The last time the English language for Siri received new voices was in iOS 14.5, and there was one new male and one new female selection, bringing the total to four available options. In the iOS 15.4 update, there's a fifth one, and it may work better as a gender-neutral middle ground between the low-pitched male voices and high-pitched female ones.

Anyone who has been within a block of any wireless brick and mortar store or tech conference in the last couple of years has no doubt seen banners, posters, and videos promoting 5G high-speed wireless services on the way.

During Huawei's P30 smartphone launch event on Tuesday, the China-based company unveiled a surprise addition to its line-up: smartglasses.

The rise and fall of Meta, the Silicon Valley-based augmented reality startup that looked to challenge the likes of Microsoft's HoloLens, and others, took just six years.

A week into my internship, I experienced pretty serious back pain and slight difficulty breathing. I scheduled a doctor's appointment to make sure nothing was wrong, and I got a surprising diagnosis: bad posture.

It took many months of cries from all around the internet—and a particularly large groan from an ex-Lifehacker editor-in-chief—but Apple has not only acknowledged the existence of its iMessage problem, it's promising a fix.

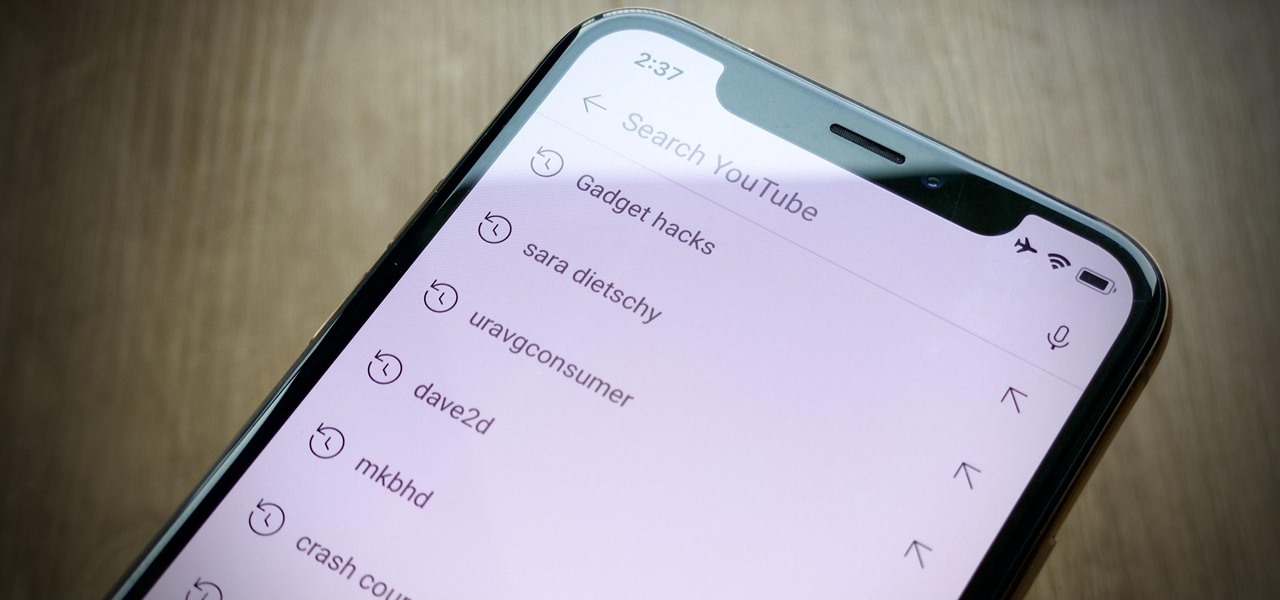
Sure, your search history can be useful, but more often than not, it's a paper trail of privacy infringement. It's perfectly reasonable not to want to see a complete list of your YouTube queries every single time you search for a new video. Luckily, blocking YouTube from saving your search history takes only a few taps.

To borrow from the canon of Game of Thrones, what is dead may never die. And while the Meta Company that we knew this time last year is no more, the patent infringement lawsuit filed against the company lives on.

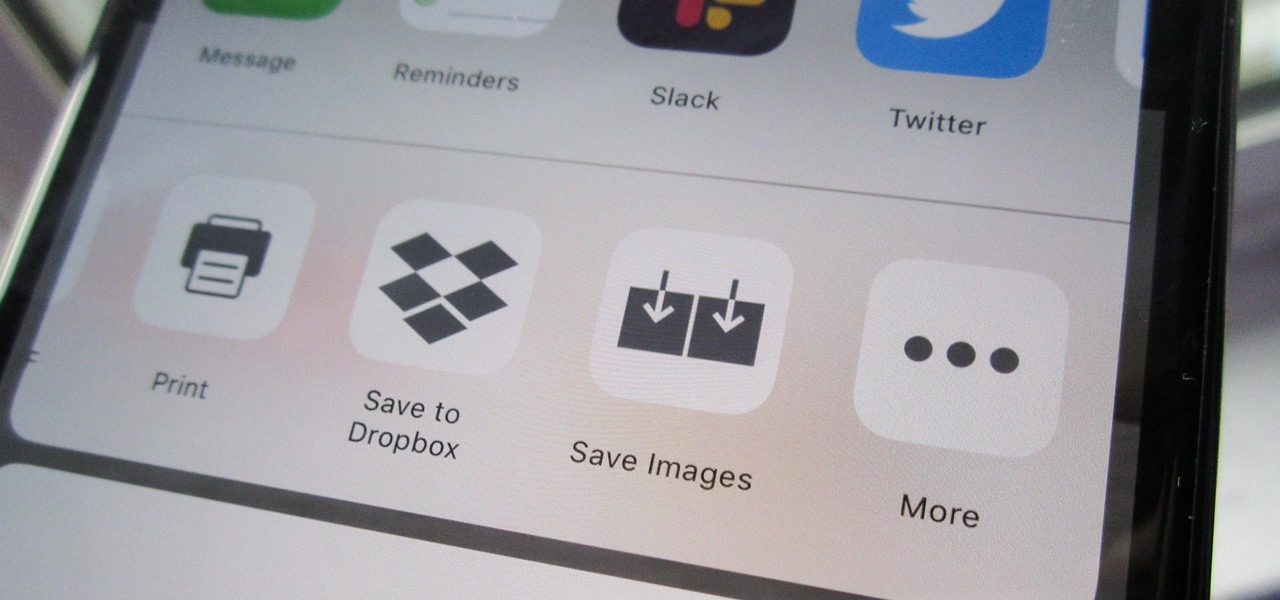
Some websites block image downloads on their webpages so you can't save them for reuse. That means long-pressing or force-pressing on protected images in Safari on your iPhone will not do anything or will omit the "Save Image" option. Taking a screenshot is the obvious solution to bypass restrictions, but you won't get the best quality. Thankfully, there's another way.

The saga of augmented reality startup Meta appeared to be at end, but there are new developments unfolding in real time that may either sink Meta deeper into trouble, or provide a tenuous lifeline for the beleaguered augmented reality company.

Richard Buccola has been playing pool most of his life, and enjoys teaching it to others Trick shots in the game of pool are often associated with hustling, or sharking. During the mid-20th century pool halls were often given an unfair reputation as dangerous, seedy dens of sin (especially after the 1961 Paul Newman film “The Hustler”) where people would lose their money to unscrupulous pool sharks. But interest in the game has seen a rebirth of sorts in recent years, and most pool halls and ...

The fight to wrest control of apps from Apple's revenue-focused grip just took a major turn in favor of Epic Games.

The long wait is over — the best augmented reality device on the planet is finally available.

The newly-announced Moto G7 Play offers some of the same upgrades as its sibling, the Moto G7, but at a much lower price. The upgrades are pretty significant when compared to last year's Moto G6 Play, taking this phone from the "only if you're on a strict budget" category into a great value option.

Google just bought a huge chunk of HTC for $1.1 billion. They're bringing in around 2,000 employees, mostly from the hardware division, and these folks will presumably work under hardware chief Rick Osterloh. There's a massive patent portfolio involved, too, so stop me if you've heard this before — Motorola, anyone?

When Google announced YouTube Red — a paid monthly subscription service that disables advertising, among other perks — many of us thought "just use an ad blocker." But it isn't really that simple.

Most carmakers now agree with Waymo that piloting driverless cars is best left to the machine — with no meddling from the human.

Pokémon GO, the global augmented reality game that's brought fans out of their homes to catch Pokémon across the planet, has brought about plenty of real-world positives. Unfortunately, when players get power hungry and start taking game hacks too far, we all get a little screwed—both digitally and in real life.

One fight for augmented reality branding that we thought had been settled has suddenly turned into a full-fledged legal battle—again.

The story of the HoloLens has been a mix of work and play. But while many developers have devoted time to creating gaming and entertainment apps for the HoloLens 1, with the HoloLens 2, Microsoft has been encouraging everyone to focus more on the enterprise side of things.

The worlds of augmented reality and virtual reality are closely linked in many ways. That means it's smart for AR insiders to keep a close on new developments in VR. If you have been paying attention, you know that Oculus CTO John Carmack is one one of the most important thinkers in the VR space.

With the best selling phone on Amazon in 2018, Lenovo had big shoes to fill when making the successor of the Moto G6. Fortunately, Lenovo was up to the task. The Moto G7 continues to provide a high performance-to-price ratio, offering a worthwhile upgrade for G6 users while remaining budget friendly.

Following the launch of the Magic Leap One earlier this month, the device and the company took a few hits from early reviewers. But it turns out those were just love taps compared to the absolute scorched earth acidic screed penned this weekend by someone well credentialed to dissect Magic Leap One: Oculus Rift creator Palmer Luckey.

Between the Cambridge Analytica scandal and the revelation that Facebook logs your calls and text history on Android, many are considering joining the #DeleteFacebook movement. But it can be difficult to leave the site, because so much of its content is only available to active users. If you want to keep in the loop without sacrificing your privacy, you'll want to follow the steps below.

Video games are one of the few items that have successfully advanced and adapted over decades, while still holding its "old school" value.

While Touch ID has been a part of the iPhone's legacy since 2013, Apple waited until 2016 to add biometrics to its MacBook lineup, and it's not as impressive. An iPhone with Touch ID can register up to five fingerprints, but Macs can only register a maximum of three per account. If that seems unfair, there's an easy trick to doubling that number, meaning six of your fingerprints could unlock your laptop!

Since the Razer Phone's announcement in 2017, we've seen a new subgroup of phones emerge. Gaming phones are now a thing, leading to companies like ASUS creating phones that are thoroughly optimized for the mobile gaming experience. And with their second iteration, they perfected it.

After years of rumors and waiting, Samsung's first foldable smartphone is finally a reality. The phone itself is a bit wild, but with Samsung going so far out of their comfort zone with this one, there were some bumps in the road that caused a delayed release. The launch has been pushed back yet again, but when it does hit stores, it could end up being one of the most influential devices in years.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

Wordle has been popping up all over in the app stores, but none of them are the real Wordle. The popular word game app has amassed two million users since its launch in November 2021 but has no plans to hit the iOS App Store or Play Store any time soon — but you can still install the official Wordle app on the Home screen of your iPhone or Android phone.

The recent announcement that Facebook will begin inserting advertisements into its VR experience on its Oculus Quest headset has set the VR and augmented reality industry into a frenzy.

Magic Leap has had a rough couple of years, highlighted by high-profile executive departures, lawsuits, troublesome patent shuffles, and massive layoffs.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

SCRABBLE. To some it's just a game, but to me it's life or death. Well, not really, but it feels that way anyway. On a normal weekend, a game becomes much like Jon Thomas' "friendly game of death Scrabble."

Google and Snap held their annual conferences this week, and both companies managed to upstage their new AR software features with fantastic new AR hardware.

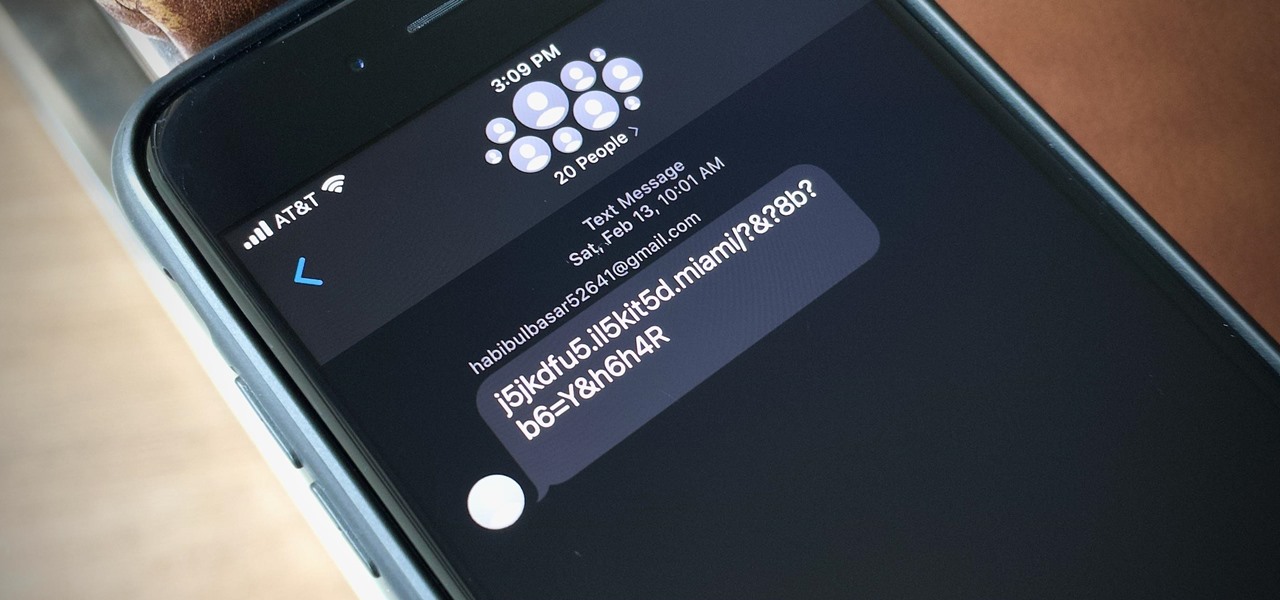
Next to spam calls, few things are more annoying than being inundated with spam, scam, and smishing texts. Your iPhone's Messages app should be a place for your friends and family to stay in touch, not a minefield of phishing attacks, malicious links, and viruses. Luckily, there are quite a few methods to block and report your way to a more spam-free iPhone.
If you did anything but watch the Superbowl alone with a small screen TV, then you are in violation of copyright infringement law, according to this article!

Ah, the image macro -- capitalizing on ppl iz stoopid and borderline copyright infringement since 1763. Sweet!

This rubik's-style, puzzle head was created for a commercial for Drench, a British soft drink. How'd they do it?? 3D Studio Max? After Effects? Anybody know? Nonetheless, awesome special effect.
Cheating ruins everything. Cheating makes game play unfair for others who may be truly competitive and strategic. Cheating makes others disrespect and un-friend you. There can be unforeseen consequences, like getting viruses, trojans or your account hacked from downloading a cheat/bot program. And you will get banned from the game for violating terms of service.