Like in the original Black Ops, there are a bunch of funny and cool Easter eggs built into Call of Duty: Black Ops 2. Most have been discovered, like the Atari arcade invincibility on Nuketown 2025, but perhaps you didn't know about Thor's hammer?

Try this delicious recipe for tomato chutney, Indian style. Watch this how-to video and learn how simple it is to make. It goes great with just about any Indian recipe you make.
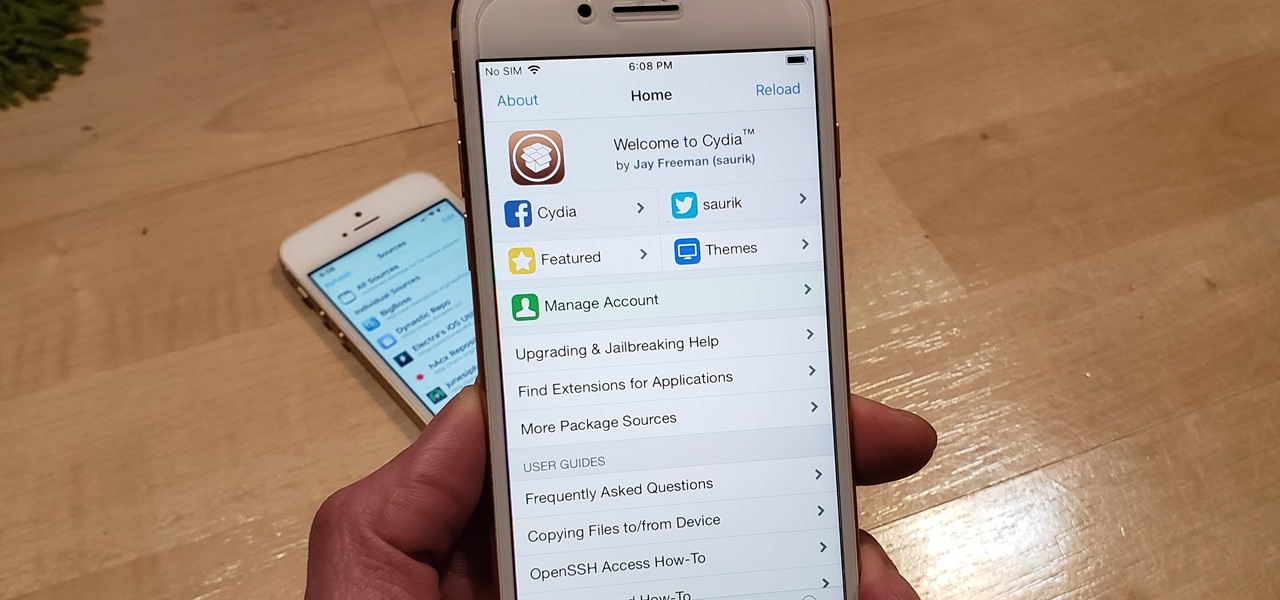
With Unc0ver, Pwn20wnd was the first to jailbreak an iPhone and iPad running iOS 12 versions. While it initially couldn't work on all devices, it's an entirely different story now. Unc0ver currently works up to iOS 13.5 for most A7 to A13-powered devices. Plus, Chimera, another jailbreak tool, supports a similar range of models on iOS 12 to 12.3 and iOS 12.4.

Augmented reality has given companies worldwide great powers for innovating business practices and engaging customers, but on Monday, Honda demonstrated that with great power, also comes great social responsibility.

With the release of the Pixel 2 XL and the iPhone X, smartphones have hit a new high not just in price, but also raw processing power. These new flagships not only cost more than twice as much as an Xbox One or PlayStation 4, they have also become almost as powerful as far as gaming goes. Because of this, a lot of games once reserved for consoles and PCs have made their way to our smartphones.

UPDATE: It was previously reported that the OnePlus 3T 128 GB in Gunmetal would be discontinued. GSM Arena received an official rebuttal from the company which noted that the phone is not discontinued, but rather, out of stock. Though, it seems like the company has more of a problem keeping track with what its reps report, rather than its phone supply.

With No Time to Die, the 25th installment in the James Bond saga, arriving in April and Black Widow, the first solo film for the Marvel Cinematic Universe's own secret agent, following a month later, what better way to get in the espionage mood than some augmented reality spy gaming?

Mobile gamers who grew up on J.K. Rowling's fantasy epic have yet another reason to rejoice, as Jam City's Harry Potter: Hogwart Mystery is slated to touch down on both iOS and Android on April 25. But if you can't bear the wait, there's a little hack you can do to give the game a try right now.

With the hype surrounding the iPhone 8, Apple's announcement that it's developing driverless software, and the new iOS 11 beta out, it seems like the tech giant is constantly in the news. Today, Apple's continuing this streak with updates for its iWork app suite on iOS and macOS.

Google announced several new devices (as well as updates to existing devices) that will take advantage of the company's augmented and virtual reality platforms.

You know how you can go to those little Mexican restaurants that have the refreshing drink machines full of that sweet rice drink, horchata? Did it ever seem like some kind of arcane powdered mix or a secret recipe you would never know? If you've ever found a recipe, did you imagine it needing all these crazy ingredients that you can't find for cheap at your local supermarket?

When approaching a target, having a precise and detailed plan of attack is absolutely necessary. One of the main goals is to increase the attack surface since the more opportunities there are for exploitation, the greater the chances of success. Subdomain enumeration is one method used to increase the attack surface, and we'll be using a tool called Subfinder to discover hidden subdomains.

Malevolent hackers can divert your incoming calls and texts to any number they want, and they don't need to be a criminal mastermind to do it. Even friends and family members can reroute your incoming calls and messages so that they know exactly who's trying to reach you, and all it takes is seconds of access to your iPhone or wireless account. These secret codes can help uncover them.

The still-unfolding story of China's Nreal augmented reality startup continues to develop, with each turn uncovering another unexpected wrinkle.

The venture arms of Samsung and Verizon Ventures, along with Comcast, are among the strategic investors backing startup Light Field Lab and its glasses-free holographic displays in a $28 million Series A funding round

A new profile on Apple's exiting design chief Jony Ive, the man behind many of the company's most successful products, paints a fuller picture of what led to his departure.

Magic Leap has earned a reputation for overt secrecy, but as it nears the highly-anticipated launch of the Magic Leap One, the company is spilling some of the beans. This week, we get a heaping helping of information on the Lumin OS, as well as a couple of great demos.

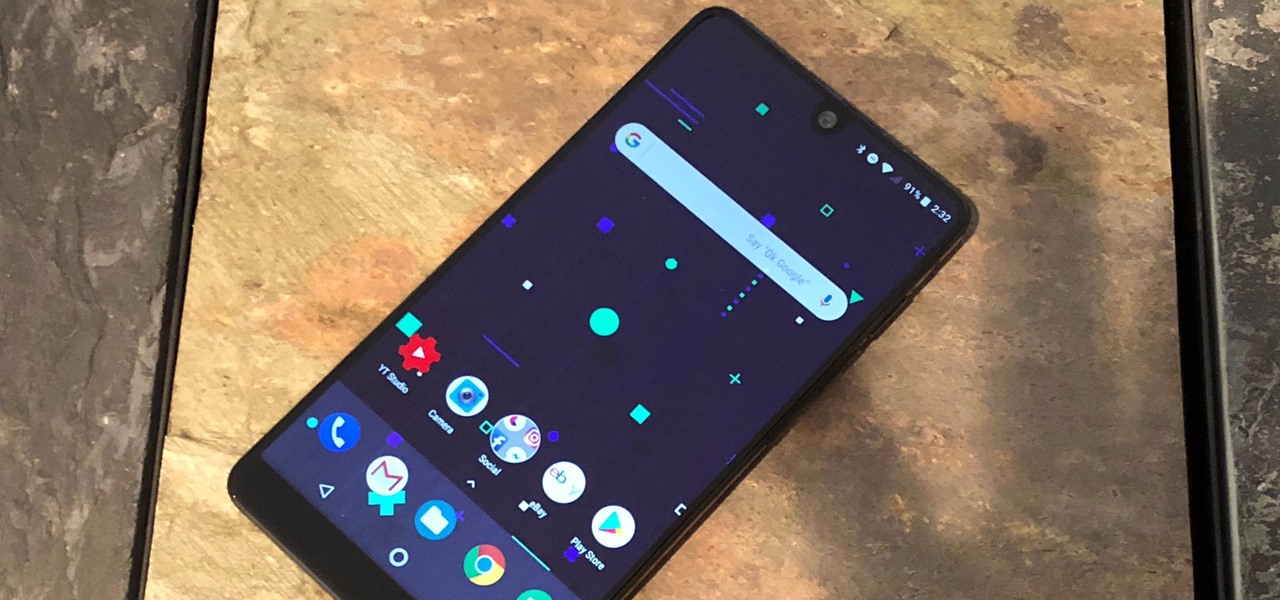
We've been running the Essential Oreo Beta on our PH-1 over the past week and compiling a list of important changes. If you're interested in getting the Beta yourself, we even put together a quick guide on how to do that. Now that we've ran down the best new features, let's take a look at all of the bugs and performance issues in Android 8.0.

To the best of my recollection, Fruit Ninja was one of the first touchscreen games that appeared to really take advantage of the new paradigm of user input, turning the player's finger into a produce-slicing katana.

If you've ever wanted to scour the basement of a Hollywood hotel looking for evidence of a gruesome murder spree, this new AR experience might be the game for you.

If you are fond of going live or watching live videos on Facebook, then you've probably experienced a number of viewers commenting. Sometimes these comments are good. Sometimes ... well, sometimes we could all go without them.

We all know Google's Image Search to be our trusty little companion when it comes to browsing through ideas on the web. Now, Google is adding on "style ideas" to its search feature to help you boost your "style IQ" every time Google catches you snooping through new handbags on the market.

We've all heard the cliches: always look at the glass as half full; a smile can change your entire day; and there's always a silver lining.

A couple months ago, I attended a Pokémon-themed party. Everyone dressed as their favorite Pokémon or trainer, Poké balls flew around the backyard, and more importantly, there was a lot of Poké booze. My friend who created the colorful drinks you see below informed me that they were infused with Skittles. This, my humble readers, was a defining moment in my life.

The number of passwords I have for different websites and emails is easily in the triple digits. And if I had to actually remember all of those individual passwords, I would be locked out of accounts on a daily basis.

While conducting an OSINT investigation, it's important to be able to pull in information based on any clue you uncover. In particular, license plate information can turn up everywhere, from photos to live data to on your own street. You could use that data to find the VIN, see if a Tinder date has hit anyone, find out who's blocking your driveway, and so on. Skiptracer can help get the ball rolling.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

Now that its first developer conference is in the rearview mirror, Magic Leap continues to nurture its content development community, this time with an assist from strategic investor and retail partner AT&T.

In its goal to push the visual quality of real-time rendering to a new level, Unity is starting the new year off right by releasing a sneak peek at its upcoming interactive rendering improvements via a short, three-minute first-person interactive demo called "Book of the Dead."

For younger children, a day at the playground is not complete without some sandbox time. Long a favorite of children and parents, sandboxes could also be sheltering dangerous pathogens.

As much as you try to safeguard your personal information, you may have made a small mistake by giving your phone number to the wrong entity, and now you're being bombarded with dozens of spam calls every day. To help parse your call log and reject the proper numbers without answering or trudging through voicemail, a good reverse phone lookup app is needed.

As drug-resistant bacteria become more commonplace, researchers are looking for new antibacterial strategies to disrupt disease-causing microbes. Some scientists are working to create new drugs, while others are trying out drug combinations. Another group, however, are ditching pharmaceuticals altogether and experimenting with non-drug alternatives.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

If you're ever faced with a situation of handing over your iPhone to law enforcement (or getting it taken forcibly), whether by the police, feds, or court system, there are things you can do to prevent them from getting access to all that potentially self-incriminating data. And it takes less than a second.

Apple's iOS 12 has finally landed. The big update appeared for everyone on Monday, Sept. 17, and hiding within are some pretty amazing augmented reality upgrades for iPhones, iPads, and iPod touches. We've been playing with them ever since the iOS 12 beta launched in June, and here are the things we learned that you'll want to know about.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.