
How To: Fix 'Error 53' on Your Bricked iPhone
Apple has finally addressed and issued a fix for Error 53, a "safety" mechanism that would prevent your iPhone from booting if you had certain repairs done outside of Apple's official channels.


Apple has finally addressed and issued a fix for Error 53, a "safety" mechanism that would prevent your iPhone from booting if you had certain repairs done outside of Apple's official channels.

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

It's becoming more and more apparent that Siri continually drops the ball when it comes to lock screen security. In the past, Siri was exploited in iOS 7.0.2 to send messages without needing a passcode. Then in iOS 7.1.1, Siri was use to bypass the lock screen again to access contacts, make calls, and send emails and texts.
Thousands of history files, cookies, other unwanted files stored in your system as logs and other formats. To manually check each one is difficult. New computers are too fast by processor behavior, after some times of working it comes to slow performance.

As we all know, our attention spans are much shorter now that we're accustomed to getting information and news in tiny snippets via text messages, tweets, instagrams, and other constant updates.

Face ID does an excellent job with keeping your iPhone safe, boasting a million-to-one odds against unauthorized access when compared to Touch ID, which is 20 times less secure. However, it's far from being truly hands-free, as you still need to swipe up the lock screen once it detects your face to access apps. But if you have a jailbroken iPhone X, this issue can easily be remedied.

When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called rpi-hunter, hackers can discover, access, and drop custom payloads on any weak Pi connected to the same network.

Up until now, experiencing augmented reality through Vuzix's next-generation Blade 3000 smartglasses would have required a trip to a tech conference where the company has an exhibition booth.

An update to the iFramed social media gateway app for iOS adds an augmented reality feature called JuxImage that gives its users Snapchat-like photo and video effects.

As it turns out, your Android apps are pairing together to share your data without asking for your permission first. Researchers from Virginia Tech developed a tool called DIALDroid to monitor exchanges of data between Android apps over the last three years, and what they've found is quite alarming.

Kryptowire, a company specializing in mobile security solutions, released a report on Tuesday, November 15 that exposed firmware in a number of Android devices that was collecting personally identifying information (PII) and uploading it to third-party servers without users' knowledge.

It started in Australia, and now seems to have made its way statewide—hackers are remotely locking iOS and Mac devices, holding them for a $100 ransom. Users awoke to the loud "lost iPhone" ringtone, with a message on their lock screen stating that "Oleg Pliss" has hacked their device, and that "they" will unlock it after being sent $100 through PayPal.
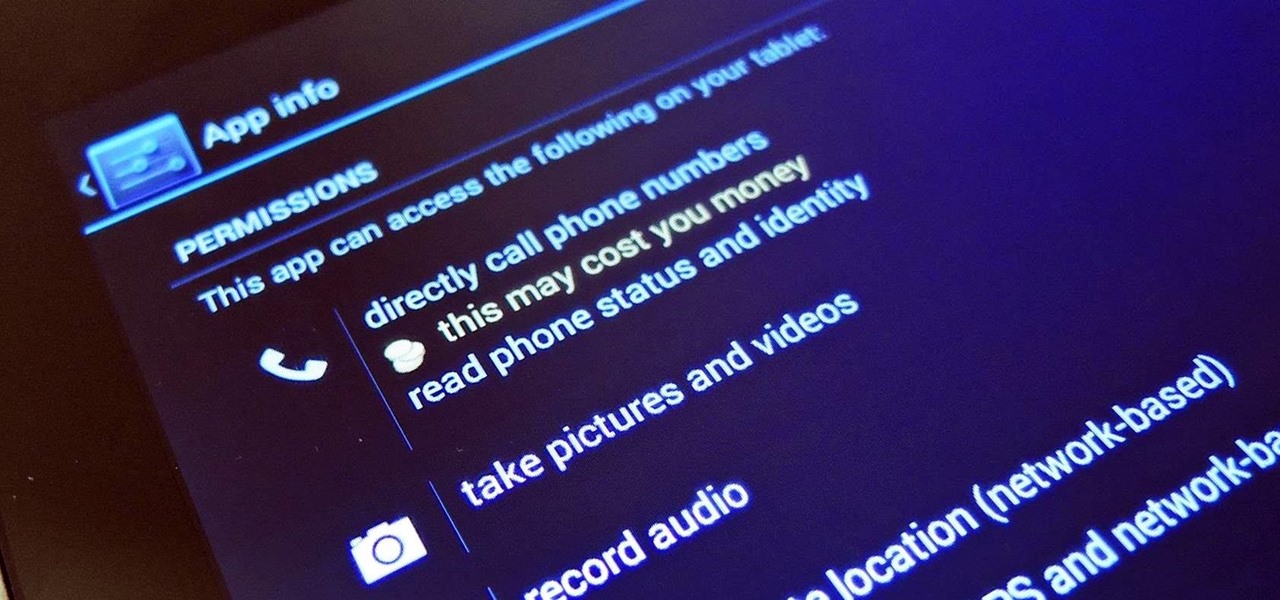
Privacy has been a heated topic in recent months, with everyone now up in arms over unauthorized leaks and exposures. And guess what—tablet and smartphone users are just as vulnerable.

International, T-Mobile, and Verizon customers all share something in common—their carriers provide unlocked Wi-Fi tethering for free. Of course, you still pay for the data used, but they don't charge you extra simply for using your Samsung Galaxy S4 as a wireless hotspot.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.
Not all threats to our privacy come from hackers thousands of miles away. Often, we just want to keep our data safe from those around us, who may snoop in our phones or demand we reveal our secrets. That's where BlackBerry Locker comes in.

Messaging apps can be a double-edged sword. Not only do they let you interact with other people, but they also let you go back and reminisce on past exchanges. However, that same archive can be used against you in certain situations. Luckily, Signal can be manipulated to remove any record of past messages.

With so much money on the line, it's no surprise that cryptocurrency exchanges are prime targets for cybercriminals. Because of this, the importance of keeping your personal account as secure as possible cannot be overstated. Binance is one step ahead in this regard, as it requires you to enable two-factor authentication to keep your bitcoins and alt-coins safe.
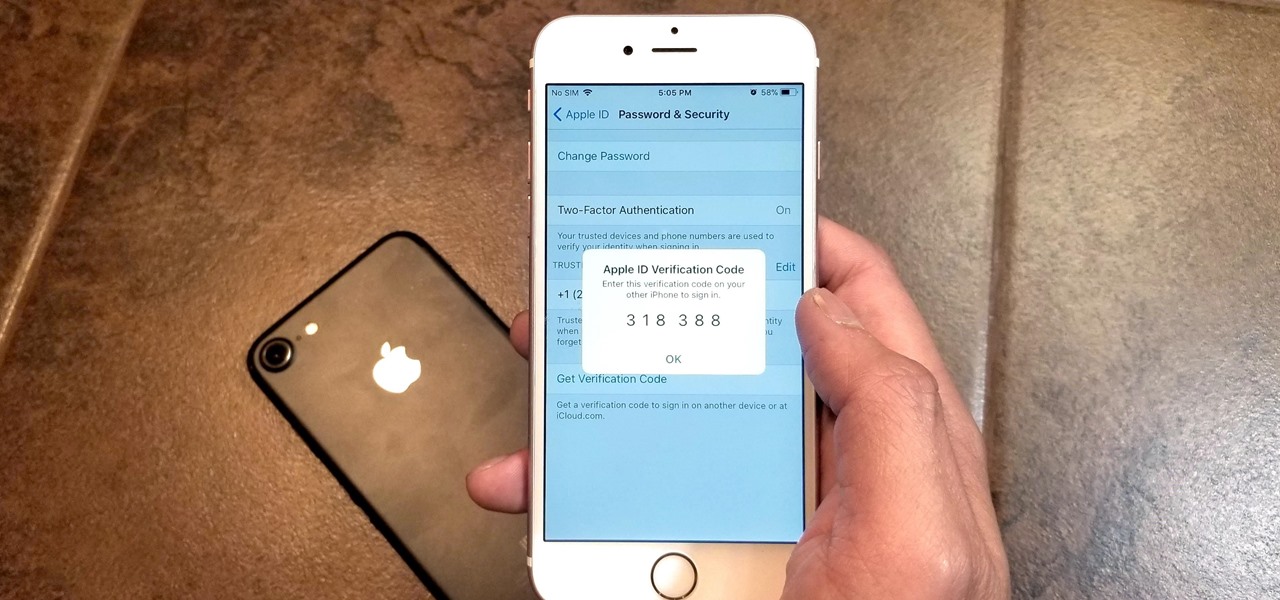
Two-factor authentication has been around since iOS 10. It's a handy option that adds an extra layer of security to your iPhone and makes its almost impenetrable security even stronger. This feature has remained intact in iOS 11 and iOS 12, and thanks to the straightforward nature of iOS, is relatively easy to enable.

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

Hello, hackers and engineers! Today we are going to dive a tiny bit deeper into the secrets of psychology, and how we can use them with hacking and social engineering attacks.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

When I first found out about Nreal, back in the spring of 2018, the most interesting thing about the company's story was the founder's background. Chi Xu, the CEO and founder of Nreal, previously worked at Magic Leap as a software engineer.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

For many, the stock version of Android is often considered the epitome of what the operating system should look and feel like by default. It's clean and clear of unwanted extra apps that come pre-installed with the system, provides a fluid and fast user experience, and runs on just about any device that has an unlocked bootloader to install a custom ROM with the stock version ready to go.

If you've ever received an email from a sketchy address purporting to be Uber, asking you to sign in with your credentials, you might be a phishing target. Hackers use a fake login page from real-looking domains to trick you into giving up your account information, and while it's been an issue in the past, Uber is making it more difficult on cyber thieves with the addition of two-step verification.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.
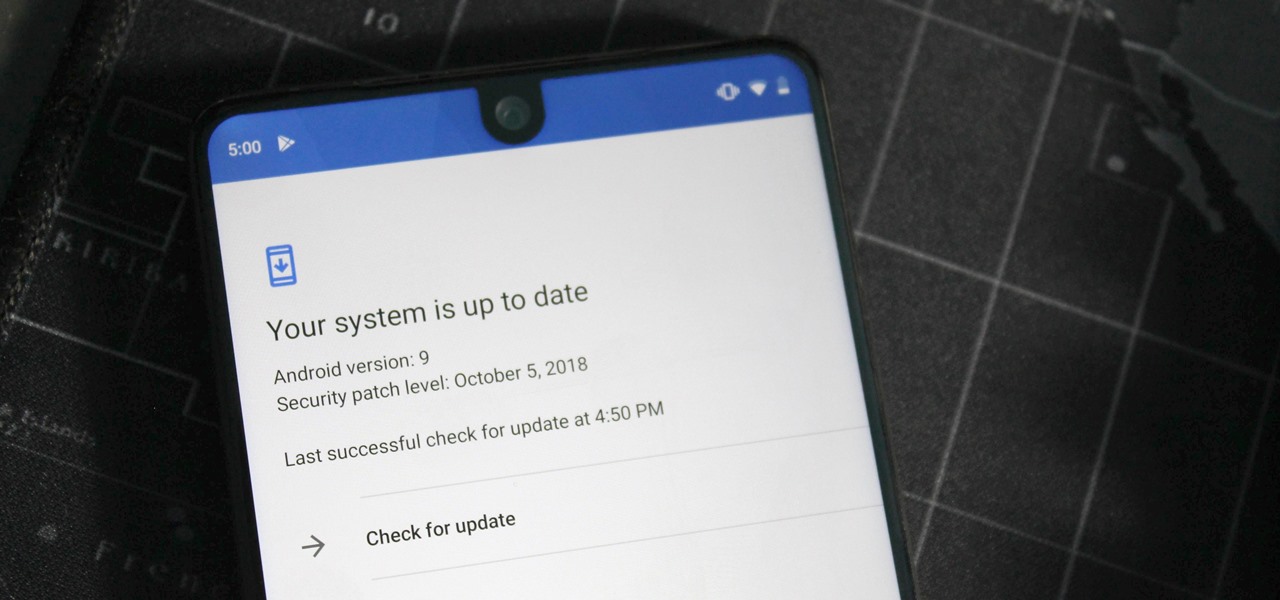
One of the issues with rooting your device is the inability to update your phone via OTA. Any security patches or software updates pushed out by the OEM are lost because your bootloader is unlocked. However, you still can update your device, it just a take a bit more effort.

Although the Galaxy Note 9 is an amazing phone, many members of the Android community won't even look at it. This isn't just because of the Samsung Experience skin, but the large amount of bloatware that comes with this device. However, with a little work, you can remove all of it.

Although the Essential PH-1 got off to a rocky start, thanks to steady updates, it has slowly become one of the best Android phones to come out in recent years. For $499, the Essential Phone is a cheaper Pixel, receiving updates almost as soon as the Pixel lineup does. What's more, you get a phone with an easily unlockable bootloader, which is the first step to rooting.

Earlier this year, we got our first taste of Android Pie in the form of Developer Preview 1. As with all past Android previews, DP1 was limited to Google devices — but at Google I/O 2018, Google announced that Developer Preview 2 would be accessible to other devices, including the Essential PH-1.

After setting up your phone, there are a number of things you should do immediately before download your favorite apps. Specifically, now that your data is on the device, you need to take steps now to ensure it's both protected and retained. Fortunately, most of these steps are a one-time process.

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.

Welcome back to control structures, part two featuring the three types of loops. Here we go! What Is a Loop?

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.


Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.