Learn how to add a new contact to the contact list in BlackBerry phone. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.
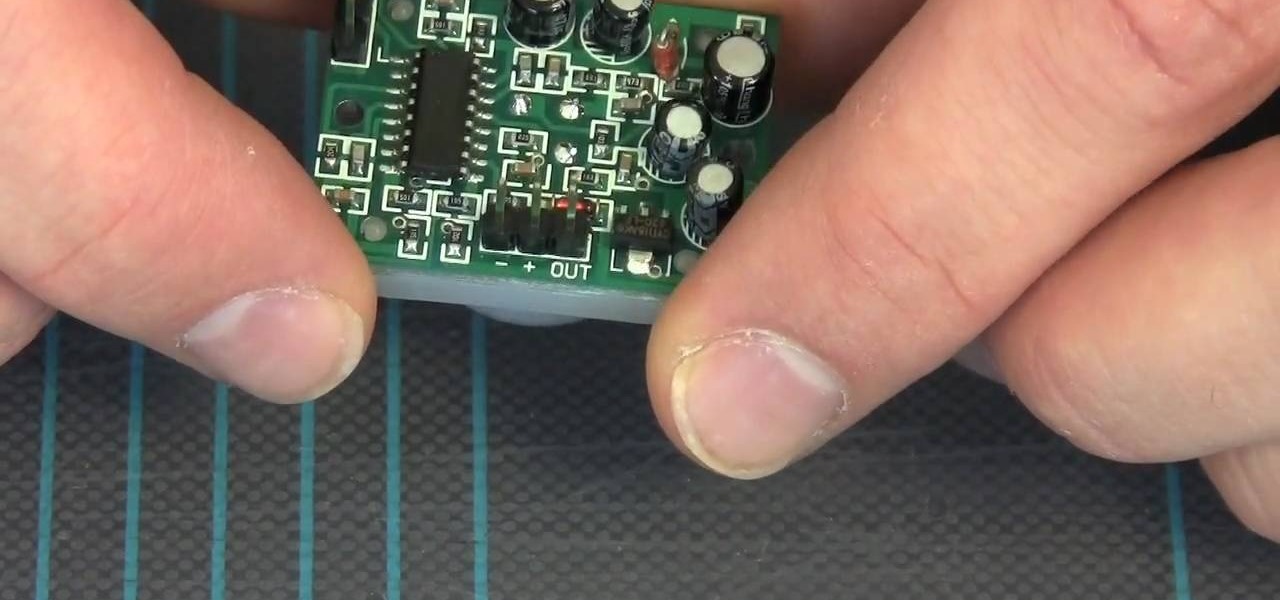
Want to build your own infrared motion detector? It's easier than you think! So easy, in fact, that this video tutorial from MAKE can present a complete overview of the build in under five minutes! For more information, including a full list of materials and detailed, step-by-step instructions, and to get started building your own passive infrared motion alarm, take a look.
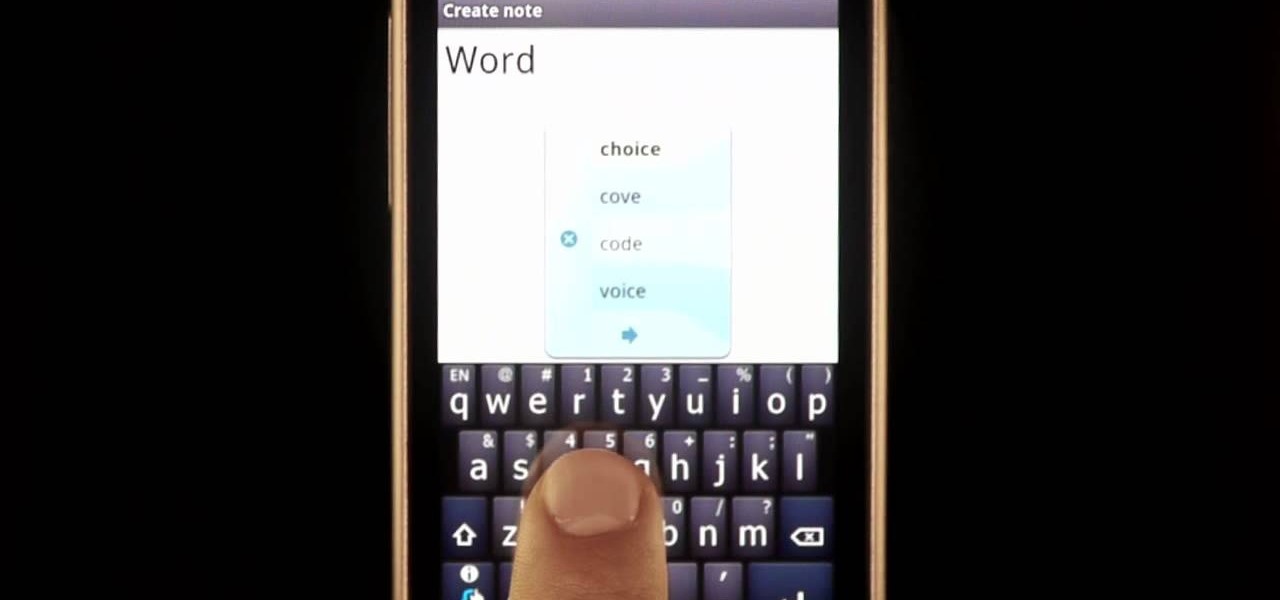
Sometimes there is more than one option for a particular finger Swype. When this happens, Swype will give you a list to choose from so that you can pick whichever word you were hoping to use. Swype is the fastest way to send texts and e-mails available and with a bit of practice you will have it mastered. Just think of Swype as the T9 of 2010 and you will catch on fast.

Want to make kalua pig for your next backyard luau without going whole hog, so to speak? Never you fear. This free video cooking lesson demonstrates an easy-to-follow Hawaiian-style pulled pork recipe. No imu required. For detailed, step-by-step instructions and a full list of ingredients, watch this tropical culinary tutorial.

In this video richpin explains to us how to remove the inside rear passenger-side door panel on a Nissan Altima. He doesn't explain why you would want to do this, but if you feel compelled to, herein you will find the most detailed instructions you could ask for. Here is a list of the readily available tools that he uses:
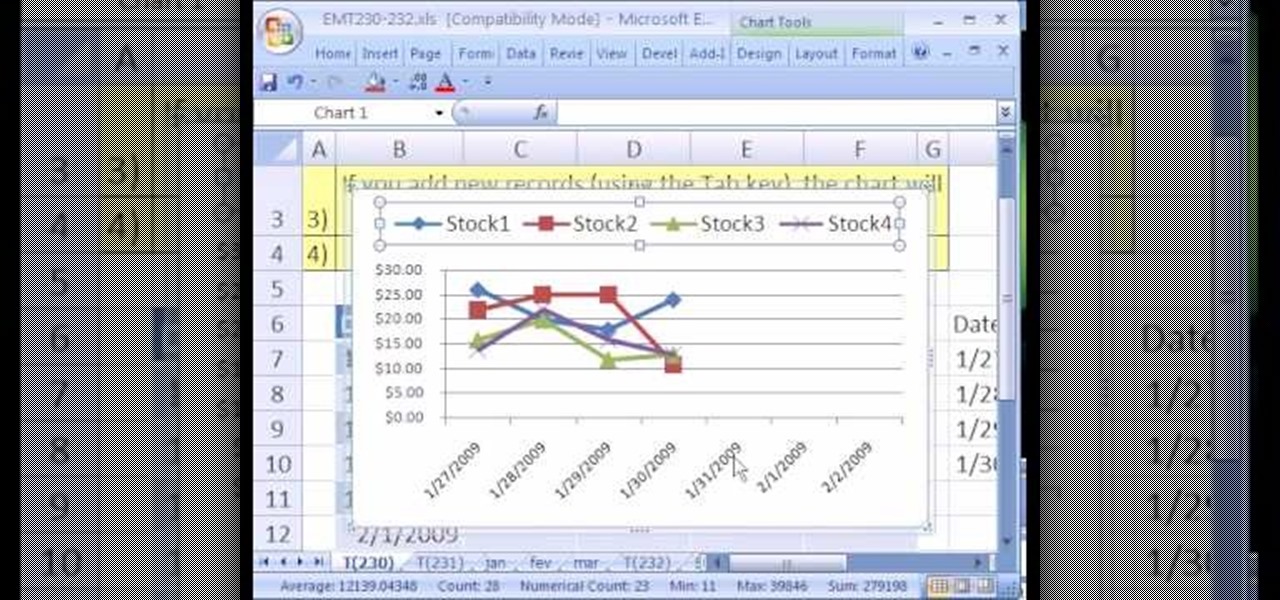
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 230th installment in their series of digital spreadsheet magic tricks, you'll learn how to use the Excel List Table feature to make a dynamic stock price line chart.

Buttermilk is a great thing to have around in your kitchen. Unfortunately, most of us don't have buttermilk on our regular grocery list, so those buttermilk pancakes will have to wait for another day. Think again! You can easily make tasty buttermilk alternatives with common refridgerator items. This video will show three easy ways to make a buttermilk substitute.

Using the Cydia App, you can delete individual calls in your recent caller list. This enables you to delete single calls, line by line, instead of having to clear your entire recent call list.

This square video teaches the following square dance calls on the mainstream list: Promenade Full 3/4, Grand Square, Half Sashay, Roll Away with a Half Sashay, Ladies In, Men Sashay

This square dance video teaches the following square dance calls on the mainstream list: Tag the Line, Half Tag the Line, Recycle, 8 Chain 4/Thru, Spin Chain Thru

This square dance video teaches the following square dance calls on the mainstream list: Spin the Top, Alamo Style Wave, Wave Balance, Circulates (Column, Box, Split, 1 1/2), Chain Down the Line, Sweep a Quarter

This square dance video teaches the following square dance calls on the mainstream list: Left Square Thru, Cast Off 3/4, Walk & Dodge, Pass to the Center, Dixie Style to an Ocean Wave

This square dance video teaches the following square dance calls on the mainstream list: Back Track, Lead Right, Circle to a Line, Bend the Line, All Around your Left Hand Lady, See Saw

This square dance video teaches the following square dance calls on the mainstream list: Right & Left Thru, Courtesy Turn, Box the Gnat, Wrong Way Grand, Ladies Chain (Heads, Sides, 3/4, All)

This square dance video teaches the following square dance calls on the mainstream list: Allemande Left, Right Hand Turn (Turn Thru), Right & Left Grand, Weave the Ring, Star Left/Right

This square dance video teaches the following square dance calls on the mainstream list: Square Thru (2,3,4), Wheel Around, Star Thru, Slide Thru.

This square dance video teaches the following square dance calls on the mainstream list: Do Paso, Thar, Allemande Thar, Slip the Clutch, Shoot the Star, Wrong Way Thar.

This square dance video teaches the following square dance calls on the mainstream list: Ocean Wave, Swing Thru, Run (Boys, Girls, Centers, Ends), Pass the Ocean, Trades (Boys, Girls, Ends, Centers), Dive Thru, Extend.

This square dance video teaches the following square dance calls on the mainstream list: Cross Run, Left Swing Thru, Single Hinge, Separate, Trade By, Wheel & Deal (Lines of 4).

This square dance video teaches the following square dance calls on the mainstream list: Touch a Quarter, Scoot Back, Flutter Wheel, Reverse Flutter Wheel.

This square dance video teaches the following square dance calls on the mainstream list: Circulates (Ends, Centers, Couples, All 8), Ferris Wheel, Zoom.

This square dance video teaches the following square dance calls on the mainstream list: Veer Left/Right, Wheel & Deal (Two Faced Line), Ladies/Gents Promenade.

This square dance video teaches the following square dance calls on the mainstream list: Pass Thru, U Turn Back, California Twirl, Partner Trade, Star Promenade.

This square dance video teaches the following square dance calls on the mainstream list: Couples Trade, Couples Hinge, Folds, Cross Fold, Centers In/Out, Split the Outside Couple, Double Pass Thru, Cloverleaf.

This simple tutorial takes you through the process of creating a widget from any list of videos from http://www.WonderHowTo.com. These customizable widgets can be created in various sizes and colors and then added to your blog or website. Enjoy.

This how to video has the Ultimate Cheese Ball recipe. It's as beautiful as it is delicious. This recipe uses a few different types of cheeses, but it's as simple as any recipe. Serve this cheese ball with crackers and it will be a big hit at your next party. Its a perfect appetizer at holiday and Christmas parties or even as a Christmas dinner recipe. Watch and learn how it is prepared.

This video walks through basic security configuration for a WRT54G Wireless Router. Also provides a default password list.

David Strom shows you how to pick from aong Google Groups, Mailman hosted by EMWD.com, and iContact and how to get started with your own mailing list

Bring your favorite software, files, and settings with you on a USB drive

Are you at the bottom of the donor list? Making a movie that calls for a fake beating heart? Then you need to watch this episode. Erik from Indy Mogul will show you how to make a bargain chest ticker for less then $37 dollars

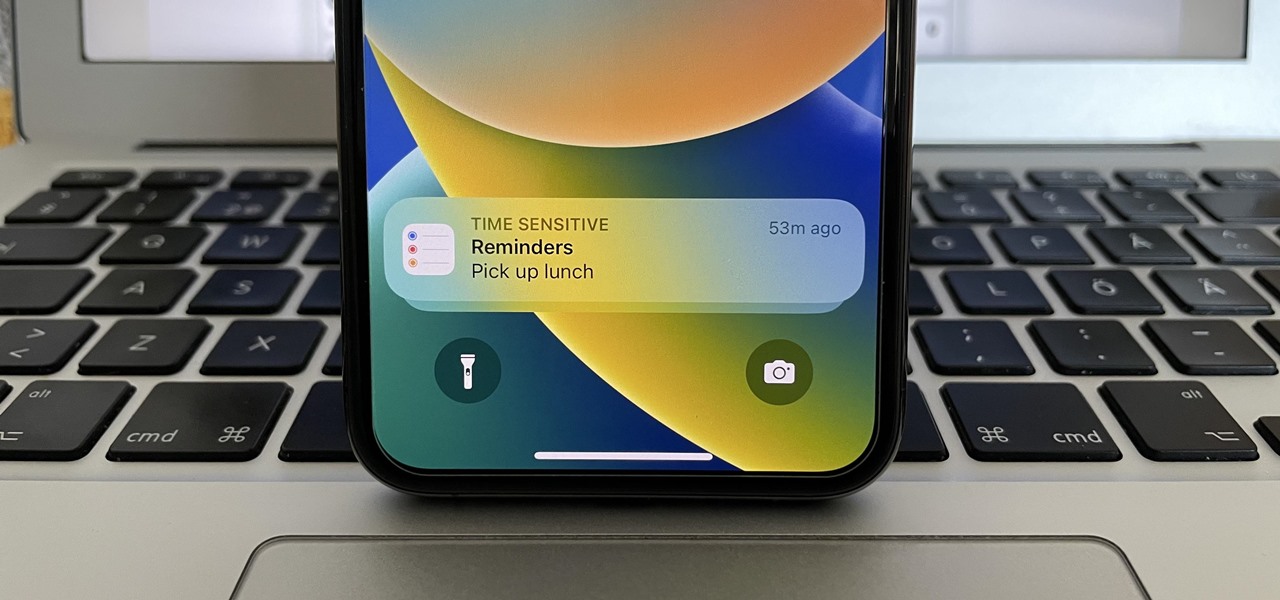
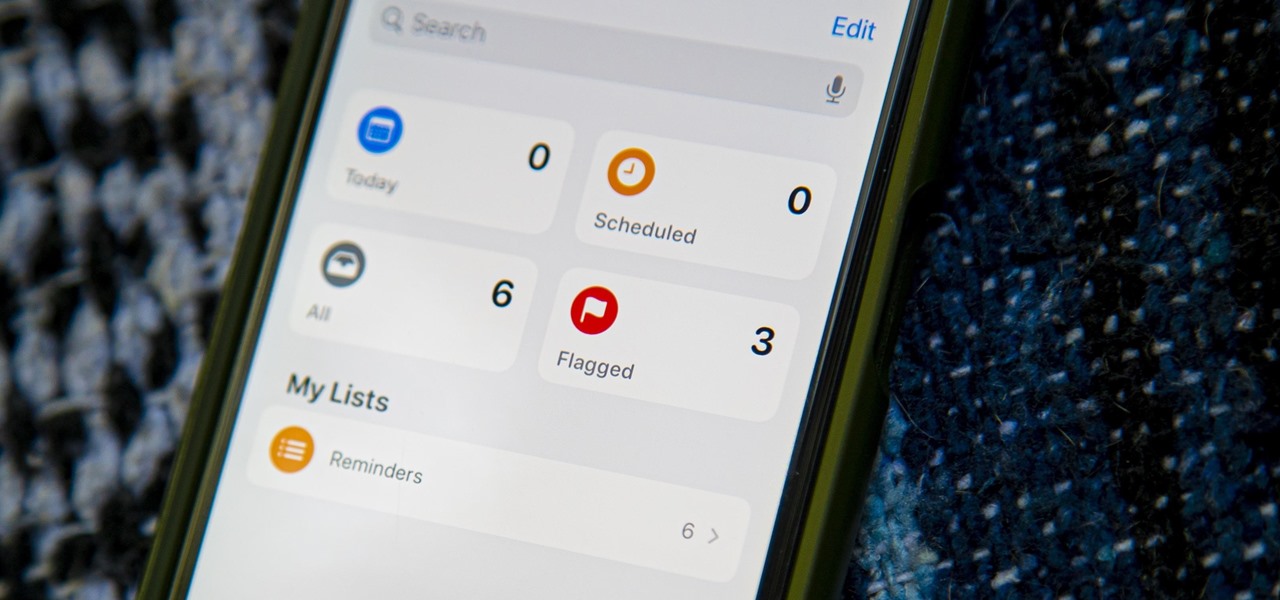
Apple just upgraded its Reminders app for iPhone, and there are some powerful new tools and improvements for task management that'll make you wonder how you ever lived without them.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

One of the coolest things about Android is the massive development community behind it. These developers keep on cooking up new things even after official support has stopped for an older device. It breathes new life into somewhat forgotten devices, which is always great news. With Android 10 out, it's time to see what phones will get the custom ROM treatment.

Reminders may have received the biggest update out of all the native Apple apps on iOS 13. Among other things, the new Reminders app now comes packed with smart lists to make it easier find things, and a flagging feature to help you better manage your most important reminders.

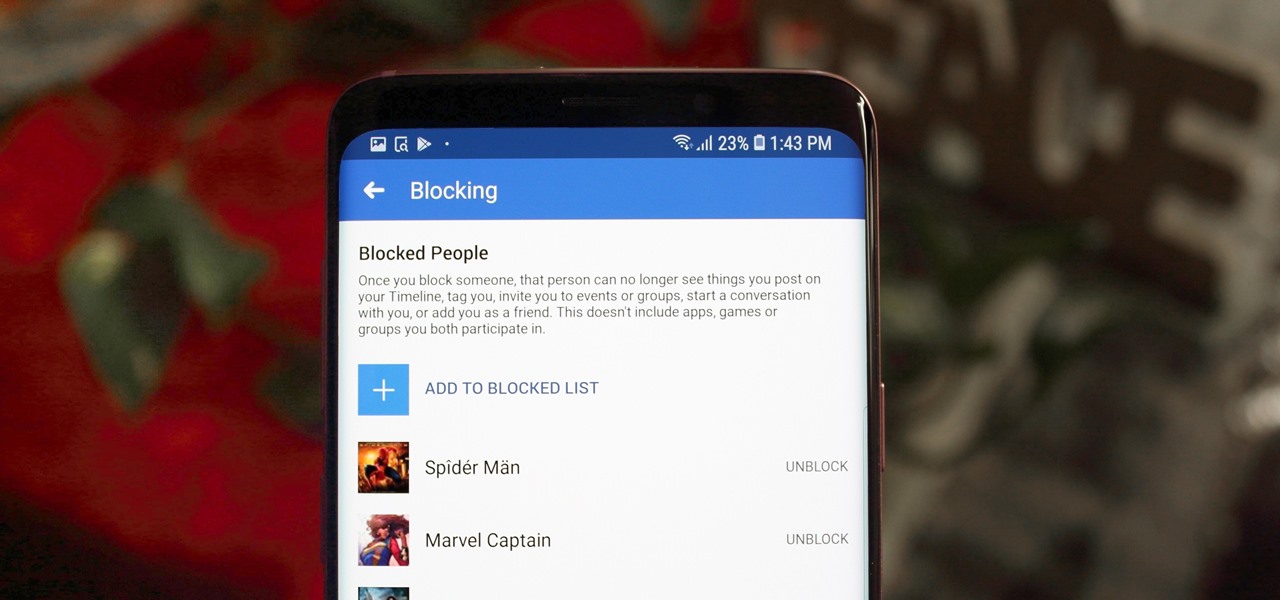
Whether it's an ex you can't stand, that annoyingly political friend of a friend, or good old fashioned trolls, the block feature on Facebook can be a great way to de-stress your feed. It will keep people from contacting you, and it will also prevent them from viewing your profile altogether. It's not just a tool for the full desktop website — in fact, the blocked list is easy to manage right from your phone.

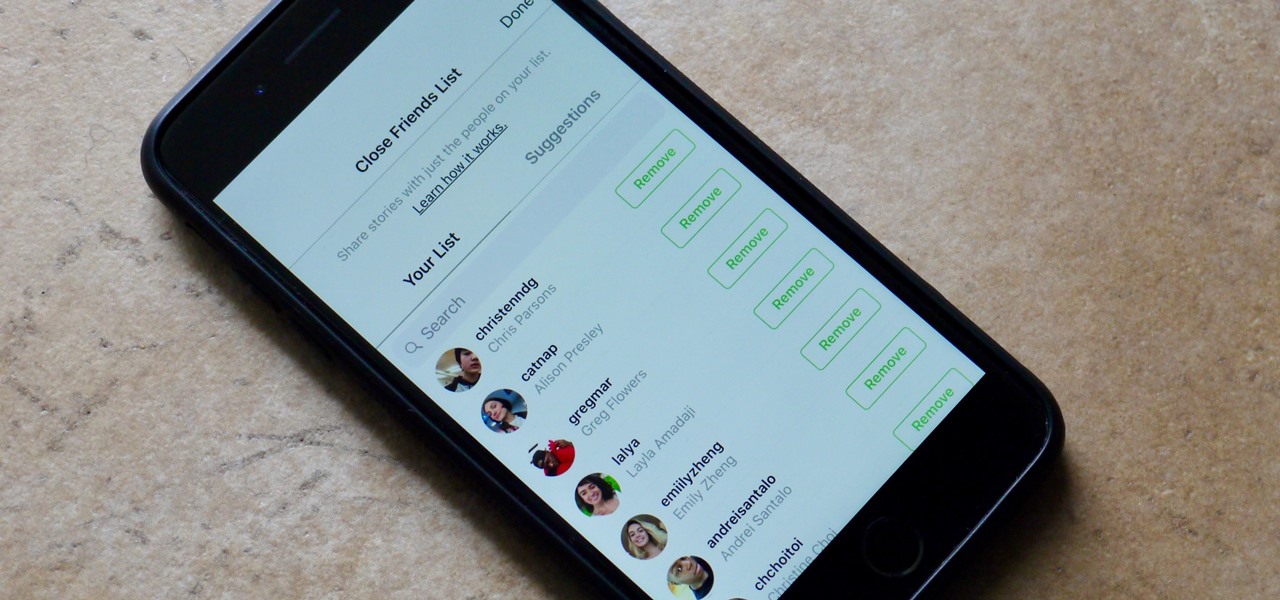
Stories make sharing your day-to-day highlights fun on Instagram. However, other than choosing who to hide stories from, by default, stories don't have much privacy control, especially if your Instagram account happens to be public. Instagram recognizes this flaw, which is what its "Close Friends List" is all about.

It appears a privacy lawsuit that began five years ago is about to come to an end, and you might get some money out of it.

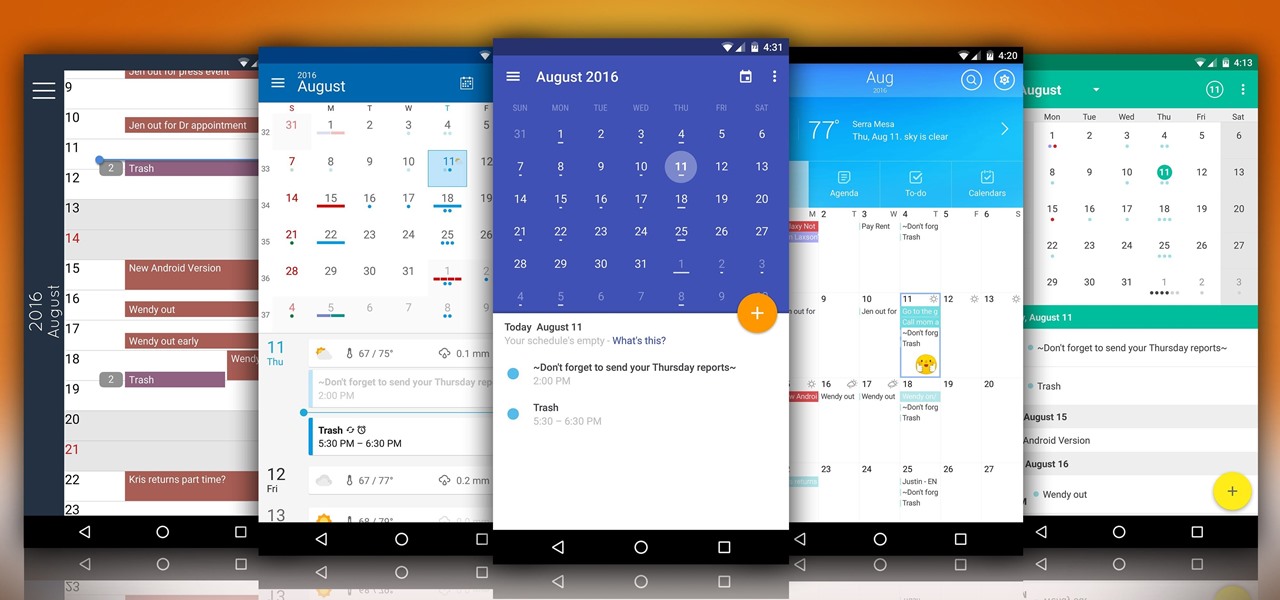
Whether you use Google Calendar, Exchange, iCloud, or any other service, you need a good Android calendar app to keep you organized on the go. For many folks, the obvious answer was always Sunrise Calendar, but Microsoft purchased the company behind this awesome app in a classic acqui-hire move, and now, Sunrise has officially been shut down.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

proxyFinderEnterprise is a tools for find proxylist . in this topic you learn how to use this tools for find a proxy list .