During our high school years, one of us (hint: her name starts with a B) worked at Cold Stone Creamery. She loved working there, and from this love emerged a fascination with adding creative ingredients to plain ol' vanilla ice cream.

You're only as smart as your communication skills allow you to be, as other people will simply never know your inner genius if you can't effectively express yourself. Regardless of the medium—be it a Facebook post or even a simple text message—this fact remains true.

Amazon has completely changed the way we purchase household items, to the point where many of us haven't visited a big box, brick-and-mortar store like Walmart or Best Buy in years. And when you think about it, all of this success comes down to two main factors—convenience and price.

It seems like Microsoft has finally come to the realization that their Windows Phone mobile operating system is probably never going to compete in today's smartphone market. Why do I say that, you ask? Because they've recently started to embrace the more popular platforms by releasing some quality iOS and Android apps.

Reddit announced this morning, April 7th, that it has finally released an official mobile app. You can get it on Android and iOS.

Welcome back, my novice hackers! As many of you know, recon is crucial to a successful hack/pentest. In most cases, hackers spend more time doing good reconnaissance than actually hacking. Without proper recon, you are simply guessing at what type of approach or exploit is going to work and, as a result, your time is wasted without any useful outcomes.

If you're gluten-free, on a diet, or just cutting the carbs like me, eating a sandwich can be a dangerous game. There are traditional alternatives such as lettuce or egg wraps, but they have their drawbacks: they can't hold as many ingredients, they can be lack flavor when raw and un-rendered, and it's hard to layer the toppings and condiments to create your perfect bite.

Here I will show you how to properly dig information on the web that has already been published, you just dont know it.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

Whether you're anxious to tune into this Sunday's Super Bowl 50 to see Cam Newton and the Carolina Panthers take on Peyton Manning and the Denver Broncos, or to see if you win some money on your silly prop bet, or just want to tune in for the commercials, there are a handful of ways to catch the Big Game without an antenna or cable/satellite subscription. When & Where

Eating out is great, but being able to cook the delicious ethnic foods you eat at restaurants is even better. It may seem daunting to put together a bunch of ingredients with which you might not be familiar (some with names you've never even heard of!), but with the guidelines below, you'll be making your own versions of ethnic favorites in no time.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

When it comes to cooking grains, there is an unspoken rule to never stray from the exact measurements. Consulting charts for the proper ratio of liquid to grain is considered the difference between crunchy, undercooked pebbles and a mushy mess... that is, until now.

Hello fellow Nullbytiens, I'm Washu, a long time commenter but first time poster. Today we'll be making an IRC bot, if you haven't seen OTW's post about the new IRC channel I would encourage you to go check it out. He does a good job at explaining what IRC is and how to get set up.

Cast iron pans are a timeless treasure—they're an essential kitchen tool that will stand the test of time, and no home kitchen is complete without one. However, they do have a reputation for being difficult to care for... with arguments both for and against regular seasoning. In 2010, a blogger named Sheryl Canter claimed that she found the best way to season a cast iron pan that would keep the cast iron from rusting... or requiring re-seasoning! And after a few hands-on test by Cook's Illust...

Ready or not, the USB-C cable is about to take over your electronics. The new industry standard is fully reversible and packed with enough power to serve as a laptop charger or an HDMI cable, so it actually has the potential to replace every cord, wire, and connector in your house. In fact, the conversion has already started: The latest MacBook, Chromebook Pixel, and Nexus phones are sporting USB-C connectors out of the box.

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

Welcome back, my tenderfoot hackers! As most of you know, I am strong advocate for using Linux as a hacking platform. In fact, I would say that without knowing Linux, you will never become a professional hacker/pentester.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

With new messaging services being pushed out constantly, it can be a pain trying to keep track of them all on your Android device. We had previously shown how to stay on top of them all with a unified "inbox" app, but that still requires you to have each individual app installed. While looking for a true one-stop messenger, I came across Disa.

Few things are as frustrating as grabbing food from the fridge just to discover that your leftovers have gone bad. When it comes to cheese, you may have taken every last precaution to keep it as fresh as possible—sealed plastic containers, saran wrap, parchment paper—but to no avail.

Last time in how to train you python, we covered the basics of variables and output. While we were covering variables, we talked briefly about strings. "String" is just a fancier way of saying "Word". A string is simply a set of characters encased in quotations, this lets python know that it is a word. Sometimes when we do things with strings we'll need to change them in order to do something. Python is case sensitive, for example "Null-Byte" is not the same as "null-byte". This is where mani...

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.

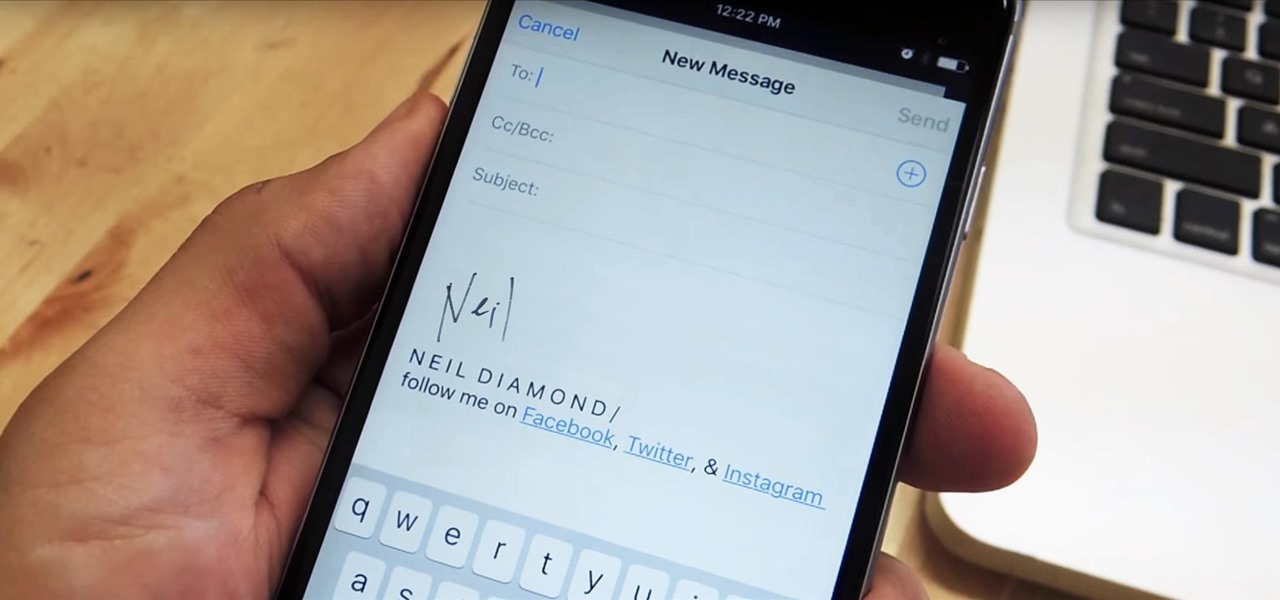
Emails sent from an iPhone, by default, are signed "Sent from my iPhone," which almost seems like a disclaimer in case the email has spelling or formatting errors. If your goal is to look professional while corresponding with coworkers or potential employers, then you're better off removing the signature completely and just typing your name out.

At first glance, caviar doesn't seem overly appealing to the masses; not very many people would be willing to spend upwards of $1,000 on a tiny spoonful of salty sturgeon eggs from the Caspian Sea. Caviar truly is the ultimate symbol of luxury and fine dining.
It's been a while, since I have just started High School. I have put a hiatus to my pentesting for a few weeks, and now, I am making a return. I have taken time to read about code, (even did a research article analysis on how humans can write "beautiful" code and something like that) and pentesting, but never made a full return. I will be occasionally coming back for a while.

Computer system authentication is critical to keeping systems safe from unwanted users, intruders, and abusers. Basically, authentication is the process of the potential user proving they are an authorized user.

Like a strong-tasting cup of joe, but want more caffeine out of it? Start double brewing your coffee. To paraphrase a big fan of the double brew process on Reddit, it'll make you feel like you can throw an orange at 60 percent the speed of light. It's that strong. Really.

Let me start by saying something controversial: I despise the gluten-free fad. I think gluten is delicious (I go through at least two loaves of bread a week, with a healthy dose of pretzels and pasta in there as well), and I think many of the health myths surrounding gluten are either fabricated or hyperbolic.

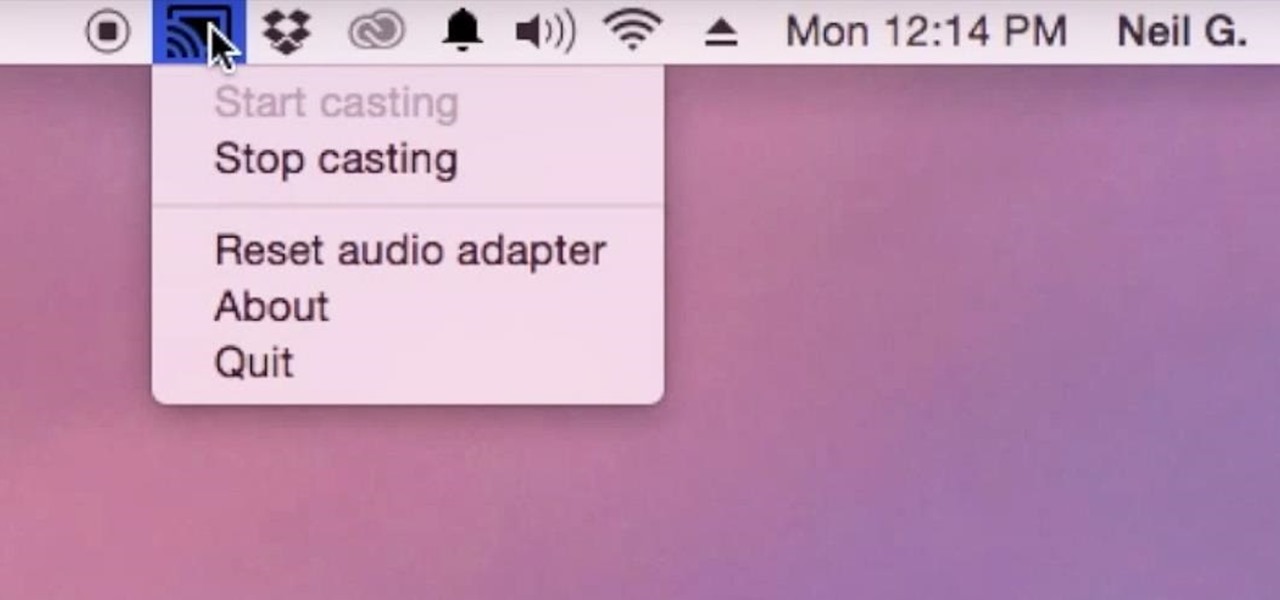
Although I know it will never happen due to Apple and Google's tempestuous relationship, I sometimes wish I could cast iTunes or Apple Music from my Mac to Google's Chromecast. When you don't have speakers to blast your music, the television is a great alternative to amplify your music.

One of the coolest features in modern smartphones is their Bluetooth connectivity. This is how two digital devices can communicate with one another—sending data like your phone call audio or your favorite song—all while using up minimal battery life.

Cooking on a budget isn't always easy, but there's a silver lining: it can be really fun. Ever since I started supporting myself I've enjoyed going shopping, finding the most affordable items, and learning how to make the most of them. Sure, sometimes I wish I could afford to buy a filet mignon and some morel mushrooms every night, but there's a different kind of enjoyment that comes from being able to turn a few dollars into a gourmet meal. For me, that means starting with cheap meat, and af...

In my opinion, there is nothing in the culinary world as satisfying as cutting into a steak, and seeing that you've cooked it to perfection. Even if you're one of those bizarre people that prefers their steak medium or well done (hey, no judgement... okay, fine, a little bit of judgement), it's culinary heaven when you realize that you achieved the perfect doneness on your steak.

Being born with a sweet tooth and Japanese blood, my desire for dessert-style sushi is practically written into my DNA. At once delicious and adorable, these one-bite delights are the perfect way to conclude a meal. They're also a killer snack. Featured below are: 1) the Banana Nutella Nut Roll; 2) the Strawberry Kiwi Roll; 3) Mango and Sweet Rice Nigiri.

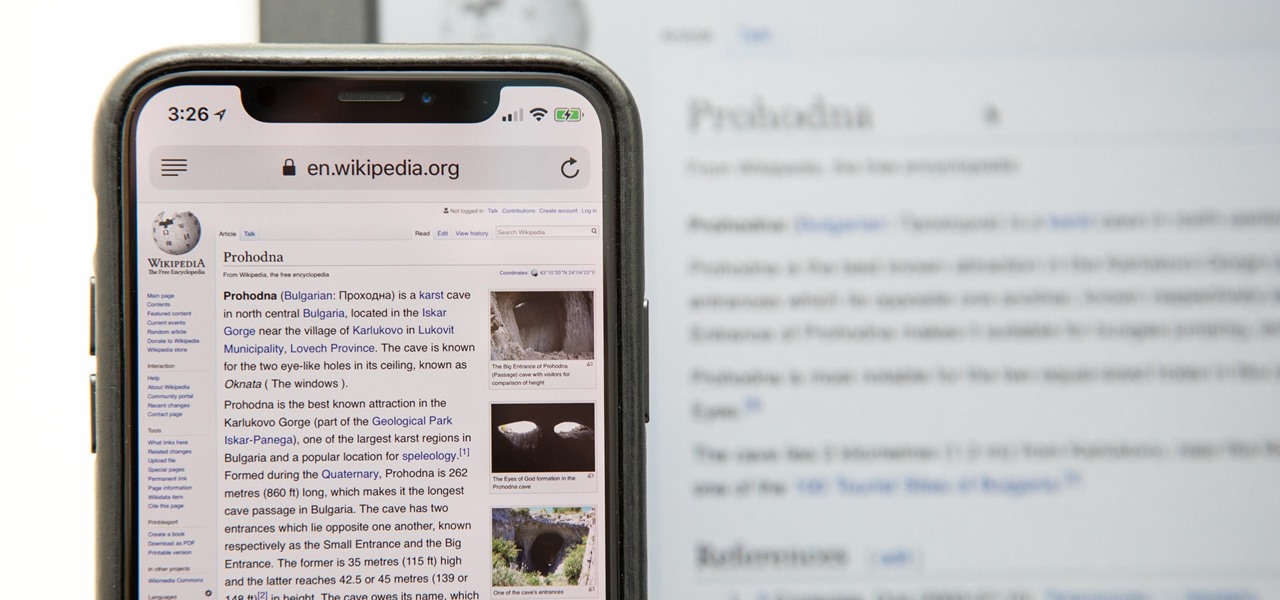
Having websites coded for mobile browsing is great for small screens, but if you have a Plus model iPhone or even the iPhone X, desktop versions of websites might show you more of what you want. Plus, there's the case of poorly designed mobile websites, where the desktop view is clearly the better option with more functionality and features. Luckily, asking for desktop sites in Safari is simple.

Independence Day is right around the corner, and that means three things: fireworks, cold beer, and great food. I always love to cook festive foods for the Fourth of July, and I don't just mean the classics, like grilled chicken and brats. I mean foods that celebrate the Stars and Stripes: foods that are red, white, and blue.

Brought to you by Purdy Paints The art of painting requires excellent tools. And with so many options on the market, it can be hard to find a brand that works for you and your DIY project. That's where Purdy comes in.

Disclaimer: All information in this tutorial is for entertainment and educational purposes ONLY. You pesky teenagers.

Whether it's terrorism or brain-hungry zombies you're neutralizing, first-person shooters are an awesome way to immerse yourself within a new world and kill some time with your iPad or iPhone. And with so many games available in this genre, we wanted to show off ten of our absolute favorites.

There may be no kitchen appliance as controversial as the garlic press. Professional kitchens and many avid cooks despise it, while others staunchly defend it.