The last iOS software update was a modest one, but iOS 17.4 has a lot more for your iPhone, including changes to emoji, Podcasts, security, Safari, widgets, Apple Cash, CarPlay, and more.

There is a whole world of smartphone accessories out there, some of which are more quirky than others and don't get the recognition they deserve. But these sometimes strange, sometimes embarrassing products can really make life easier on your iPhone or Android phone.
Apple's latest big software update includes an entirely new Apple app, a controversial change in the TV app, better Siri control, an improved Shortcuts app, interesting Safari upgrades, Apple Music Sing, and more. Keep reading to see what iOS 16.2 has to offer your iPhone.
Apple made significant improvements to its Shortcuts app in the latest iOS update, so you can do even more with your custom-made macros for iPhone.
Believe it or not, there are legitimate iOS apps beyond the App Store that you can install on your iPhone. Some of them even work for iPad, Apple TV, and Mac, and there are also benefits to using them over apps found in the App Store.

Bash scripting is a convenient way to automate things on any Linux system, and we're going to use it here to automate certain tasks we use all the time.

A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangible or intangible from harm. While there are more nefarious uses for a dead man's switch, white hats can put one to good use.

Apple has four iPhone models for the remaining months of 2020, but the most impressive ones are the iPhone 12 Pro and iPhone 12 Pro Max. While the iPhone 12 and iPhone 12 mini are great smartphones, the "Pro" models offer more advanced features, especially for photographers and augmented reality enthusiasts.

There are countless tutorials online that show how to use Netstat and Tasklist to find an intruder on your computer. But with a few PowerShell functions, it's possible for a hacker to evade detection from the almighty command line.

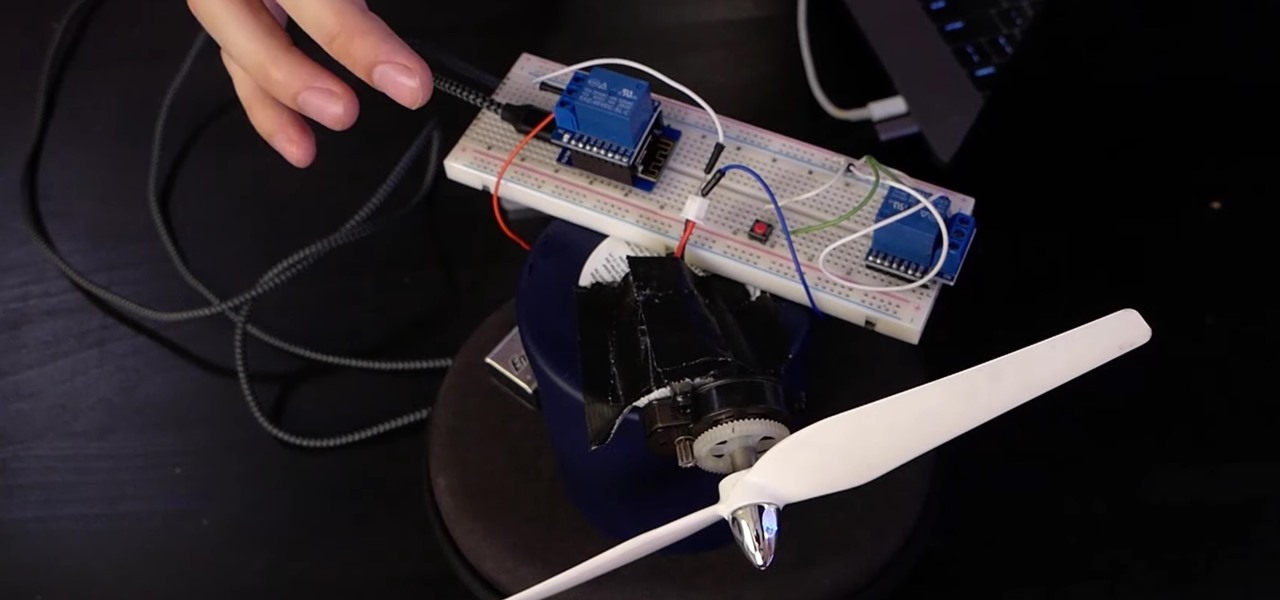
If you want to control electronic devices, such as a relay or motor, you can do so using MicroPython with an ESP8266 and web browser. Usually, you'd program an ESP8266 using Arduino, but C++, which Arduino uses, is not always the easiest programming language for beginners to learn.

In the case of Apple Watch v. Fitbit, the winner comes down to the judge at hand. Apple currently offers two smartwatches — the Series 5 and the Series 3 — while Fitbit offers three models — the Fitbit Versa 2, Fitbit Ionic, and Fitbit Versa Lite. Whatever your assumptions about these devices are, throw them out the window, as each has something unique to bring to the table.

In a time where we're more connected than ever, privacy and security have never been more important. Maybe you're not concerned, but I'm sure there's someone in your life who is, and shopping for them can be daunting. However, with these gifts, you can provide them the tools they need to enhance their protection.

Apple's iOS 13 has been available for beta testing since June, and the stable release pushed out to everyone on Thursday, Sept. 19. To help you make the most out of iOS 13 for iPhone, we've rounded up everything you'll want to know, whether a colossal feature, small settings change, interface update, or hidden improvement.

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

With smartphone cameras and software getting better and better every year, more and more users are getting passionate about photography. So when you're shopping for a gift to get someone, if they have a smartphone, chances are they'll more than appreciate some tools and accessories for taking better photos with their pocket friend — and we've got some gear ideas they'll love.

Airgeddon is a multi-Bash network auditor capable of Wi-Fi jamming. This capability lets you target and disconnect devices from a wireless network, all without joining it. It runs on Kali, and we'll cover installing, configuring, and using its jamming functionalities on a small, inexpensive Raspberry Pi. When done correctly, it will deny service to a wireless network for up to several blocks.

Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, it requires no special dependencies and can be run via SSH, making it easy to deploy remotely.

With Facebook and Twitter dominating the world, playing chess opposite a real, touchable person is no longer necessary. With the ChessBot, you can now play on a real chessboard remotely - the next best thing to in-person play.
DARPA is at it again. This time, the Defense Advanced Research Projects Agency has announced plans to create nanochips for monitoring troops health on the battlefield.

Avoid awkward moments with this tip on getting lipstick off your collar. One of the nightmare scenarios for boyfriends to deal with, but if this happens just follow this videos advice on how to remove lipstick stains from clothes. Remove lipstick stains from clothes.

We love tearing apart security here at Null Byte. Several years back, upon returning items to Wal-Mart due to a malfunction, I noticed something very peculiar about the way their overall procedure goes. I brought the item up to the desk, and the woman asked if it didn't work, which I responded affirmatively. Without a moment's notice, she takes it right off to the defective items area and asks if I would like cash or store credit.

Rajo from the SubStream's "Film Lab" has some tips regarding sound recording. Not all microphones are created equal... some are small, some are big, but all have their advantages. Depending on the scenario, of course. There's the lavalier mic, and the handheld, and the shotgun mic. See how to record sound properly with the right microphone. Record sound properly with the right microphone.

Guiding internet users to useful content is one of the most lucrative businesses in the world. This process is called aggregation. Google and other search engines form the top of the food chain, aggregating all of the content on the web in response to queries. There are all sorts of other important aggregators though, and you probably use at least one every day: Fark and Reddit for web content, Rotten Tomatoes for movie reviews, and Metacritic for a variety of media, but most importantly, vid...

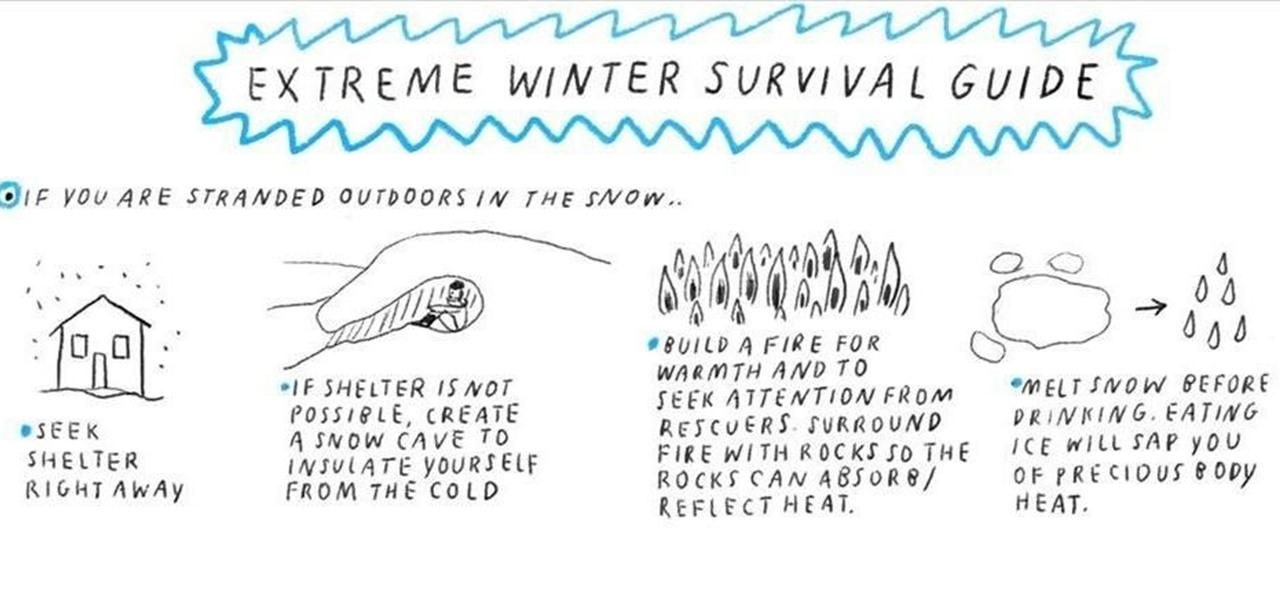
Whether it's a shark in the ocean, a crocodile in the swamp or a swarm of angry bees, trekking through the wilderness always comes with its fair share of perils. To prepare for the worst case scenario, equip yourself with the right knowledge—then the worst that can happen to you is an awesome bar story when you tell your friends about your close encounter.

If you ever find yourself in the unfortunate predicament of being stranded outdoors in the snow, don't eat snow off the ground. Eating solid snow will sap your body of precious internal heat (since the heat will be used to melt the consumed ice), so it is best to melt the snow completely before drinking to stay hydrated.

Need to bike around in cold weather to get to places? Winterize your bike by adding plastic zip ties around your tires to add more traction when you are biking through ice and snow.

Just like it's hard to fall asleep when it's too hot in bed, it's difficult for some to fall asleep when it's really cold. Avoid this unpleasant scenario by investing in a heated mattress pad so that by the time you are ready to check out for bedtime, your bed and blankets are already toasty.

Admittedly, we've been quite hot on Kipkay lately, but can you blame us? This guy just keeps rolling out the wild inventions and bold pranks!

Penny pincher? A true believer in "waste not want not"? Then listen up—here's a quick tip that will save you some spare change.

By "God," I mean Morley Davidson, John Dethridge, Herbert Kociemba, Tomas Rokicki and about 35 CPU-years.

Yes, you read the title correctly. GameStop has problems, and if you're lax in morals, you can take advantage of them for free games and cash. I'm bringing you all yet another exclusive Null Byte that falls into the fascinating category of life hacking.

Associate editor Tom Skowronski of Videomaker demonstrates how to cut video transitions for action scenes. Create an illusion of continuity by keeping only key shots of continuous motion, while taking out aspects that slow the pacing of the video. Use the technique of 'cutting on the action' to transition from one video clip to another clip of the same action. Maintain screen direction between shots by making sure that any moving subject is always moving in the same direction on screen across...

Edit your photos with ease with Canon's free software, Digital Photo Professional (DPP). It's primarily for editing and processing Canon RAW files. See everything there is to know about this comprehensive photo editing software bundled with most of your Canon Digital SLR cameras.

There's no more exciting ways to fish for bass than top water. There's a big explosion with a bass hooked up. Wade Bourne, host of Wade's World on MyOutdoorTV, shows you how to use a follow-up lure when you've missed on a big bass.

The community tore up the first realistic mission last week. You've applied the techniques learned in the basic missions to a real scenario, so I'm pretty content. The realistic missions are where the learning gets intense and where we can apply real knowledge to extremely realistic situations. We will also be continuing the normal Python coding and hacking sessions. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, f...

Having bills to pay is one of the worst parts of life, especially around the holidays. And if you're extremely unlucky, you might also have to pay some hefty medical bills. This can put a heavy damper on plans, wants and needs. What's worse? The people that you owe money to are pushy and always bother you to pay in a more timely fashion, or worse, pay bigger premiums.

Most indie game developers will never see a million dollars in their bank accounts, and I certainly doubt that Eul, the anonymous developer responsible for the original version of Defense of the Ancients (DotA), expected to. But now even the fans can earn a little green. Some lucky and talented DotA players are about to win $1,000,000 for playing the unreleased sequel to the free unsupported Warcraft III mod from 2003.

Each aspirant nursing assistant is require to obtain CNA certification for their work employment. Thus, passing the CNA state exam is highly recommended. Usually the CNA testing process has two types of test - written and clinical exam. The most difficult yet challenging part of CNA test is the skill exam.