Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

Around this time in 2016, the predictions for the next year had reached something of a consensus: 2017 would be the year of augmented reality. But a funny thing happened on the way to the future — nothing much, really. At least not for the first half of the year.

This is a tale about microbes, a man who became a hermit, and the parchment that carries both of their stories.

Andre was enjoying the carefree life of a 12-year-old with his friends, riding his bike and playing sports, like all kids that age. Schoolwork wasn't hard for him, and his grades showed that.

After years of telling patients to finish any prescribed course of antibiotics completely, a group of researchers in the UK say it is no longer necessary, and could even be harmful if we want to preserve the antibiotics we can still use.

Montezuma's revenge, the runs, the trots, or just diarrhea — everyone gets it sooner or later. What exactly is diarrhea good for, if anything?

The Deepwater Horizon oil spill that began on April 20, 2010, was the largest maritime oil spill in history. Killing 11 people and discharging 4.1 million barrels of oil and natural gas into the Gulf of Mexico, the event was an unparalleled personal, environmental, and business disaster. It was also the first major oil spill to take place in the deep ocean.

Within the coming months, software startup Neurable plans to introduce the next paradigm in virtual and augmented reality: the brain–computer interface (BCI).

LOOOK, a Seattle-based mixed reality and development studio, can now peer into the future with their new geotechnical engineering visualization application for Microsoft HoloLens.

Where in the world did it come from? All of a sudden, one day, someone had an infection with flesh-eating bacteria. It captured headlines and worldwide attention because it was such a severe, strange, uncontrollable, and really disgusting condition.

Findings from a mouse study suggest that the Zika virus infection may have serious reproductive consequences for men.

If you've ever wanted to live in the Matrix—or at least the iconic digital rain data visualization that Neo saw when realizing he was, indeed, the "one"—you can now do that with the Microsoft HoloLens. Just download The Red Pill.
In this Tutorial I will show you how you can use the frequency of letters to decrypt the famous Caesar cipher. I hope it is easy to understand and helpful for getting in touch with basic cryptanalysis. If you find any mistakes or have questions feel free to ask me. Finally I ask you to give me feedback which I will take into account for the next part.

As many of you know, I have been running a couple of series here on Null Byte about digital forensics called Digital Forensics for the Aspiring Hacker and Digital Forensics Using Kali. Although many readers have seemed to enjoy these series, just as many seem to be pondering, "Why should I study digital forensics?"

Welcome back! In our last training session we covered classes and how OOP can make programming/scripting easier. Today we'll be taking a breather and covering something fairly simple, bitwise operators.

I mentioned in one of my earlier articles something about ghost hackers, and very shortly stated a thing or two of what they do.

Hey everyone! This is a video tutorial for how to tune your guitar to Drop D in 10 seconds or less! Many guitarists, especially beginners ones, cringe at the idea of taking the time to tune their guitar out of standard. I know, because I was one of them! This tutorial will help change that assumption! In this video guitar tutorial I break down a few very basic and simple to understand steps to get your guitar tuned to Drop D in mere seconds! Hope this video helps you out!

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.
Welcome back Hackers\Newbies!

Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it.

Believe it or not, you can put your money to use very efficiently in a new way: your credit or debit card can serve as a blade in desperate situations. (It might even be handier than dental floss as a brilliant substitution for specialized kitchen tools.) While I wouldn't take bets on it slicing a New York strip steak, there are definitely many other foods it will easily slice through. What Is It Made Of?

Android is all about customization: "Be together. Not the same," as Google's latest ads for the platform put it. Changing your device's boot animation, for instance, is one of the many great ways you can add a touch of personal flair.

Complete silence or a non-stop Pandora playlist? People are often divided on what type of work environment they prefer. Whether you're a frequent loud music listener or you can't stand any kind of background noise, chances are you're pretty set in your ways.

The Xposed Framework offers many great customization options for your Galaxy S5. S Health, with its ability to read your heart rate through a built-in monitor, is one of the main selling points of the GS5. Trouble is, the two don't seem to play nice together.

Android's permissions system is simple, transparent, and straightforward. When installing an app, you get a chance to review all of the permissions that the app has requested. These can range from accessing your location data to holding a "wakelock" in order to prevent your phone from entering sleep mode. But your only choice in this matter is to accept all requested permissions, or not install the app.

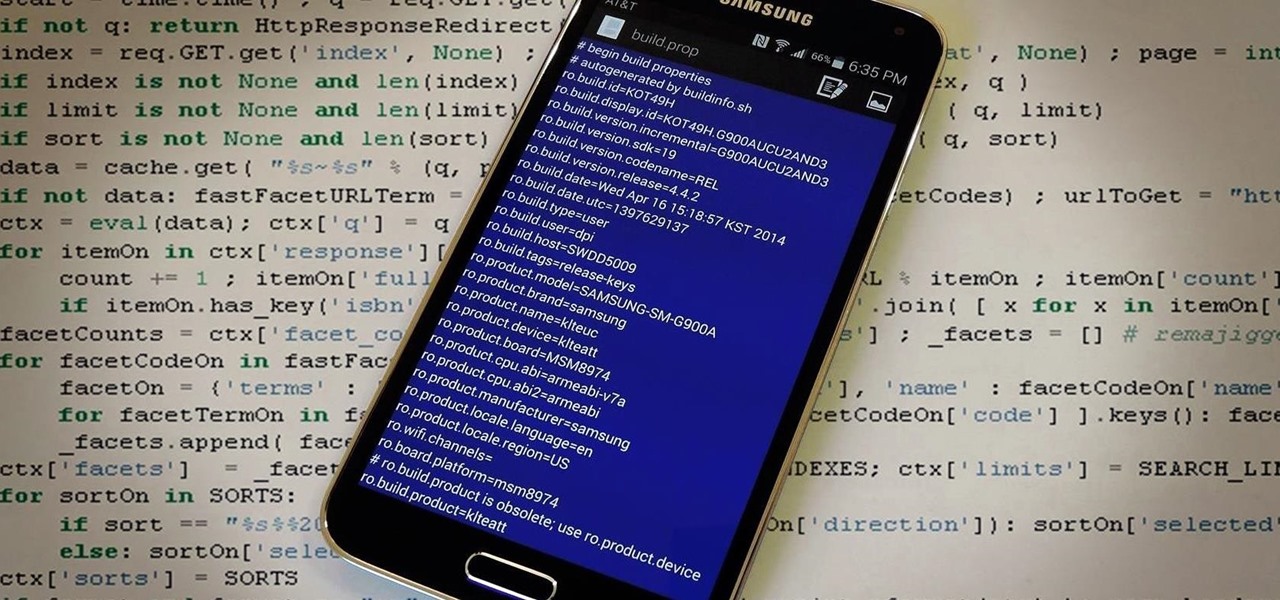
The build.prop file in an Android device is home to many system-level values and settings. Everything from screen density to video recording quality is covered in this file, and people have been editing these entries to get new functionality and better performance since Android has existed.

I'll give Samsung credit where it's due—the stock keyboard on the Galaxy S5 is actually pretty nice. There's a dedicated number row that resides at the top (something that the Google Keyboard needs a hack to achieve), and various settings exist to make switching between languages a breeze.

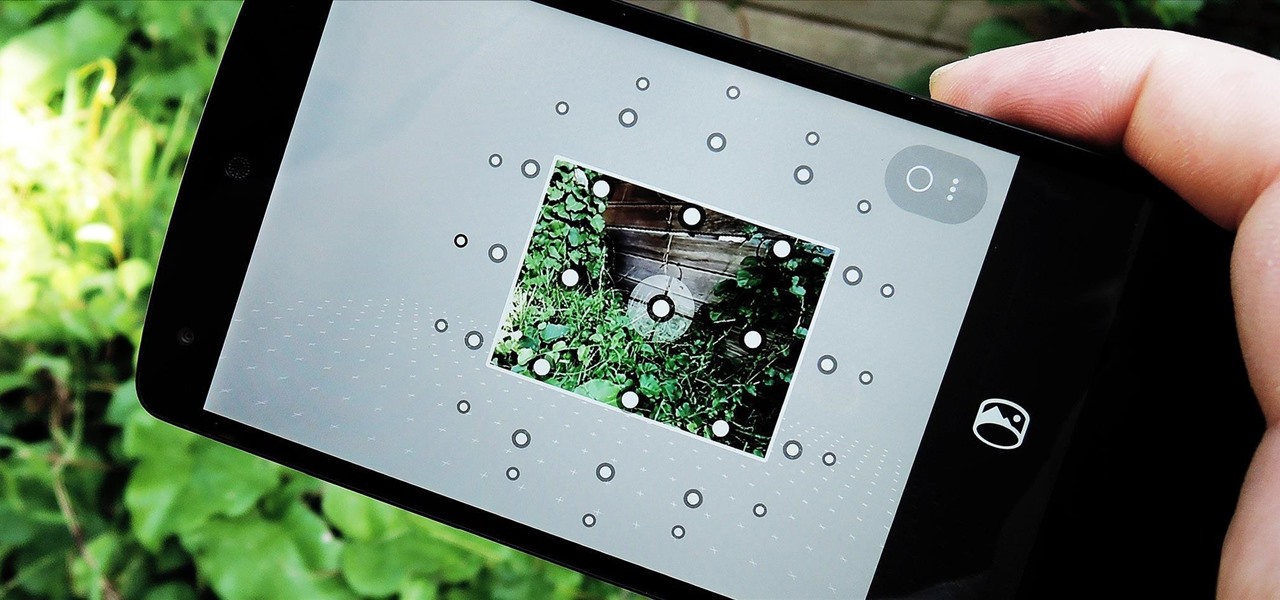
Just over a month ago, Google made its camera app available to all devices running Android 4.4 and higher. Originally exclusive to Nexus devices, the app got a UI overhaul and a new Lens Blur mode, but lost some features in the transition.

Recently, there have been some questions regarding networking popping up and we have decided to put together this series to try and cover this gap.

Rational numbers can be written as a fraction or as a/b. The "b" in a/b cannot be zero because you can't divide by zero. an example is 1.5. 1.5 can be written as 3/2/ Irrational numbers are numbers that can't be written as a fraction. A famous irrational number is pi. You can use this as a subject if you're a math teacher. Here is a video to help understand.

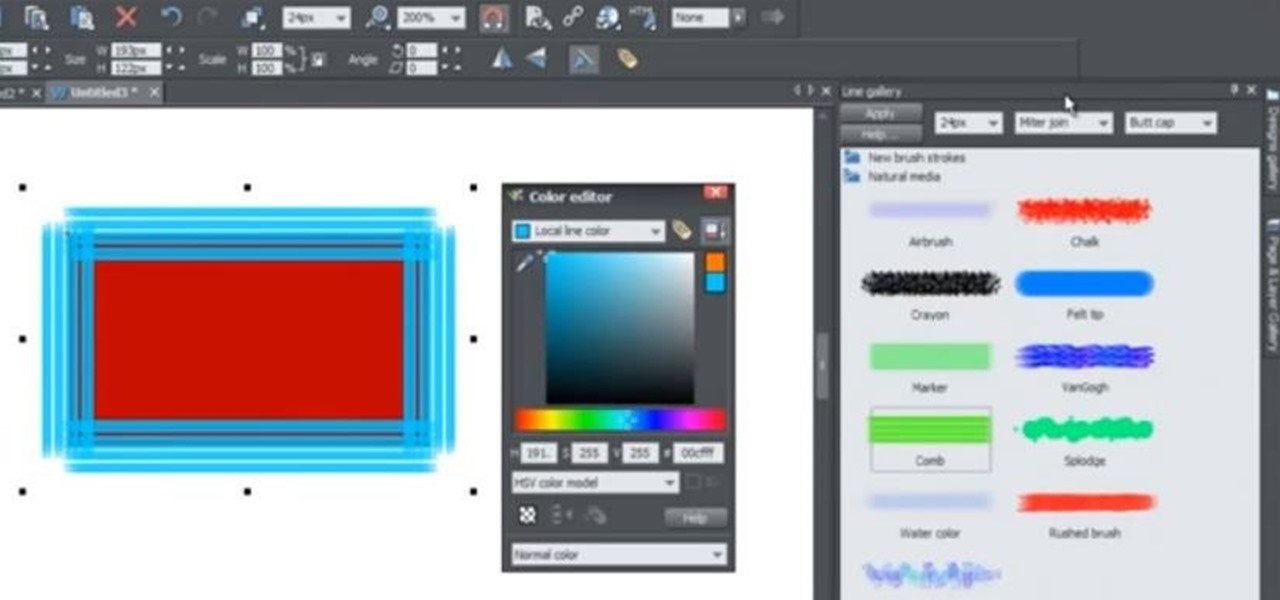
Web Design Tutorial for Xara Web Designer to help you learn how to apply line strokes to objects. Our web design tutorials are geared toward complete beginners although each web design tutorial will go deeper into helping you understand how to use the Xara Web Designer software. Line strokes a beneficial because it allow you to give objects in your web design space a unique look. In this web design tutorial I will experiment and show you some of the different variations of patterns that can b...

In this "Quick Clip," I tried dunking inflated balloons into a container filled with liquid nitrogen until they were completely flattened and seemingly destroyed. Once out of the liquid nitrogen, the balloons come back to life and reinflate on their own—without even touching them!

In this web design tutorial learn how to use the shape tool. In This Web Design tutorial for Xara Web Designer you will learn how to create straight and curved lines and smooth and cusp joins. Also this Xara Tutorial covers deleting and breaking nodes apart on a given line. The shape tool will allow you to make custom shapes and objects to give your website a creative boost.

The Jetsons may not have gotten everything right about the future, but even though we may not have flying cars or live in the sky (yet), one thing they imagined correctly was our electronics eventually being able to understand us.

I obviously do a lot of Steampunk projects, but there are a ton of things out there that I haven't tried yet. So, in an effort to broaden my horizons, I recently taught myself how to use Arduinos, which I plan to incorporate into some of my future Steampunk builds.
(Series designed to help explore whether your ideal employment ideas should be formalized into a business venture or as an employee or volunteer value added problem solver).

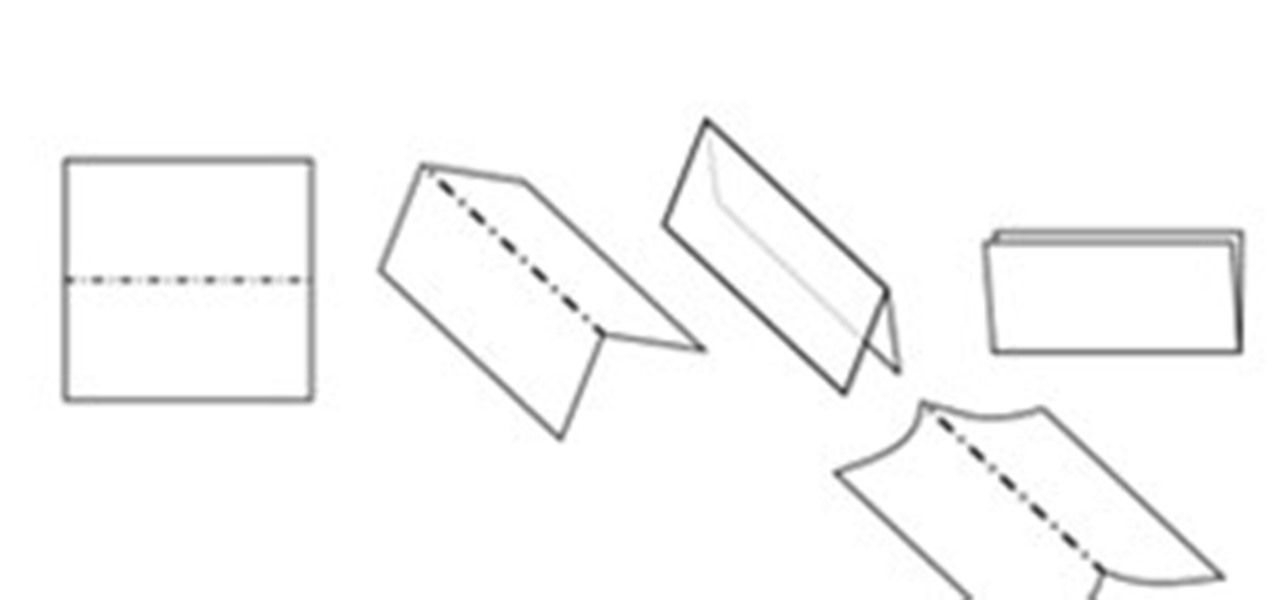
In this article you will learn how to understand written origami instructions, called diagrams. You can follow the video below or read the entire article

Amazon Web Services (AWS) is the premier on-demand cloud computing platform. Offering a wide range of APIs to companies, governments, and individuals on a pay-as-you-go basis, this Amazon subsidiary pulled in over $35 billion in revenue in 2019 alone.