The start of a new year is generally thought of as a chance to start over, a time to improve or "fix" things in your life. Yet most people who set stringent New Year's resolutions find themselves failing within weeks—or even days—of setting their lofty goals.
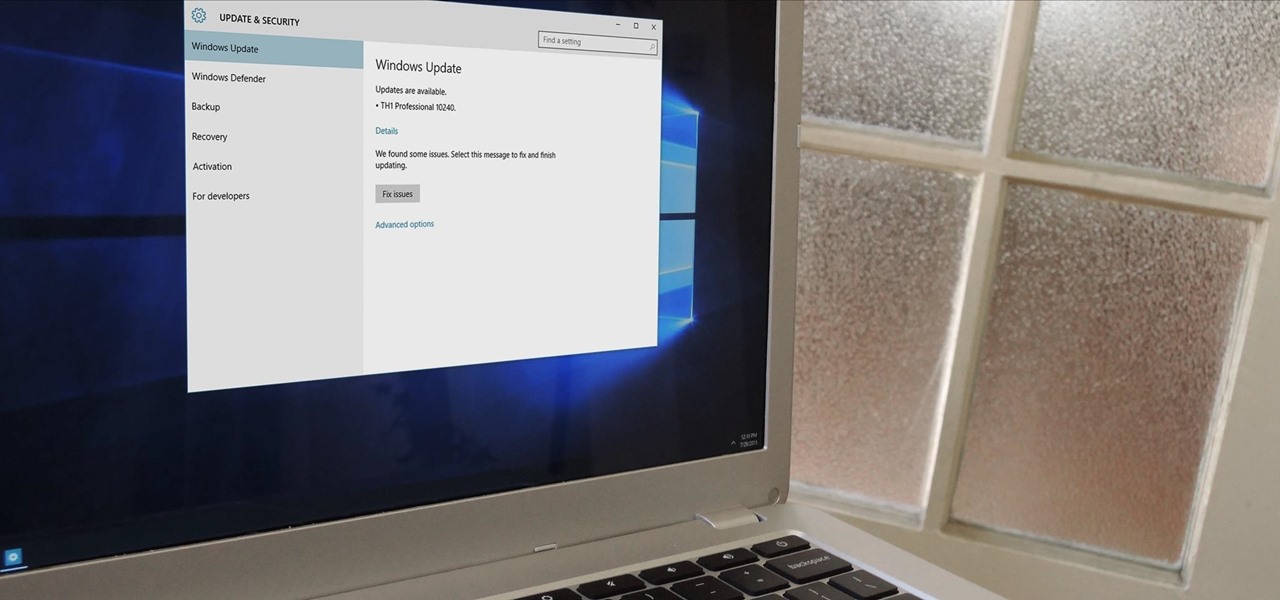
In a bit of a strange decision, Microsoft has made it to where some users don't have a choice in the matter of applying failed automatic updates. When a Windows or driver update comes your way and fails to apply for any reason, your computer will continue to attempt applying the broken update at seemingly random intervals. The Pro and Enterprise editions of Windows 10 will allow you to delay or stop updates altogether when something like this happens, but the Home edition has no such setting.

We have all seen videos of people walking off of platforms and into street signs because they were too distracted by their phones to pay attention. This has become such a problem that cities have even considered fining pedestrians for texting and walking.

When ringtones and vibration alerts miss the mark and fail to grab your attention, causing you to miss an important call or text, LED flash alerts are a great backup plan. While we already showed how to activate this on Samsung devices, the apps shown below make this feature easier to toggle on and off. Plus, they work on devices that don't have flash alerts included in the system settings.

The interwebs is a great source of information, but sometimes said information is not always legit. That can be frustrating when it comes to making fun food, costumes, and arts and crafts for Halloween, like this bowl of "bloody" gummy worms.
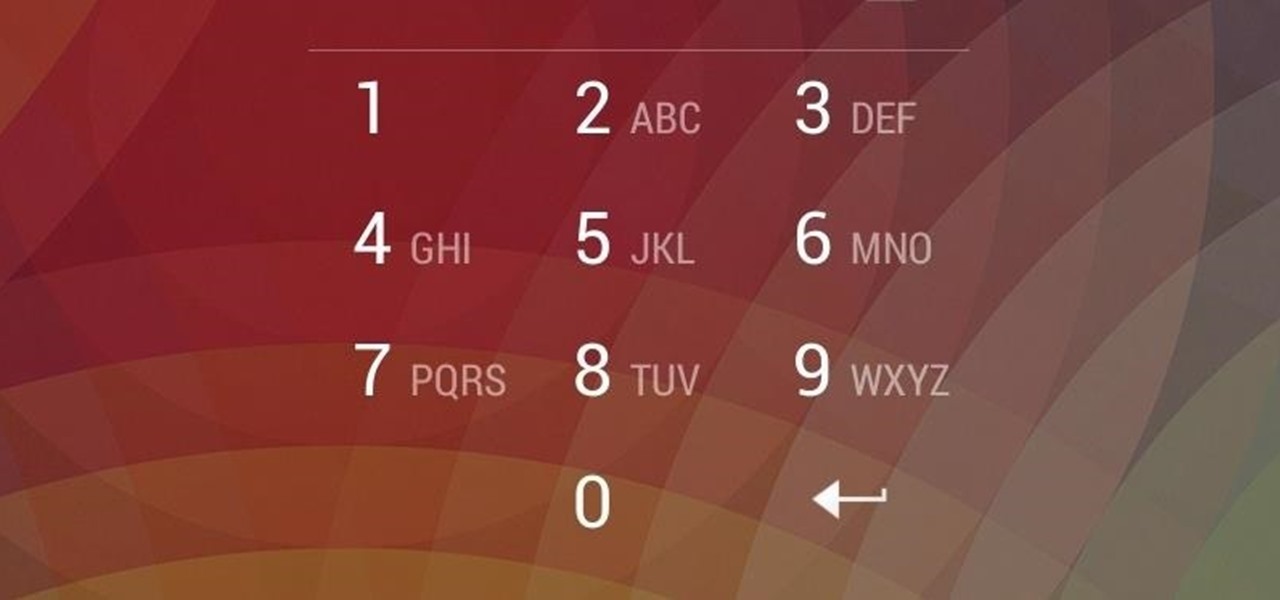
It happens to everyone: you set a lock screen password in a hurry and cannot remember it the next day. To unlock your device again, you need to reset the password (or PIN, pattern, etc). There are two official methods of doing this.

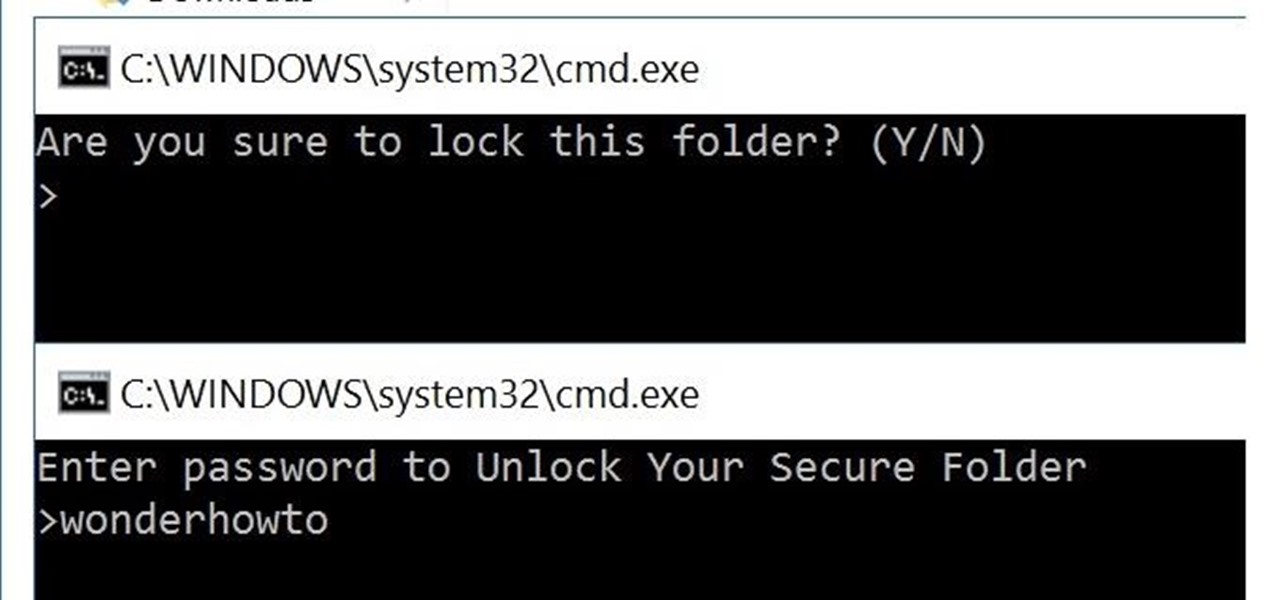
You can easily lock any folder on your Windows computer with a simple Notepad hack. By creating a batch file, you can hide a folder and require a password be entered before it becomes visible and accessible. This is a great tool for locking sensitive information, like pictures, financial statements, and a lot more.

What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl.

This video tutorial from iDeviceTutz shows how to change the SSH root password for iPhone or iPod.When iPhone or iPod is jailbroken it sets its password to default - alpine.Thus your device becomes vulnerable from a network attack that could steal your information or identity. So you need to change your password as soon as possible when your device is jailbroken.For this you'll need Mobile Terminal program on your device and SSH client (Cyberduck or WinSCP) on your computer.First download and...

Popular Mechanics' Senior Auto Editor Mike Allen shows you how to safely stop your car if you become the victim of sudden unintended acceleration.

Kipkay never fails to impress, and this so-called "condom hack pack" is no exception. Who knew there were so many useful uses for a condom besides the obvious! In this Kipkay two-part video, learn how to hack condoms for nine different uses.

Watch a 41 part series on Spore's Space Stage. How will you create the universe? With Spore you can nurture your creature through five stages of evolution: Cell, Creature, Tribe, Civilization, and Space. Or if you prefer, spend as much time as you like making creatures, vehicles, buildings and spaceships with Spore’s unique Creator tools.

Everybody's hacking these days. Everybody wants to be a hacker, but that's what happens as technology becomes more and more accessible. Hacks are due to a lot of things. The main point is that you allow your user to access your WordPress Admin section or any section. So, may a problem could come with your user or writer. So, you must know about your login details and failed login details. Then only do you know about your user and what they are doing in your WordPress Admin section.

There’s nothing more special than a beautiful pearl necklace. But how do you know if they are real? Knowing some qualities that pearls have should help you determine when there is an obvious fake in your presence. It might ultimately be necessary to leave it to a professional to authenticate those pretty little presents from the sea.

Well here it is. The ending of spore. We finally made it to the Center of the Universe. We also made it to the end of the galaxy, as well. This is a walkthrough of the absolute last stage of Spore. This is both the center of the universe and end of the galaxy.

In previous versions of Acrobat you could run PDFs against the Preflight tool and it would either pass or fail. If it failed you would then have to manually resolve the problems in the PDF or by generating a new PDF. In Acrobat 8 Professional you can now apply "Fix-ups" to correct the most common problems encountered in working with PDFs for print.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

Since the San Bernardino shooting in 2014, Apple's been engaged in a game of cat and mouse with law enforcement. Authorities want access to evidence on criminals' iPhones, but Apple wants to protect all of its customers' personal data equally. The latest installment in this saga has Apple outright disabling the Lightning port.

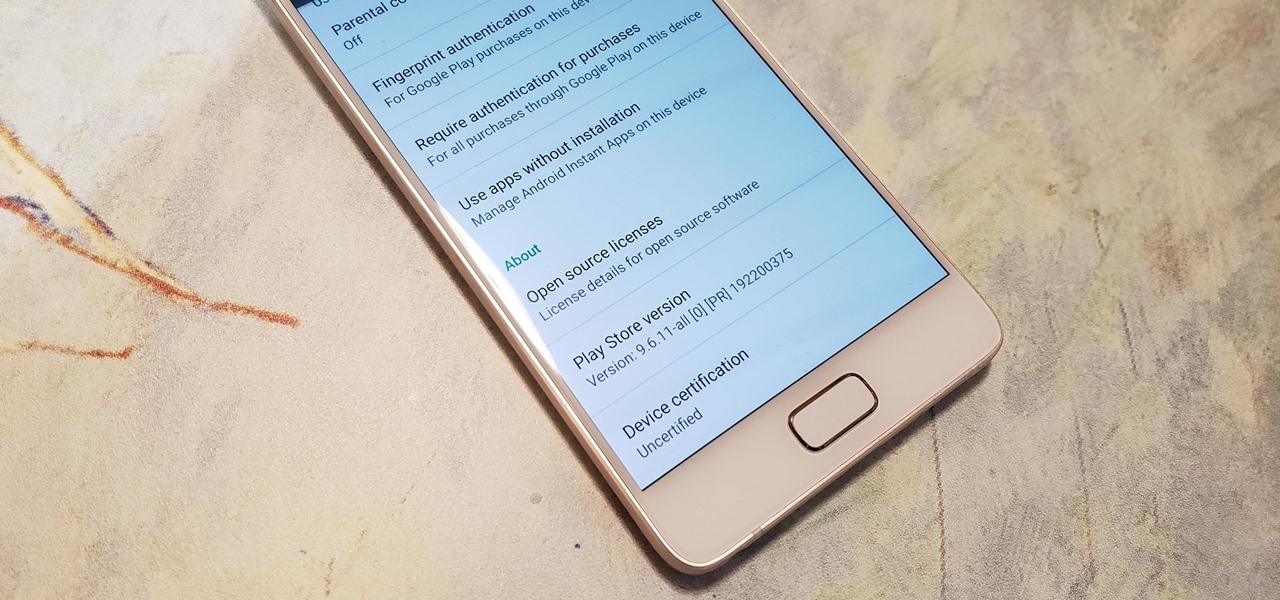
Google has started blocking certain devices from accessing the Google Play Store and other Google services. This is part of an effort to clamp down on OEMs that skirt its certification requirements, but now millions of phones have been uncertified to download or update Google apps. Fortunately, there are a few workarounds.

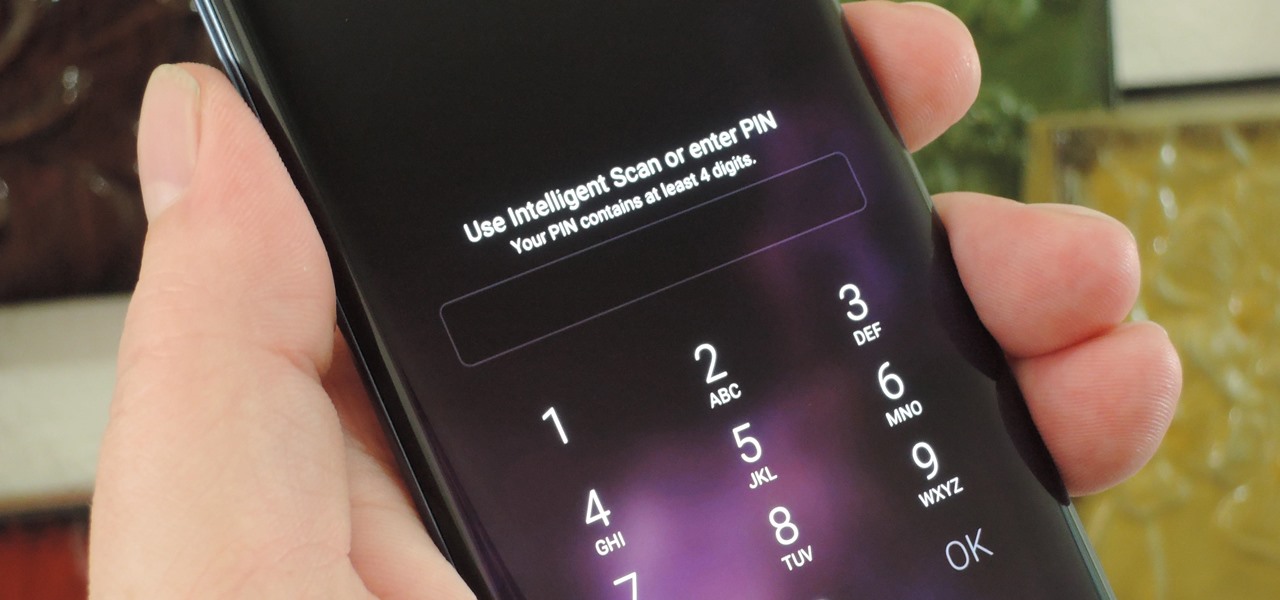
The Galaxy S9 is full of minor improvements and revisions that come together to make it a worthy upgrade over the Galaxy S8. One such improvement is facial recognition, which Samsung has fortified with machine learning and the inclusion of another sensor. The result of these efforts is called Intelligent Scan.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

When you have an infection, a doctor prescribes antibiotics to make the bacteria that causes it disappear. Sounds like a good idea, but the disappearance of microorganisms that have inhabited humans for millennia could be driving rising numbers of serious illness and debilitating conditions.

Because of Android's new SafetyNet system, certain apps can now block rooted users or prevent you from accessing them altogether — but at least for now, there are still ways around these restrictions.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

The truth is, it's not about how many repititions of an exercise you do; it's about how well you hold the form and what kind of exercise you do. Heck, you could probably do 1,000 sit ups a day and still have some extra flab on your belly. That's because sit ups only tone the upper portion of your core, making the rest liable to grow chub.

If you've ever gone on a diet then you know that "dessert" usually leaves your vocabulary quickly. But sometimes you gotta live a little and satisfy that sweet tooth! After all, not doing so may just cause you to pig out and totally fail on your diet.

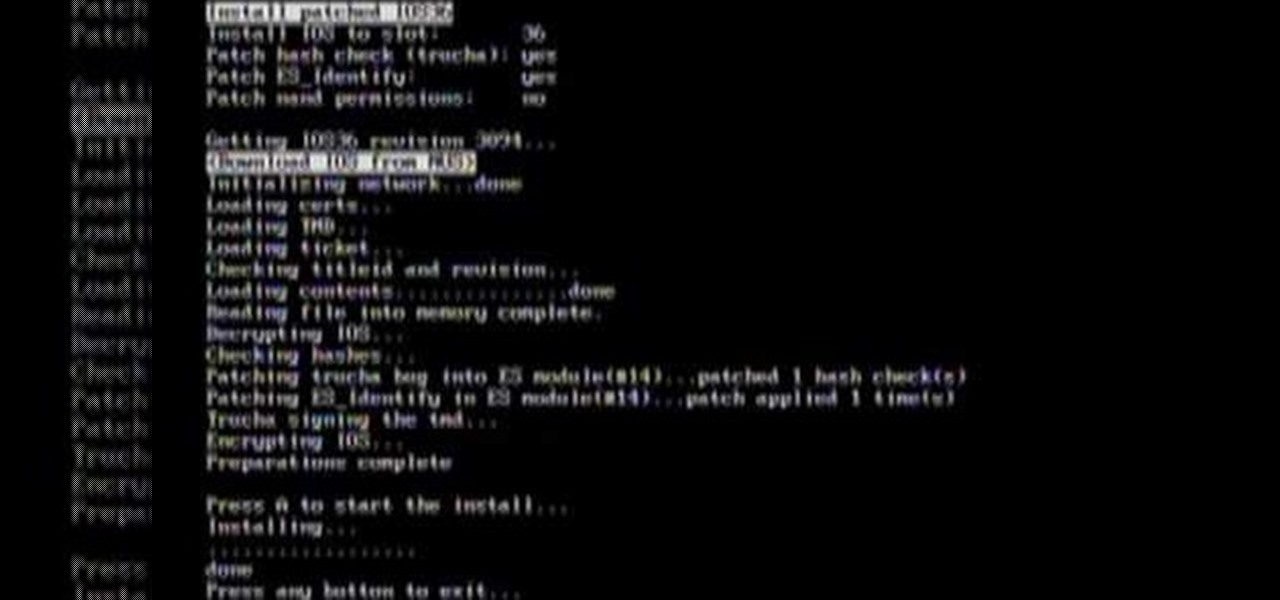
Trucha Bug Restorer is a powerful piece of homebrew software that you can use on your Wii to make sure that it is formatted properly in order to play burned games and use other hacks. This video will show you how to use it to set up an installation of cIOS on your Wii, which is the program that allows you to play burned backup copies of games.

Whether you're prepping for an outdoor picnic with your loved ones or creating a finger food menu for afternoon tea, tea sandwiches never fail to be a healthy yet appetizing treat.

In this how-to video, you will learn how to stop your dog from barking excessively. Dog's bark naturally. It becomes a problem when your dog barks too much. First, determine the reason why your dog is barking in the first place. From this, you can determine the next step. If your dog looks like he or she is barking at nothing, the dog is definitely barking at something because of heightened sense of hearing and smell. You must communicate to your dog what is acceptable behavior. Never reward ...

Here's a good way to do the rope coin cheat on Pet Society using Cheat Engine. Cheat Engine never fails to amaze, so download it, use it, and enjoy.

This how-to video shows a guaranteed, never fail way to get even the hottest girls at the bar to talk with you for at least 20 minutes.

Many have tried to prove (or disprove) that tennis ball lock picking really works, but it still seems up for debate. Mythbusters have supposedly debunked this technique (watch the video). Someone over at the Auto Blog also has tested this car lock method with failed results (watch the video).

Master Rafael Negron, 6th DAN Master Instructor, and Jessica Sherlock, 2nd Degree blackbelt. Hapkido is an eclectic Korean martial art that is literally translated as “the way of coordinating energy” or “the way of coordinated power.” Hapkido is ultimately used as self-defense and combines other skilled martial arts with common attacks. he main focus of Hapkido is footwork and body positioning used to employ leverage.

Want to know how to play some good music on the acoustic guitar? Well, this video tutorial will show you how to up your guitarist skills by learning to play "Life for Rent" by Dido. When you play this song from the lesson, play the capo on the 3rd fret.

Drones give you the joy of experiencing the sky without any of the downsides of gravity. Copernicus was the astronomer who put the sun at the center of the solar system. This little drone is aptly named after him because it similarly gives you a true look at the sky through a crystal clear camera and agile, intuitive controls.

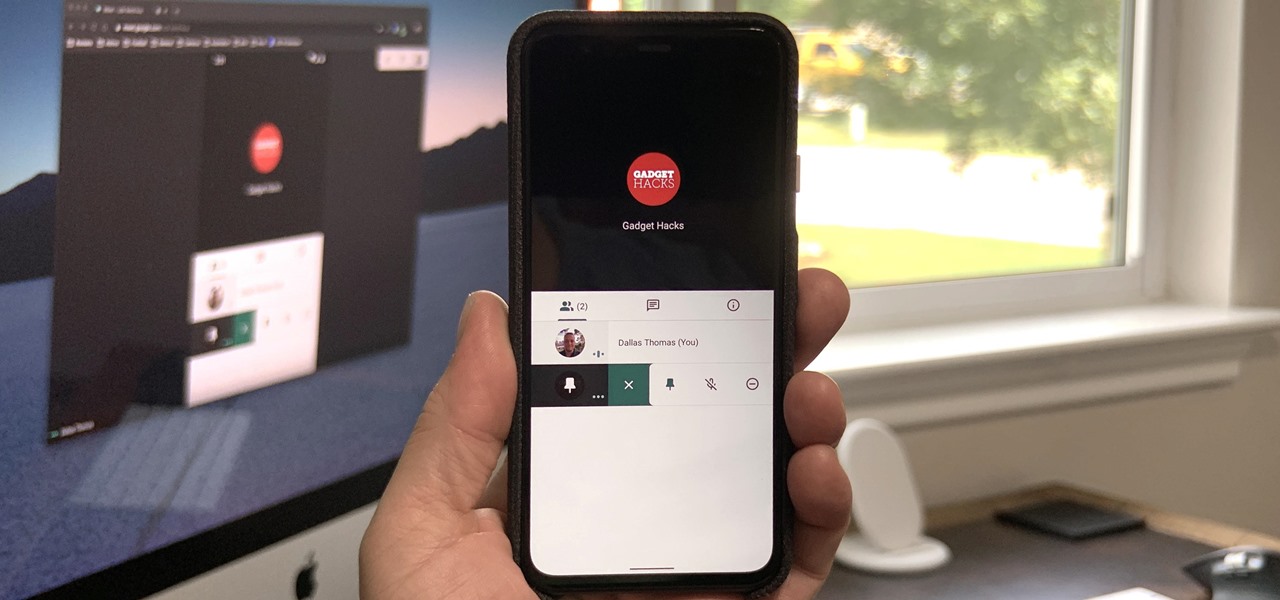
Now that Google Meet is free for anyone with a Gmail address, you can expect to see invites from Google's service alongside Zoom calls.

Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

Congratulations, you've made it deep into the middle of flu season! If you're reading this, you're either a very smart preemptive sick day prepper, or already in the throes of fighting off a cold or flu situation.

After three rounds of beta testing, Apple finally released iOS 13.3.1 today, Jan. 28. It's the latest update to iOS 13, coming exactly seven weeks after the release of iOS 13.3. So, what's new?