Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

Hello, all. In this article, I will be showing you how to make one of the most useful products known to man. I am talking, of course, about charcoal.

Magic Leap is making it easier for developers to share their spatial computing experiments with other Magic Leap One users.

Despite funding difficulties that forced Meta to place employees on temporary leave in September, the augmented reality headset maker is reminding enterprise companies that it remains a viable option for visualizing and working with 3D design models.

The team at Magic Leap just got a millennial-style boost with the announcement that financial news network Cheddar is coming to the Magic Leap One.

Magic Leap shows up in the weirdest places. Last week, right at the start of World Cup fever, for some reason, the Magic Leap One appeared on a Brazilian television show.

While self-driving cars appear to be as inevitable as augmented reality headsets, the auto industry and its technology partners likely have years of testing to complete and regulatory loopholes to jump through before self-driving cars hit most highways.

The Google Assistant is great about understanding what you actually mean, so you don't have to issue exact commands like you do with Amazon Alexa, for instance. But even though it's a master of colloquial speech, it could still be better, and that's where shortcuts come into play.

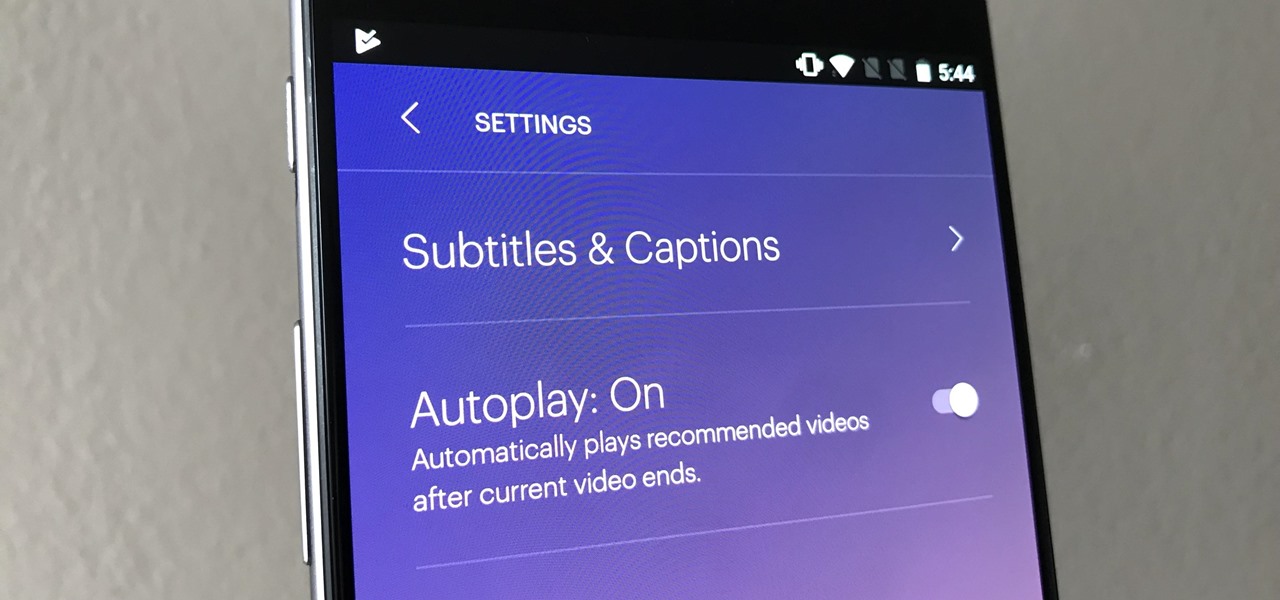
We use subtitles when we can't understand what's being spoken on screen, but most of the time it seems like those subtitles are out of our control. Maybe we find them too small, or even too large. Maybe the color is too faint, or the background too distracting. If only we could change the subtitles to reflect our own needs and styles ...

At Apple's yearly event, the World Wide Developers Conference, the tech giant finally announced their decision to enter the augmented reality space. Through adding basic AR functionality to the beta release of Xcode 9, the development environment for Mac computers, as well as their line of iOS devices, the company has said they understand the importance of the tech.

Google Assistant will be getting an AI makeover with the addition of Google Lens. This new feature is basically a set of vision-based computing capabilities within the Assistant.

There's now more reasons to make sick workers stay home—a new game theory study suggests adequate hand washing and other illness-aversion tactics aren't as useful as we thought to keep you from getting infected when a virus or bacteria is circulating.

When you wear a holographic computer on your face, you gain some things and lose others. That's certainly the case when using Skype in Microsoft's HoloLens. Some video chats will work better because your caller can see what you see, rather than your face—but others just feel weird.

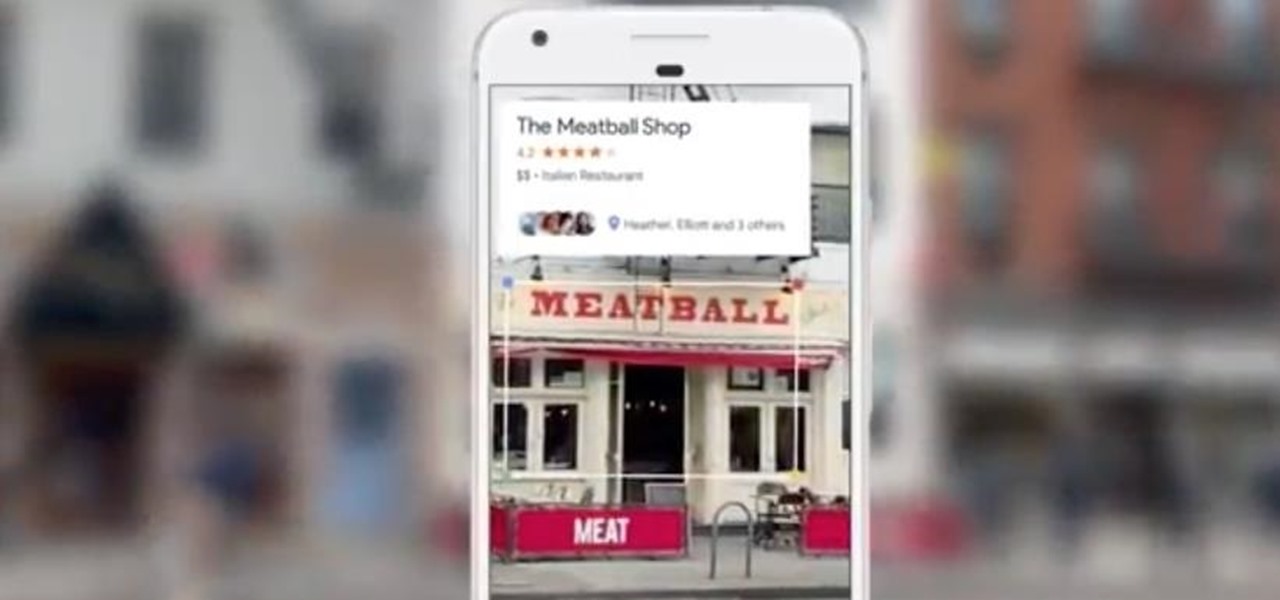
If you're standing in a foreign city, surrounded by signage in a language you don't understand, you won't suddenly be able to read it. But with a clever feature in Google's Translate app, your smartphone can.

So you dropped your smartphone and the screen cracked. Again. Just the thought of sending it out for repair or buying a new phone is driving you mad.

Welcome my aspiring hackers and programmers! Today i will introduce you to a programming language that as a hacker you should have in your set of hacking/programming skills (except if you're only interested in web hacking/programming...then you should go learn some html or PHP instead of C#).

Hello again! In this tutorial, we are going to go over something called "operators" which will help us build upon conditions of control structures and also some variable manipulation. Without further ado, let's dive in!

Hi there, Crackers, Welcome to my 7th post (Part-1), this tutorial will explain about the basics of Batch Scripting.

Hi everyone! In the previous part of this series, I introduced one way to hijack a program's execution flaw, though I only showed you how to crash the program and left you with a little mystery to solve. Today we are giving the solution of that and then introducing shellcode usage and remote command execution.

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

Hi everyone! Last time we explained what roles Ebp and Esp registers have. We first introduced function's stack frame building, return address and calling conventions, but left some of the concepts floating without a full stop.

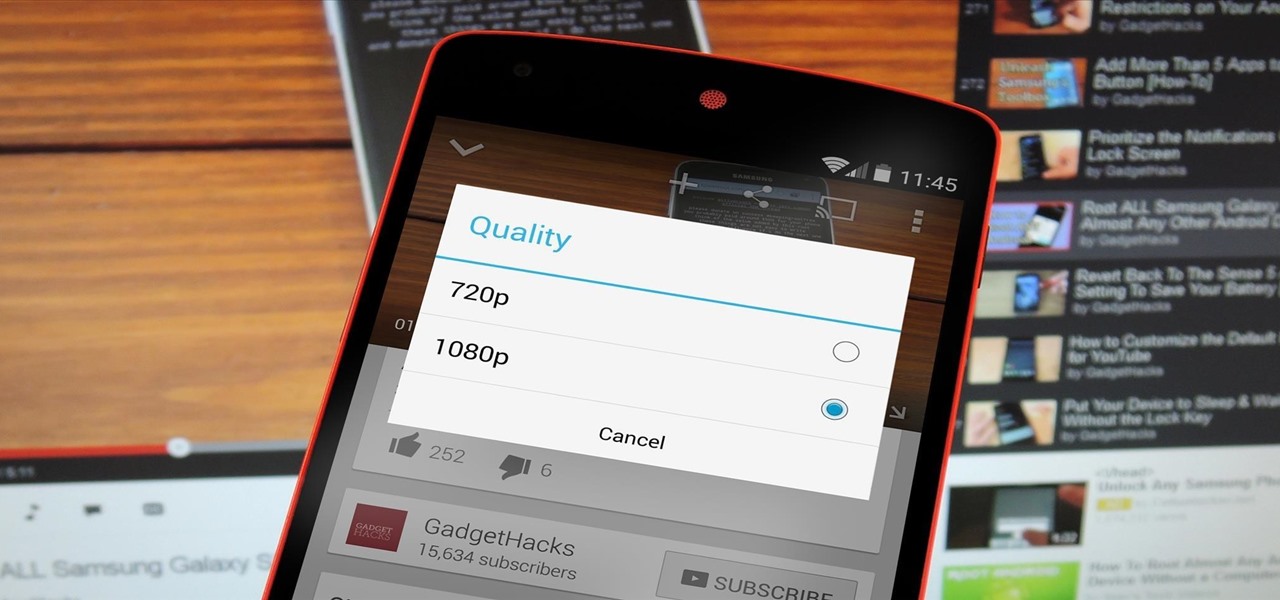
The Nexus 5 and Nexus 7 (2013 edition) boast beautiful 1080p screens that are capable of displaying images and videos in ultra-sharp high definition. But for some strange reason, the YouTube app only allows for streaming of 720p content on these devices. It's not a limitation of YouTube for Android, since other devices support 1080p playback out of the box, and some, like the LG G3, even support higher resolutions.

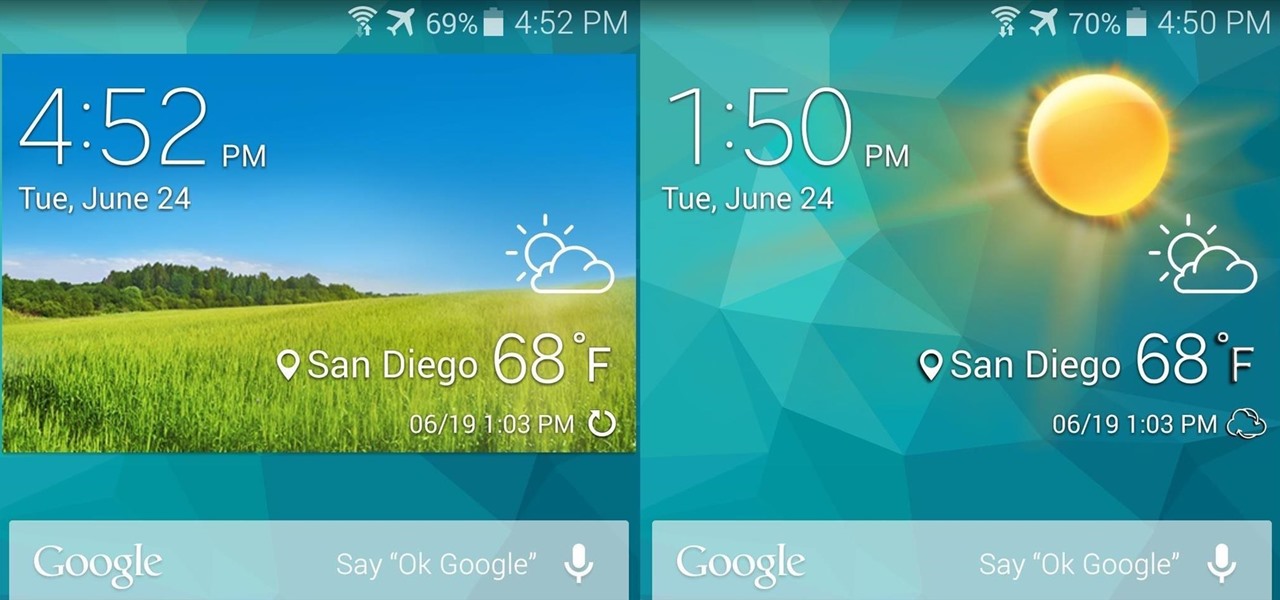
The weather widget on the main home screen of a fresh-out-of-the-box Galaxy S5 is meant to show off the screen. Super-high contrast and crisp definition on the individual blades of grass in the background let you know that the phone you're holding has one helluva display.

As this generation continues to evolve, we become more involved with social media. For example, you may have a Facebook, Twitter, and a Google+ account, and be heavily involved in using all three, but the constant switching between sites, logins, and conversations can get very tedious.

I have the AT&T version of the Galaxy S5, so every time I start my phone I get the pleasure of hearing AT&T's lovely jingle. Actually, that's sarcasm—I absolutely abhor this sound. I haven't had the chance to play around with a Sprint, T-Mobile, or Verizon variants of this phone, but I imagine they have some sort of equally annoying boot sound.

The team over at Spatial isn't done innovating its way through augmented reality in 2020. Just days after adding a mobile option to its groundbreaking Spatial virtual collaboration product, the company is releasing Tele, a new app geared toward more casual, AR-powered video chats.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

The older I get, the more my Friday nights involve watching Netflix at home with a bottle of Maker's Mark and a box of Oreos. Netflix is a big part of my life, and I'm not alone. YouTube and Netflix make up over 50% of all activity on the Internet, so it might be worth your time to understand why Netflix seems to cause so many headaches and what can be done about it.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

You must ONLY conduct this experiment if you are experienced in using combustibles and understand the risk. Fire is very dangerous and can seriously burn you. Seems harmless at first, but believe me, these are bubbles turned evil. When ignited, the bubbles pop almost instantly, and all the propane is released in a huge fireball.

To some, SCRABBLE is just a board game to play during family game night or during a casual get-together. Others think of SCRABBLE as a mere hobby. But with any activity, there will always be fanatics—the ones who would rather sell their soul than stop—the ones with a constant yearning for self-improvement—the merciless.

Feeling someone's forehead when they are sick is an outdated way to check for a fever. Follow along with this video and learn how to take an accurate reading so you know whether or not to seek medical help.

Know & Understand all basketball signals! Learn how the referee signals all the different basketball penalties with expert tips and advice in this free video.

Since Motorola engineer Bill Smith invented Six Sigma in 1986, corporations around the world have employed it to eliminate costs and process cycle time while increasing profits and customer satisfaction. These techniques and tools for process improvement were invaluable to famed CEO Jack Welch, who used them to redefine General Electric's business strategy in 1995.

Java is one of the world's leading programming languages thanks to its virtually endless array of applications. Since Java's initial release in 1998, this Open Source platform has become beloved by coders for its speed, flexibility, and dependability.

In 2018, Niantic unveiled its in-development augmented reality cloud platform for smartphones, the Niantic Real World Platform. A demo showed Pikachu and Eevee cavorting in a courtyard, darting in front of and behind potted plants and people's legs as they walked through the scene. This would be the future of Pokémon GO.

Spotify launched an experimental feature in early-2018 called Spotify Voice, a voice assistant that lives right in the app. It lets you speak to quickly find and play your favorite songs, albums, artists, videos, and podcasts on the music streaming service. Although the feature was initially only available on iOS, it's been ported over to Android so that anyone can take advantage of it.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.