Water makes up about 60% of your body weight. Whether you like it plain, flavored, bubbly, or in beverages or food, we all need water daily to avoid dehydration and stay healthy. For communities in need of clean drinking water, new research using bacteria may offer a simplified, lower-cost method for boosting potable water supplies.

Specialized cells in the lining of the gut may provide a key to preventing an infectious brain disease caused by misfolded proteins.

Starting in October, many Nexus 6P users have been experiencing a bug that causes their phone to completely shut down, even though there was 20% or more battery life remaining. At first, it was thought to be a direct result of the recent Android Nougat update, but a combination of factors indicate that this isn't necessarily the case—or, at least, it's not the only problem.

Whether you made the switch from iOS, or you came from a different Android device, there's a lot to learn about your new Galaxy device. Samsung does things a bit differently, and thanks to their TouchWiz interface, there are tons of added features to take advantage of—though some folks might find these extras to be a bit too much.

Android's stock battery menu is pretty decent. You can see which apps have been using the most power, and you can tell when your CPU was awake or asleep, among other things. But a lot of times, battery-sucking services will get lumped under the generic "Android System" header, and even though you can see when your CPU was awake, you can't exactly see why.

Step 1: Tie a Ponytail Use clear elastic to tie a ponytail and divide the ponytail into 2 segments.

No need to make a bad situation worse when running into an ex boyfriend or girlfriend. There is no need to be petty or spiteful when keeping to a nice yet vague conversation will ultimately leave you looking like a real class act.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

Google just bought a huge chunk of HTC for $1.1 billion. They're bringing in around 2,000 employees, mostly from the hardware division, and these folks will presumably work under hardware chief Rick Osterloh. There's a massive patent portfolio involved, too, so stop me if you've heard this before — Motorola, anyone?

Google is working on something so big they had to name it after an entire galaxy: A new operating system that merges Android and Chrome OS into one unified front.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

After months of waiting, it looks like HMD has finally answered the call. Nokia's parent company is finally releasing a true flagship phone — one that isn't just an enhanced version of a previous phone and actually brings something new to the table. That phone is the Nokia 9 PureView.

There once was a time in the Android rooting scene where we couldn't rely on using a custom recovery for all of our modding needs. Manual file flashing was very popular in the early days of Android before custom recoveries started taking over. With the rise of TWRP, it seemed like there was almost no need for manual file flashers; however, they appear to be making a welcomed return in a big way.

On Thursday, Osterhout Design Group (ODG) revealed a new, specially-crafted oxygen mask that uses the same augmented reality technology from its smartglasses to assist FedEx Express pilots navigating dangerous conditions.

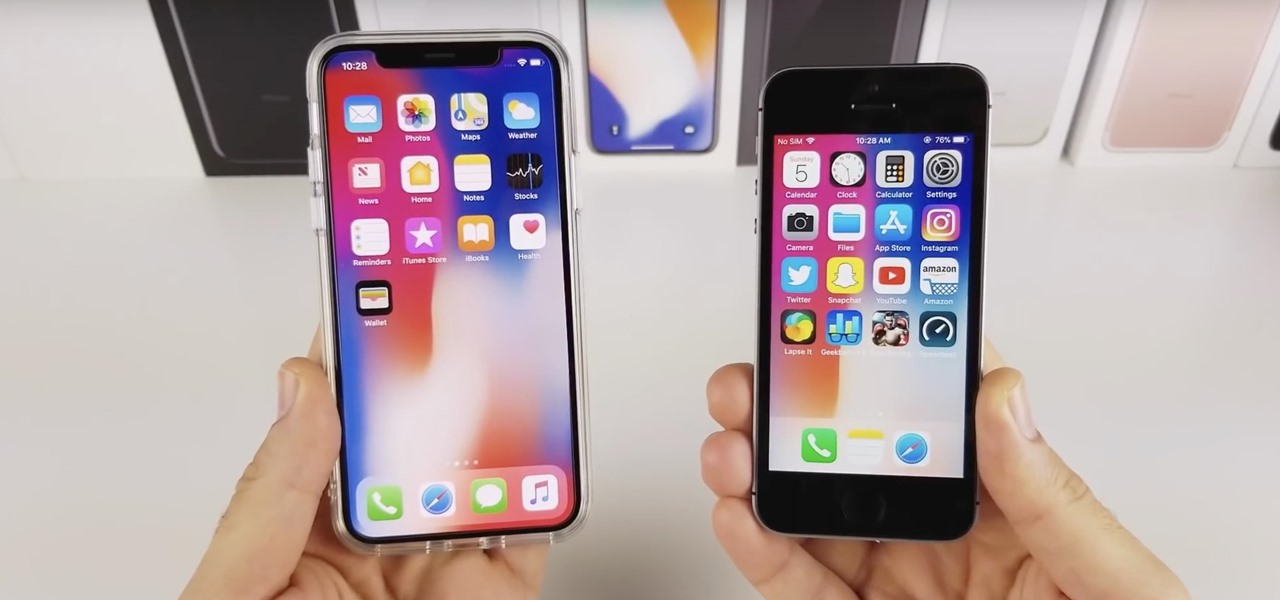
When first released, the iPhone SE was nearly identical to its iPhone 6S counterparts in all but form factor. While the rumored SE 2 (if it even happens) is expected to follow suit with the iPhone 8 models, that hasn't stopped people from wondering what it would look like with an iPhone X-like bezel-less display.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

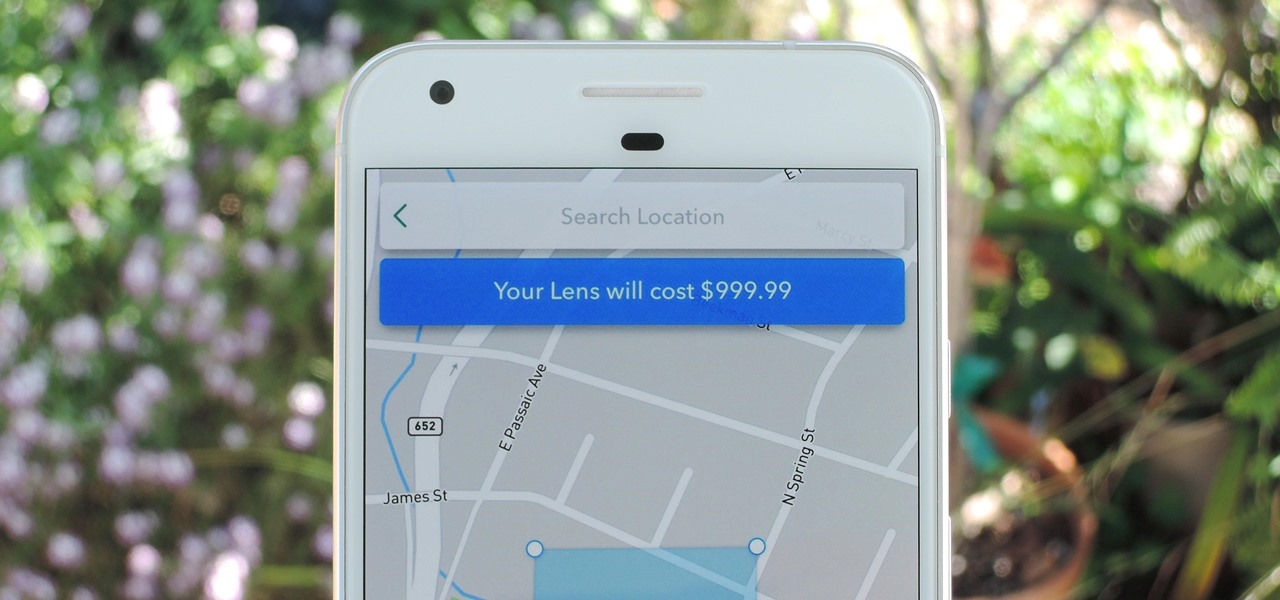
Snapchat just rolled out a feature that lets you create custom Filters and Lenses. While the average Geofilter won't run you more than a few bucks, it's not that hard to exponentially jack up the price. Amazingly enough, Snapchat's latest attempt to monetize their platform can ultimately cost you as much as $999.99. Ignore the penny, let's call that a cool grand.

Honeywell recently completed successful testing of virtual window technology that enabled drivers to maneuver an otherwise windowless combat vehicle on rough terrain at speeds exceeding 35 miles per hour.

It wasn't too long ago that Uber threatened to fire star engineer Anthony Levandowski. Eleven days to be exact. If Levandowski didn't turn over the documentation he allegedly stole from Google's autonomous car division, Uber informed Levandowski that they would take "adverse employment action." Today, The New York Times reported the ride-sharing firm has delivered on that threat. In a memo sent to employees Tuesday morning, Uber announced Lewandowski's official departure from the company "eff...

Phuket, the island in Thailand typically associated with paradise and most recently, illegally-run hotels, now has a different problem—a stray cat with the claws of death.

The force is strong with this project. Colin Furze is a British YouTuber who is a self-proclaimed "garage inventor and video maker." In a recent collaboration with eBay, Furze created the "ultimate Star Wars project," an 18-feet-tall playhouse version of the AT-ACT from Rogue One: A Star Wars Story.

Don't Miss: The Difference Between Virtual, Augmented, & Mixed Reality

More often than not, when you find an app that offers a particular functionality, there are ten other apps on the Google Play Store that offer virtually the same features. But the reason we choose one app over the alternatives is mainly due to one thing—a preference for the user interface of the app we ultimately install.

There are over 1.6 million apps on the Google Play Store, which makes it the largest collection of mobile apps on the planet. However, a large portion of this total is occupied by apps with overlapping functions—think social media, news, weather, music players, and various other categories where developers compete against one another to garner the largest user base.

There has been a huge shift over recent years to alternative medicine as people get disillusioned with conventional medicine to overcome anxiety. Natural and herbal supplements are becoming popular as people re-engage with nature. The list of potential side effects from drugs and the rebound effects from withdrawing often make the thought of taking medication unpleasant. Often the promise of how effective the medication can be is exaggerated or it simply does not have the effect it should bec...

Whether it's to flaunt your new digital face on Instagram or to show off a unique app to your friends, you'll ultimately need to know how to take a quick screenshot with your shiny new Apple Watch. Turns out, it's not that much different than taking one on your iPhone.

It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography.

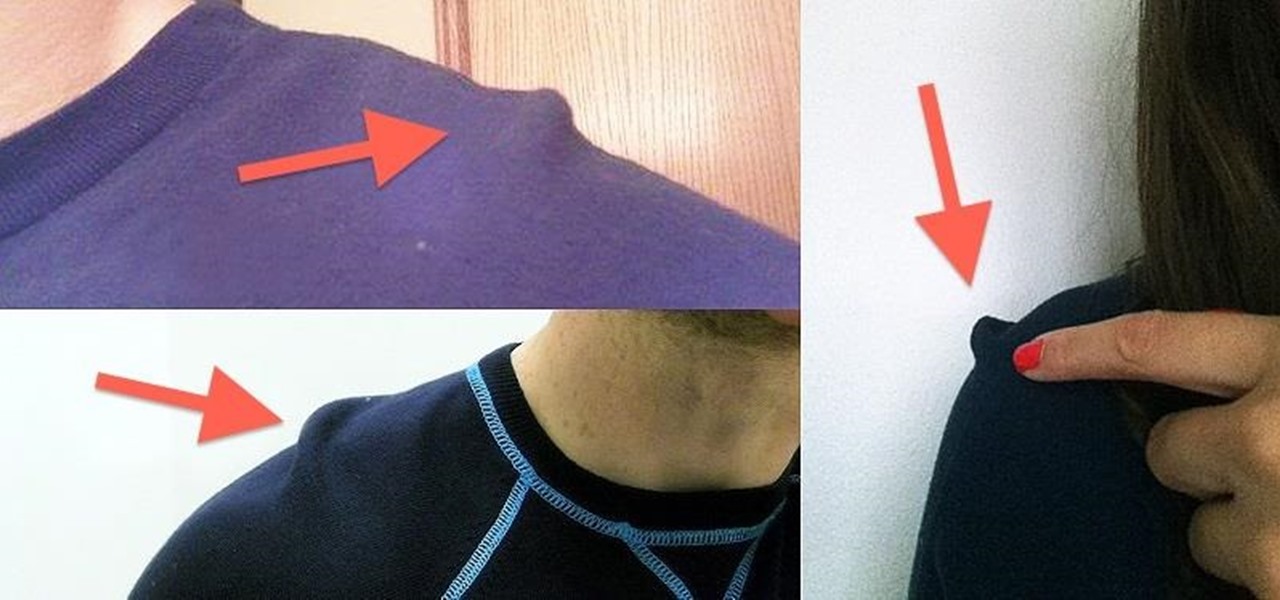
Let’s be honest: you’ve thrown a few delicate, "hand wash only" clothes into the wash with your jeans. Maybe you’ve even ruined a sweater or two. There are so many things to look out for when doing laundry, and they’re easily ignored or forgotten, especially when it comes to drying.

Just like some of its popular puzzle predecessors, 2048 is an extremely simple yet insanely addicting game that pits you against a slew of blocks, to be configured into increasing sums with fervid, high-paced moves. If you have yet to play it, check out either the iOS (by Ketchapp) or Android (by Estoty) versions of the game. Due to its overwhelming popularity, dev TalkLittle has ported the puzzle game as 2048 for Chromecast (available for Android only), which lets you play the game solo or b...

I'm one of very few Americans that suffer from TMS syndrome, i.e. Too Much Swag. While there are no current cures for the disease, I'm in no rush to rid myself of the problem.

Apple is extremely strict when it comes to modifying your iPad, iPhone, or iPod touch. For example, let's look at the dock on iOS 7 devices. You've only really got two options for the dock background, either the default frosty translucent one, or the dark gray version. That's it, and the dark one will also change the look of other things on your device.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

There are two things I can definitively say about Katy Perry. One, she makes extremely terrible but catchy songs that I end up hating myself for singing in the car. Two, she single-handedly made Elmo the most popular Sesame Street character ever for males 13 and up (though, Kevin Clash ultimately made him the least popular shortly thereafter). Needless to say, Ms. Perry knows how to show off her assets. How can we forget California Gurls and whip cream breast cans?

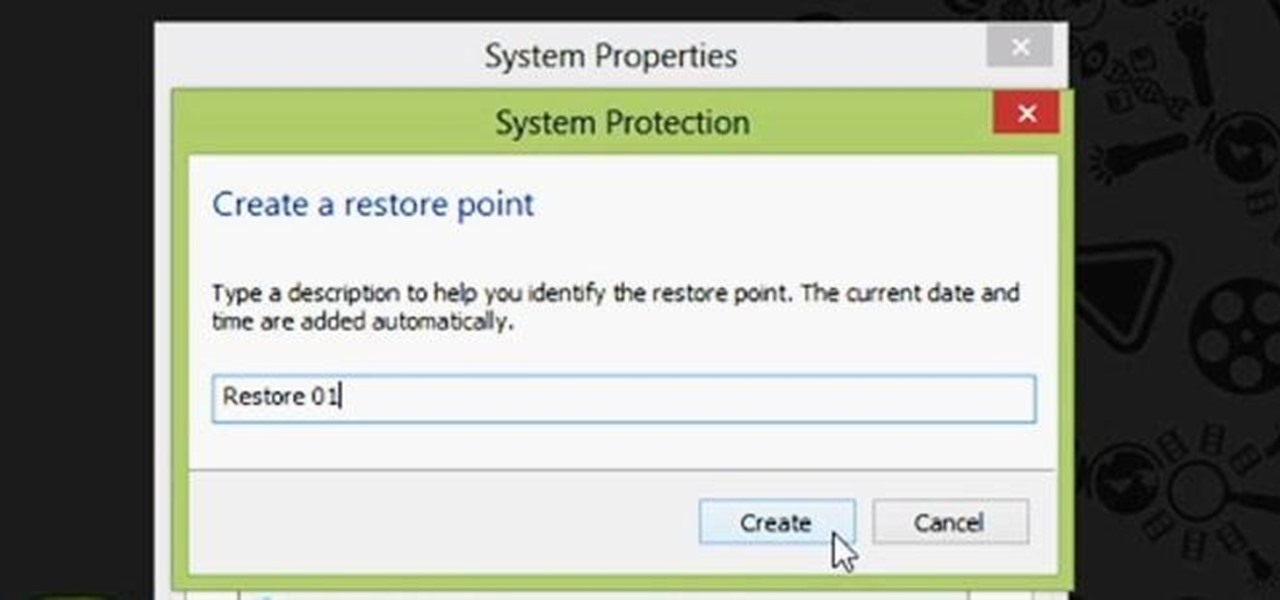
Restoring your computer to a previous point is an extremely important thing if something goes wrong. I've restored my computer at least a dozen times after downloading some suspicious software or running into an error I couldn't remedy on my own.

What do Justin Bieber, Kim Kardashian, Chris Brown, Rihanna, and Soulja Boy all have in common? They suck at Instagram.

Okay, so you've decided to take the plunge, and participate in our Love. Earn program with a how-to article. But, for whatever reason, your article keeps getting rejected by WonderHowTo, and you're wondering, well, where's the love?