How To: Make a Player Detecting Pistondoor
This tutorial shows how to make a seamless (undetectable) piston door that opens when you walk towards it.


This tutorial shows how to make a seamless (undetectable) piston door that opens when you walk towards it.

Don't you hate when you get a broken nail? Broken nails can be disastrous for a manicure. Next time this happens, don't reach for the clippers right away! In this tutorial, you will learn how to use a simple tea bag to fix your broken nail. This method will seal up the crack and allow you to repaint your nails so no one knows!

Household Hacker brings you fun hack how to projects in a variety of areas: electronic hacks, computer hacks, pranks, etc. Search Household Hacker on WonderHowTo for more videos by this creator. In this video, learn how to cheat with a blank piece of paper.
HIV-infected people who are treated long-term with antiviral drugs may have no detectable virus in their body, but scientists know there are pools of the virus hiding there, awaiting the chance to emerge and wreak havoc again. Since scientists discovered these latent pools, they have been trying to figure out if the remaining HIV is the cause of or caused by increased activation of the immune system.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

In this tutorial, we learn how to change your body features with makeup. To enhance the cleavage, you can purchase a product called Beautiful Breasts. You will first take the matte color and start to define where the breasts and cleavage are. Make the angles natural and make sure the makeup is blended so it's undetectable. Apply shimmer to the collar bone and shoulders to give a glow as well. The products work for any size and any shape and will give you extra enhancement. There is also a pro...

Have you ever found something in your suitcase that wasn't yours? Maybe it was, but you're almost certain it wasn't. Maybe a friend slipped something in your baggage before your departure flight? Maybe the TSA was playing a joke on you, since they have all the master keys for your approved travel locks?

Hello again, folks! I'm back with another (final) guide on runtime crypters which is an extension on my previous runtime crypter guide. If you have not read it yet, I highly recommend that you do since the fundamental theory of the PE format. Again, this will be a Windows-specific guide, so I'll repeat this: If you're a hater and cringe at the slightest sound of Microsoft's grotesque baby, feel free to close this tab, delete your history, exit your browser, pour some oil onto your machine and...

The Galaxy S5's camera is amongst the most capable smartphone shooters on the market. With a 16-megapixel sensor that is capable of recording 1080p video at 120 frames per second, the stat sheet was officially stuffed when Samsung brought this device to market.

HIV infections persist despite treatment that successfully decreases viral blood levels to the point where doctors can't detect the virus. But that doesn't mean the person is cured. The virus hides in the body, not replicating, just waiting for a chance to jump out of the shadows and reemerge.

Video: . Recycle your hard drive into a hidden flash memory device that only you know how to turn on and use in secret. This DIY hack project allows you to recycle your broken hard drives back to life and turn them into something useful.

PowerPoint 2008 for Mac can help you turn boring old bulleted lists into something nobody would forget. With SmartArt graphics in PowerPoint you can now make your bullet lists pop using pre-formatted charts, graphs, and more. The Microsoft Office for Mac team shows you just how to make a bulleted list more visual in this how-to video.

Developing an imperceptible lie is difficult, especially when you're lying right to someone's face. Thanks to smartphones, getting people to trust you is now easier than ever. You can craft a lie in seconds and hit send, all without ever seeing their untrusting faces.

It's exciting to get that reverse shell or execute a payload, but sometimes these things don't work as expected when there are certain defenses in play. One way to get around that issue is by obfuscating the payload, and encoding it using different techniques will usually bring varying degrees of success. Graffiti can make that happen.
Dull and drab bulleted lists are no longer necessary with the help of PowerPoint 2008 for Mac. When you make a bullet list in PowerPoint, you can now transform those boring text charts with actual visual charts and graphs and more. The Microsoft Office for Mac team shows you just how to convert text to a SmartArt graphic in this how-to video.

This video explains how to add a bulleted or numbered list in Microsoft Word 2007. The shortcut to create a bullet-list is simple holding Shift and pressing the "A" key. After you hit the space bar or type a character the bullet will appear, and when you hit the Enter key it will continue the bulleted list. For numbering you just need to type the number you want and a dot after it and it should begin a numbered list. The list will continue if you press enter just like a bullet-list will. If y...

You're all kale-d out, you've had it up to here with golden milk, and you're on the prowl for the next superfood. Well, get ready for some unicellular goodness: the next superfood is an algae named Spirulina, also known as Blue Majik. (Kudos to the marketing exec that came up with that, am I right?)

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Was Napoleon's death really due to stomach cancer, or was it arsenic poisoning? Some scientist believe the latter. Arsenic poisoning was a deadly weapon in that era, because it was undetectable when administered over a long period of time, making murder seem like natural causes. But if arsenic (As) is poisonous to most multicellular life, then what's with the newest NASA discovery?
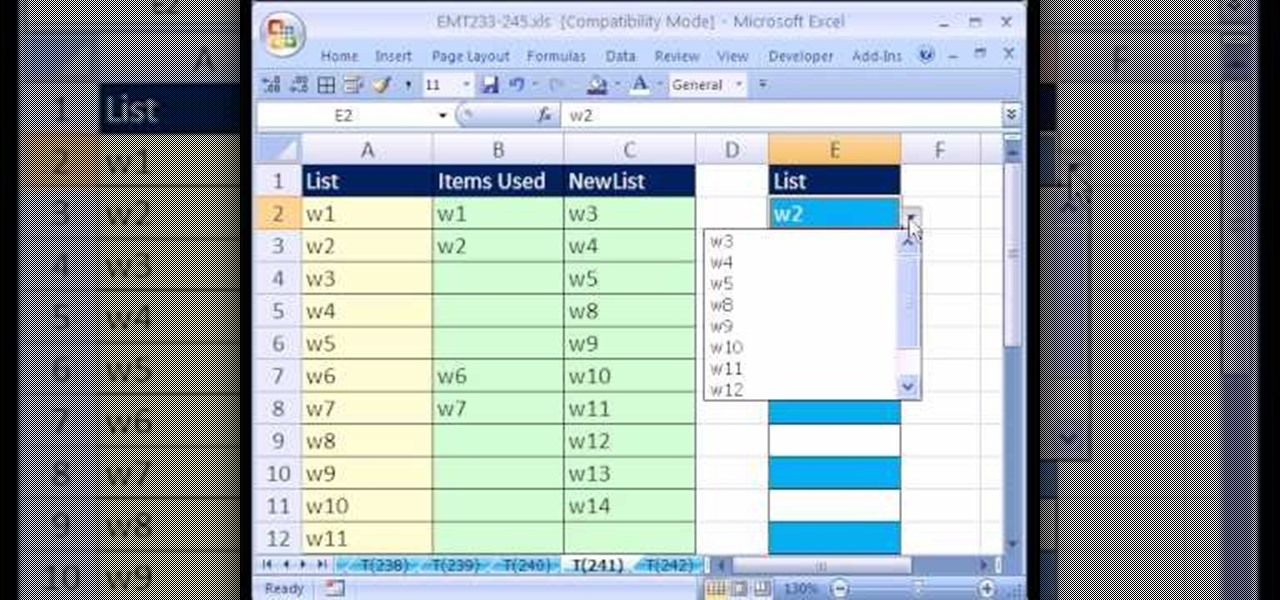
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 241st installment in their series of digital spreadsheet magic tricks, you'll learn how to create a data validation drop-down cell list where the list shrinks as you select values.
In this video, we learn how to create a favorites list on an iPhone. Doing this will make it easier and quicker to speed dial! First, just tap on the "favorites" button. Then, click on the "+" button to add a new favorite from your contacts. You can then click "edit" to rearrange or remove favorites from your list. Click on the blue arrow next to a name to see the full contact details for that person. As soon as you add or remove someone from your favorites it's saved. That's all you need to ...
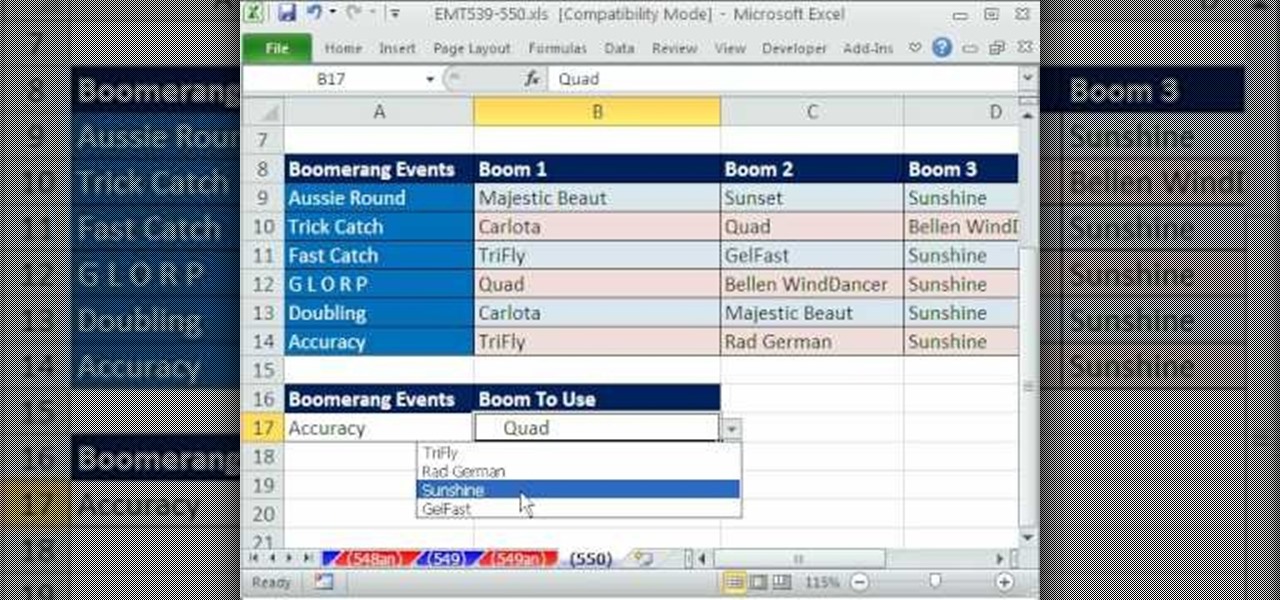
Excel dilettantes and seasoned Microsoft Office professionals alike may be surprised to learn that in Excel one can make a drop down list based upon a second drop down list (or, similarly, data validation list that is based on a second validation list).

This video will go over how to insert a check box in Microsoft Word for printing or for electronic distribution. With just a few clicks you can get a check box. You can even add different symbols or styles for your check box.

Ever since the introduction of Google's SafetyNet feature, it's been an ongoing battle with apps trying to detect root access. For a while, there was a lot of back and forth between Magisk and certain apps. Pokémon GO was a high profile example of an app aggressively checking for anything related to root. Luckily, Magisk has made great strides to keep apps from detecting root for good.
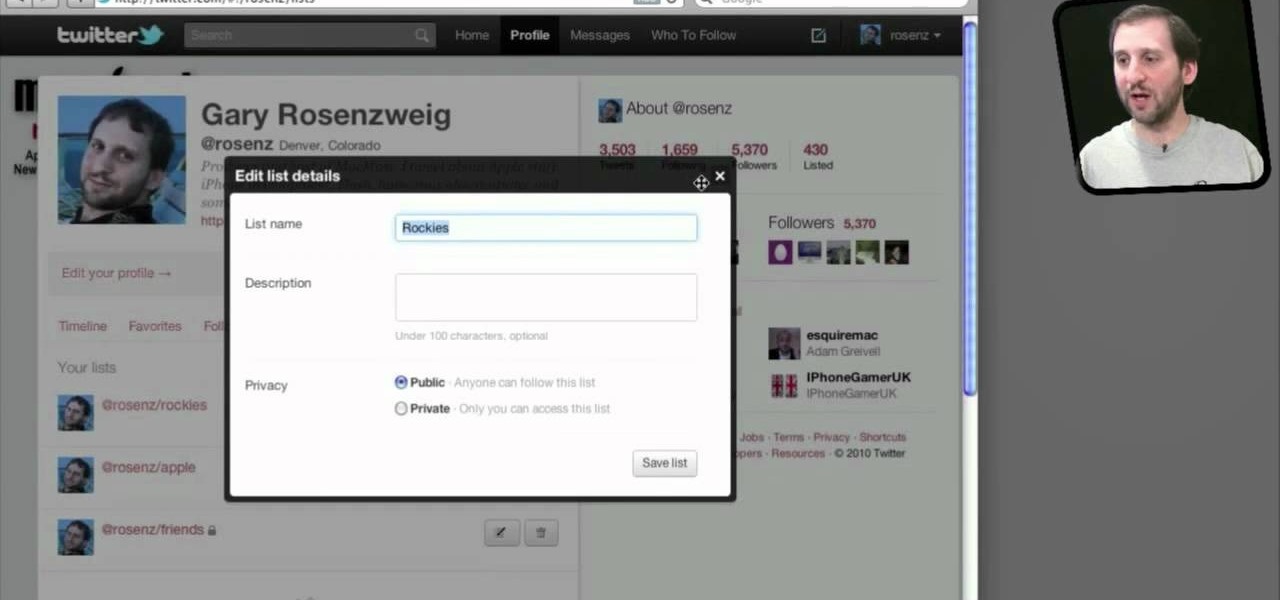
Do you spend a lot of time on Twitter? You can sort and organize the people you follow by grouping them together into Twitter lists and then viewing only that list. These lists are arbitratry categories that you create and can be viewable by others, or made private. You can also view other public lists that people have made. This video shows you how.
MySpace gives users the ability to hide their friends list. This video walks you step by step through being able to view this list. First, go to the desired profile. You'll see the hidden friends list. Now, click on "Edit with notepad" and code will pop up on your notepad. Because the list is on the page, editing the source code will make the list appear on the page. Next, type the command >table border=0 cellspacing=0 align="center">. Now you'll be instructed on how to delete the source code...
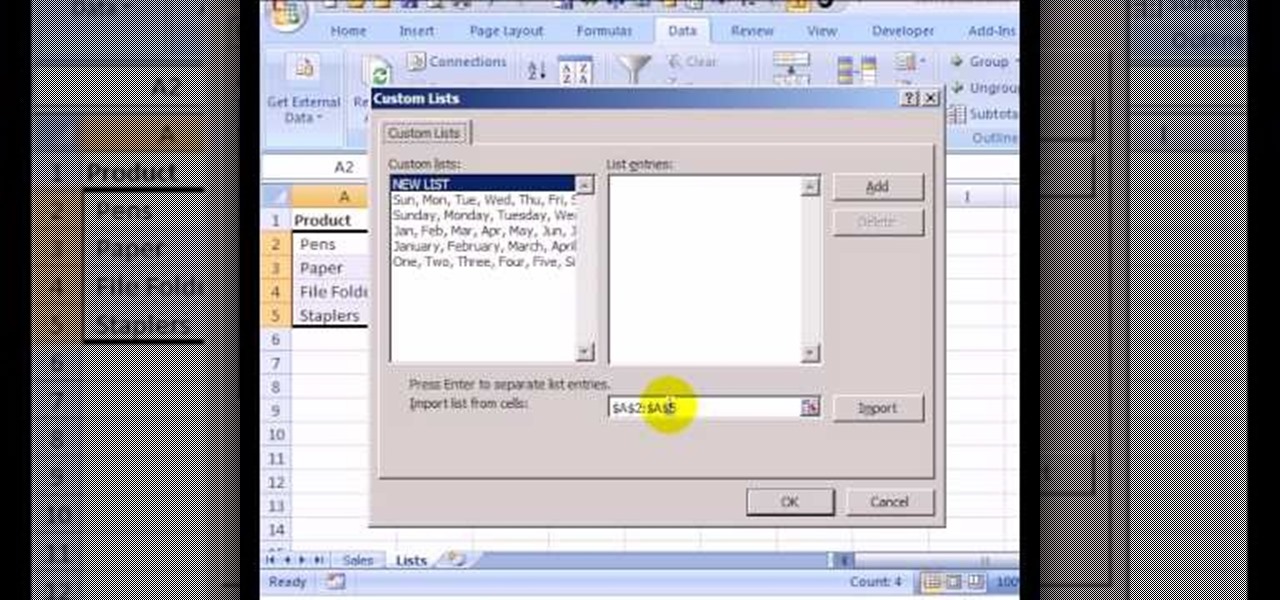
This how to video shows you how to sort data in Excel in a custom order. First, open a spread sheet in Excel. Select a column of cells with words that you want sorted. Click the office button and select Excel options. Go to edit custom list. You will see different custom lists. Click import to import your selection as a custom list. Next, you can go back to a sheet with those words that you want sorted and click the sort command. Select custom list on the order tab and select your new custom ...
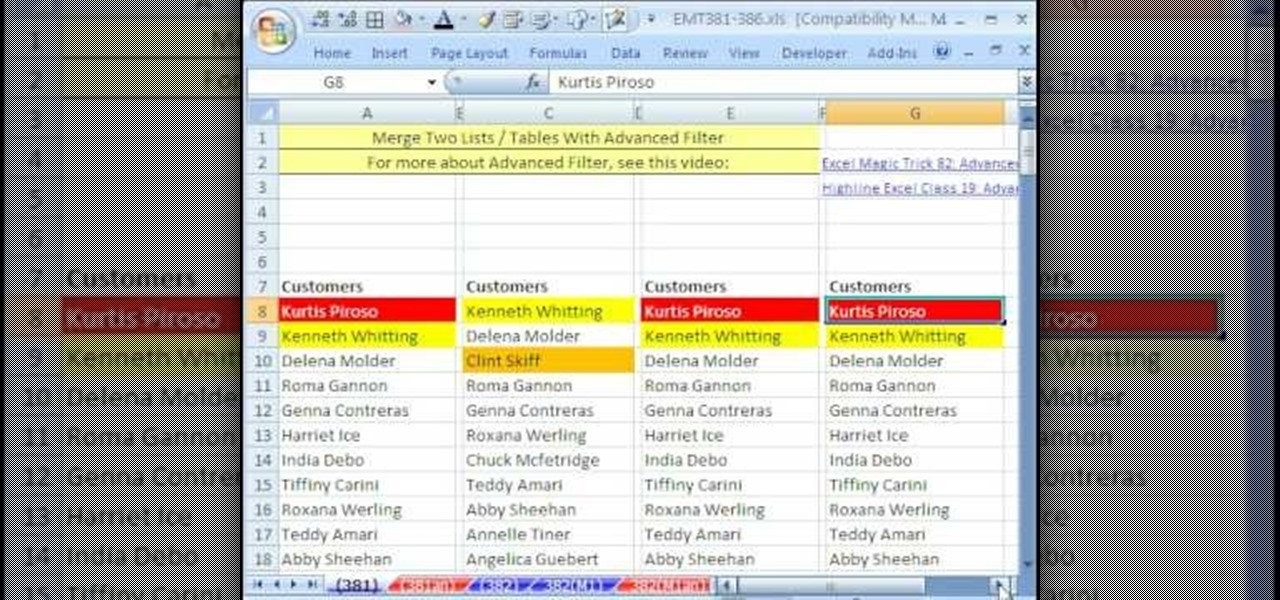
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 381st installment in their series of digital spreadsheet magic tricks, you'll learn how to merge two lists into one list while keeping unique items from list 1 and list 2 and removing duplicates.

Apple's Reminders app has never been particularly sexy or appealing, but that changes in iOS 13. Although the productivity tool has always been useful for quick to-dos, it now has an overhauled user interface with several new features, including grouping lists together for improved organization.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.
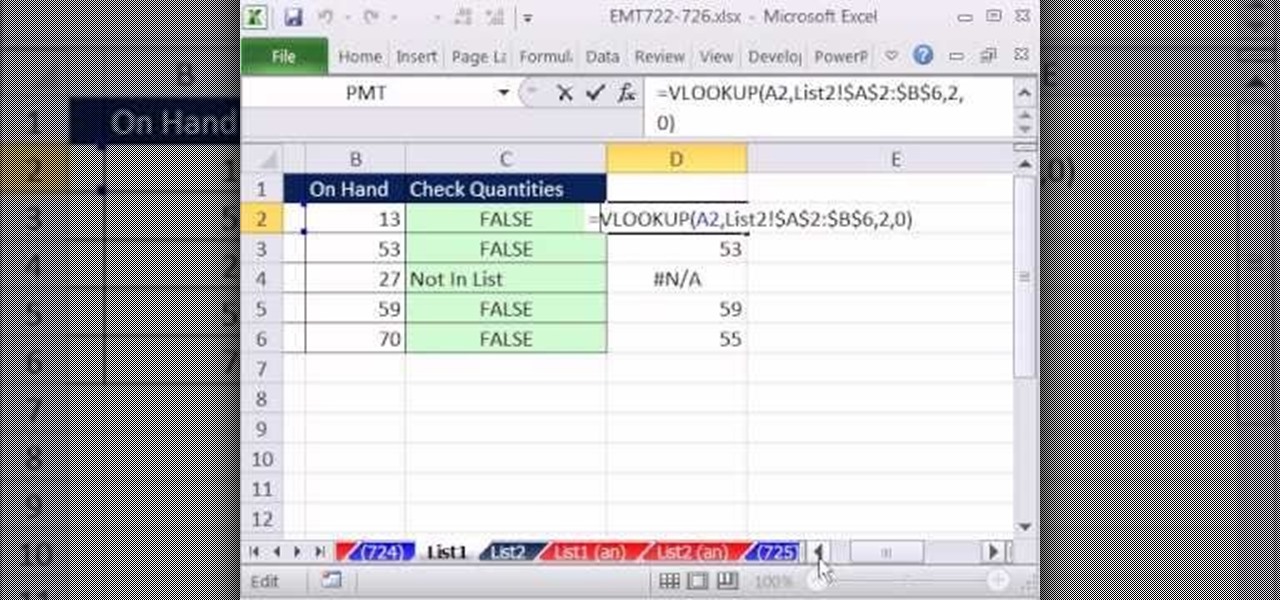
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 724th installment in their series of digital spreadsheet magic tricks, you'll learn how to check if quantities are the same in two lists and show the differences if not, list the word "equal" if they are the same, and "not in list" if the lookup items is not in list using the MATCH, INSA, VLOOKUP and IF functions.
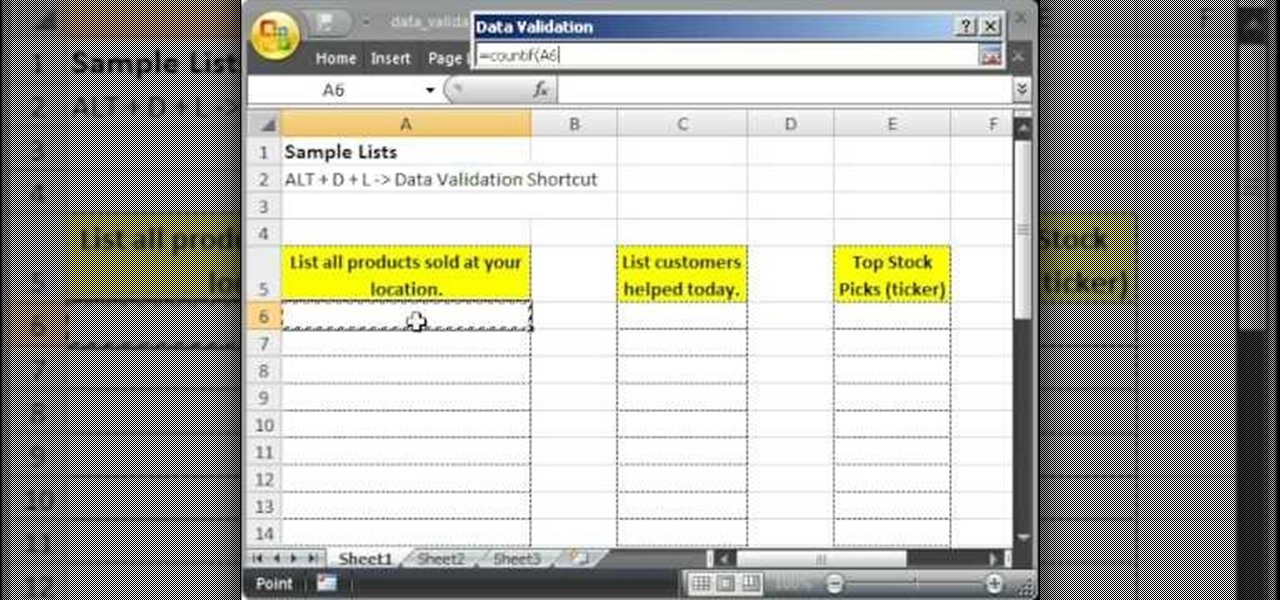
This tutorial describes how to make a list with unique values in Excel.This procedure makes the defined cells in a column (called as list) NOT to accept repeated values, which makes the list more simple, readable, easy to manipulate when preparing a worksheet.
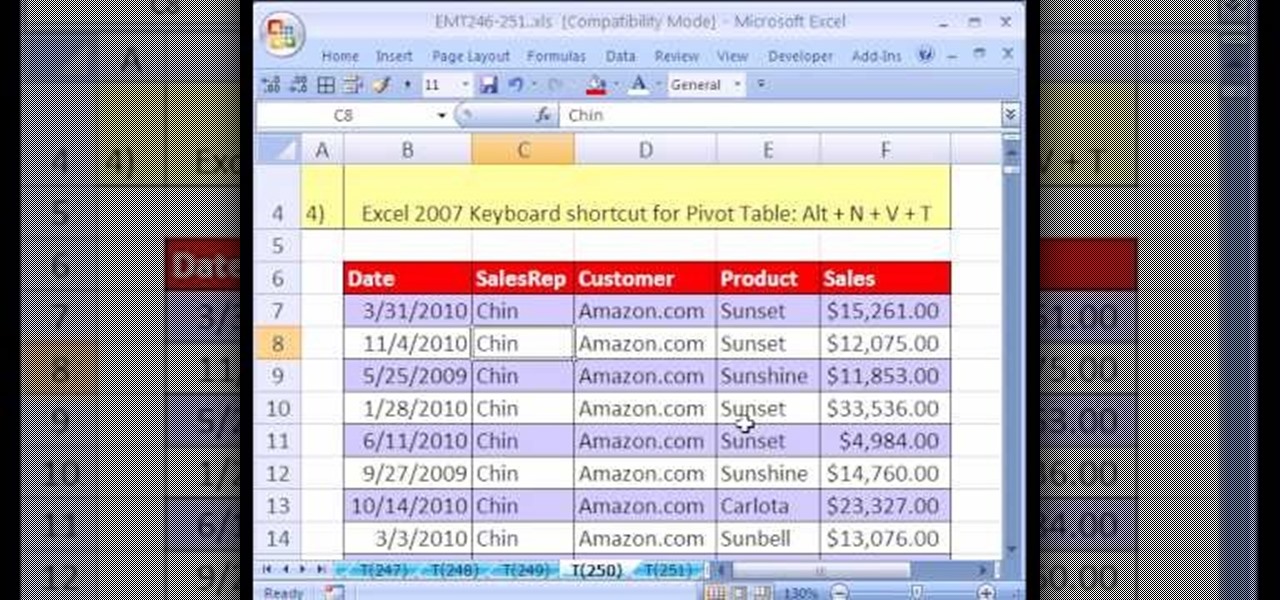
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 250th installment in their series of digital spreadsheet magic tricks, you'll learn how to create a unique list of customers within a unique list of sales representatives using a pivot table (PivotTable).
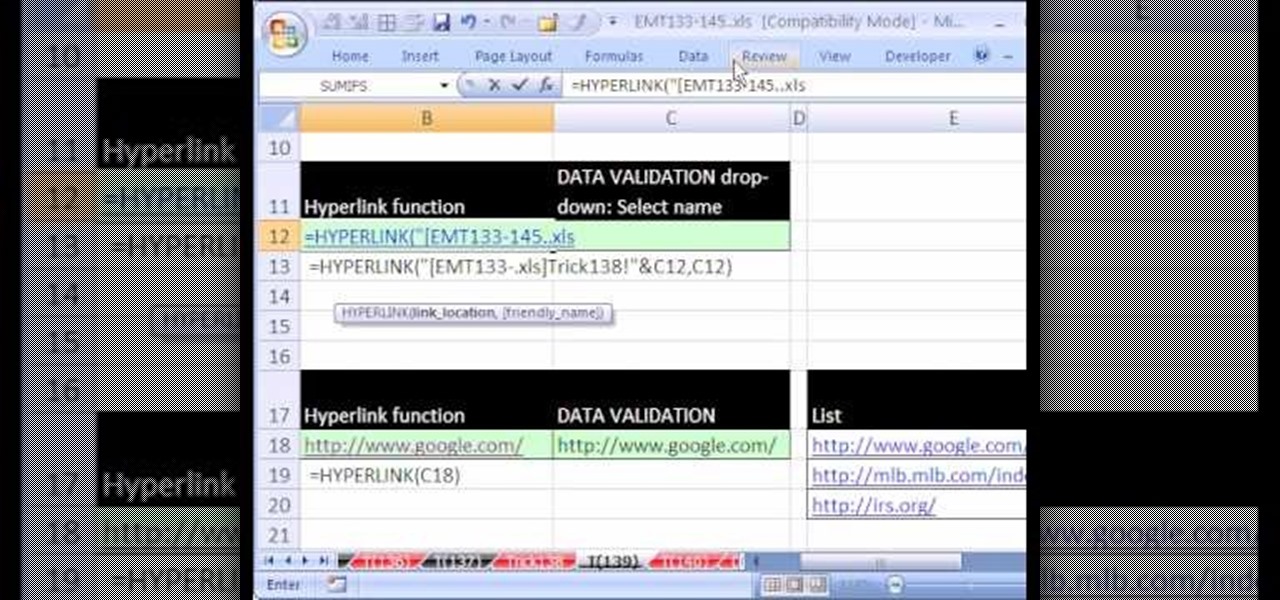
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 139th installment in their series of digital spreadsheet magic tricks, you'll learn how to use a data validation list drop-down and the hyperlink function to create a list of links.
Add lists to your Flash-based website, game or other project. This tutorial shows you how to use Action Script 3 and Adobe Flash CS4 to create custom lists with interactivity features, like music playlists, and incorporate them into your project.
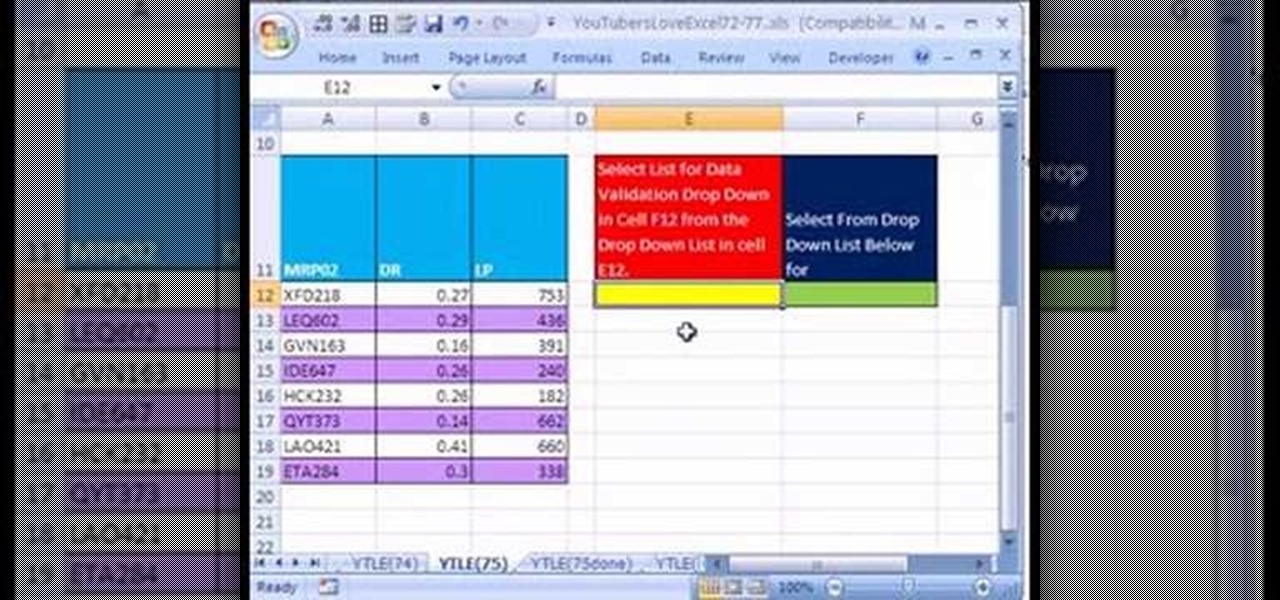
Love Microsoft Excel? This clip contains a tip that just might induce you to. With this free video tutorial from ExcelIsFun, the 75th installment of his "YouTubers Love Excel" or YTLE series of free video MS Excel lessons, you'll learn how to use name, the INDIRECT function and data validation drop-down lists to create DV lists based on DV lists.
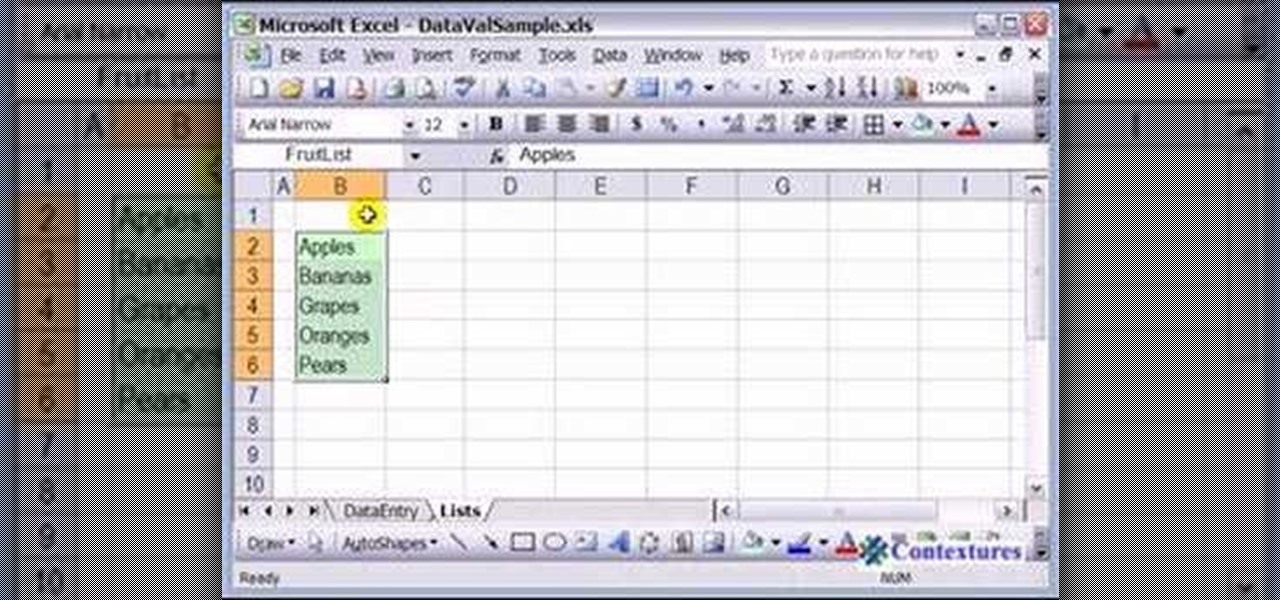
This how to video shows you how to use drop down lists in Microsoft Excel. This will be useful for stores and avoiding people ordering items that are not available. First, type the items in a column. Select them and then click in the name box. Type the name of the list. Note that it must be one word. Now, go back to the order sheet. Select the cell where you want the list to be placed. Go to data and select validation. On the settings tab, choose list and type in = and list name. You can pres...
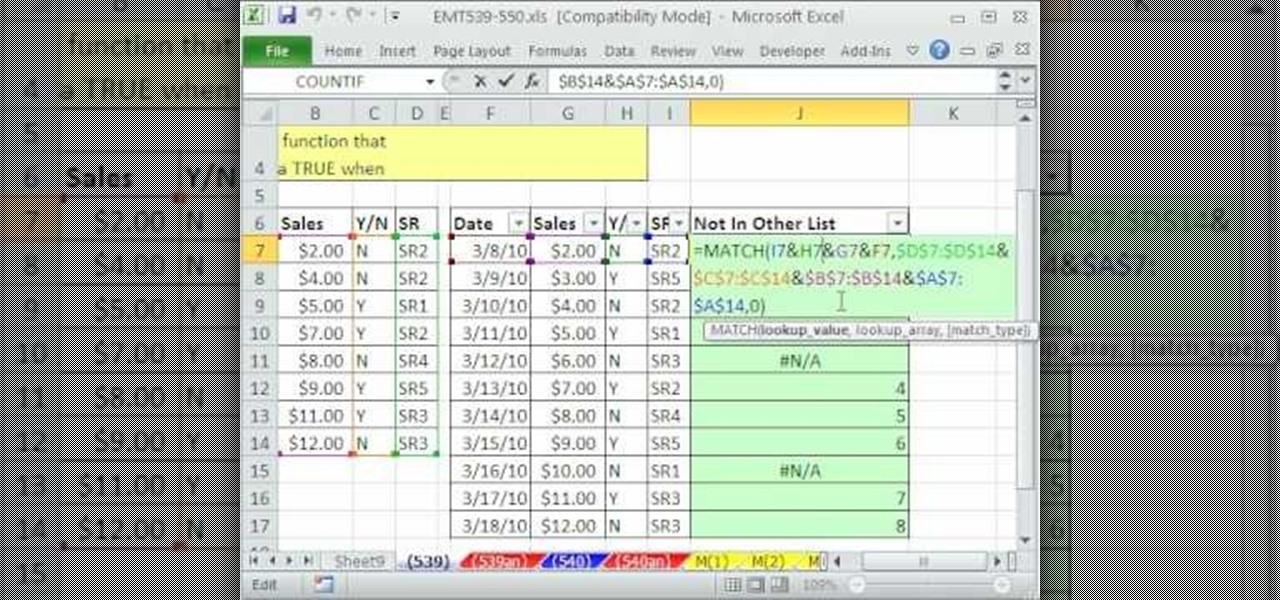
Need to compare two datasets and extract the new values? In this the 539th installment of ExcelIsFun's series of Excel magic tricks, you'll see how to use the MATCH function, the Join Symbol (& Ampersand), and the Filter feature to check two 2 lists of transactoinal records and extract only the new records (records that are in new list but not in old list).