Dragon Age 2 is the latest fantasy RPG from the folks at Bioware, and if you're watching this video you've probably either just gotten it or are thinking about it. Check out the vid for a walkthrough of the prologue quest, Destruction of Lothering.

Want to learn a valuable skill? Well, just watch this video tutorial to see how to cross one eye or speak with an echo.

Lava lamps are cool and retro, but they can be expensive and there is a risk of fire if you leave them unattended and they tip over accidentally. By using this tutorial by Shooting Eggs, you can make your own light up bubble tube using materials you might already have around the house, and it will be safer and a whole lot cheaper than the kind you'd buy. Make one of these babies, and your 1966 love den will be all ready to go.

Check out this DIY video tutorial from Curbly, the best place to share pictures of your home, find design ideas, and get expert home-improvement advice.
Microsoft recommends a unique user ID and password for every user. In order to switch user ID or log off one need to click to the 'Start' menu as shown in the video. Press the move button at the shut down menu as shown. In the sub menu you can see the Change user and Log off. The window will typically shut down and restart on change of user ID or Log Off. In case you need to leave your PC unattended you can press 'Lock' from the same menu which will refrain anyone from changing your desktop s...

Nothing can ruin a nice bike ride like getting your bike stolen. Improperly locking your bike or just leaving it unattended is a sure way for it to be stolen.

Roses are beautiful flowers that hold many different representations, including love. Growing them can automatically add beauty to your home's garden and a scent that is very relaxing. Pruning them is important since leaving them unattended can cause problems. This tutorial will show you how to properly prune roses during a cold winter month, January. Good luck and enjoy!

Gigafide will show you how to slipstream Windows installations. You need to go to Vlite and download the program for Windows Vista. Install and run it. Select install at the main window. Use 7-zip to extract the ISO file. Next, go to that folder and run startcd.exe. You click next, agree to the terms and install it to the Vlite folder. Go to that folder, then Tools - x86 and select the file wimgapi.dll. Copy and paste that into the main Vlite folder. Go to Vlite, select your Windows Vista dis...

Cars are expensive to buy, replace or repair. Check out this video and learn how to avoid the most statistically dangerous parking areas. There is no guarantee that no one will touch your vehicle, but by take precautions you are much less likely to be targeted.

If you're having a hard time with starting your lawn mower, there could be several problems. One of the main issues can be because of the vehicle's carburetor. If unattended, it can give you a hard time.

This is a video showing how to handle and mince garlic. Make sure that the garlic is firm and not dried up. The skin is broken with a hammer to get the cloves loose. The skin is then peeled off of the garlic. The garlic is then cut into long pieces. Each slice is a 16th of an inch thick. Heat up olive oil and place the garlic into the oil. Let it cook for about a minute so that the flavor is drawn into the oil. Do not leave the garlic unattended. Garlic burns quickly. The garlic is removed an...

Watch this video tutorial to learn how to play the Google language computer prank on a coworker. Change your colleague's Google settings with this easy prank, and watch their head spin!

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

If you want to cause one of your friends some extreme discomfort and possibly ostracization, try doing this to them! This video will explain a simple prank that you can pull when one of your friends / enemies leaves their cell phone unattended in your presence. I won't give it away, but they are sure to feel the wrath of this one and will not be able to blame it on your concretely. Brilliant!

Android has several features built into the platform that improve user experience but require extra attention to prevent a security breach. By modifying these settings, you can drastically reduce the possibility of someone exploiting your device or intercepting information.

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

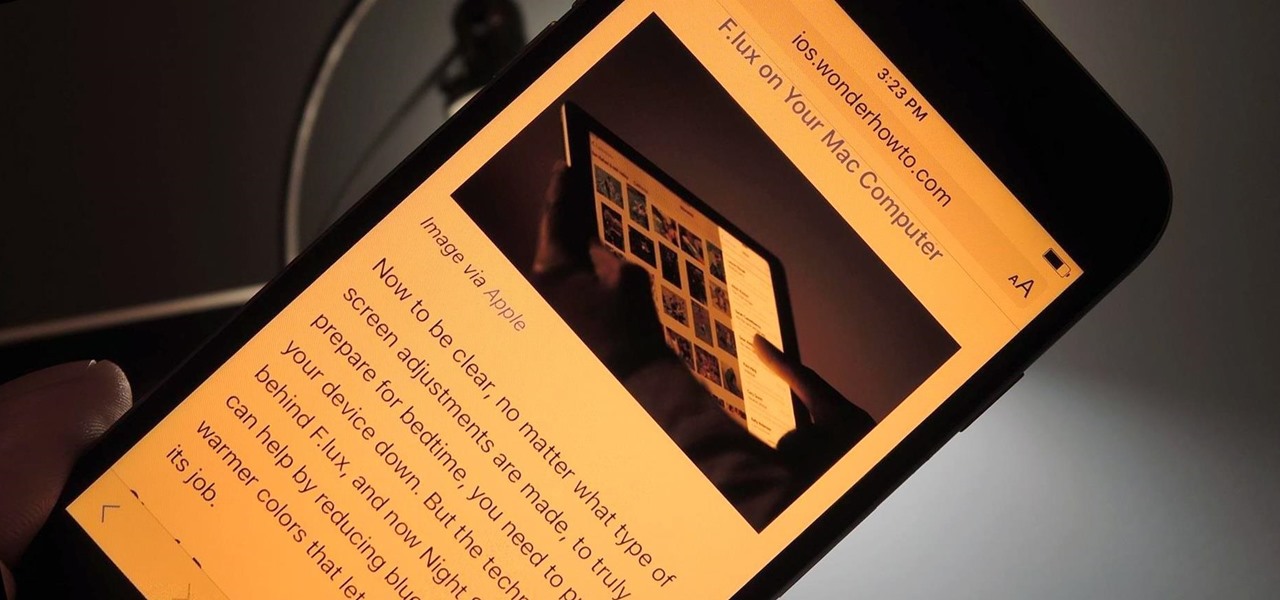
If you left your iPhone sitting unlocked, or have friends and family that like to play pranks, you may be stuck with an overly orange screen out of the blue. Or worse, your screen is normal most of the time, but seems to randomly change its tint in certain parts of the day.

Animal lovers, especially dog owners, know that pets are a part of the family, but it's often incredibly frustrating to know if and when something just isn't right with our furry companions. If you're out and about most of the day, your dog will be so happy to see you when you come home that you may have no idea they were tired and listless all day long, which can be a sign of health problems for your pup. This is where FitBark comes in.

Our dog has tons of energy and always wants to play. However, play time can be exhausting to the humans of the house. We found out a few months ago that the dog loves to play ‘chase the red dot.' Boredom leads to creativity, so we attached a laser pointer to her head with a bandana and small piece of tape. This kept her continuously occupied until we removed it after 20 minutes. I assume you could try this with a cat if you were daring enough – good luck with that. Caution: Laser pointers (ev...

Although sleep mode and screen savers contribute to the security and energy preservation of my MacBook, it can become a nuisance when they initiate unwelcomely. Yes, I could just change these settings in System Preferences, but to do this every time I momentarily leave my Mac unattended would be tedious, to say the least.

The Digispark is a low-cost USB development board that's programmable in Arduino and capable of posing as a keyboard, allowing it to deliver a number of payloads. For only a few dollars, we can use the Digispark to deliver a payload to a macOS computer that will track the Mac every 60 seconds, even bypassing security like a VPN.

Epic Games just released update v3.4 for Fortnite Battle Royale on all four platforms. This new version brings a number of UI changes, performance improvements, and bug fixes, but the addition that will get the most players excited is a new weapon: the Guided Missile.

Apple's once flawless mobile operating system has seen its fair share of bugs recently. From Messages and Wi-Fi settings crashing to having your photos and contacts exposed, iOS has been standing on shaky ground for a while now.

Do you ever walk into a nice boutique, a friend's house, or a fancy restaurant, and think, “I wish my house smelled like this”? Because I sure do.

Hopefully you never have to deal with a grease fire, but if it happens, how you handle it is important. A grease fire isn't like a regular fire, and trying to put it out the same way can make it worse. Grease fires are caused by letting oil get too hot, so the best way to prevent them is to never leave your kitchen unattended. Oil smokes before it burns, so if you see your pan start to smoke, take it off the heat before it has a chance to catch fire. If you're outside grilling, you can add a ...

Snapchat was created for the sole purpose of removing evidence from your mobile that a photo or video ever existed. That way, snoopers can't find any of these questionable selfies in your photo gallery. Of course, there are plenty of ways around this safeguard, but it's still more private than the standard social networking app.

Even though smartphone audio quality has improved in recent years, the tiny built-in speakers aren't always loud enough. But if you want to turn the volume up to 11, all you need is a few household items to make a rig that will amplify your phone's speakers throughout the whole house.

Coffee shops are a relaxing place to get work done on your laptop; there's free Wi-Fi, fresh coffee, and people generally leave you alone. Inevitably, those cups of coffee will go straight through you, resulting in a much-needed bathroom break. But while you're attending to your bodily functions, who's attending to your MacBook?

I may not be a parent just yet, but I've dealt with enough worrisome mothers to know that keeping a watchful eye over your child is of the top-most importance. Since most people cannot afford to stay right by their child's side 24/7, developers are always looking for ways to make the pain of stepping away a little less stressful for parents.

If you're anything like me, you probably think it's borderline sacrilege to even think about a sandwich or a burger that doesn't have a layer of smooth mayonnaise. But I don't just keep a jar of it in my fridge for lunch—it's also there for practical purposes.

Kitchen tools are a personal thing. One hard lesson for me to learn is that just because something is popular doesn't mean that it's right for me. Take the slow cooker, for instance. Many rave about it, but I never cottoned to the thing. However, the more research I do, the more I think the pressure cooker might be a game changer for my cooking style.

Leaving your computer unattended, whether at home, work, or a coffee shop, even for just a short while, is enough time for someone to steal it or look at your personal files. While there are ways to deter thieves, it's a little harder to keep snoops away.

Sometimes, doing the right thing is way more difficult than it should be, like trying to return a lost smartphone. Despite having the best intentions, it's often hard to track down the rightful owner, especially if the device is armed with a passcode. On the other hand, there are plenty of people who see an unattended iPhone or Samsung Galaxy S3 as a chance for profit. In 2011 alone, the number of lost and stolen cell phones in America was worth over 30 billion dollars. That's right, billion....

If you have children, then you know firsthand how many crayons parents end up buying. There is no such thing as using a crayon until it disappears. Kids use crayons until they are a nub, and then they toss the crayon aside, never to use it again.

As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers.

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

Most people are familiar with the decline of honeybee colonies around the world. Among other threats, Colony Collapse Disorder (CCD) is eroding the capability of honeybees to maintain their hives and provide their services to human farmers.