With the S9 and S9+ upon us, you maybe wondering if it's time to retire your aging Galaxy and either sell it or do a trade-in to get Samsung's latest flagship. Before you do, however, it's important to make sure that all its components — most notably the sensors — are working fully in order to avoid potential headaches.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

So, you want to install the Oreo beta on your Galaxy Note 8 but you're not sure if it's stable enough. It is a beta, of course, so waiting until others have tried it out sounds safer. Well, over the past five days, I've used the T-Mobile version as my daily driver and there are a plethora of new features, as well as a few glitches. Let's take a look at the bugs, performance, and battery life.
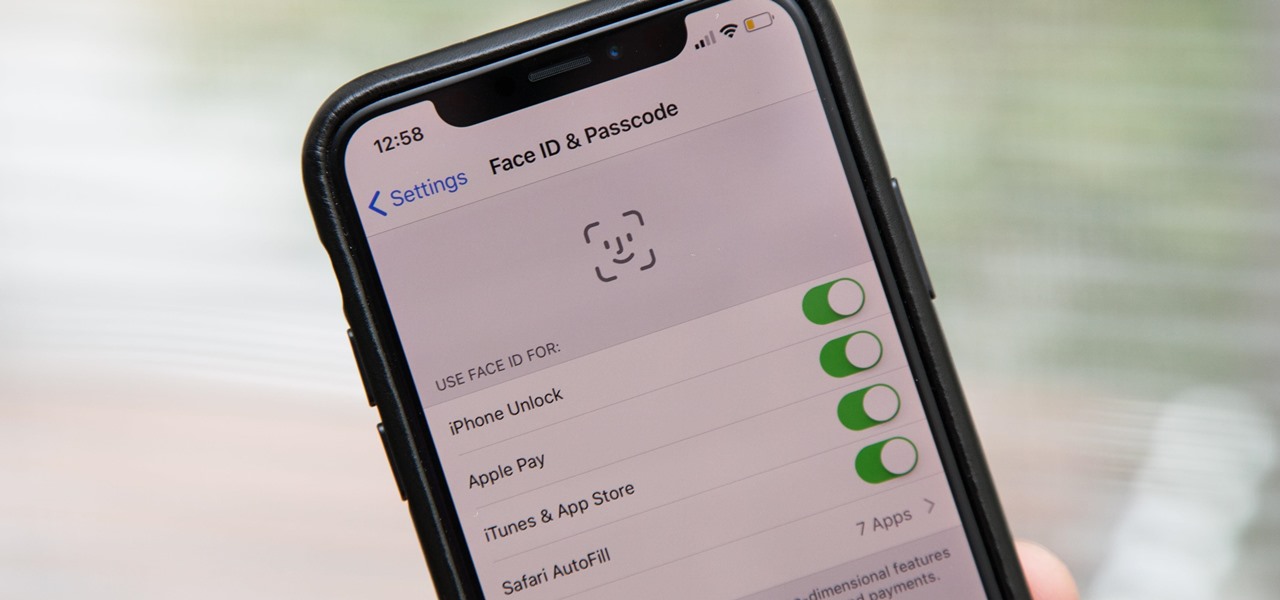
Aside from the second-generation iPhone SE, all new iPhone models since the iPhone X have had Face ID instead of Touch ID as the biometric authentication technology. While Touch ID can be touchy, Face ID is not without its own issues. If you can't get Face ID on your iPhone to recognize your face and unlock your iPhone, there are plenty of things you can try to get it working again.

Now that Fyre Festival co-founder Billy McFarland is charged with fraud, this is the perfect time to list off those top 15 influencers who promoted tickets to the disastrous event to their loyal followers, right?

If you want to share a video to Stories — but it's over 24 hours old — it may seem like you can't, but there's actually a simple hack on how to do just that.

Alzheimer's disease — an irreversible, progressive brain disorder — is the sixth leading cause of death in the US and more than afflicts 5 million Americans. As if those numbers aren't scary enough, the Centers for Disease Control and Prevention expect that number to nearly triple by 2050.

Even before we are born, our immune system is hard at work. New research shows how the developing fetal immune system takes advantage of the time and opportunity of gestation — in the presence of mom's cells and tissues — to develop a sense of self.

Since I recently had this problem and fixed it, I might as well share the solution. This is actually REALLY simple to fix but will impact your cards' performance.

Why, for the love of God, do people keep inventing ridiculous devices that make the simplest things more complicated in the name of convenience? This may be a rhetorical question that will forever go unanswered—because these crazy gadgets just keep rolling out, one after the other.

Greetings my fellow aspiring hackers, It's still Christmas and we have a lot of things and hugs and kisses and ... to share ( you know the things that you do ). I have never done this before but I just felt to encourage you on the quest for knowledge, security and defence, skills and a whole lot more that comes out as a result of pursuing hacking. What we mean by hacking on this forum is White hat Hacking and OTW has great articles on it and I don't need to explain myself on that one.

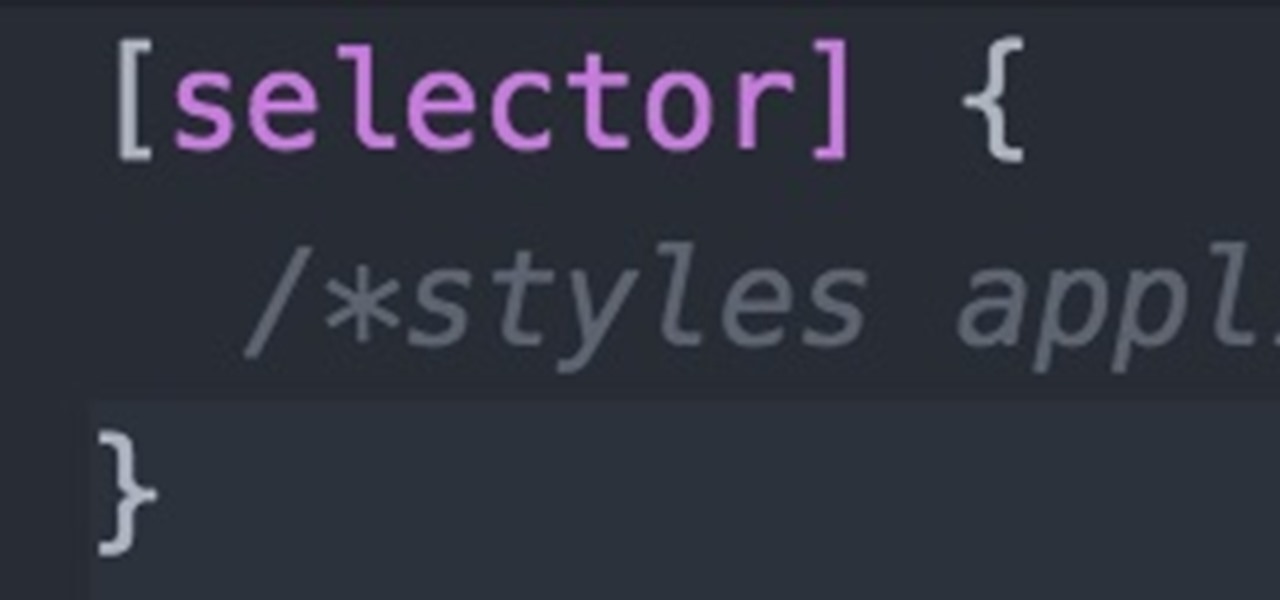
Welcome back Null-Byters! You finally have the pre-basics of CSS and we can begin with styling our web page. If you did not read our last adventure, I suggest you go and read it.

Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it.

I picked up my Galaxy S6 Edge on release day and have loved it ever since. Did I spend an extra hundred bucks for the mostly-aesthetic Edge display? Yup! Did I have buyer's remorse about my frivolous spending? Not even a little.

Welcome back, my eager hackers! In recent blogs, I've demonstrated how to grab password hashes remotely using Metasploit's meterpreter and pwdump. Once we have the Windows passwords from the SAM file, we can then crack these hashes using tools such as Cain and Abel.

Ultimately a doctor’s note is the only necessary proof needed to show your boss that you really did go to the doctor’s but if you feel like making an airtight case you can always take a few extra steps to make sure there’s not a shadow of a doubt.

Here is an improved version of how to tie an albright knot for fishing. I have never had it fail, look and see as I test it.

The 'if' function in Microsoft Excel is perfect for projects such as doing grades for a pass/fail course. Find out how to add it to your spreadsheet.

iPodTouchedMaster shows how one can easily SSH into their iPod Touch with all firmware! To SSH is the ability to hack into your iPod Touch's file system. First, your iPod Touch must be jailbroken. Next, you'll have to open Cydia. Click "Featured Packages" or search for the terms "Open SSH" (it will be listed under Console Utilities & Daemons). When you have OpenSSH click on it and click 'Install' and 'Confirm'. After this is finished, click return to 'Cydia'. This may take a lot of battery po...

Is your neighbor creating a ton of racket? Suffering in anything but silence? It can be hard to approach a noisy neighbor without starting a big riff. Follow these steps to get the quiet you deserve.

Tired of losing your shirt playing poker? How about a fun game for couples instead? You Will Need

Batting a ball back and forth while you're barefoot on the beach is a fun way to get some exercise. Get started with these basic rules. Watch this video to learn how to play beach volleyball.

Learn how to never lose at tic-tac-toe. Almost anyone knows how to play tic-tac-toe, but not everyone knows the strategy that guarantees they'll never lose another game.

Instead of pushing, pulling, and cursing, why not fix that door that sticks? You Will Need

It's already easy, but we'll help you make it even easier. Watch this video for tips on getting guys to buy you drinks in a bar. If the guys are going to hit on you, might as well get some free drinks out of it.

One fight for augmented reality branding that we thought had been settled has suddenly turned into a full-fledged legal battle—again.

Last year this guy made his own smartwatch from scratch, so in 2020, naturally, he decided to give making smartglasses a try. And it worked!

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

If you're quarantining with other people, consider yourself lucky — but it's not always easy. Staying in one space for so long with too many people can be challenging, so you need to find things to do to make the time go by (and to keep everyone sane). Our advice? Try out these seven free multiplayer games that only require one iPhone or Android device to play.

With all the talk about privacy concerns recently, Google's name keeps coming up because they are a very data-driven company. As an Android user, they know basically everything about you based on your device usage. That can easily scare some people off who are worried about their privacy and security. You do have some say in what personal data Google controls, but what if you want total control?

There's something about alcohol that compels you to contact people. Most of the time, the drunken calls or messages you send out will have you cringing hard tomorrow morning. But if you have a jailbroken iPhone, you can help prevent this potential embarrassment with a free tweak.

The latest immersive production from Magic Leap Studios finally got its debut on Monday at Siggraph, during which the company also released the app to the general public, so we took it for a spin.

If you've ever traveled to a country where you do not speak the language, you know there are times you need to translate text. Or maybe you just ordered a foreign good that requires text translation. Google Translate can easily solve this with its camera translation feature. It will translate any text you see in the real world into your desired language.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

When I first found out about Nreal, back in the spring of 2018, the most interesting thing about the company's story was the founder's background. Chi Xu, the CEO and founder of Nreal, previously worked at Magic Leap as a software engineer.

The long and somewhat tumultuous journey of Leap Motion has come to an end, thanks to another startup.

MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer never bothered to issue one.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

By far the most significant development for AR in the coming months and years — the development that will drive AR adoption — will be our reliance upon the AR cloud.