Apple's new iOS 16 software update is finally here, and there are over 350 new features and changes for you to enjoy on your iPhone. There are major lock screen and home screen improvements, a pleasant surprise for the Contacts app, and tons of new upgrades to Safari, Mail, Messages, and more.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.
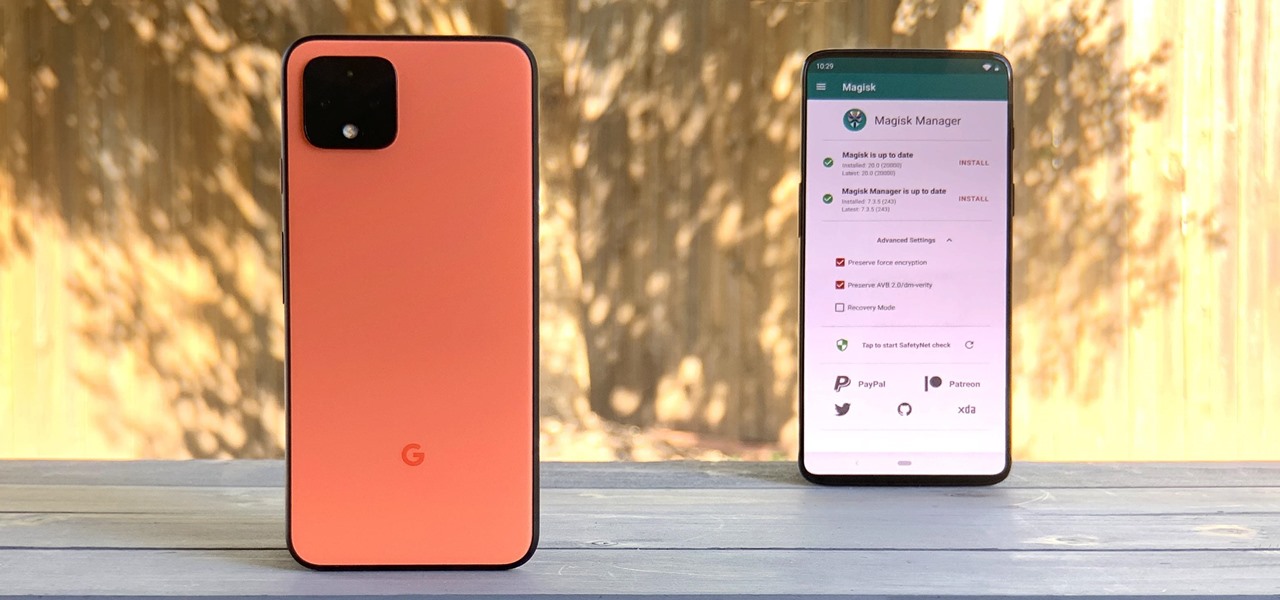
According to a study done by Kaspersky, 7.6% of Android users root their phones. That may not sound like a lot, but with over 2 billion Android devices out there, the math works out to over 150 million rooted phones — more than the total population of Russia, Mexico, or Japan — so root nation is an important demographic that deserves being catered to.

Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

Andre was enjoying the carefree life of a 12-year-old with his friends, riding his bike and playing sports, like all kids that age. Schoolwork wasn't hard for him, and his grades showed that.

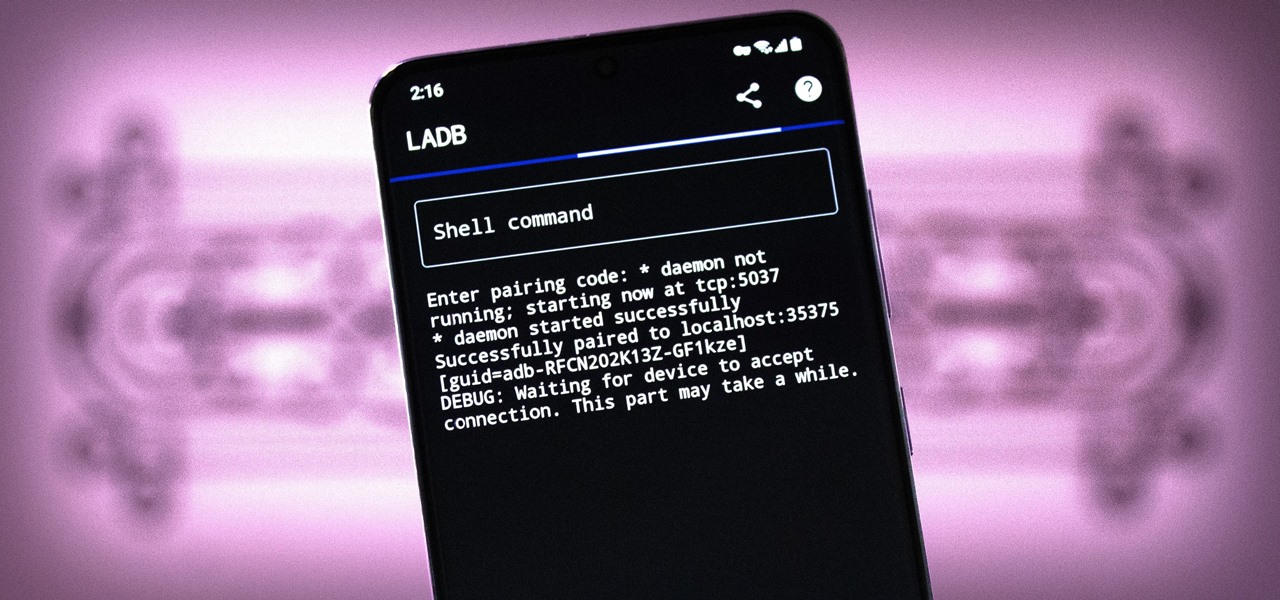
Bloatware is a problem on Android, and it's not just a Samsung thing. Removing apps that have the Uninstall or Disable button grayed out in Settings has always involved sending ADB commands to your phone from a computer, which itself was always such a pain to set up. Thankfully, that has finally changed.

There are three tiers to Android customization: things you can do by default, things you can do with ADB, and things you can do with root. While root is still pretty tricky to get, ADB mods just got a lot easier.

In the first guide, we laid the groundwork for our ultimate goal of uploading and running the unix-privesc-check script on our target. We identified an input field vulnerable to SQL injection and utilized Sqlmap to set up a file stager on the server. Now, we're ready to upload files and execute the script, so we can identify any misconfigurations that could lead to privilege escalation.

For many, phones are starting to replace televisions as the primary device for watching videos. Thanks to their portability and easy to use apps, it's often simpler to watch Netflix, Hulu, YouTube, or Prime Instant Video on the smaller screen. But not every phone is suited to fit this need, so we did some testing to find the best of the best when it comes to streaming videos.

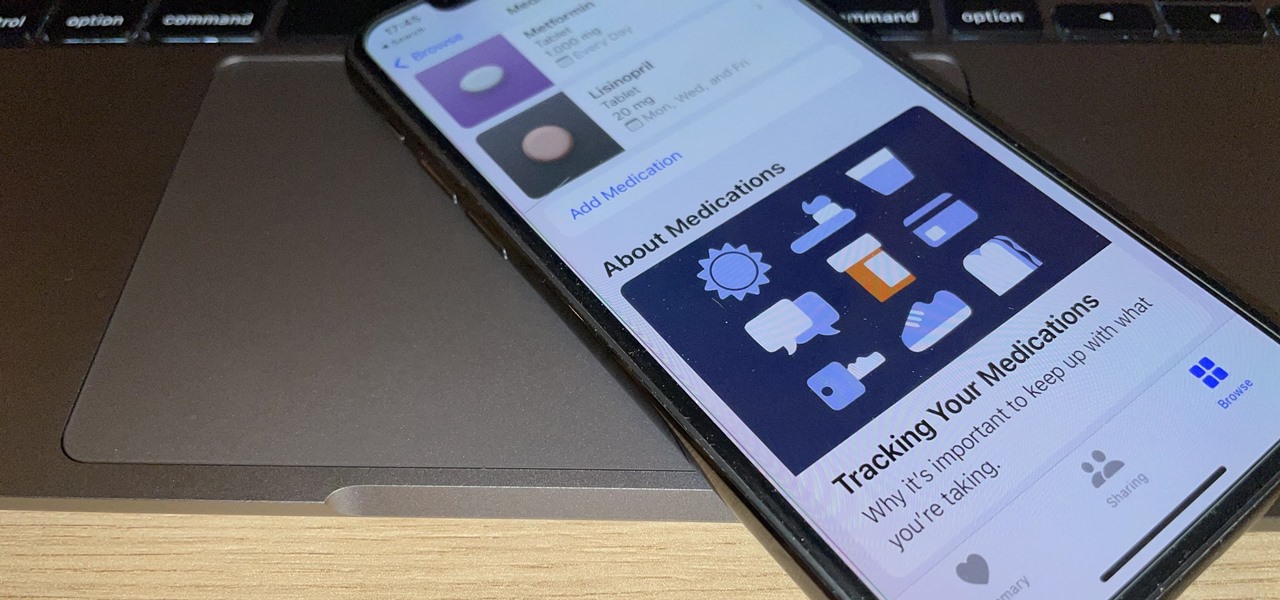
You've probably already been using iOS 16 on your iPhone for months, but there's a good chance you haven't found or explored everything the new software has to offer. Health-related features are usually the first to be ignored or go unnoticed, but they're essential to know about even if you don't plan on using them right away.

When Microsoft unveiled Mesh a couple of weeks ago, the move revealed a major part of Microsoft's next steps toward dominating the augmented reality space, particularly with regard to enterprise customers.

Network enumeration is one of the essential phases of an attack, but it can take a lot of time and effort depending on the size. We've all been spoiled by Nmap and similar tools, and while there is a learning curve involved, they are extremely useful. But there's also GoScan, a tool that builds upon Nmap, offering an automated way to enumerate networks and services quickly.

In the case of Apple Watch v. Fitbit, the winner comes down to the judge at hand. Apple currently offers two smartwatches — the Series 5 and the Series 3 — while Fitbit offers three models — the Fitbit Versa 2, Fitbit Ionic, and Fitbit Versa Lite. Whatever your assumptions about these devices are, throw them out the window, as each has something unique to bring to the table.

Phone in one pocket, wallet in the other? It's the classic combo guaranteed to give you more pocket bulge. But it's 2024. Half that stuff in your wallet is practically antique. It's time to finally ditch all the dead weight and get a MagSafe wallet for iPhone — and we've got the best picks to slim you down to the essentials.

The year 2020 was a pivotal span of time during which the word "virtual" took on a brand new meaning. Instead of referring to VR or augmented reality, the term was hijacked to describe meeting across long distances through a variety of software tools, most often through video.

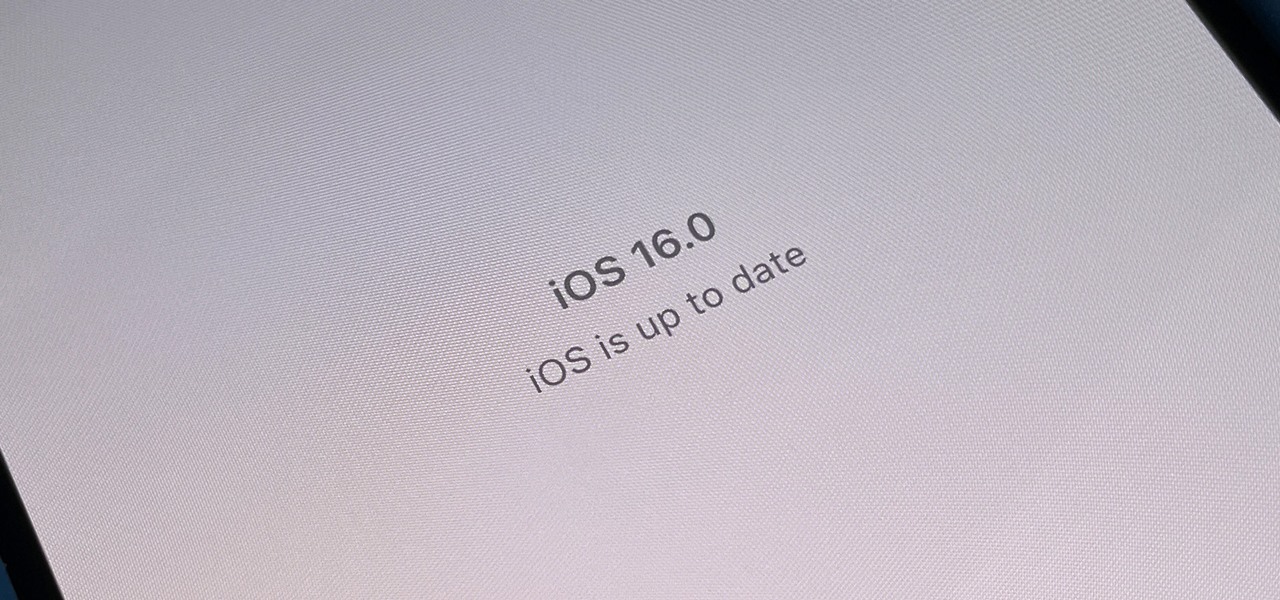
Apple's iOS 16.3 update for iPhone had impressive new features, but iOS 16.4 might impress you even more.

Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians across the web.

In this video demonstration you will see the work done on a GM 3.1 Liter V6; your instructor is replacing the cam cover seal. First raise the car into the air, remove the tire wheel assembly and place a jack stand underneath the car or vehicle on the side where you have removed the tire wheel assembly. Now remove the serpentine belt from the engine by using a 3/8ths breaker bar. Place it on the tensioner and lift up while removing the belt from the alternator. Keep lifting the belt out from t...

Computer crashes, fried hard drives, red rings of death, delinquent memory cards... nothing is worse than dysfunctional technology. In just a minute, your favorite and most used device has become the biggest headache of your life, frustrating you to the brink of madness. But what's worse than your electronics just giving up on you?

If you’ve got a minor cut or nasty sunburn you may reach for the aloe vera for the soothing and healing qualities. You don’t have to buy aloe, it is easy to extract the aloe from the inside of the leaf of a living aloe vera plant.

Though jewelry making can be meticulous and dependent on dexterity, using the right wire makes the whole process easier and faster. Wire necklaces and bracelets are simple when using the soft flexible wire, or soft flex. This demonstration video will help walk you through the process of this threading with soft flex.

Watch this how-to draw a horse video for a walk through of this horse drawing. To begin with you want to start to define the major areas of the head like the nose, mouth ears and eyes of the horse along with the general shape of the head. At this stage keep your lines loose and light so that if you make any mistakes they will be easy to erase later.

I will show you how to make a loud whistle from a twig from a sycamore tree. In fact they are so loud that they could be used in an emergency situation to attract attention from potential rescuers. The international distress signal is 6 whistle blasts in quick succession.

Do not ever laugh or shrug off what medical bottles or boxes give you as side effects or warnings. All of the side effects and warnings are put on the medication for a purpose. Priapism is a topic we all laugh or giggle about but it is a very serious emergency problem.

Over the past 10 months the once peaceful city of Christchurch in the South Island of New Zealand has been haunted by a plethora of devastating earthquakes with hundreds of fatalities. To date there have been over 7000 earthquakes. This photo was taken on Worcester Boulevard, opposite the Christchurch Arts Centre. It was a dull, cold day, so I used a monochrome 'film' which captured the sombre mood of a mourning city; this was coupled with underlying parallelisms of an angled shot emulating t...

What feature would we most like to see in the robots of tomorrow? Why, the ability to interact with human beings without crushing them to death, of course. Happily, thanks to a new pressure-sensitive synthetic skin technology, the dream is within reach:

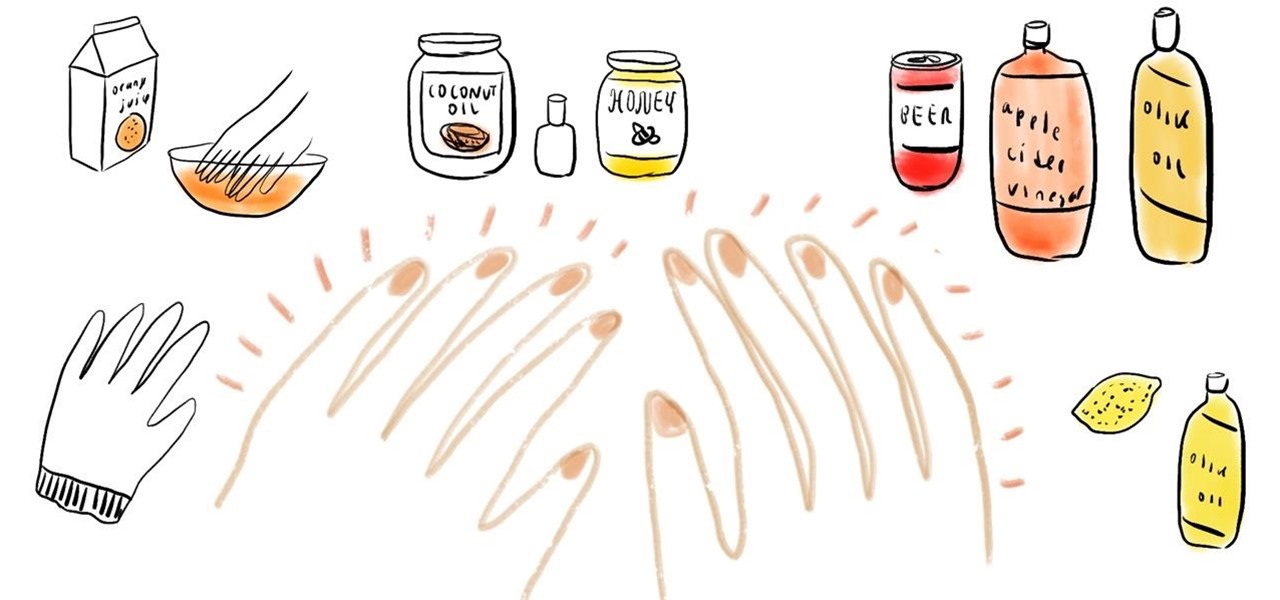
How important is it to have healthy and strong nails? Strong nails are better for manicures and are also more pleasing to present in public. Regular nail growth is also an overall indicator of good health, while discolorations and indentations on your nail beds, or even just slow nail growth, can be a sign of underlying health problems.

Rolling out right now are the latest KitKat updates to both the Exynos (SM-N900) and Snapdragon (SM-N9005) variants of the Galaxy Note 3. These over-the-air (OTA) updates will be staged out, beginning with networks in India, South Korea, and Switzerland. As reported by @lalithbhaskar, and confirmed by Sammobile, the latest update brings Android 4.4.2 to Samsung's current flagship device. If you reside in one of the mentioned regions, you can force a manual check by going to Settings -> About ...

In my Wireshark article, we talked a little bit about packet sniffing, but we focused more on the underlying protocols and models. Now, I'd like to dive right back into Wireshark and start stealing packets.

Everyone's been in the following situation. You're sitting there at a nice bar, chatting up a smoking hot member of the opposite sex when all of a sudden they drop this bomb: "Can you engrave on wood in Photoshop?" The next thing you know, the night spirals into blackness and you wake up in a puddle of your own tears with some half-eaten beef jerky hanging out of your mouth.

Pull up outside any construction site and you'll see tools scattered about—hammers, jigsaws, nail guns, hydraulic pipe benders—these are the tools of the trade. You would be hard-pressed to build a home or office building with just your hands! On that same page, security professionals also have their own go-to tools that they use on the job site, only their job site is your server.

What is a burn? It's a form of injury to body tissues which is caused by heat, corrosive substances or friction. There is another form of burn, which is known as scald; it results from exposure to hot water or steam.

It's once again Monday, which means it's time to highlight some of the most recent community submissions posted to the Math Craft corkboard. Since two of these posts were on polyhedral versions of M.C. Escher's tessellations, I thought we'd take a look at building a simple tessellated cube based off of imitations of his imagery.

How do we really come to the decisions that we make? Is it just flip a coin and hope for the best or is there some underlying procedure that we go through, consciously or unconsciously, that guides our course of action?

It was brought up a while back in a Community Call to Arms that *math* is handy for encryption (and let's face it, everything) so let us go over things you just have to know. "In its simplest meaning in mathematics and logic, an operation is an action or procedure which produces a new value from one or more input values."[source]

You walk over to your laptop, wiggle your mouse to wake up the screen, then fire up your browser to come visit Null Byte. Catching the article about Anonymous and how they presumably will not take down the Internet, you find yourself wondering... how would someone take down the Internet? Could they even do it?

Mark Burnett is, financially speaking, perhaps the most successful television producer today. While I had launched America's Most Wanted and COPS a decade earlier, Mark exploded onto network television with Survivor, the glossy and fantastical innovation to reality television. With Survivor now entering its 11th year, I recently interviewed Mark at the Los Angeles public radio station KCRW, where the podcast will be made available. Below, Mark's 10 steps from soldier-to-nanny-to-premiere-Holl...