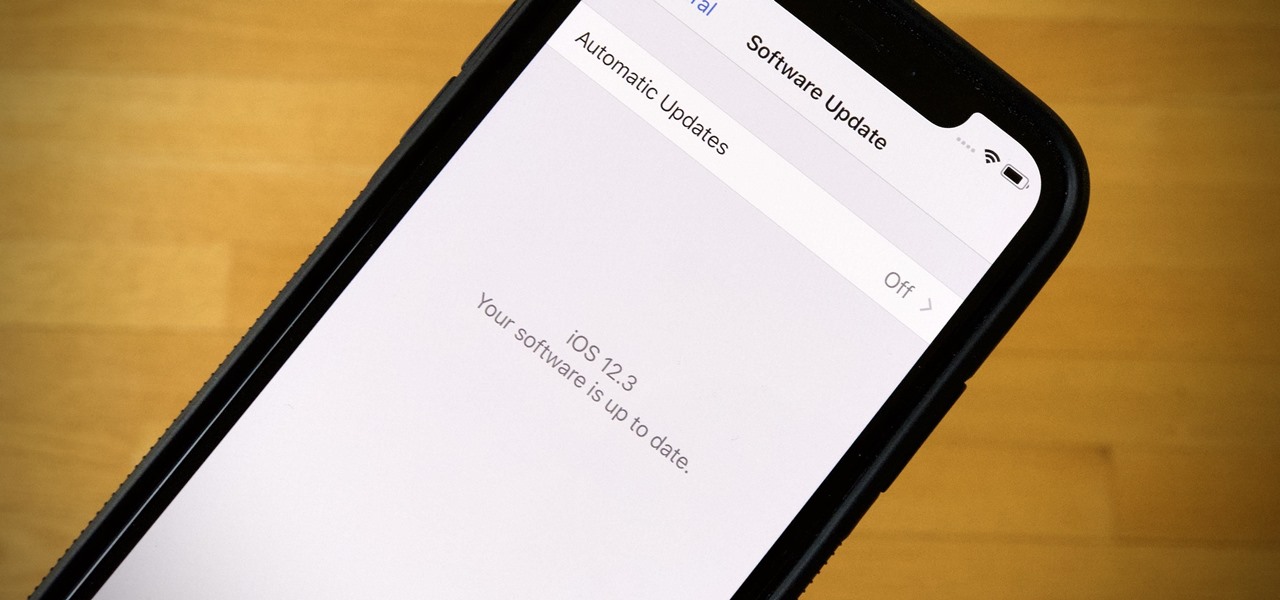
If you're a public beta tester, your Thursday just got awesome. Apple just released the first public beta for iOS 12.3 today, March 28. This update comes right on the heels of the first developer beta for 12.3, which itself released just one day ago. Thanks to that release, we know that this update contains a new TV app with updated layouts, Apple TV Channels subscriptions, a new logo, and more.

It's here! Apple just released the latest version of iOS today, Monday, March 25. Version 12.2 has seen six beta releases, spanning the course of fewer than three months. The new update sports 30+ awesome features, including new Animoji, air quality reports in Apple Maps, and AirPlay 2 support for compatible TVs, in addition to a slew of new UI tweaks and redesigns.

If there was a version of the Doomsday Clock for counting down the release of Microsoft's HoloLens 2, then the caretakers of that imaginary clock would move the minute hand to "one minute to midnight."

With CES in full swing, it seemed like Magic Leap would have little to announce at the major tech event, but it turns out that one of its partners has weighed in with a rather substantial update regarding the company.

The interactive displays of the future as visualized in Steven Spielberg's science fiction classic Minority Report, as well as the augmented reality interfaces used by millionaire playboy Tony Stark in the Marvel Cinematic Universe, are now closer to becoming reality in the military realm.

Developers opened their iPhones on Wednesday, Nov. 7, to find an update to the iOS 12.1.1 beta. Apple seeded developers the first 12.1.1 beta on Halloween, marking one week between it and the second beta. It's a quick update turnaround but in line with trends as Apple typically waits at least a week in between beta releases.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

The day has finally come. About eight months after unveiling Magic Leap One: Creator Edition, on Wednesday, Magic Leap made the device available for order through a reservation page on its website.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Looking to inject a little more processing juice into your HoloLens? Unity can fix you up with the Standalone Universal Windows Platform Holographic Emulation.

We learned during the LG G7 ThinQ announcement that AT&T would be carrying a new V series device, the V35 ThinQ. In the LG V35 ThinQ's press release, LG revealed its specifications but left out pricing and availability. Thanks to Project Fi, we now know its price tag, and you may not like it.

Royal wedding fever has officially taken over the media, and that obsession with the UK's latest marriage event has now extended to Snapchat, thanks to a new Lens from the Today Show.

Two weeks ago, Samsung took the wraps off their much-anticipated Galaxy S9 flagship. Preorders opened on March 2 with official retail availability scheduled for March 16. As usual, several of the US carriers have begun shipping the devices ahead of schedule. Last week, Sprint began shipping out devices to a few lucky customers. Today, T-Mobile appears to be joining the party.

Augmented reality developers are rapidly bringing science fiction tropes into the real world, with the latest example leveraging the TrueDepth camera on the iPhone X to emulate the cloaking technology made famous by movies like Predator and Marvel's The Avengers.

So you want to do Kendrick Lamar's "HUMBLE." in Animoji Karaoke, but you need the lyrics. Well, now you can see those rhymes spit out in augmented reality.

Augmented reality headsets with larger eye boxes than any device currently available could make their way to market by the end of next year if current timelines hold true.

The future is here with a new demo made with Apple's ARKit and LeapMotion. Typically, since ARKit works through your iPhone, in order to move augmented reality objects that are appearing on your screen, you have to drag them with your finger. However, developer Arthur Schiller is now playing around with how you can move augmented reality objects on your phone with gesture recognition, rather than by touching.

Love is the spice of life — it is also the microbes that couples share through sickness and in health, through the bathroom and in a hallway.

With the announcement of Google Glass Enterprise Edition last week, a literal behemoth entered the arena of companies serving augmented reality solutions to business customers. While Google Glass, with the backing of Alphabet, has the potential to be a disruptor, the field already has a number of players who have been in the game.

Obstetric tetanus in an unvaccinated Amish woman after a home birth has emphasized the need for preventative healthcare.

Princess Cruises' Coral Princess voyage disembarked in Fort Lauderdale on Saturday, March 18, after a 10-day cruise in which 182 people were sickened with symptoms of vomiting and diarrhea. According to federal health officials, a norovirus is suspected for the outbreak.

It's the bane of many a tech geek's existence that the customizability of Android software cannot be combined with the sleek design of the iPhone. A new Kickstarter project titled Eye, however, is looking to change that with a new iPhone case that allows you to combine the two.

Phuket, the island in Thailand typically associated with paradise and most recently, illegally-run hotels, now has a different problem—a stray cat with the claws of death.
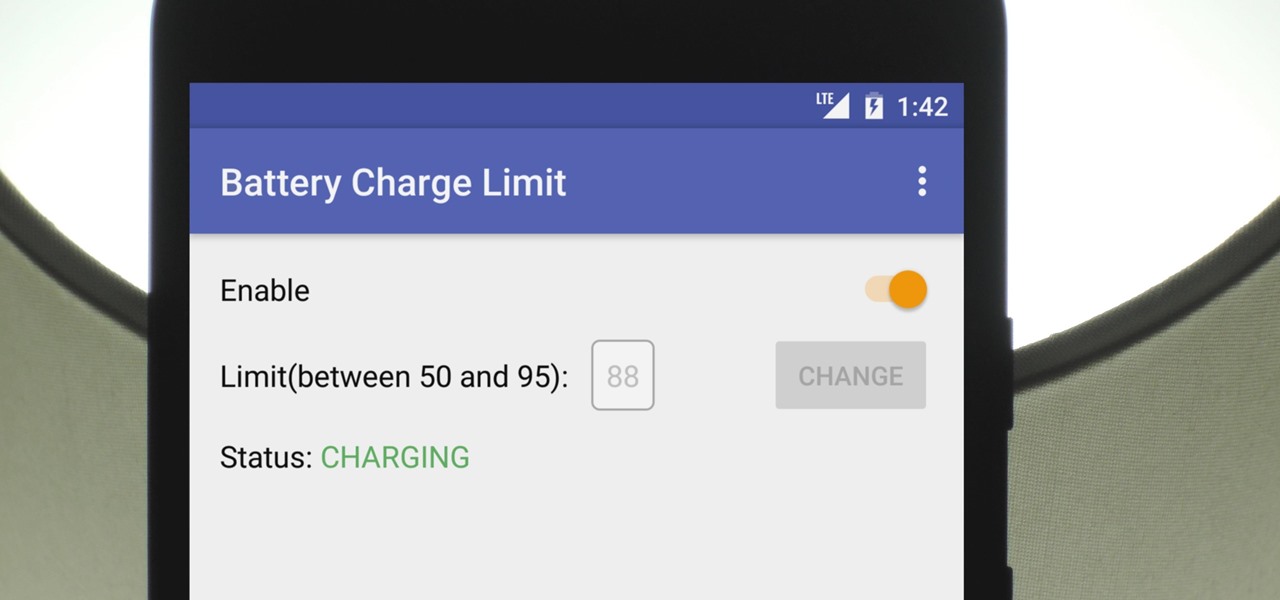
There's a lot of conflicting information out there when it comes to the best habits for charging a smartphone's battery, so let's clear some of that up right off the bat. Lithium ion batteries (the type used in most modern electronics) start to lose their ability to hold a charge over time, and the two biggest factors that contribute to this are excess heat and overcharging.

Students from Carnegie Mellon University's Entertainment Technology Center have been working on an augmented reality system to help teach music in a project called Music Everywhere.