The sprouts, they're alive! Alive, I tell you—aaaaaaliiiiiive! (Cue dramatic music.) It's true: sprouts are a living food, and they're packed with more nutritional benefits than some raw vegetables. It's easy and fun to grow your own sprouts from seeds, legumes, and grains. Plus, watching them grow is incredibly satisfying—you're bringing new life into the world (and onto your plate)!

Greetings my fellow hackers, In the previous article, I discussed briefly about ransomwares and their devastating capabilities. Devastating in a way that ransomwares are not only known to encrypt files but to also lockout some specific functions of the system and hold it up for a ransom.

When it comes to security, Android generally takes an all-or-nothing approach—once someone has your PIN, they're free to do just about anything, up to and including wiping your device. This is why you have to be extra careful to ensure that neither strangers nor friends are looking over your shoulder while you're entering your PIN.

Apple's MacBook line of laptops is quite famous for their extensive battery life, thanks to various technologies that Apple has utilized. However, all things must pass, and over time your MacBook's battery will degrade. Certain use scenarios can accelerate the degradation of the battery—from excessive usage to high temperatures to overloading the system—and this can all lead to the untimely obliteration of your battery.

Welcome back, my greenhorn hackers! In many cases when a computer, phone, or mobile device is seized for evidence, the system will have graphic images that might be used as evidence. Obviously, in some cases these graphic images may be the evidence such as in child pornography cases. In other situations, the graphic images may tell us something about where and when the suspect was somewhere specific.

Remember that feeling when you first took your smartphone out of the box, powered it on, then proceeded to futz around with it for the rest of the day non-stop? If you've owned your device for more than a year, chances are, that scenario is a distant memory by this point.

Welcome back, everyone! In this lesson, I'm going to go over the use of the echo function and variables, as well as basic syntax.

After months of speculation and sifting through rumors, Samsung finally unveiled its Galaxy S7 and S7 edge flagships, and they're pretty much what we had been anticipating. But just because there weren't any major surprises doesn't mean that it's not still exciting. Let's have a look.

As many of you know, I have been running a couple of series here on Null Byte about digital forensics called Digital Forensics for the Aspiring Hacker and Digital Forensics Using Kali. Although many readers have seemed to enjoy these series, just as many seem to be pondering, "Why should I study digital forensics?"

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

YouTube's massive user base comprises almost one third of all people on the internet, and collectively, users spend well over 100 million hours on the site watching billions of videos each day. Add it all up, and this means that YouTube is viewed by more people than any U.S. cable network—making it by far the favorite "TV station" of the internet generation.

I'll be the first to admit that I have a problem: I'm utterly addicted to tea.

Welcome back to a tutorial on malware. We'll be discovering a method to beef up our little trooper. Without further ado, let's jump right in!

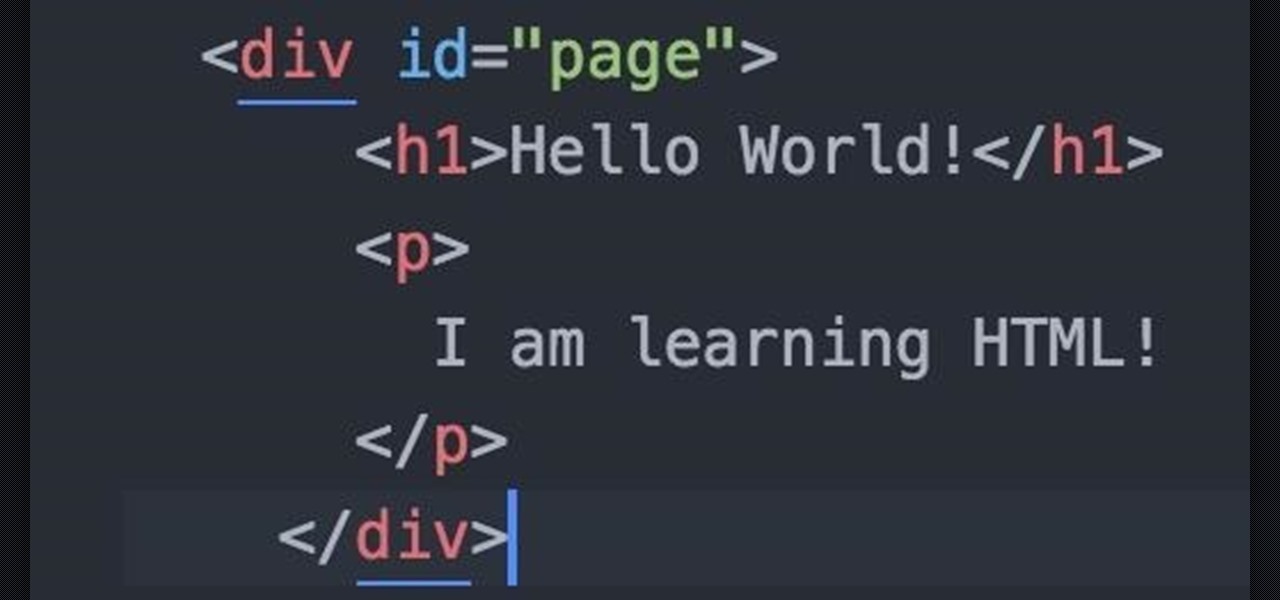
Welcome fellow Null-Byters! Sorry for the delay, this time of the year can be hectic for all of us. Hopefully this will not happen again. In this "tutorial" we will go over more styling and make our page look even better!

Welcome back! In the last training session, we covered logical and membership operators. We're going to switch gears and expand our knowledge of lists.

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

I'm not ashamed to admit it: I love Gatorade. It's probably from all of those times I watched Michael Jordan chug it during basketball games when I was a kid. But I'm not the only one that loves Gatorade—a large percentage of people who work out regularly choose to replenish their electrolytes with sports drinks.

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .

In the last iteration of how to train your python, we covered the concept of control flow and covered the booleans associated with it. Today, we'll be putting those to use as we discuss how to use if, else, and how to make conditional statements. So, Let's get started!

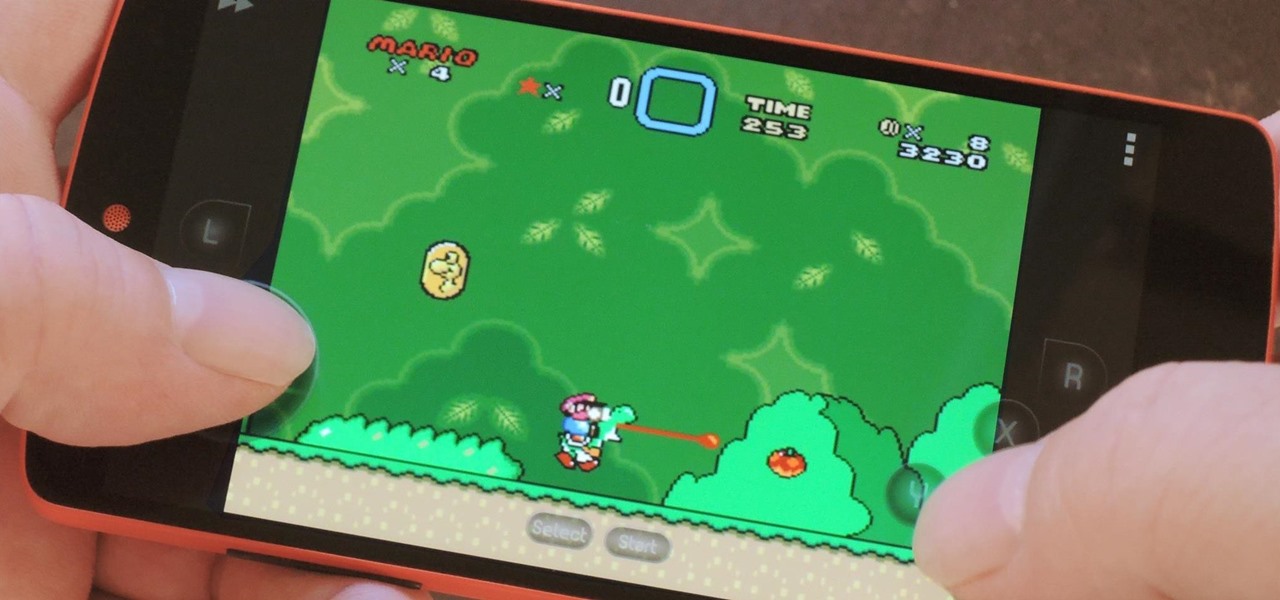
Smartphone games are getting pretty good these days, but they still can't beat the retro appeal of a good emulator. I mean, who wouldn't want to have their all-time favorite console and arcade games tucked neatly in their front pocket? Classics ranging from Super Mario Bros. to Pokémon can all be played at a silky-smooth frame rate on today's devices if you can just find a good emulator to run them on.

In case you didn't know, Android has an awesome hidden settings menu called "Developer options" that contains a lot of advanced and unique features. If you've ever come across this menu before, chances are you just dipped in for a minute so that you could enable USB debugging and use ADB features.

There are many hacks for increasing productivity, but so many depend on tricking your own mind or behavior. When it comes to motivation in the workplace, though, sometimes the space within which you work dictates how you behave and the work you produce. So if you want to increase your ability to get more done in a single workday while doing a better job, consider changing your surroundings in the following ways.

In response to the success of Apple Pay and an attempt to stave off the appealing Samsung Pay service, Google is completely revamping Android's mobile payments system. Instead of just using Google Wallet as an app to make payments with your phone, a new service called Android Pay, with an extensive underlying framework and API, will soon make its debut—and maybe even sooner than you'd think.

Well hello dear readers of Null byte, let me start off stating english is not my first language and they will be some grammar mistakes. This also is my first tutorial so don't hesitate to give me feedback :)

From our work life to our home life, we have an awful lot of projects, tasks, and activities that require more productivity than play. After working for an entire day in the office, no one wants to face even more that needs to be done at home.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

Protein powder is a fad in the same way that Justin Bieber's music is: you either love it, or you hate it. Everyone I know has a strong opinion about protein powder, ranging from "daily necessity" to "utterly useless."

I've never met a person who doesn't love French fries. And, to be frank, I have no desire to meet such a person.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

Whether it's terrorism or brain-hungry zombies you're neutralizing, first-person shooters are an awesome way to immerse yourself within a new world and kill some time with your iPad or iPhone. And with so many games available in this genre, we wanted to show off ten of our absolute favorites.

At last, what you all finally waited for! Hi! Fire Crackers,

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

Canned pumpkin is something I always stock up on and keep in my pantry, because it's endlessly useful when cooking or baking. Sweet, creamy, and mild, pumpkin can be folded into baked goods and savory dishes with ease.

One of the great joys of cooking is taking the most basic of foods and preparing them in new and exciting ways. About two years ago, my wife opened my eyes to a delicious staple of Indian and Moroccan cuisine that is made in a very elementary way, the preserved lemon.

Job interview success can be a difficult thing to measure. Is confidence a job-winning trait? Or were the interviewer's questions not answered as fully as they had hoped? Maybe you weren't sure how your big, happy smile went over with such a formal setting.

We are living in a golden age of craft beers. Originally invented by the ancient Egyptians, every culture now has its own tastes regarding beer. The process of making beer is so multi-faceted, it's a miracle that any gets made at all.

Injustice: Gods Among Us is one of the most popular games to come out over the last couple of years. It was a hit on video game consoles, and it's got a solid 4.5 rating on both Google Play and the iOS App Store, with almost 2 million people rating the game combined.

The first few times I posted on some of the Android forums out there, I asked things like "Does anybody how I can make my phone do this or that?" Without fail, the responses to these types of questions were always one word—Tasker.