Hydrangea is a garden favorite. It has lovely blooms and can become a good sized plant. Many ask when should it be pruned or cut back. A good rule of thumb is to understand that Hydrangeas bloom on old wood. As soon as the flowers are spent, as soon as they start to turn brown it is a good idea to prune. This allows a maximum time for the branch to grow, set new wood which will then turn into old wood and produce more flowers.

For preschoolers a great art and science activity! Lot's of small motor skills are involved with brushing and placing tissue paper. The reaction from the tissue paper and vinegar is the exciting science element of the activity. Art gives your child a chance to express themselves through their imagination. Art allows children to explore and understand their world through creative experiences that emphasize the process of art, not the product. When your child is creating there is no right or wr...

The amount of information we see on a daily basis is overwhelming. Then there's all the data we never even see. If your career depends on making sense of all of this information, you need to understand the programs that do the heavy lifting.

We've been so worried about volumetric scans possibly robbing celebrities and performers of their agency and right to control their image that, somewhere along the way, we forgot that scans may not always be necessary to produce passable holographic performances.

While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. In this guide, we'll build an Arduino program from scratch and explain the code structure in a way anyone can understand.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

Every day the young world of mixed reality is creating new ways for people to work with with computers. We are looking for, and finding, new ways for these head-worn computers to understand what we tell them. Sometimes it is with our hands, sometimes it is where we turn our head, sometimes it is what we say. In the case highlighted below, it's where we walk.

If you've ever built a piece of IKEA furniture, you're familiar with the confusion that some 2D instruction booklets can create. But neuroscience suggests that they're cognitively overloading, as our brains have to translate their basic flatness into physical reality and that's pretty hard to do. Fortunately, augmented reality has come to the rescue.

It's no surprise that the Microsoft Kinect can provide far better motion tracking than the HoloLens currently can on its own, but at least one developer didn't want to wait for the company's own eventual implementation. Kyle G, founder and CEO of Wavelength Studios, projected his movements using a Kinect into a holographic zombie.

When Microsoft release an update to the HoloLens Development Edition at the end of May, there were a bunch of cool new features added in. Among them: New voice controls that make working in the HoloLens operating system much easier.

It seemed appropriate that we announce the winner of the first White Hat Award for Technical Excellence on the Academy Awards weekend. This is, in essence, our "Oscar" here at Null Byte. Remember, this contest began on January 4th, 2016 and just recently closed on February 15th. In this contest, I was looking for:

In my last tutorial I very briefly introduced Zanti , but in this tutorial I will start to show its many features. The first step on hacking is recon . You could use Nmap , but the problem with Nmap on Android is that by itself, in order to gain full functionality your phone must be rooted. Thank goodness for a few geniuses in Zanti's dev team whom managed to implant full fuctionality of Nmap in Zanti without rooting your phone. With that being said, boot up your Android phone and lets start ...

Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

Welcome back, my budding hackers! In this series, we are trying to understand how AV software works so that we can learn to evade it. To that end, we are working with the open-source AV software, ClamAV. I had previously introduced ClamAV in Part 2 of this series. If you have not installed it yet, go back to that and install it.

In an article published in early-2015 by Peninsula Press, it was reported that the demand and the salaries for cyber security professionals are exploding! They cite that 209,000 cyber security jobs were unfilled last year, and that job postings have increased over 74% in the last 5 years. Job opening are expected to grow by another 53% over the next 3 years. You are definitely in the right field, my tenderfoot hackers! Some researchers are expecting information security jobs to continue to gr...

!!!WARNING!!! !!!Because of misleading informations please wait for the new post about this same argument instead of reading this post!!!

DATING & RELATIONSHIP IN FRANCE VS. THE U.S This video compares and helps understand dating and relationship concept in France Vs. in the U.S.

So, you find an interesting article online, but there’s something you don’t quite understand about it and instinct kicks in. Open new tab. Go to Google. Enter keywords. Search. Find information. Understand.

Learn the and understand the mechanics of the PowerPoint interface. This tutorial will explain the Ribbon, Slides Pane and Slides Tab. Throughout this tutorial it is assumed that you are a complete beginner however as new tutorials are added the complexity will slowly increase from basics to advance. This tutorial is brought to you by Cozy HowTo your place for a snugly warm learning experience.

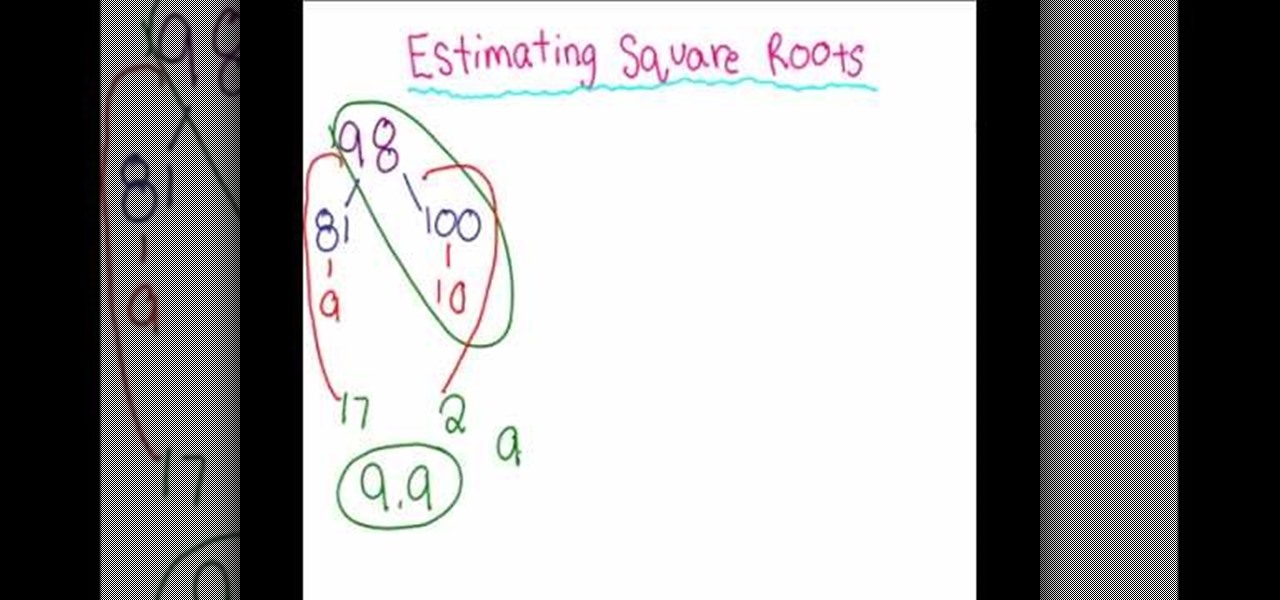
In this how to you will learn how to estimate square roots. You could use this in the real world if you are an engineer or if you are a video game designer. Here is a video to help you understand.

In this web design tutorial learn how to adjust width and color of speech bubbles and text within speech bubbles. This is a two part series web design tutorial so make sure to watch the following web design tutorial to help you fully understand how to modify speech bubbles from designs gallery.

Website Design Tutorial for Xara Web Designer learning how to switch between single page view vs. multi-page view. When working with your web design it is important to understand, which website design view is best for completing your project. This web design tutorial covers two of in my opinion the most important views for your web design work environment.

Video: . Requested by quite some people out there.

Steampunk is a tremendously interesting phenomenon because of its reliance on science fiction, and fiction in general. Steampunk can arguably be broken down into two categories: the fiction, and the aesthetic. Sometimes these categories cross over, but they're often more distinct than most people suspect; that said, the aesthetic is firmly based in works of fiction.

Tim Carter shares some insights about vapor barriers and how to install them on your next project. This easy-to-understand video will show how to install new water infiltration barriers which will protect your house.

This tutorial teaches you how to fold an origami mouse with an ordinary sheet of paper. This model is suitable for beginners and children. Origami is great for small kids as the only material needed is paper, no scissors or glue that could do harm!

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

At a very early age, I would go on summer camping trips. I remember every night being handed a pack of sparklers that were my own, to swing around wildly, which gave me many valuable life lessons on cause and effect.

In this detailed, creepy, video series you learn and understand the fundamentals of having an Out of Body Experience (OBE) or Lucid Dreaming. Everything from a clear explanation fo "The Phase", getting started, deepening of the experience, and much more.

She thinks just because you're related that your closet is her closet; and if she ever gives your things back, they're never washed. If it's time to stop your sister from being a closet bandit, check out this video. This tutorial is full of tips for gettinf rid of that pesky sibling and keeping your clothes all to yourself.

The name of your business will leave an impression on people as this is probably the first information they will receive. Make sure to express yourself and give the impression you intend by choosing the best name for your business.

Need to know what kind of oil your car needs? How about your vehicle load capacity? What about the standard maintenance procedures for you specific make and model? All of this and more can be located inside your owner's manual. If you don’t have an owner’s manual for your used car, you may still be able to find one even if your car is an antique.

Motivational speaker and leadership coach Tim Warneka teaches how to write a successful college essay in nine simple steps. Read and understand the directions and expectations the professor has for the assignment. Sit down and write whatever comes to mind on the topic. Edit your paper, making sure to use academic English. Allow yourself time to "sleep on it" and come back to re-read your essay with a fresh mind. When you come back to it, read the paper out loud to find any mistakes. Allow one...

This video shows you the basics of dealing a hand of Texas Hold 'em. When dealing you always start off dealing the cards to your left; deal two cards to each player to start the initial round of betting. After the round of betting is over you "burn" one card by placing it face down, then turn over three cards called the "flop". This is followed by a round of betting. Then you burn one card and flip over one card called the "turn". This followed by another round of betting leaves you to burn o...

Studio one single window interface now eliminates multiple windows and complex menus enabling to focus on music in an easy way. The important music creation and production tools are instantly accessible. Studio one directly opens into the start page by default. Here we can find the recent files that enable to easily choose the ongoing productions. The default page also helps to open tutorials and demo songs. We can create songs on the song page using hot keys to access various panels. For exa...

Arranging fences can be a hassle if FarmVille. Once you understand the basics, however, you will be creating elaborate fence layouts in no time!

A stager is a small piece of software that's typically used by malware to hide what's happening in the early stages of infection and to download a larger payload later.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

It finally happened! In a world of "go big or go home," Magic Leap has finally done something other than tease us with vague promises and rendered video concepts. Although, other than actually showing us what the developer's kit will look like, it seems little more than a slightly different kind of a tease. To demystify this new product, we here at Next Reality decided to put together what we know about the hardware.