Huawei's sub-brand, Honor, just announced a pair of new smartphones to help close out the year. We knew the midrange Honor 7X was on its way, but what came as a surprise was the announcement of the Honor View 10 and its impending release in the US. Thanks to Honor, US customers will have even more choices in the flagship market with this new device.

Just when you thought Google Glass was dead, it turns out there may be a second life for the often ridiculed device that won't relegate it to the staid confines of factories and repair jobs.

While other devices are moving away from fingerprint scanners (cough, iPhone X), for many, a fingerprint scanner provides the best balance between security and speed. Typically, the rear fingerprint scanner on the LG V30 is quick and accurate, but every so often the phone will not recognize a registered fingerprint.

Not to be outdone by Apple and it's new line of flagship phones, Google has followed suit and finally announced the followup to their highly regarded Pixel line of handsets — the aptly named Pixel 2. Thankfully, the tech giant has also joined in on the trend towards more durable devices, and has engineered both the Pixel 2 and Pixel 2 XL to have a rating of IP67 under the IEC standard 60529.

In case you didn't catch the big event in Cupertino, Apple just unveiled two of the most cutting-edge phones ever made — the iPhone 8 and the iPhone X. Out of the many glorious specs that were rattled off on stage, one stands out for being just a little confusing: Both models are rated IP67 under the IEC standard 60529.

When the climate changes, so do all the things that rely on the climate, including people, plants, and pathogens. A European study recently took a broad look at what kind of microorganisms are most likely to be affected as climate change heats, cools, dries, and wets the world around us.

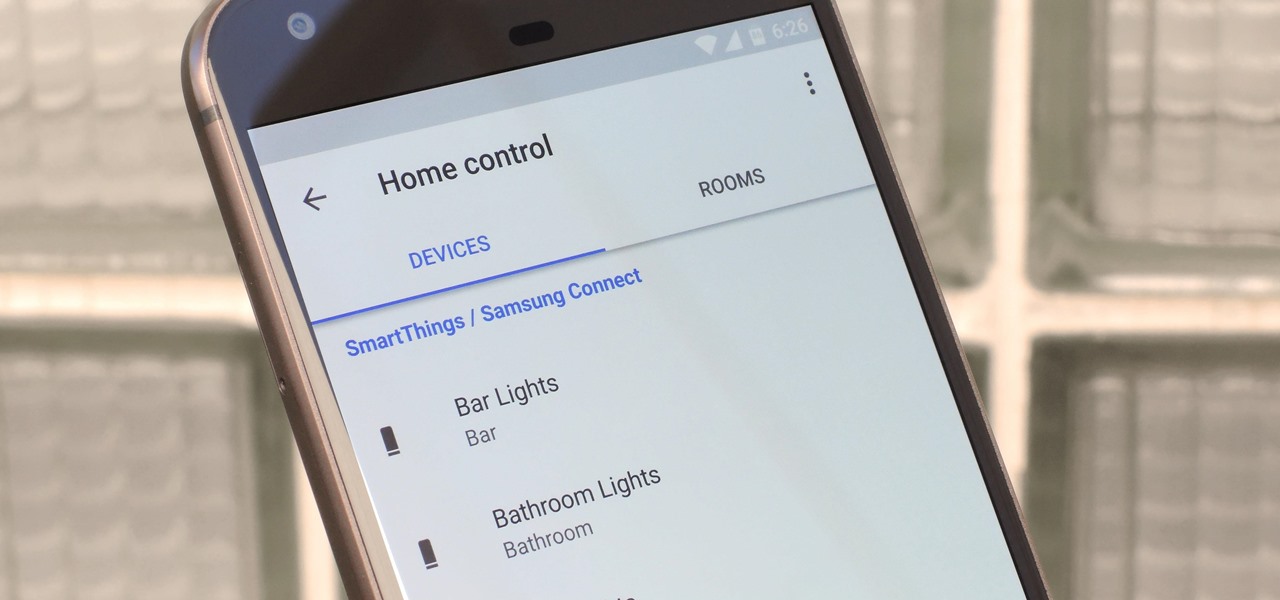
The world around us keeps getting smarter. Not only do we have advanced AI services like the Google Assistant, but now we've got the Internet of Things connecting physical objects to the digital world. It's amazing when you think about it, but the real sci-fi stuff starts to happen when these two technologies intersect.

Forget the rise of the machines. Tardigrades are set to outlive everything — even the bots. When the last echo of a whisper in a cell phone has long dissipated into space, the water bears will still be hanging out.

Nvidia has emerged as the indisputable leader in chips for Level 3 and even more advanced driverless applications, catching some of the world's largest semiconductor makers and automotive suppliers by surprise.

Forget Waymo, Uber, Tesla, and other other heavily mediatized driverless contenders — German premium carmaker Audi AG has become the first OEM to introduce a Level 3 car sold in retail channels.

Tesla hopes high-level personnel changes will help it gain an edge in neural network knowhow for its models' self-drive features, following the replacement of its Autopilot chief and the appointment of a recent Stanford grad to head its AI and Autopilot vision research.

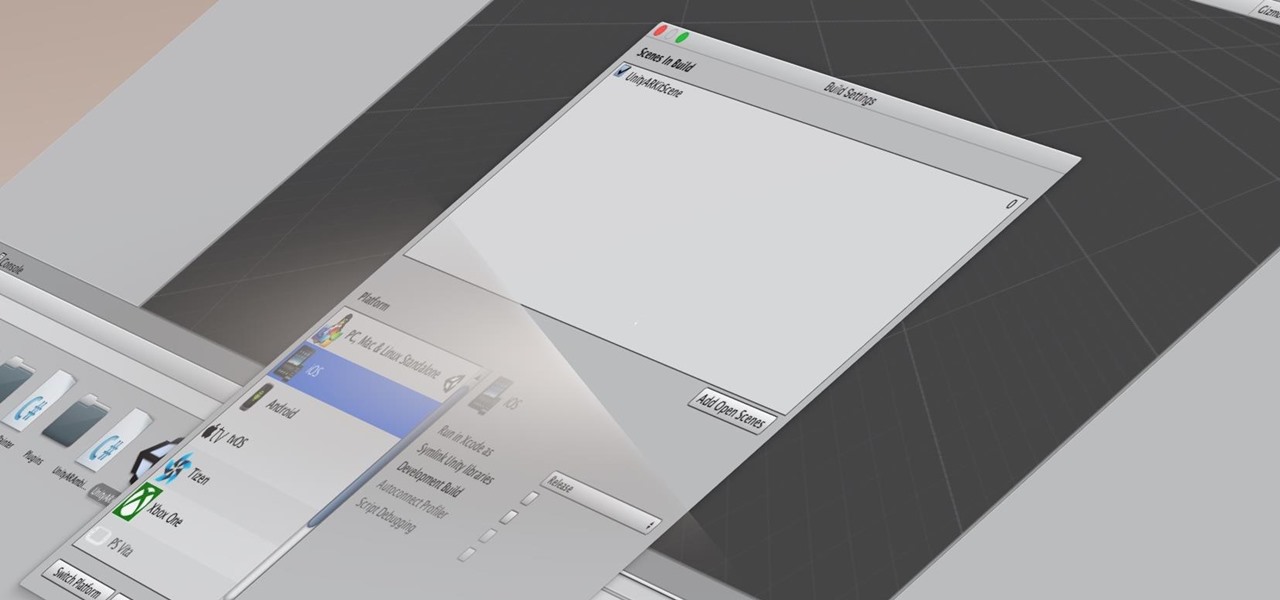
Many developers, myself included, use Unity for 3D application development as well as making games. There are many that mistakenly believe Unity to be a game engine. And that, of course, is how it started. But we now live in a world where our applications have a new level of depth.

The next-generation Audi A8 to launch in July is expected to be the world's first Level 3-capable production car to go on sale in retail channels.

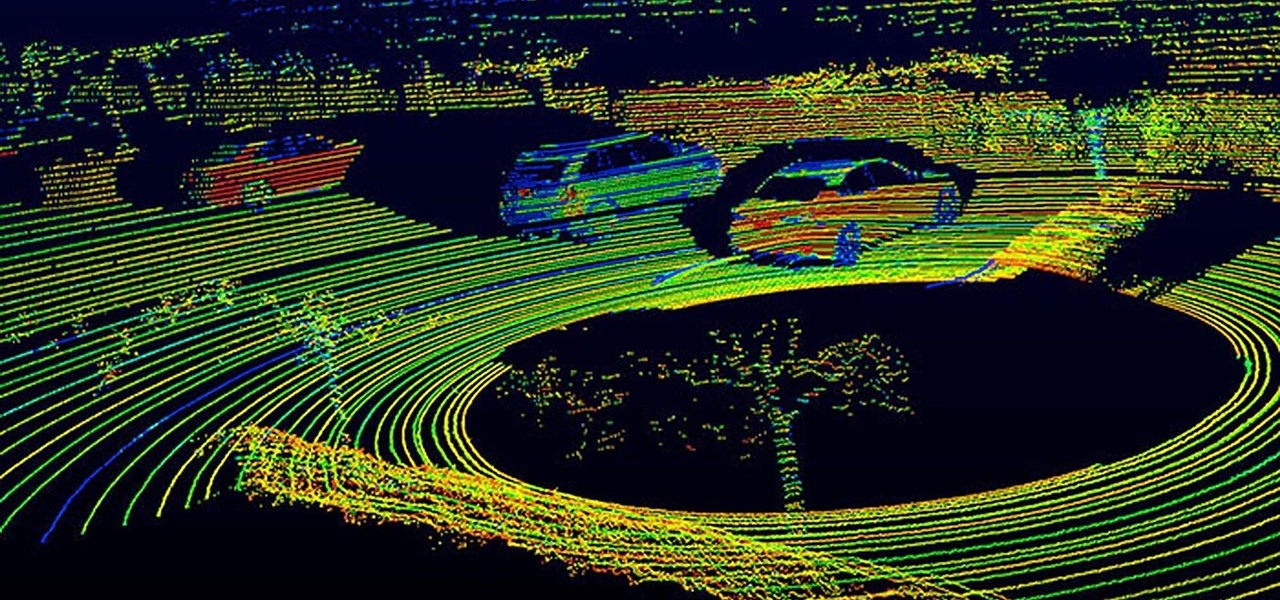
Solid-state LiDAR is cheap, robust, and compact in size — this is why the device is seen as the LiDAR of choice for future high-volume production of level 3 and level 4 cars.

If you're a developer in the augmented and mixed reality space, there's a high probability that you're intimately familiar with the 3D application and game engine Unity. In May, at VisionSummit 2017, Microsoft announced that 91% of all HoloLens applications have been made with the software. But there's a section of Unity that you may not be familiar with, which has become very important to augmented, mixed, and virtual reality (known collectively as XR, for "extended reality") — Unity Labs.

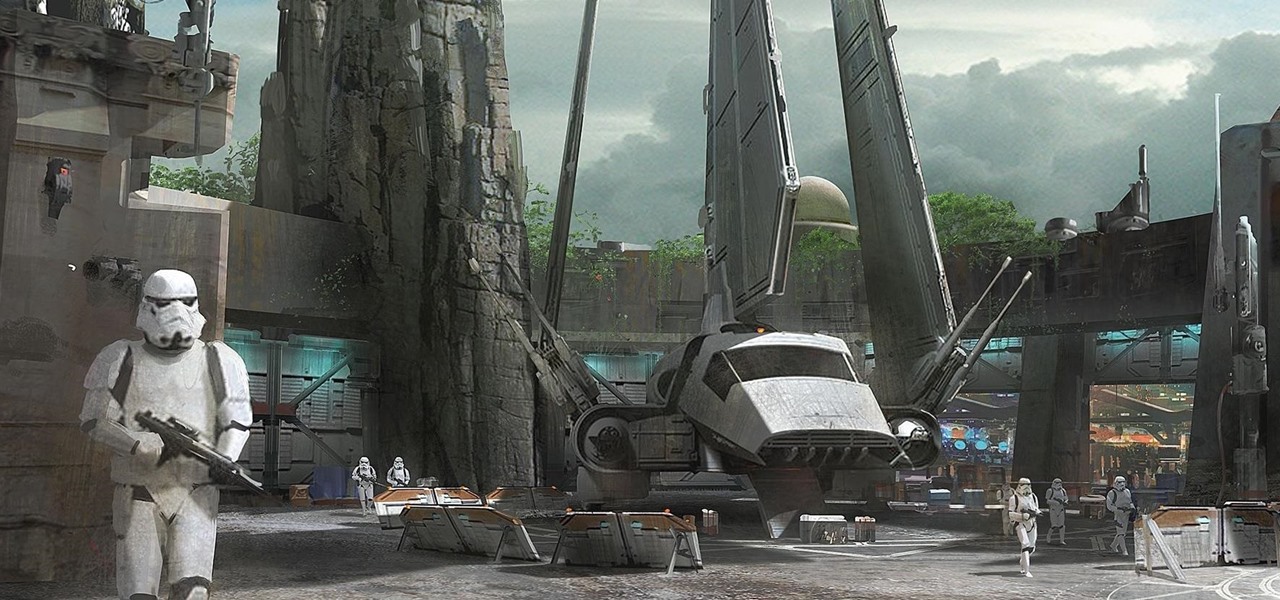
Disney Parks are hard at work bringing the technology from a long time ago in a land far away to life for the opening of Star Wars Land parks in Anaheim and Orlando in 2019.

Rumors that Apple is honing its automated car technology have skyrocketed. Thanks, now, in no small part to some enterprising members of the media who leaked the names of Apple's self-driving car team to the public.

Within the coming months, software startup Neurable plans to introduce the next paradigm in virtual and augmented reality: the brain–computer interface (BCI).

Have you ever had the stomach flu, aka the 24-hour flu? Well, chances are high that you never had influenza, but an intestinal infection called gastroenteritis.

A group of researchers from Stanford University and Princeton University has put together the largest RGB-D video dataset to date with over 1,500 scans of over 700 different locations across the world, for a total of 2.5 million views.

This month, Iowa issued their first hepatitis C virus epidemiological profile and the news was not good. The number of cases of hepatitis C reported in Iowa between 2000 and 2015 rose nearly threefold, from 754 cases in 2000 to 2,235 cases in 2015.

You know the signs—sneezing, fever, nagging cough, no energy, no appetite. It's the flu, but this time, it's your dog who's down and out. Yes, dogs get the flu, too. However, a team from the University of Rochester Medical Center and their collaborators have developed a new vaccine that may make the doggy flu a thing of the past.

The largest and arguably most widely known event of its type, especially in the US, the Sundance Film Festival is an annual celebration of independent film—ones made outside the Hollywood system. This year, a new type of experience appeared at the Sundance Film Festival in an installation called "The Journey to the Center of the Natural Machine." This mixed reality presentation offered the user the newest type of storytelling in a long and important line—continuation of the species kind of im...

The Snapdragon 820 and 821 were met with praise last year, receiving almost no complaints compared to their overheating predecessor, the Snapdragon 810. But now, all eyes are on Qualcomm to see what goodies they have in store for us this year, as their new SoC, the Snapdragon 835, will be revealed this week at CES 2017.

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.

We're almost there to completing the setup of your Mac for hacking! Now that we have Git and Homebrew under our belts, it's time to take on something fairly easy, but very important for our hacking needs.

Hello Guys, Today I have made a script for ddosing sites with VBScript! And I don't know how you guys do it, but I've made a script that refreshes the page in a chosen amout of milliseconds. And if you want it a number of times or if you want it to go on and on. And this is a script to run it on your botnet. But again I don't know if this works on your botnet too.

Hello everyone. It's been a while since I've posted anything (with good reason). But, now that the digital dust has settled, it's time to be an adult about this. I will be continuing to post to Null Byte on a smaller scale, and will also fully participate in whatever communities Null Byte members branch into.

Sometimes the best way to hide things is in plain sight. Whether you're trying to sneak some medication past security at a concert with a zero-tolerance policy, or you're just worried that maybe Omar comin', YouTuber MrGear has a clever way to put your mind at ease.

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

Welcome to the final tutorial of the series on standard C. This article will cover the linked list abstract data type (ADT). There will be a lot of abstraction to try to deliver the understanding in the most basic way for easiest interpretation of what they are and how they work, then we will get into the guts of it and learn the technical code underneath. For those who have yet to grasp the concept of pointers, it's advisable that you do that first before approaching this. Having learned thi...

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.

In python, or any scripting language for that matter, there are certain things that you will carry with you throughout your entire scripting career. Some of the most basic things that you will keep with you are output, variables, and their value types. We'll start by going over output, then cover variables and their types. So, let's get started!

In case you didn't know, Android has an awesome hidden settings menu called "Developer options" that contains a lot of advanced and unique features. If you've ever come across this menu before, chances are you just dipped in for a minute so that you could enable USB debugging and use ADB features.

Hello, fellow grey hat hackers and aspiring coders. I'm back again with another python tutorial. Just that this one is gonna be a lot cooler ;-). We gonna make an encryption program, that well you know encrypts all the files on your pendrive or hdd or whatever you want....Also lots of thanks to DrapsTV. They have helped me a lot with Python and making awesome programs. The video is here:

There's a whole world of wallpapers out there. Apple always includes a selection of stock wallpapers, some unique to every iPhone model you have. Of course, sometimes, stock wallpapers don't cut it. Sometimes, you want to add your own style to your home screen and lock screen. In these cases, using an app to find the best wallpapers out there can be just what you need.

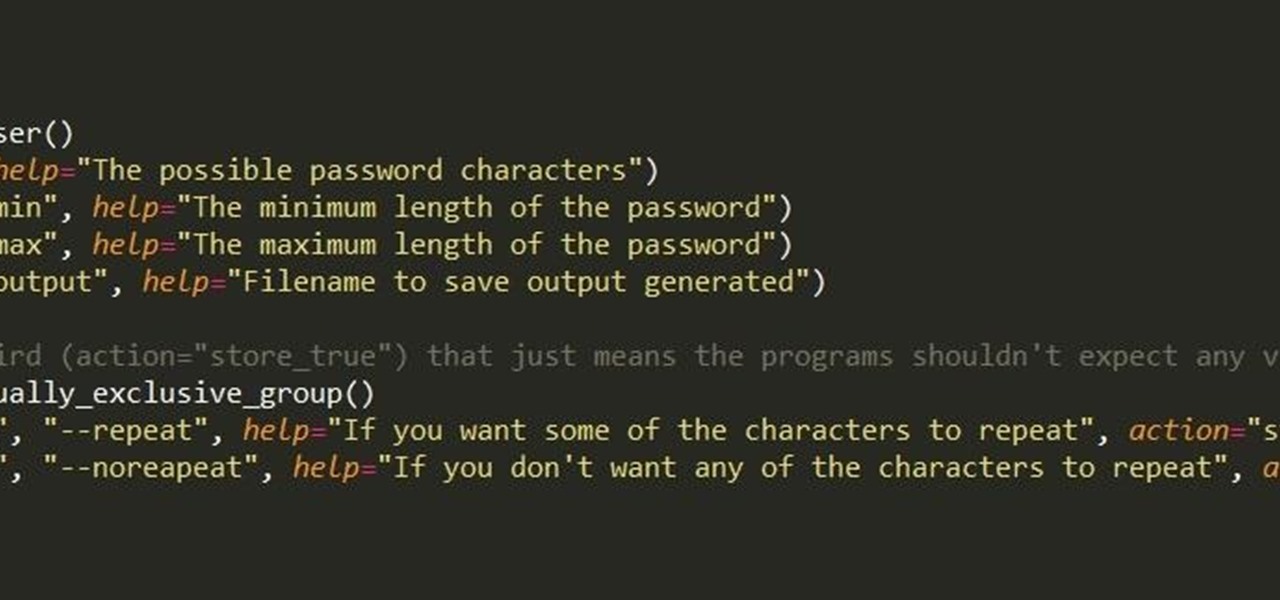
First of all, I hope the title makes sense. :D Well, this is basically creating a program that can help with dictionary attacks. Generate possible passwords. It pretty much lies in you knowing the person you want to hack.

A while back, I wrote review of my favorite hacking movies of all time. Two of my key criteria were; (1) how realistic was the hacking, and (2) are the hackers portrayed as the "good guys." This past winter, a new hacker movie was released, appropriately named Blackhat starring Chris Hemsworth (from Thor fame) as a blackhat hacker who is released from prison to stop a notorious and destructive hacker that only he can stop. Although the movie did very poorly at the box office, I thought it was...