
How To: Easily Share Your Complicated Wi-Fi Password Using Your Nexus 5
If you're like me, then you've got an incredibly complicated Wi-Fi password with uppercase and lowercase letters, numbers, and special characters.


If you're like me, then you've got an incredibly complicated Wi-Fi password with uppercase and lowercase letters, numbers, and special characters.
Most of the time, the LED notification light on the front of your Android device just sits there doing nothing. Other than that brief period of time between when you receive a notification and when you turn your screen on, it's practically useless for anything other than showing when your charger is plugged in.

Buried deep in the code of many Google apps is a set of debugging options. These options, which are designed for developers to help test the way their apps interact with Google's own, are normally hidden from view.

One of the coolest features of the Galaxy S5 is its IP67 certification. This means that the S5 is internally impenetrable to dust and can be submerged in water for thirty minutes at a depth of one meter. It's definitely a handy feature for folks who've lost a phone to a toilet in the past.
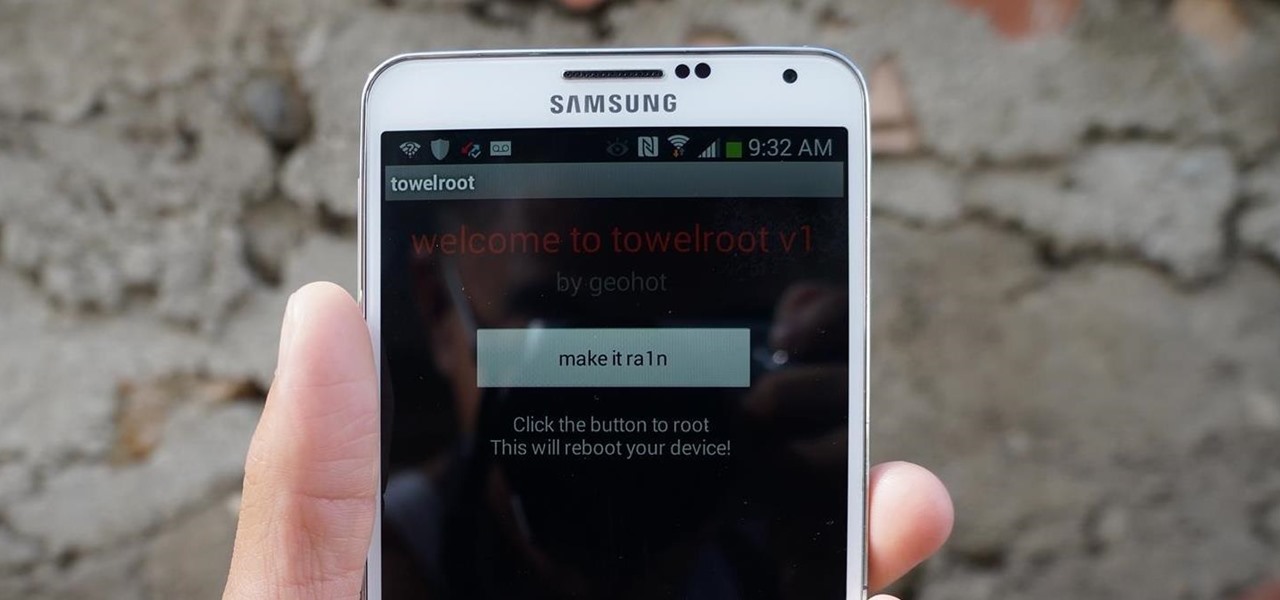
AT&T and Verizon customers, it's finally happened. After many long months of waiting, and a fairly significant bounty up for grabs, your Galaxy Note 3s can finally be rooted! Best of all, it may be the simplest method for achieving root we've ever encountered.
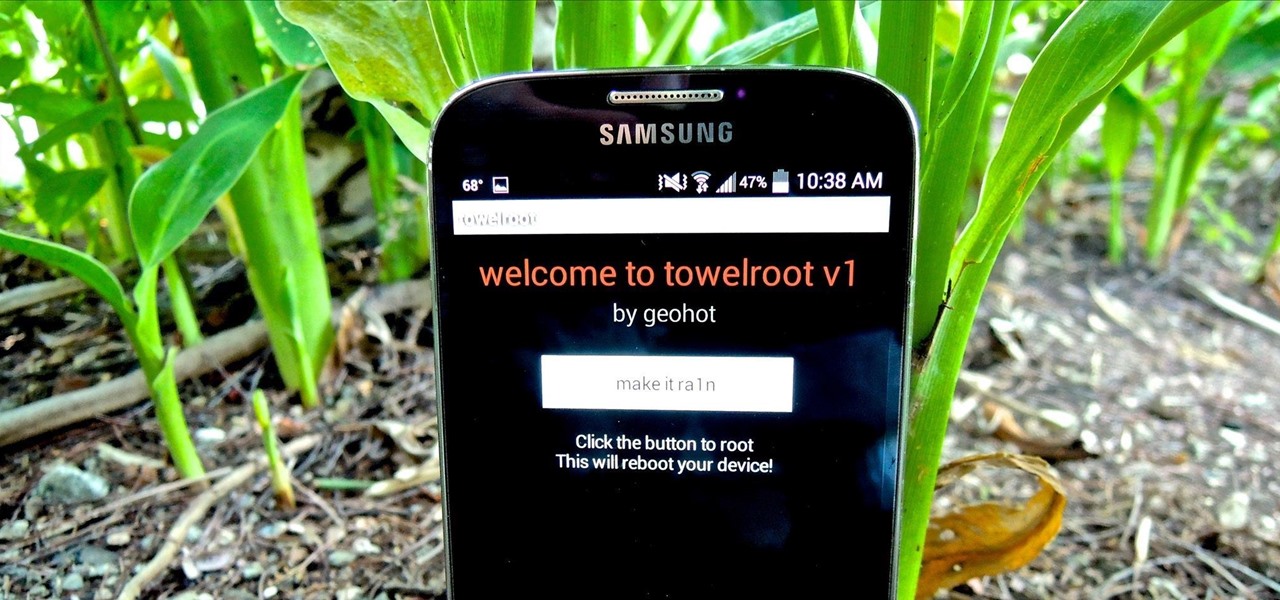
Something pretty awesome happened over the last couple of days. George Hotz, better known as Geohot, the infamous hacker known for jailbreaking iOS and exploiting the Sony Playstation 3, has brought joy to owners of just about all Android smartphones and tablets, especially those on AT&T and Verizon.

One draw that Samsung's Galaxy S line has had over the Google Nexus 4 and 5 and the HTC One (though the M8 appears to be following suit) is expandable storage. Pop a microSD card into the slot and you have extra storage for music, photos, and even apps themselves in some cases.
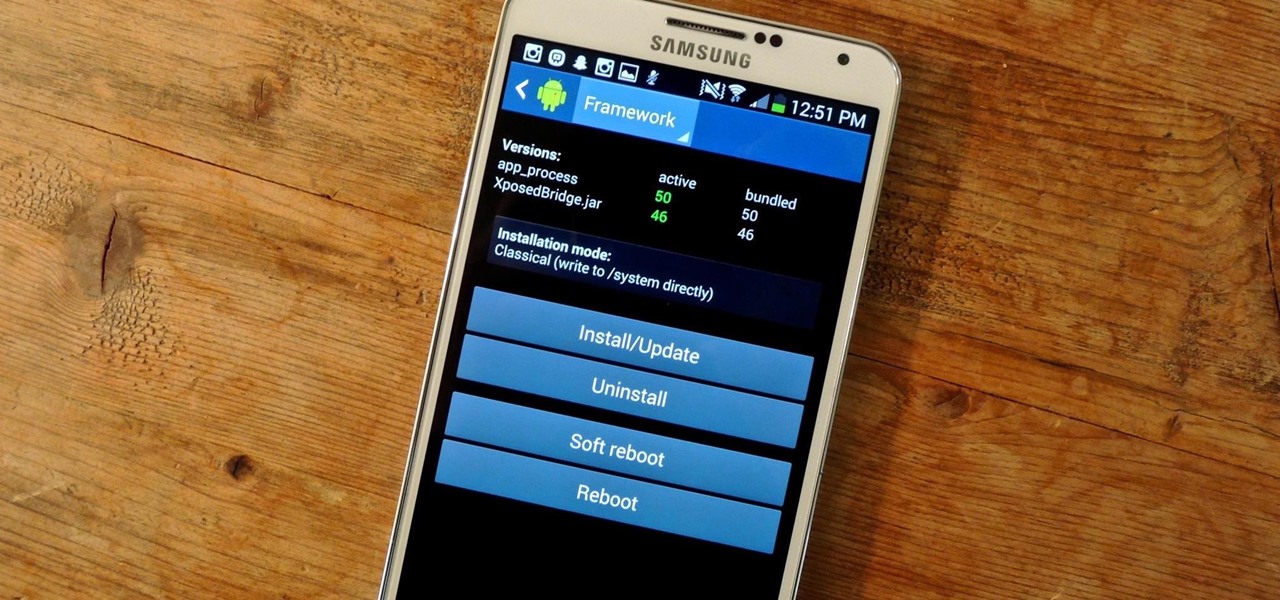
Allowing us to easily get features that would otherwise be available only through flashing mods and custom ROMs, Xposed Installer has been a godsend since its development, simplifying the sometimes tasking and potentially harmful process of changing the core components of Android's operating system.

Last week, Apple issued an iOS 7.0.6 update that fixed a serious security vulnerability that could allow hackers to steal passwords, read emails, and get info from other SSL-encrypted communications.

Update 1: Evad3ers have released a statement to the jailbreak community, claiming that the safety and security of their users is the most important thing to them and that all speculations about malware being encoded into the jailbreak is simply not true. You can read the full letter over at Evasi0n's site.

While the Samsung Galaxy Note 2 has an integrated LED for notifications, it only works for a few things, like charging and low battery, and it only flashes two main colors (red and blue) when the screen's off. As someone that usually has their phone on silent or vibrate, it's hard to tell when I receive important messages or notifications. Sure, I could set a specific vibration or ringtone for individual apps, but that can quickly get annoying and distracting, especially at work or school.

I rarely ever turn my desktop off. For starters, it takes a few minutes to boot up, which I hate, and secondly, putting the computer to sleep is perfectly adequate. You really only need to completely shut down your computer every once in a while.

UPDATE: A patch to fix the exploit has been released. Download it here.

These days, news papers, online editorials and magazines are filled with news on Iran and Syria. Of course, that is expected, as such sources need to stay current to stay in the game. My concern is that most of these articles talk about what to do about these situations.

Did you know there's a way to make animating your own cartoons that's way easier than it looks — and that you can learn all the skills you need from home? Whether you want to pick up a fun, creative hobby over the holiday season or learn the skills to start working in animation, The Ultimate Cartoon Animator 4 Pro Mac Bundle will have you quickly making your own cartoons. Right now, it's on sale for 74% off, at just $49.99 (regular price $196).

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

We're wild for whipped cream in our coffee, atop our brownies, and in-between wafer cookies, so we always have some in our fridge. To be specific, we always have homemade whipped cream in our fridge, because the taste is just so much better than the pre-made stuff.

As a self-proclaimed chocoholic, any day with chocolate mousse in it is a good day in my book. And thanks to prominent chemist Hervé This, one of the founding fathers of molecular gastronomy, chocolate mousse is not only easy to make every single day—but only requires two ingredients.

Wait, don't dump that milk! It may have a slightly sour smell and be expiring tomorrow, but you can still put it to good use by making sour milk jam.

The octopus is famous for its bulbous head, enormous eyes, and four pairs of long arms. The stuff of legends and nightmares, octopi have been featured in stories, artwork, and meals galore. But how do you eat this distinctive looking, bilaterally symmetrical sea creature?

Why, for the love of God, do people keep inventing ridiculous devices that make the simplest things more complicated in the name of convenience? This may be a rhetorical question that will forever go unanswered—because these crazy gadgets just keep rolling out, one after the other.

In my opinion, there is no candy greater or more timeless than Sour Patch Kids. They're the ultimate treat: sweet and refreshing, yet sour and tangy. These contrasting flavors are what make Sour Patch Kids perfect for the people of all ages—especially your kids. So let's make dishes that incorporate this awesome candy into your cooking rotation!

We've had the pleasure of test driving the ASUS Transformer Book T100T for the last couple of weeks, and for a $400 Windows 8 machine, it's impressive to say the least.

Many people find Steampunk problematic for a whole host of reasons, not least of which is the glorification of an era of Western history that featured institutionalized slavery, racism, sexism, elitism, and many more -isms.

By now you're probably already an expert at creating cover images for your Facebook Timeline, especially if you've taken advantage of those free Facebook cards that were (and still are) being offered. But just in case you need some help making eye-grabbing cover images, there's a few tools you can try out to streamline the process.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.
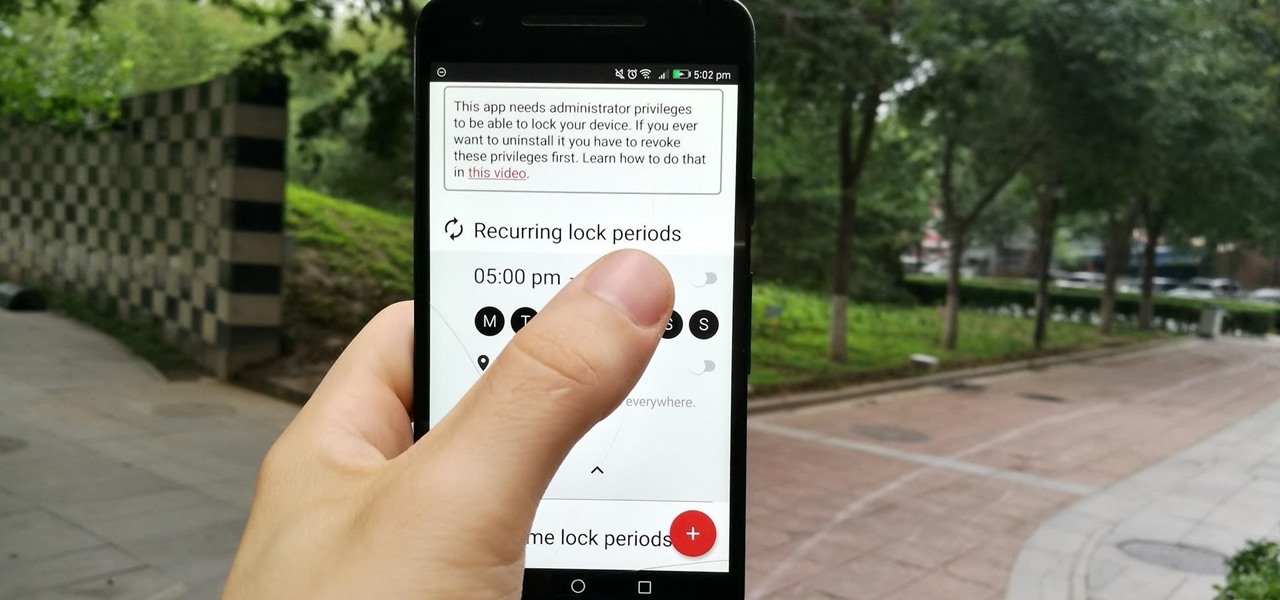
The OnePlus 7 Pro comes with a new Zen Mode feature to help increase your concentration and reduce distractions. It takes things a step further than Google's Digital Wellbeing by disabling your device and stopping sounds. But even if you don't have a OnePlus, you can now get this distraction-free feature on any phone.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).
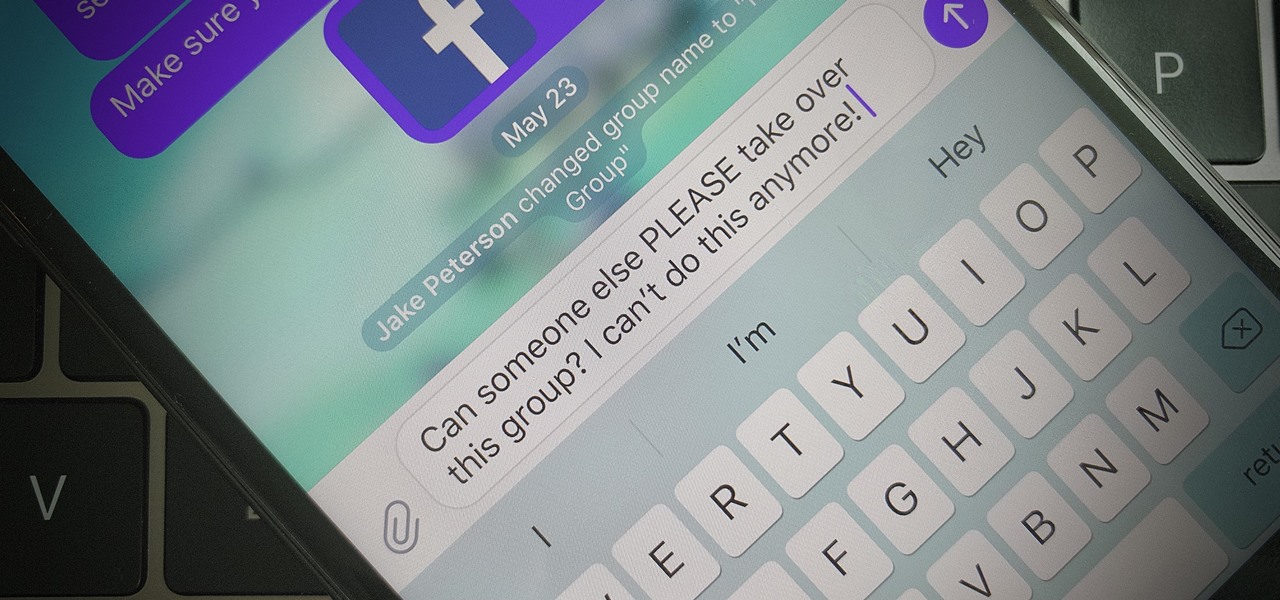
Group chats are fun, effective ways of staying in touch with the many people in our lives. Whether it's the local friend chat or the group from work, we rely on these groups to keep connected. Running one of these group chats, however, can be a monster task. If you're feeling overwhelmed with administrative responsibilities, why not pass on that burden to another member of the Telegram group?

Android 9.0 Pie moved the status bar clock from the right corner to the left to accommodate phones with notches, but there's one major downside for Samsung users: since no Galaxy phones have a notch, all this did was take away space for the notification icons that would otherwise start from the left corner.
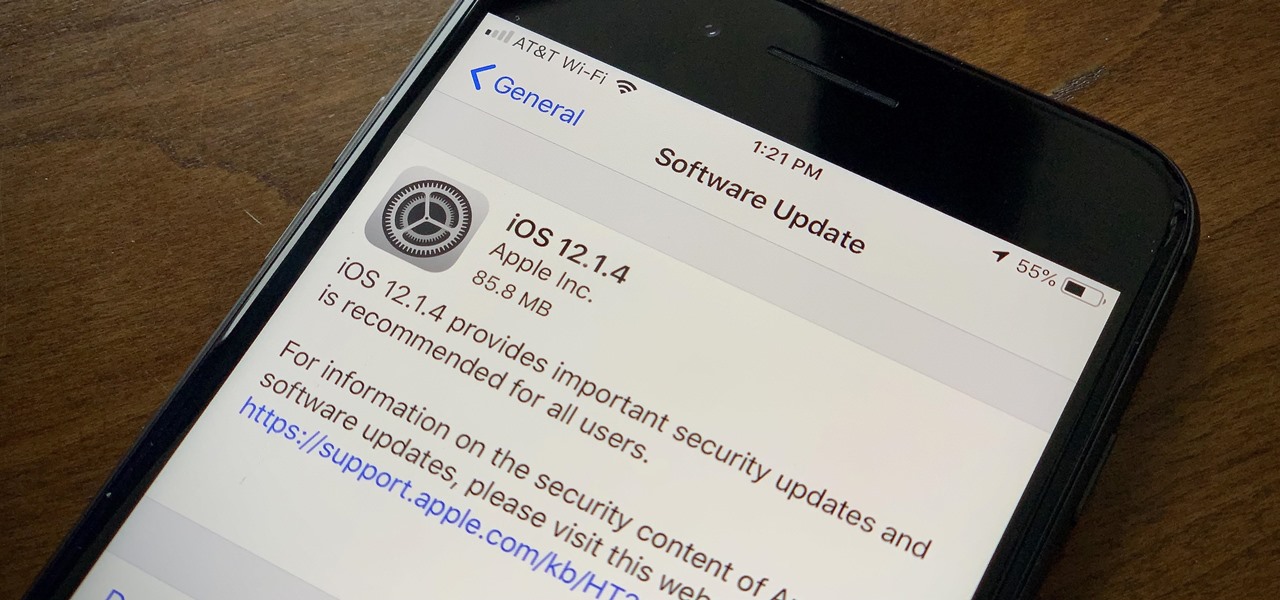
Apple found itself in serious trouble last week when a teenager discovered a critical FaceTime bug that threatened the security of nearly every iPhone user. The bug enabled a user using Group FaceTime to access either the microphone or the camera of a recipient before they answered the call. According to Apple, the issues have been fixed in an iOS 12.1.4 update released Thursday, Feb. 7.

Although next week will mark the late David Bowie's 72nd birthday, his fans and admirers are the ones receiving a gift in the form of an augmented reality app that explores the artist's career

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.