If you lend someone your phone, even if it's just for a second, there's a chance they can enter an app and see something you'd rather they didn't. Whether it's a personal email or a private photo, there are plenty of reasons why you'd want to keep snoops out of certain apps.
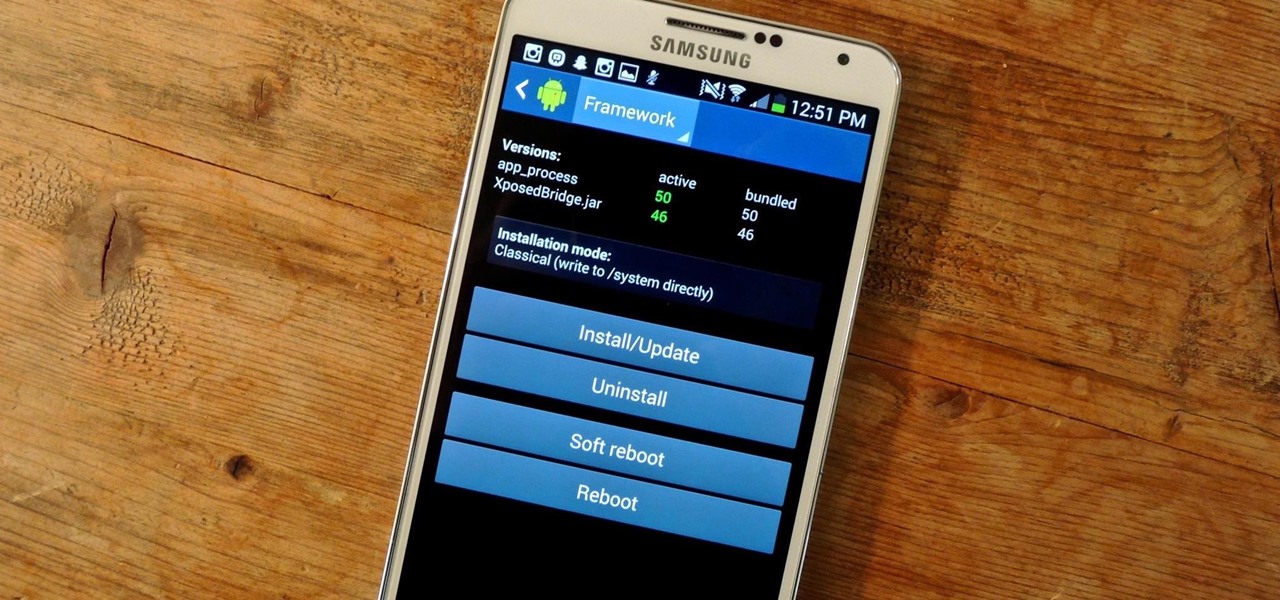
Allowing us to easily get features that would otherwise be available only through flashing mods and custom ROMs, Xposed Installer has been a godsend since its development, simplifying the sometimes tasking and potentially harmful process of changing the core components of Android's operating system.
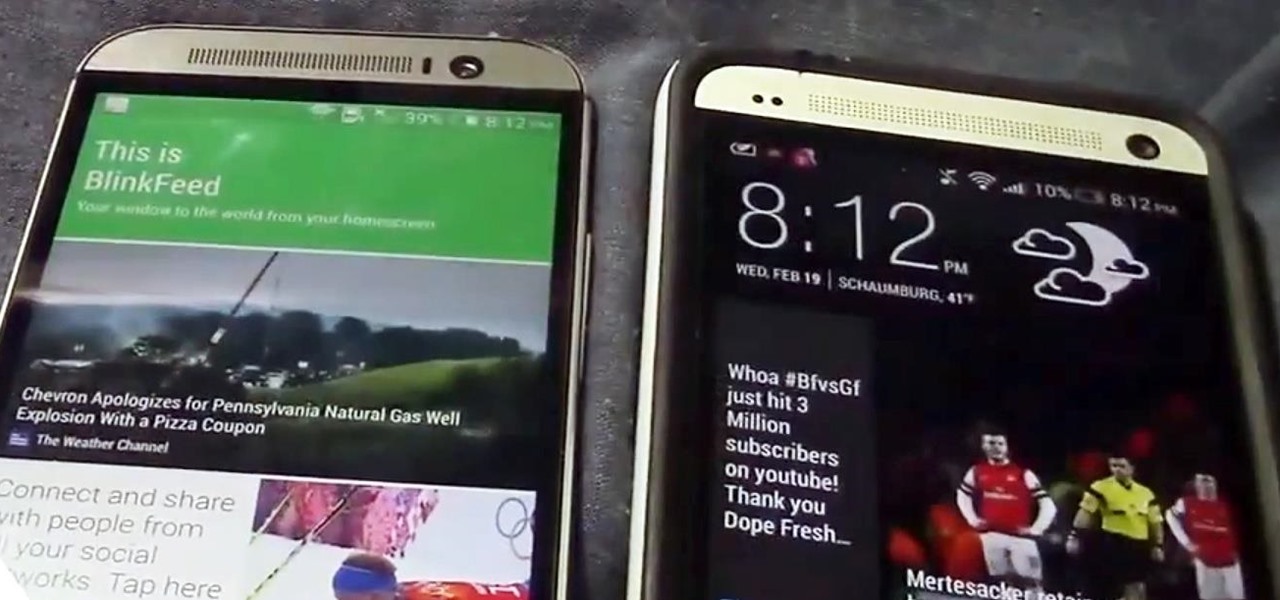
Confirming a lot of what we already knew, now we have a physical walkthrough video on HTC's new flagship, the M8. Or, maybe the "New HTC One", but let's hope that's not the name of the final product. Before we get to the video, here's what we already know:

Americans consume over 1.2 billion pounds of potato chips each year, making it one of the most popular snack foods in the United States.

The newest version of Android, 4.4.2 KitKat, is making its way onto AT&T Samsung Galaxy S4s right now. Itching to try out the latest that Google has to offer? Keep an eye on your status bar for a notification letting you know that a system update is ready.

You probably already know by now that a custom Android ROM can change your user experience and give you what feels like a new OS on your device, and there's no shortage of them out there to try out.

The inclusion of the parallax effect caused a shitstorm amongst iPhone users when it was released in iOS 7, especially when it came to creating custom wallpapers. It was hard to control, and even disabling it didn't fully get rid of it, making it one of the most hated new features in Apple's latest mobile OS.

In the wake of the NSA controversy and its subsequent fallout, many dashed towards finding means of secure communication—using private internet browsing and encrypted text messaging applications—out of fear of being spied on.

Oversleeping isn't just an epidemic that affects millions of hungover college students every year, we all want that extra minute or two of sleep. Unfortunately, oversleeping and showing up late to work or class isn't something we can generally afford to do.

Unless your work clothes require dry cleaning, you probably only go to the cleaner a few times a year. And for those few items in your closet for which you do, you have to then find the time and extra budget to make a trip all the way to the cleaners and back again. In the end, it can be quite the hassle.

Welcome back, my tenderfoot hackers! I recently began a new series on digital forensics to help tenderfoot hackers from being detected and ultimately, incarcerated. In this installment of that series, we will look at recovering deleted files. This is important to hackers because you need to know that even when you delete files on your computer or on the victim's computer, a forensic investigator can usually recover them.

What you watch in the privacy of your own home should be no one's business but yours. That was the case until Prime Minister David Cameron decided that there was too much porn available to minors in the United Kingdom.

Welcome back, my greenhorn hackers! I recently began a series on scripting and have received such positive feedback that I'm going to keep this series going. As I've said before, to graduate from the script kiddie to the pro hacker, you'll need to have some scripting skills. The better you are at scripting, the more advanced your hacking. Ultimately, we are leading up to developing the skills to build your own zero day exploits.

As the protectors of all things good, the Federal Communications Commission is usually busy behind the scenes pissing off Slim Shady, giving out fines for indecent nipple exposure at certain halftime events, and warning the NSA about losing any "confidential" phone information they steal from us.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

Why can't I see who is stalking my Facebook profile?

Snapchat's self-destructing nature is the perfect way to send funny and potentially embarrassing photos and videos (something Anthony Weiner wishes he knew about). That's why there are currently 150 million Snapchats sent each day. While it may be used for fun, many fail to recognize that there's a dark side to every good thing. While Snapchat claims that the pictures and videos on their application are completely obliterated—not only from the phone, but from the Snapchat server—there are oth...

Matte and flat colors have became quite popular. I was surprised to see how many cars used these colors at SEMA 2011.
In any project management career, there is no such thing as a person who knows everything for each project. Many times, those who got too much confident with their jobs fail because they were not able to make things clear before and during the project implementation.
Project management covers a lot of processes needed for project completion. Among the many functions in managing projects, one of the most important is resource management. It is an aspect of project management which deals with various project management resources like human, materials, equipment and costs.

Life has many perils: parasites, predators, and pitfalls. Eventually, any organism will succumb, and if that organism has not first passed on its genes, those genes will face extinction.

What's the meaning of life? That's the age-old question; but can it ever really be answered? I mean, isn't life just a big game anyway? Perhaps, a game of inches?

The holiday season is here, and most people have already started counting down. Advent calendars are a very traditional way to keep track of how many days are left, but most of the ones you see are either boring, made for little kids, or just plain ugly.

At first glance, the iOS home screen looks nearly identical to the original release back in 2007. Though those experienced with the evolving iterations of iOS will tell you that the features have changed. Furthermore, with the App Store continuing to explode with (lets face it) better options than the stock software, these included applications are only causing clutter across the springboard.

There is no better example of a risk-versus-reward scenario than jailbreaking your iPhone or rooting your Android phone. While both jailbreaking and rooting undoubtedly has its advantages, this possibility of something going wrong and you ending up with a 500-dollar doorstop is never too far out of mind.

Android has released a new application called ezNetScan, which is a free app that scans the wireless network you're connected to and gives you a full log of all of the devices connected to that network. This isn't new for smartphone users, let alone Android users. Fing has been around for a while and does practically the same thing that exNetScan does. It gathers information such as the IP and MAC addresses, device vendors, and ISP location. But while Fing is a great program, it does lack a f...

It's no secret that most people who got an iPhone 5 (or upgraded their old iPhone to iOS 6) have been sorely disappointed with Apple Maps. We may all miss Google Maps, but the Google says they aren't even working on an app for iOS 6 yet. Even worse, Google exec Eric Schmidt says they're waiting on an invitation from Apple, and if we know Apple, that could be a while. Users who didn't get an iPhone 5 have had an even worse time of things—Apple disabled 3D maps and turn-by-turn directions on ol...

Think your roommate's been using your computer while you're not around, but don't have any proof? Worried your little brother or significant other is snooping through your stuff? Here's how to check on both Windows and Mac OS X so you can catch and confront anyone who's logging onto your computer without your permission.

You may or may not have heard of alt-rock band Panic! at the Disco, but a year and a half ago they released a single called "The Ballad of Mona Lisa", which had an accompanying music video that was Steampunk-themed. In fact, here's the video:

Let's say you forgot the code to your Master Lock combination padlock. What can you do besides buy another one? Well, there's a surprising abundance of ways to open a combination lock other than with just the combination, some of which will even let you reset the code. Of course, these hacks aren't limited to folks just looking to open their own locks, but let's just assume that's what you're here for.

Okay, so you've decided to take the plunge, and participate in our Love. Earn program with a how-to article. But, for whatever reason, your article keeps getting rejected by WonderHowTo, and you're wondering, well, where's the love?

Despite the controversy over Scrabble Trickster across the word world, Mattel's modern take on the classic crossword board game is out in stores— but not in the United States. It's only available in and around the UK, but you can snag your copy just in time for Christmas from Amazon UK. You can also visit the official Scrabble Trickster website. I imagine this is going to be a hot item in the United Kingdom this holiday season, but as for me— it's the one Scrabble game I refuse to add to my c...

C++ is one the most powerful and fundamental languages commonly used to computer programming. If you've ever wanted to get started using, then please watch this video series. It's 29 parts will teach you everything you need to know about coding in this magnificent language, allowing you to create your own fairly full-featured computer programs. Honestly, if you have any questions about C++ at all, or want to learn it and don't think that you can because you've tried programming before and fai...

If you love the ocean and love swimming, it's time you step up to the next level… snorkeling. Snorkeling is one of the best ways to explore the underwater life, without fancy equipment or expensive training. And all you need is a snorkel. If you want a better look at what’s underwater, all you have to do is snorkel.

Bid Whist can be a fun game for family or friends. It's challenging enough for adults, but enjoyable for kids too. Bidding and predicting wins are what make playing Bid Whist fun and exciting, whether you win or lose.

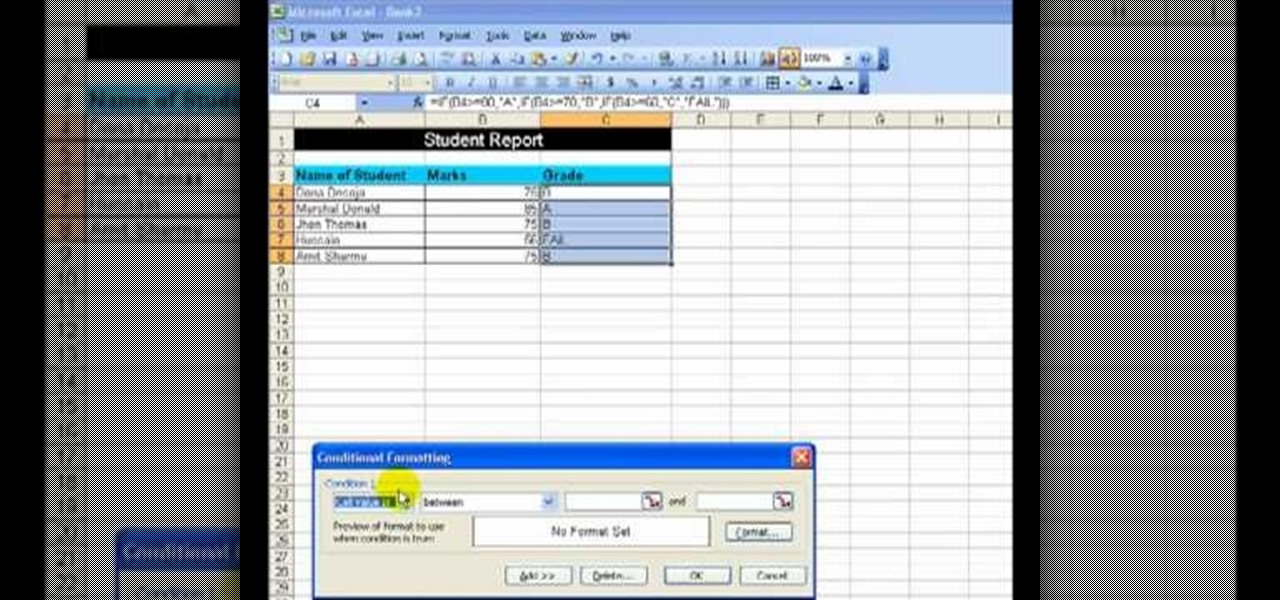
If you're looking for a way to create a student report, Microsoft Excel makes it easy to create a wonderful spreadsheet with tons of information. This video shows an example of a student report being created, which has three simple items in the columns of the sheet, which are the names of the students, the marks obtained and the grades.

This video series takes you through every step of building a building in SketchUp and is taken from chapter 4 of "Google SketchUp for Dummies" in case you want to follow along. PART 1 explains how to switch to a 2D view to get you ready to build the floor plan. It's a good idea to have accurate measurements of everything you want to build before starting this project. PART 2 familiarizes you with the tools available in SketchUp to help you create your floorplan. PART 3 shows you how to draw t...

In this series of home car repair videos, our expert mechanic takes you through each step of repairing your valve cover gaskets. He demonstrates how to remove and replace valve cover hoses, spark plug wires and ultimately the gasket itself.

Have you ever been locked out of your iPhone? Maybe you forgot your passcode. Or perhaps someone with access changed the passcode as a prank. Your iPhone's display could have even been damaged and unresponsive. Whatever the reason, there's an easy way to get back access to your iPhone the next time it happens.