Many of the beauty products you buy at drug and department stores are loaded with potentially toxic ingredients like parabens, while their active ingredients are made of things like glycolic, lactic, malic, and alpha hydroxy acids and retinoids, which are all derived from foods.

Find out how you can kick butt in Obsidian Entertainment and SEGA's video game Alpha Protocol. The RPG and action hybrid came out on June 1st, 2010, and is available on the PlayStation 3 (PS3), Microsoft Windows (PC), and the Xbox 360. This video game walkthrough series from Mahalo focuses on Alpha Protocol for the Xbox 360.

Even the biggest fan of Mario Kart may have reservations about traveling to Super Nintendo World in Japan in the middle of a worldwide pandemic to experience the augmented reality-enhanced roller coaster ride that recreates the game in real life.
So, you've just plugged in your new Chromecast with Google TV. You lean back to watch a TV show or movie and you notice that people look kind of ... odd.

QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into custom QR codes.
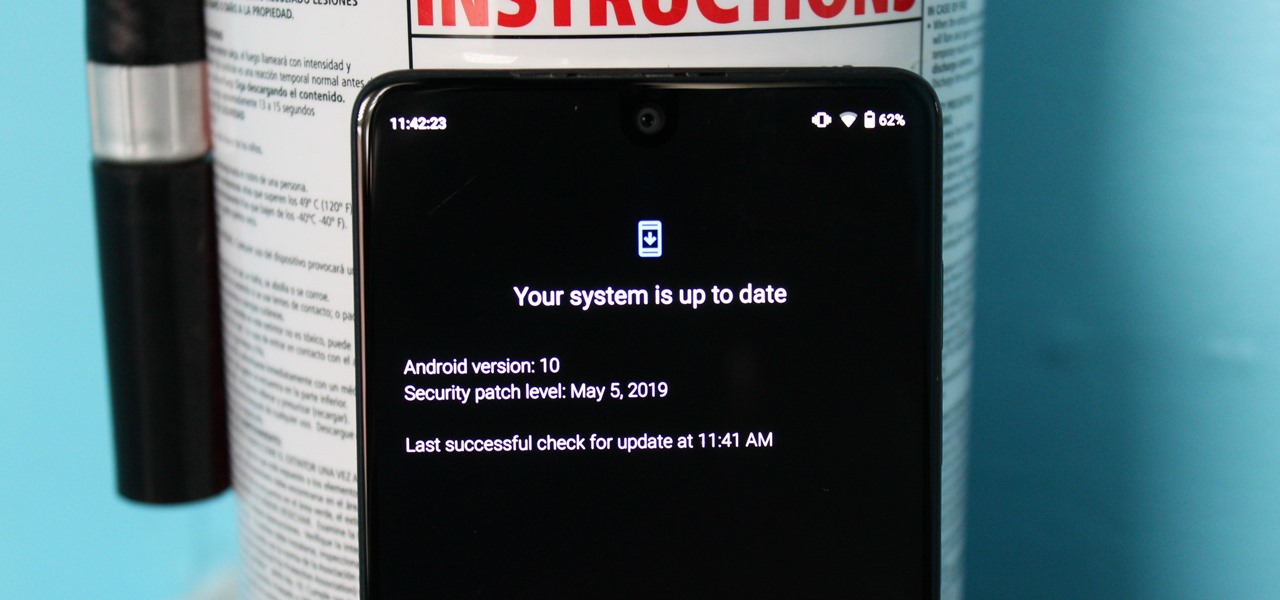
Like last year's beta release of Android Pie, Google has allowed the Android Q Developer Previews to support some non-Pixel devices. Announced at Google I/O 2019, there are 15 non-Pixel smartphones eligible for the Android 10 Beta, including 2017's Essential PH-1.

When you want to install a new tool or game on your iPhone, you go straight to the App Store to do so — but it's not the only place you can get apps from. Some developers use back alleys to get their apps to you, while others can trick you into installing them without giving it much thought. This can lead to malicious software running on your iPhone, software you'll want to get rid of asap.

The rise and fall of Meta, the Silicon Valley-based augmented reality startup that looked to challenge the likes of Microsoft's HoloLens, and others, took just six years.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

Hey, all you Instagram lovers, haters, or people who have no choice but to submissively bow down to the social app giant for other reasons, you've come to the right place. Today, I'm going to walk you through a very simple marketing trick to start boosting traffic to your IG account.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

The first written account of "stock" as a culinary staple goes back to 1653, when La Varenne's Cookery described boiling mushroom stems and table scraps with other ingredients (such as herbs and basic vegetables) in water to use for sauces. But really, the concept of stock has probably been around for as long as people have been using water to boil food.

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

Unless you're vegan or lactose intolerant, butter is an indispensible ingredient. However, butter is no one-trick pony. It can take many forms that make it even more versatile and useful in the kitchen. Clarified butter has many advantages over regular butter—but there are certain cases where you shouldn't use it. More on that later.

It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography.

All kinds of people pretend to be someone they're not on the internet, including scammers, people attempting to wind others up, hackers and web predators. Almost all of these people will leave bases uncovered and they're all easy to expose when you understand how to. Here are my favorite ways of finding out when somebody is lying quickly. Image Search

As the iOS 18 beta continues, Apple's still investing time into fixing up iOS 17. Compared to iOS 17.4 and iOS 17.5, which both had over 30 new features and changes, iOS 17.6 is a relatively small software update for iPhone. But there are still some important things to know about.

An iPad can serve as a second screen for a Mac via Sidecar, available since iPadOS 13, but Apple isn't the only manufacturer to support such a feature. Samsung has had a similar tool since One UI 3.1 that lets you turn certain Samsung Galaxy tablets into second displays for your PC — and there's a hidden feature that expands it to more tablets and even Samsung Galaxy smartphones.

This was a busy week in the tech space. After everyone got over the major announcements of Apple's latest, we examined the metaverse through the lens of Hollywood, and then took a closer look at Facebook's first smartglasses.

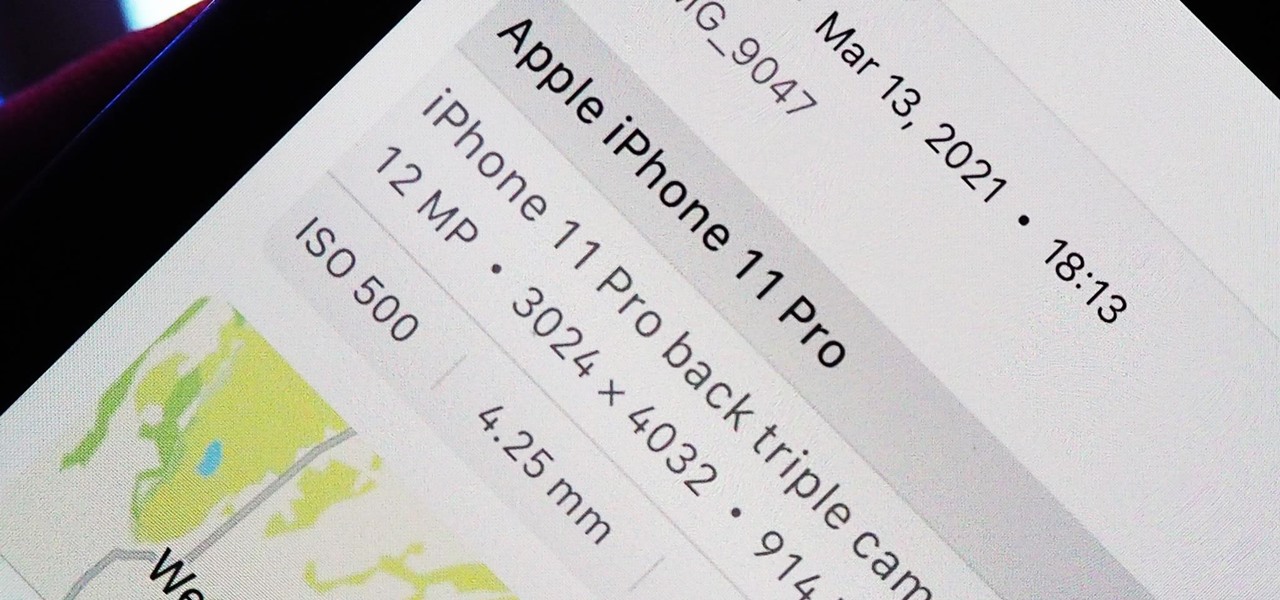
Apple introduces several new privacy settings with iOS 15, including the ability to better manage the metadata in your photos. With just a few taps, you can effectively spoof a photo's geolocation and change its creation date and time, providing a sort of disguise over your personal information. If you constantly take and share photos, it's a welcomed feature, but its results are not permanent and can be reversed.

Almost 190 secret characters are hiding behind your iPhone's default keyboard, and I'm not talking about what you see after tapping the "123" or "#+=" keys. These special composite characters can include accents, dots, and other diacritics, and you'll even see some strange typographical characters like the section sign, inverted marks, and per mille symbol. Here's how you find them.

Snapchat's first foray into augmented reality started with the selfie camera and face-tracking technology, with the app's AR capabilities expanding from there.

When approaching a target, having a precise and detailed plan of attack is absolutely necessary. One of the main goals is to increase the attack surface since the more opportunities there are for exploitation, the greater the chances of success. Subdomain enumeration is one method used to increase the attack surface, and we'll be using a tool called Subfinder to discover hidden subdomains.

Android has not had the best reputation for privacy and security, though Google has made strides in those departments in recent years.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

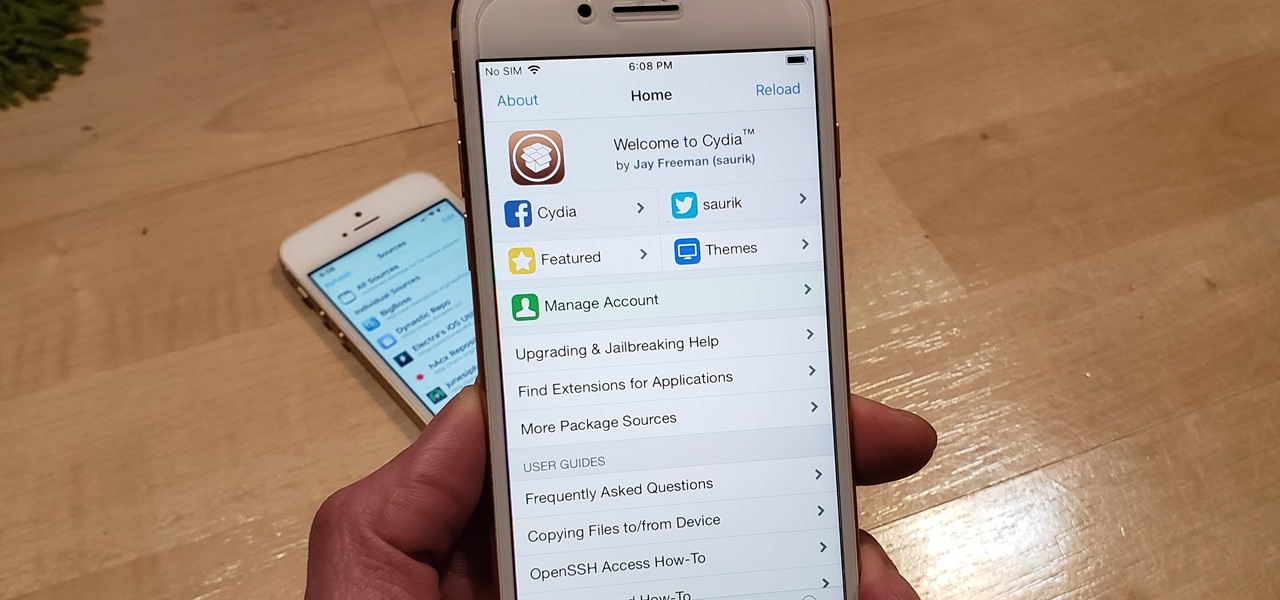
With Unc0ver, Pwn20wnd was the first to jailbreak an iPhone and iPad running iOS 12 versions. While it initially couldn't work on all devices, it's an entirely different story now. Unc0ver currently works up to iOS 13.5 for most A7 to A13-powered devices. Plus, Chimera, another jailbreak tool, supports a similar range of models on iOS 12 to 12.3 and iOS 12.4.

The Pixel 3 runs stock Android, so you might think that since you've used an Android device before, you should know your way around the new phone by default. But Google has actually added several great Pixel-exclusive software features to its flagships, and not all of them are easily discoverable.

This time last year, we got our first taste of what mobile app developers could do in augmented reality with Apple's ARKit. Most people had never heard of Animojis. Google's AR platform was still Tango. Snapchat introduced its World Lens AR experiences. Most mobile AR experiences existing in the wild were marker-based offerings from the likes of Blippar and Zappar or generic Pokémon GO knock-offs.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform OSINT (open-source intelligence) gathering tool.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

Black Mirror, Netflix's technology-horror anthology, never fails to provide thought-provoking entertainment centered around emerging and futuristic technologies, and the third season's second episode, "Playtest," delves deep into the worlds of mixed, augmented, and virtual reality. While designed to leave you haunted by the end, offering a more "evil" narrative than we'll likely see in our actual future, the episode explores possibilities that aren't as far off as one might think.

This year, like every year before it, Black Friday sales are starting earlier than ever. A lot of stores will be opening their doors as early as 5pm on Thanksgiving to get a head start on the madness (and it really is madness). As we've discussed in the past, one of the keys to emerging victorious on Black Friday is to plan, plan, plan. So, we've compiled some of the best deals in tech, gadgets and appliances to help you prepare for battle.

Generative AI, or GenAI, is the hottest thing in tech at the moment, particularly for its ability to create content,p including essays, images, and videos. After Microsoft added its own GenAI tool to its Bing web search engine, Google is eager to follow suit, and you can be one of the first to try out Google's new GenAI search tool.

Now that Bard — Google's response to the revolutionary ChatGPT generative AI chatbot — is out in the wild, it's beginning to let its freak flag fly.

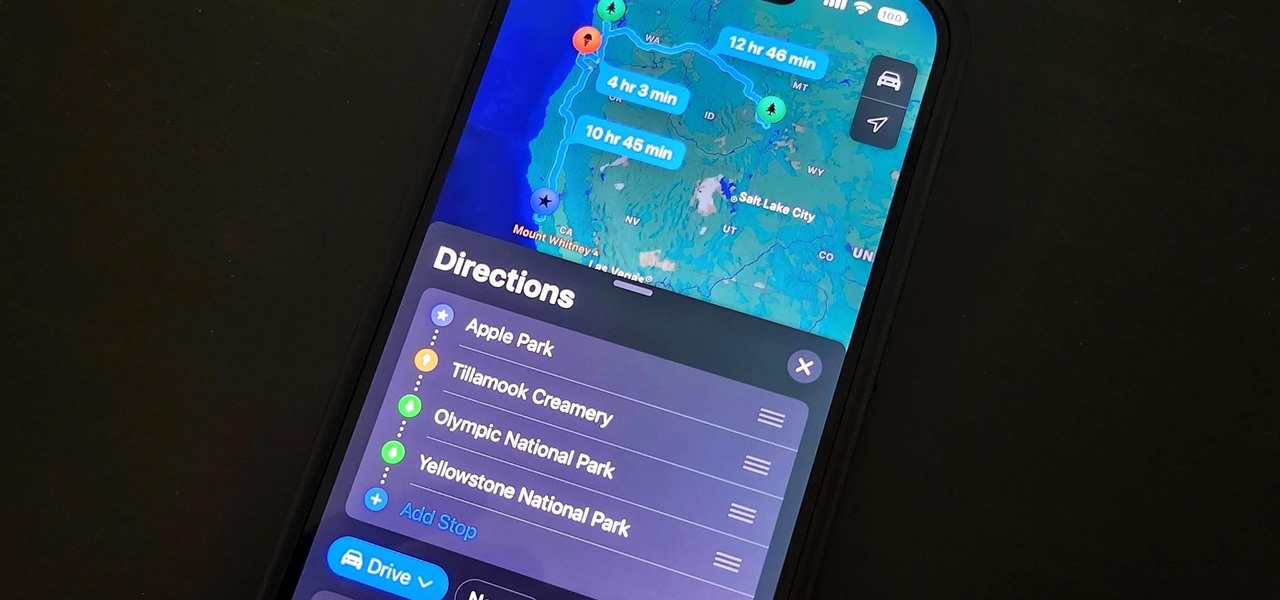
One thing Apple Maps always lacked was the ability to add stops along a route while planning a trip. Navigation would help you travel from the beginning location to the final destination, and the only places you could add between that were pit stops like banks and ATMs, coffee shops, convenience stores, eateries, fast food, gas stations, and parking lots. That all changes in Apple Maps' latest update.