New York-based startup CTRL-Labs has closed a $28 million Series A round of funding from Google parent Alphabet's GV and Amazon's Alexa Fund, among others, for its next-generation neural interface technology for AR/VR and robotics.

Epic Games just released update v3.4 for Fortnite Battle Royale on all four platforms. This new version brings a number of UI changes, performance improvements, and bug fixes, but the addition that will get the most players excited is a new weapon: the Guided Missile.

Mobile augmented reality developer Blippar's mission is to construct a computer vision map the world, with visual recognition of thousands of notable buildings, bridges, castles, holy places. A major step toward that goal has been taken by the company this month with the announcement of its landmark recognition API.

On Friday, game developer PreviewLabs released the first online multiplayer game for the Microsoft HoloLens.
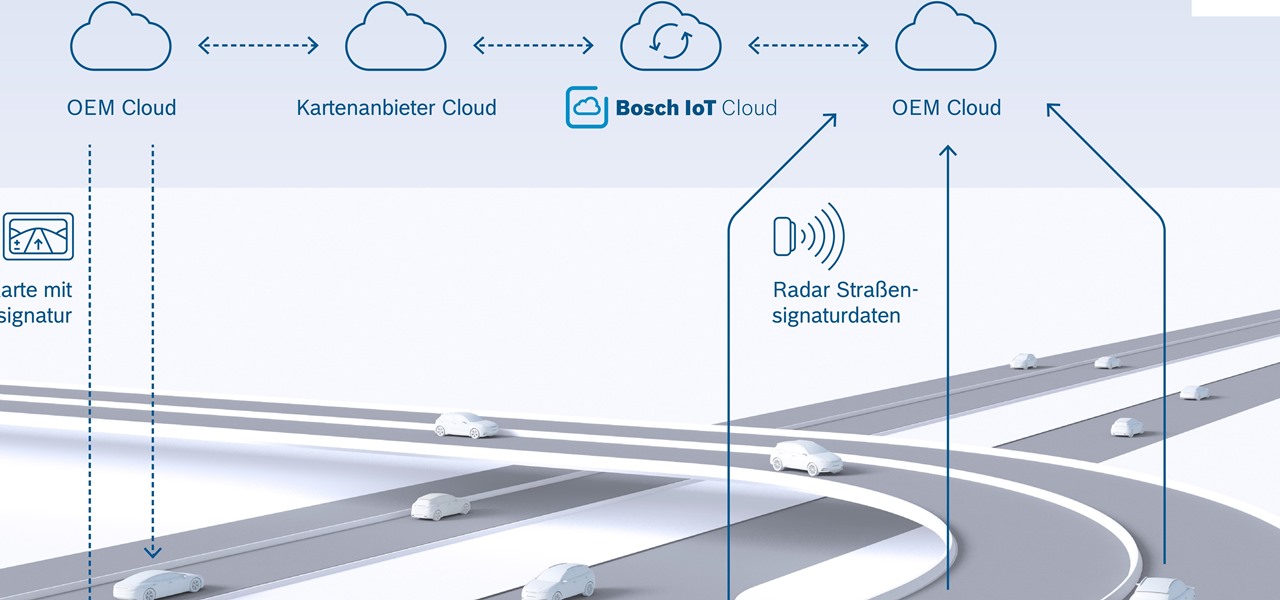
New "radar road signature" technology from Bosch will be used to create maps for high-accuracy self driving. The new map is the first to use radar signals for a localization layer.

The Galaxy S8 and S8+ come with a set of AKG-tuned earbuds that would cost you $99 by themselves. Unfortunately, the earbuds alone don't automatically translate to superior sound, and they've been met with lukewarm reception. But as it turns out, there's a fairly hidden menu on Samsung's flagships that'll give you a tailor-made audio experience and help you get the most out of your S8-AKG pairing.

If OnePlus co-founder Carl Pei was trying to be slick about using the new OnePlus 5 phone — especially before its speculated summer release — well, he didn't do that great a job of hiding it from us.

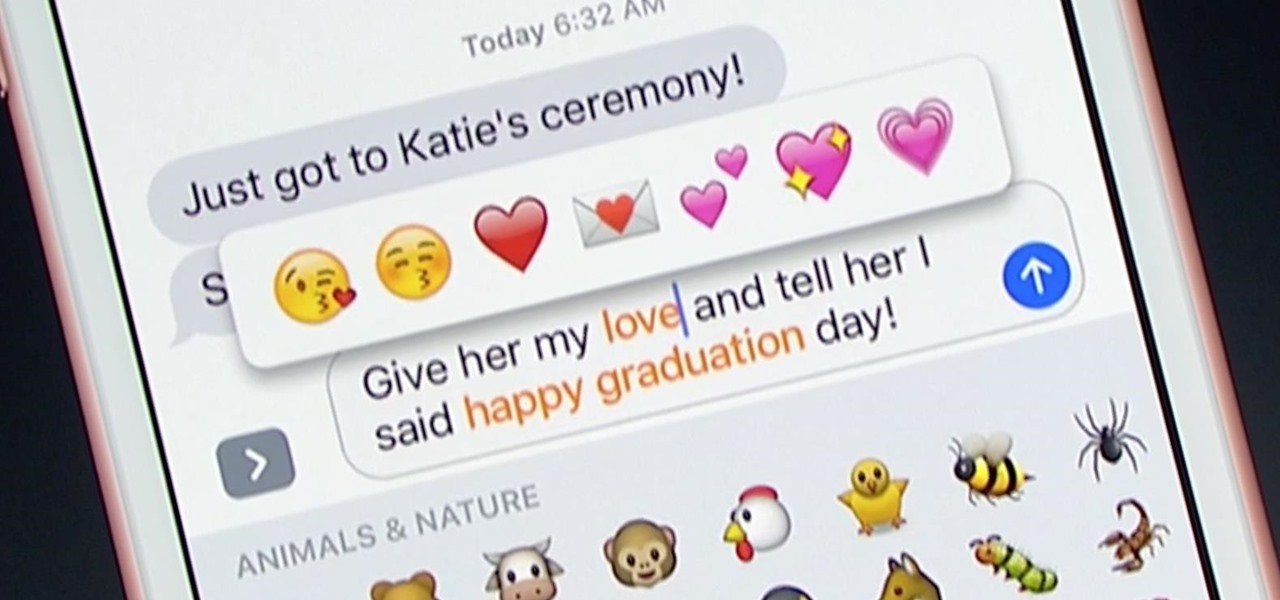
Apple unveiled huge improvements for Messages in iOS 10 at WWDC '16, and my favorite new feature is that searching for emojis will be much, much easier. But there's a lot more to this update besides emojis.

Gender standards are entirely pervasive. We raise our sons to be masculine and our daughters to be feminine, which perpetuates the gender role formula when they grow up to be parents and raise their own children. Part of this whole equation is that boys are supposed to remain stoic and project an air of strength, and girls are expected to be amiable while being held to unrealistic standards of outward beauty.

A video showing what is alleged to be the new Apple iPhone 7 has appeared online. The uploader of the video claims that it was shot on one of Foxconn's assembly lines.

Hi guys. I'm here to go for level 7 now lets get it start but i apologize u all that i posted this very late but now lets rock:

Let's say you're watching a video and everything's going great, but you feel the need to raise the volume a tiny bit. You hit the volume button on your Nexus 5, and all of a sudden, a giant volume slider appears that obscures half of your video for 3 seconds.

In direct competition with Pandora, iTunes Radio, and Spotify, Samsung has just launched Milk Music—a strangely named, yet completely free music streaming service for Android.

Facial recognition software is being more widely used with every passing day. Your local law enforcement is probably already using it, and it will be even easier for them now that the FBI handed out its own facial recognition software to state authorities. Even the fine folks at Facebook are using this technology. Obviously, this brings up some pretty serious privacy concerns amongst most people, because honestly, who wants to be tracked? Right now, there's not a lot we can do about it being ...

With a rather brief and obscure introduction, Brad teaches us how to hook up our computers and our laptops with a television. He starts us off by saying how this can help alleviate boredom when working out on a stationary bike. With a close up of the outlets in the back of the television, Brad shows us step-by-step how to do this process. The last few minutes he tries to humor us a bit by showing how it all works in the end.

In last week's guide, we covered the best places to purchase digital copies of computer games online. This week we'll cover another type of downloadable content: those available for video game consoles. Every major console out today either has or plans to have a DLC platform, but which one is the best? If you don't like leaving your house and want to play console video games, which console should you get? Below I will break down what the online marketplace offers so you can decide which conso...

While the automotive industry is moving towards adopting AR displays in future models, BMW is already shifting into the next gear with its vision of the technology.

A relatively unknown musician from the early-'70s that's gained popularity stateside over the last ten years just got the remastered treatment with two new reissues available on CD and 180-gram vinyl. And they're available right now.

On Monday, with just days left before Christmas, Lowe's dropped a surprise augmented reality treat in everyone's lap: a brand new Magic Leap One app.

I hate folder names, especially the one Apple shoves down our digital throats. On a computer, they make total sense, but on my iPhone, it's just more clutter on the home screen. You can tell what folder is what just by looking at the app icons within it, so why are we forced to label them? Technically, we're not, since there is a workaround in iOS 12 and iOS 13 to make those labels disappear for good.

Magic Leap shows up in the weirdest places. Last week, right at the start of World Cup fever, for some reason, the Magic Leap One appeared on a Brazilian television show.

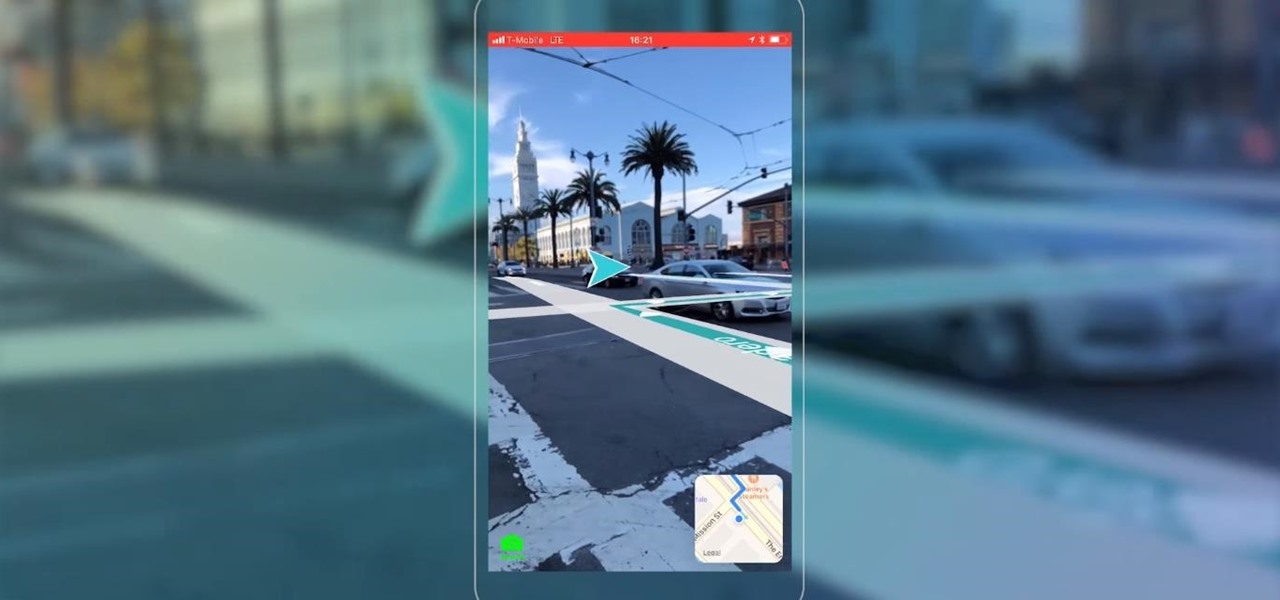
Mobile AR developer Blippar has achieved a breakthrough by releasing what appears to be the first commercially-available AR navigation app.

In case you didn't already know, augmented reality is here. It's no longer just an idea in a cyberpunk novel. And while augmented reality has been around for a long time, the actual technology is finally catching up to the idea.

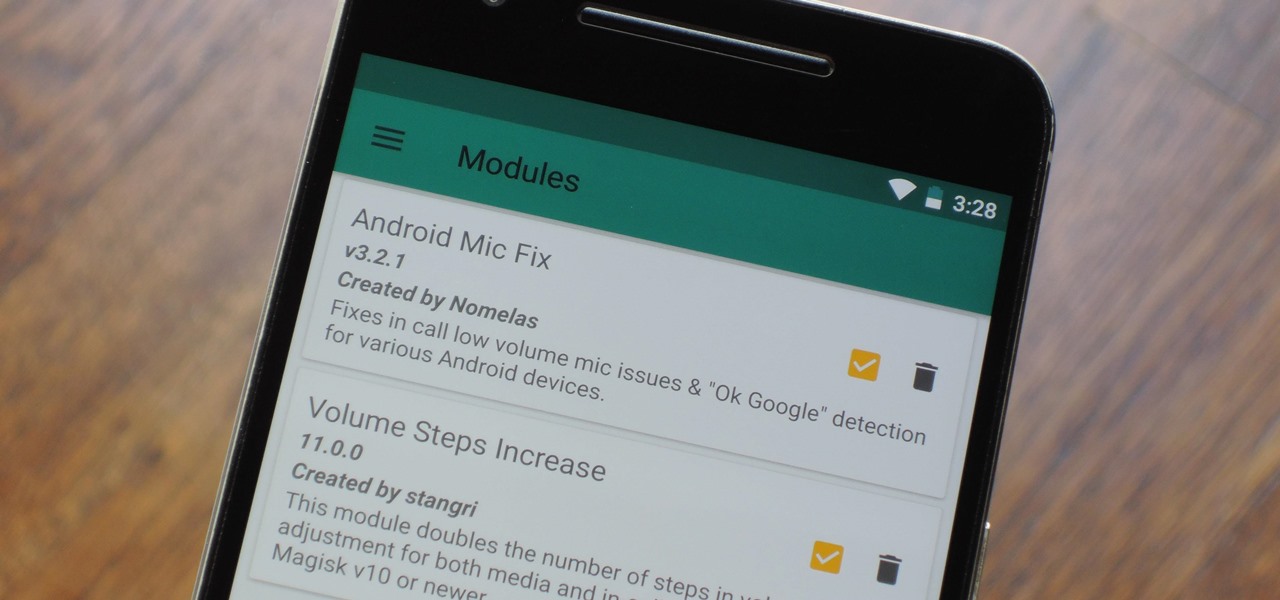
Much like Xposed or Cydia, Magisk has an official repository that makes it easy to download root-level tweaks. These tweaks are called modules, and they can do anything from changing your emojis to installing high-level audio mods. But as it stands, a large number of Magisk modules are not hosted on the official repo just yet, so there are two primary ways to install them.

If you maintain a digital library of your favorite movies, Plex is the perfect solution for bridging the gap between your computer and your mobile device. All you have to do is install the server program on your Mac or PC and point it to the folder where you store your movies, then you can use the Plex app for Android or iOS to watch the movies on your phone or tablet.

Rooting a phone lets us install custom operating systems, known as ROMs, which replace the device's preinstalled OS. Most custom ROMs are based on code from the Android Open Source Project (AOSP), which gives them a look and feel similar to Google's version of stock Android. But every now and then, you'll see a ROM that isn't based on Android, though these are few and far between — at least, until now.

A little-known company in India is making waves after announcing that it will sell an Android 5.1 Lollipop smartphone for less than $4 (or, more precisely, 251 rupees). The Freedom 251, from Ringing Bells, sounds almost too good to be true. Is that because it is?

School internet filters serve a valid purpose—they keep students from wandering off into the deep corners of the web while still allowing at least some internet access. But a lot of these restrictions are completely ridiculous, to the point where some school districts block access to the educational material in National Geographic or forbid searching terms like "China," "Iran," or "Russia"—because, you know, breasts and commies.

Like most people who spend a good deal of time in front of their computer—whether for work, school, or play—I jump back and forth from window to window, working and playing with different things at the same time to get my work done faster or procrastinate harder.

There's something primal about the smell of smoking food. Somewhere deep in the recesses of our souls, we remember a time when humans only ate by the fire. Or perhaps that's just something I tell myself. Either way, it's hard to smell smoke and food and not feel like you should be eating. And, as chef Edi Frauneder said in a recent Saveur article, "Grilling is convivial. There's something about this act of coming together over an open flame that just says vacation."

This sounds a little crazy, and it is—in a good way. Cooking food in the dishwasher while it cleans your dishes multitasks your appliance and saves time and energy. And who doesn't want to spend less time over a hot stove? How Dishwasher Cooking Works

I have the AT&T version of the Galaxy S5, so every time I start my phone I get the pleasure of hearing AT&T's lovely jingle. Actually, that's sarcasm—I absolutely abhor this sound. I haven't had the chance to play around with a Sprint, T-Mobile, or Verizon variants of this phone, but I imagine they have some sort of equally annoying boot sound.

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

Timely costumes for Halloween are awesome—especially really obscure ones—because they're indicative of social awareness. In 2010, I remember seeing several Chilean Miner costumes, which I thought were great. 2012 brings new stories, new characters and more importantly...new Halloween costumes.

Trivia games are among the most entertaining ways to learn factoids and interesting info you may have never known about before. They're also the perfect genre to enjoy with friends and family, as they're particularly great at breaking the ice to make for a more memorable time together.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

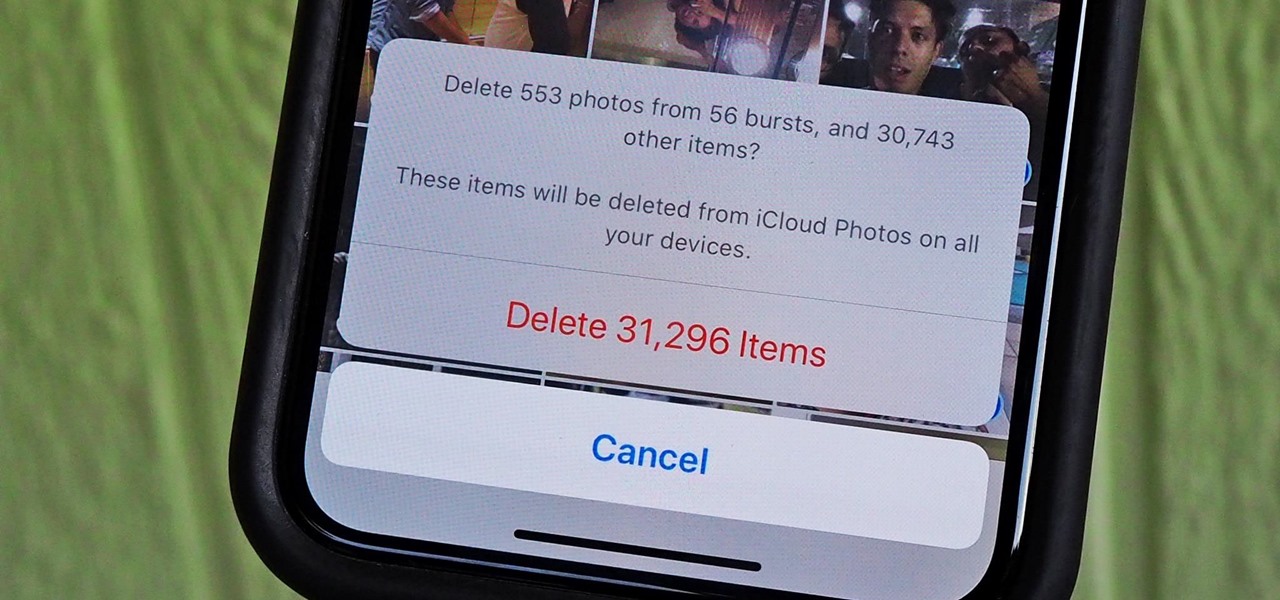
With high-resolution photos and 4K videos being standard these days, it's no surprise that media hogs most of the storage space for many iPhone users. If that's you, there's always iCloud, but you only get 5 GB free, and a paid 50 GB or 200 GB plan can fill up fast. To save money and reclaim storage, you can just delete content from the Photos app, and there's a trick to doing it faster.

If you don't want to be found on Twitter, there are several ways to do that without making your account private. For instance, you can choose an obscure username, omit your real name, or pick a random avatar. But there are lesser-known features deep in your settings that can also protect your privacy online, including preventing photo tags.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

Every step in the evolution of computing brings an in-kind leap forward in user input technology. The personal computer had the mouse, touchscreens made smartphones mainstream consumer devices, and AR headsets like the HoloLens and the Magic Leap One have leveraged gesture recognition.