
News: Soil Microbes Are Key to Understanding Climate Change on (& in) The Ground
That soil under your feet is not just dirt. It is teeming with life that may not change as fast as we would like when challenged by global warming.


That soil under your feet is not just dirt. It is teeming with life that may not change as fast as we would like when challenged by global warming.

One of our favorite kitchen items, hands down, is a good old-fashioned wooden spoon. It's practical, versatile, and can last for decades if cared for properly. There are specific ways to nurture wooden utensils in order to keep them from cracking and to help them maintain their glossy sheen.

We here at Food Hacks are all about saving you, our wonderful readers, time and trouble in the kitchen. So when I saw that Barilla had come out with their Pronto line of "One Pan, No Boil, No Drain" pasta, I had to give it a try. While no-boil lasagna noodles have been around for a while and allow the pasta to essentially cook en casserole, this relatively new addition to the pasta scene includes elbow, penne, spaghetti, and rotini varieties that allow for usage in a greater variety of pasta ...

hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack.

When the Chromecast first came out about a year ago, developers were quick to find a way to root the streaming device. Google was almost as fast, however, in updating the Chromecast's firmware to close the loophole that this method used.

The new LG G3 is the latest Android flagship-level device to be released this year, and it's ready to give the Galaxy S5, HTC One M8, and the OnePlus One a run for their money. Sporting a gorgeous 5.5-inch QHD display, 3GB of RAM, and a huge 300mAH battery, the device looks great and has tons of power to boot.

The point of ice in your cocktail is to make it cold, right? Yes and no.

Even the biggest fan of Mario Kart may have reservations about traveling to Super Nintendo World in Japan in the middle of a worldwide pandemic to experience the augmented reality-enhanced roller coaster ride that recreates the game in real life.

When you want to install a new tool or game on your iPhone, you go straight to the App Store to do so — but it's not the only place you can get apps from. Some developers use back alleys to get their apps to you, while others can trick you into installing them without giving it much thought. This can lead to malicious software running on your iPhone, software you'll want to get rid of asap.

The rise and fall of Meta, the Silicon Valley-based augmented reality startup that looked to challenge the likes of Microsoft's HoloLens, and others, took just six years.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

The first written account of "stock" as a culinary staple goes back to 1653, when La Varenne's Cookery described boiling mushroom stems and table scraps with other ingredients (such as herbs and basic vegetables) in water to use for sauces. But really, the concept of stock has probably been around for as long as people have been using water to boil food.

Unless you're vegan or lactose intolerant, butter is an indispensible ingredient. However, butter is no one-trick pony. It can take many forms that make it even more versatile and useful in the kitchen. Clarified butter has many advantages over regular butter—but there are certain cases where you shouldn't use it. More on that later.

All kinds of people pretend to be someone they're not on the internet, including scammers, people attempting to wind others up, hackers and web predators. Almost all of these people will leave bases uncovered and they're all easy to expose when you understand how to. Here are my favorite ways of finding out when somebody is lying quickly. Image Search

Almost 190 secret characters are hiding behind your iPhone's default keyboard, and I'm not talking about what you see after tapping the "123" or "#+=" keys. These special composite characters can include accents, dots, and other diacritics, and you'll even see some strange typographical characters like the section sign, inverted marks, and per mille symbol. Here's how you find them.

Snapchat's first foray into augmented reality started with the selfie camera and face-tracking technology, with the app's AR capabilities expanding from there.

Android has not had the best reputation for privacy and security, though Google has made strides in those departments in recent years.

This time last year, we got our first taste of what mobile app developers could do in augmented reality with Apple's ARKit. Most people had never heard of Animojis. Google's AR platform was still Tango. Snapchat introduced its World Lens AR experiences. Most mobile AR experiences existing in the wild were marker-based offerings from the likes of Blippar and Zappar or generic Pokémon GO knock-offs.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform OSINT (open-source intelligence) gathering tool.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

Now that Bard — Google's response to the revolutionary ChatGPT generative AI chatbot — is out in the wild, it's beginning to let its freak flag fly.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highlight all of the features and changes.

You might have missed it, but the virtual keypad you use to enter phone numbers in your smartphone's dialer and contacts app isn't all numbers. Take a closer look, and you'll notice a few mysterious buttons you've likely been tuning out unconsciously. But it's time to stop ignoring them because each has a particular purpose that could come in handy one day.

Apple AirTags are super helpful for keeping track of your keys, backpack, and other frequently misplaced items, but there are some pretty clever things you can do with them beyond finding regularly used stuff.
The next big iOS version for iPad, iPhone, and iPod touch was revealed by Apple at WWDC 2018 and dropped for everyone on Sept. 17, 2018, less than a week after Apple revealed the new iPhone lineup. We've rounded up all the big picture items and secret features and changes we could find so you know exactly what to expect when updating to iOS 12 on your iPhone.

If you’re a dancer, athlete or just breaking in a new pair of shoes you know that blister can add pain and discomfort long after they’re formed. By keeping a blister sterile and away from further friction you can get your blister to heal quickly.

There are always those days when bread-lovers want a hearty savory bread to eat, but there isn't quite enough time to make a yeast bread. After all, yeast breads take anywhere from an hour to a full day for the first rise. Well, that's where this whole-wheat beer bread comes in! It doesn't take long to throw together and bake, but tastes delicious and is relatively healthy due to the use of whole wheat flour. If you don't like whole wheat flour, you can always substitute the same amount of pl...

Ingredients 1 small onion (4 ounces), cut in 1-inch pieces

This is a pretty versatile sauce, with an aromatic mix of roasted tomatoes, peppers, onions, garlic and scallions. And it's called romesco sauce, and can be used as a spicy red sauce, zesty spread or hearty dip. It's a little different than the classic Spanish romesco because it's spiced up with a jalapeño pepper and hot crushed peppers. Toasted almonds, fresh basil and thyme are added just at the end of roasting. Adjust spiciness to your liking and serve with grilled fish and meats.

Amy H. Hughes helps you make a vintage tile tabletop. Part of the fun of making this table was rooting through the tile crates with Rosi Zingales at Olde Good Things in New York City. Our first find was an 1890s 6-by-6-incher depicting a Spanish Colonial mission, for $45. This, we agreed, would be the centerpiece. Next were four flowered accents, $8 each, and 30 yellow-and-white marbled tiles from an old fireplace surround that we bought in bulk for $40. We also uncovered the wrought-iron tab...
Multiple airport screeners have been arrested for allegedly taking handsome bribes to look the other way while loads of illegal drugs slipped through security at Los Angeles International Airport, federal officials announced today.

Every Modern Warfare game has had bits of enemy intel for you to recover, and they're always hidden within the level. The few pieces I've uncovered across the series has always been through dumb luck. But if you want that 'Scout Leader' achievement, you'll have to find all 46 pieces of intel throughout the entire single player campaign.

Have an HTC smartphone? Chances are that some of your stored personal data has been hijacked by malicious apps on your device. Android apps that have permission to access the Internet, which is pretty much every ad-supported app out there, can snag valuable information such as email addresses, location history, phone logs, text messages, and more.

In the wealthy oil man's world of Arabian camel racing, the tradition of using child jockeys has been replaced with the use of small robo-jockeys in recent years. But after finally ridding the game of the mistreatment of children, the sport is now under scrutiny again. The Dubai police have discovered a new feature illegally added to the torturous, whip-endowed robots: hidden stun guns.
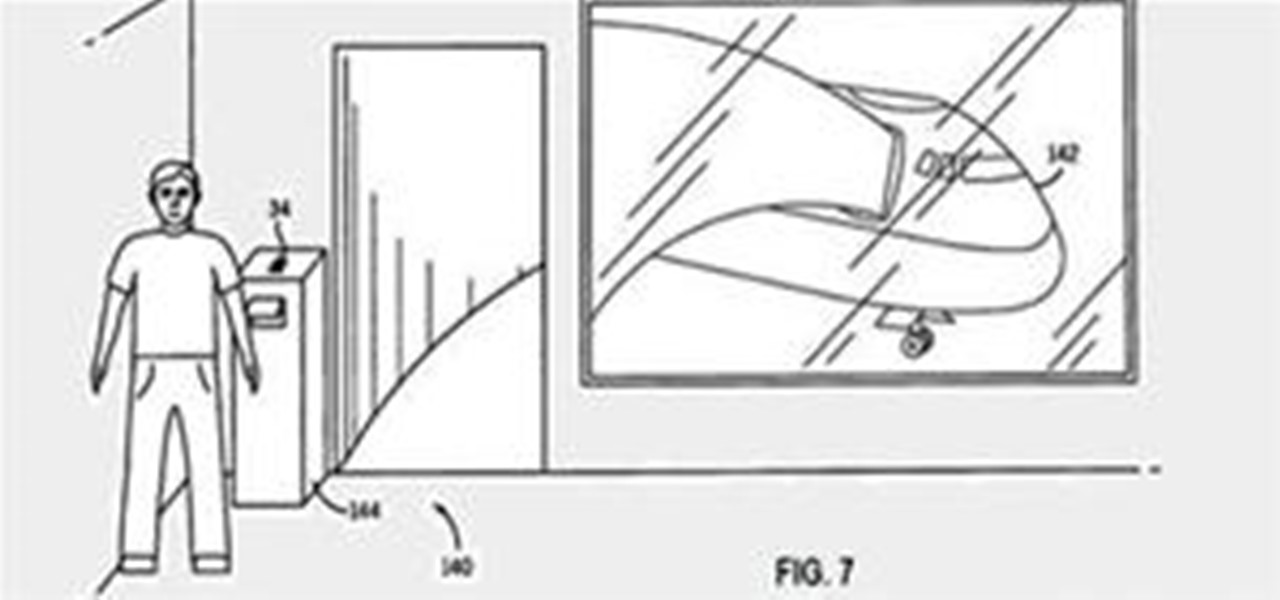
The folks over at Patently Apple have uncovered some very promising looking plans for a future iPhone app called iTravel. iTravel plans to cover ticket-buying, electronic check-in, car rentals, and possibly even Apple designed airport kiosks. Fingers crossed it comes out soon. Apple excels at making dummy-proof, intuitive, easy-as-pie user interfaces, and man, the airline travel process sure could use a little streamlining.

Paper shredder not working like it used to? Soak several pieces of paper in baby oil and run them through the shredder, which will help lubricate the blades and make them run smoothly for future shredding purposes.

No one likes having their home invaded, and sometimes you just don't want to have to wait those precious few seconds for someone or something to drown, suffocate, or burn up. This trap utilizes gravity to destroy anyone who may want to pillage your home, be they monster or player. No drowning or suffocating here... they just go splat at the bottom of a deep hole, and you can instantly forget about them.