The rumors have been circulating for months, but now there's a source attached to the notion that Magic Leap is looking to sell itself off after a rough couple of years following the launch of its Magic Leap 1 augmented reality device.

Picture it: you wake up in the middle of the night and check your phone. Maybe you want to check the time (your phone is your alarm clock, after all) or see if that person ever replied to your message. You double-tap or lift to wake it, and the screen lights up. You flinch at the bright light, squeezing your eyes shut. It takes a few moments to adjust, even if your screen's brightness is as low as possible.

Do you see a red door and wonder if it might be a good idea to paint it black? You could "ask Ask Sherwin-Williams," or, better yet, you could just ask the new augmented reality features in the retailer's mobile app.

If you've been paying attention, you already know that ARKit can detect horizontal surfaces and estimate ambient light, but did you know that it can also help you improve your soccer game?

Android Oreo may not be the flashiest release, but it's got tons of under-the-hood changes. We recently discovered documentation in the AOSP source code that outlines one of these understated features, which has been dubbed "Rescue Party."

Adidas' new app All Day isn't going to be your average fitness app. Oh no, the company had the "versatile athlete" in mind when it came to creating the well-rounded program that not only encompasses fitness, but also provides nutrition plans, encourages a balanced mindset, and makes sure you get an adequate amount of rest.

The conversation around augmented reality has largely been focused on apps and gaming, and how AR can be used as a marketing tool. However, a new exhibit at France's Scène Nationale Albi is using AR for more artistic expression.

The next generation in mobile communications has officially arrived. A new "Universal Profile" was just published to help carriers and OEMs enable Rich Communication Services (RCS) on any of their smartphones, and the standard hopes to replace SMS with a feature-rich, iMessage-like experience on all phones.

The headsets of tomorrow offer some amazing possibilities in both gaming and work, but what we've seen so far only begins to scratch the surface. The US Navy saw the potential to use augmented reality in a helmet to provide divers with an incredible amount of information we have so far only seen in Hollywood movies.

The Unicode Consortium just unveiled 72 new emojis that will be included in the upcoming Unicode 9.0 release, but we're not here to talk about the winners. Instead, let's take a look at the five poor emojis that will have to wait until at least next year to join the Unicode roster.

Today I will show you how to make a metasploit exploit really quickly. This tutorial is mainly applied to stack based buffer overflows and seh buffer overflows exploits .There is a simple way for rop exploits too but I will dedicate a special tutorial on this subject.

There are two scenarios that absolutely suck when someone calls you. The first is when you accidentally pick up a call you seriously didn't want to take. Debt collectors (thanks college), crazy exes, or that one guy from work. And the other is when you miss a super important call and can't get a hold of them afterwards.

Bigger and faster. Two words that are pretty much always wanted no matter what the scenario is. The new PlayStation 4 has been out for only a few hours now and people are already looking for ways to one-up their friends and upgrade their already awesome systems.

Obviously, millionaires like me don't really have to worry about an empty wallet, but for the rest of you out there, having no cash when it comes time to paying a bill can be excruciatingly embarrassing.

In this Windows 8 Tutorial you will learn how to disable automatic maintenance. Their are really two situations I can think of when you would want to disable automatic maintenance in Windows 8. The first being if your Windows 8 computer came with a Solid State Disk then you will probably want to disable automatic maintenance. The reason being is that a solid state disk does no benefit from defrags and the automatic maintenance automatically defrags your hard drive and this will take away from...

So, you've finally managed to get addicted to one of those free farming games, like Farm Story or Tiny Village. You play the game nonstop now, and the only thing stopping you is that dreaded on-screen notice to come back in 23 hours to finish farming or building. Come back in 23 hours… WHAT?!? Most of these free games will start charging you at this point. Time becomes a luxury. Well, not anymore, thanks to XDA Developer StupidIdea, who made a time-tricking app called GMD Speed Time (that's t...

With the Samsung Galaxy S III being a hot commodity, it's no surprise that your friends might try unlocking your fancy password-protected phone. While some friends have good intentions when using your phone, there are those certain friends who get into the phone to do this... The worst scenario might be that you leave the phone around a group of friends, come back and find that all of your social media accounts have been hacked. When you yell out to your friends asking who did it, no one make...

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

Check out this video to learn the fundamentals of woodsball, a mission or scenario oriented type of paint ball. Positions are meticulously explained to help in deciding which player type best suits an individual.

This video shows how to be a more efficient sniper or back player in Woodsball, a scenario or mission oriented game of paintball. Counter sniper tactics are also explained for Woodsball enthusiasts.

A vulnerability in the design of LiDAR components in driverless cars is far worse than anything we've seen yet outside of the CAN bus sphere — with a potentially deadly consequence if exploited.

When the time comes to replace your car, you most likely have a checklist of criteria that you would like on the new one. Your car is possibly the most expensive possession you have—or the second-most expensive, after your home—so you want to make sure that you are not only getting what you want, but that you are getting the best deal possible.

Apple's MacBook line of laptops is quite famous for their extensive battery life, thanks to various technologies that Apple has utilized. However, all things must pass, and over time your MacBook's battery will degrade. Certain use scenarios can accelerate the degradation of the battery—from excessive usage to high temperatures to overloading the system—and this can all lead to the untimely obliteration of your battery.

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.
I see many people posting the same thing on the internet. "How do I become a hacker? Where do I commence?"

A landmark bill finally went into action this week that will allow American cellular customers to unlock their smartphones for free. The process of unlocking may vary between mobile service providers, but you can rest assured that you are now entitled, by law, to carrier-unlock your smartphone.

Welcome back, my nascent hackers! In previous tutorials for my Wi-Fi Hacking series, I have shown you how to crack WEP and WPA2 passwords, break a WPS PIN, and create Evil Twin and Rogue access points. In this continuation of the series, let's look at slightly different approach to attacking wireless.

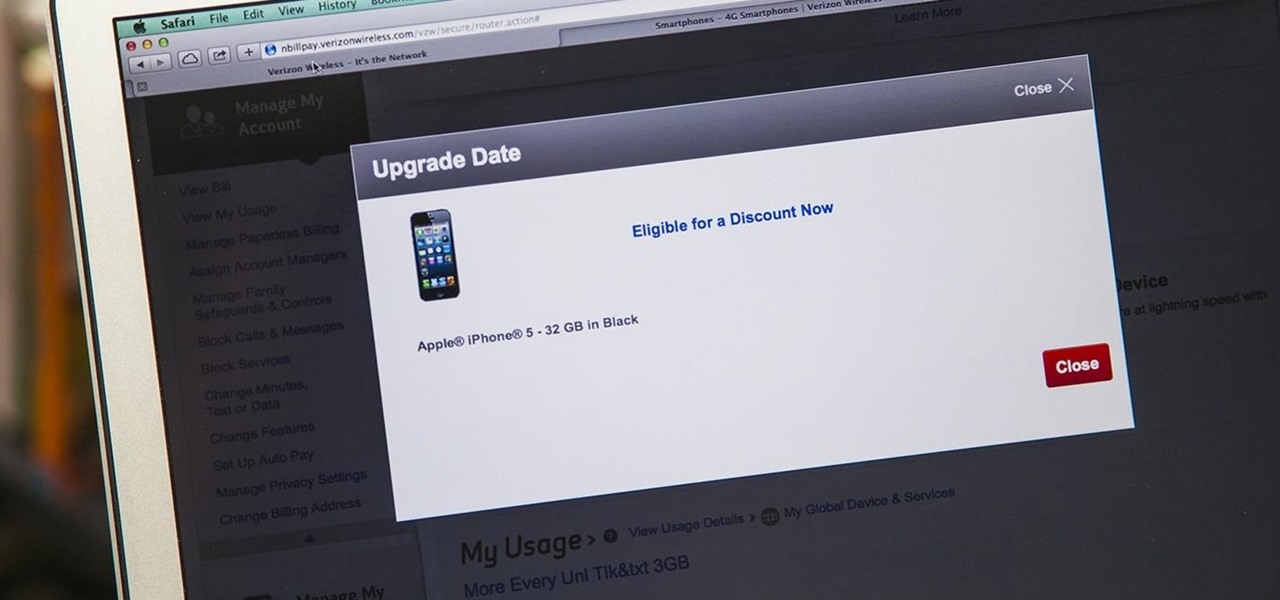
iPhone 6 pre-orders begin on September 12th, with the devices set for sale on the 19th. If you're ready to pick one up—no matter if you're a loyal iPhone user or an Android user about to make the switch—now is the time to check your upgrade eligibility.

Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what applications are installed and running.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

It's already easy, but we'll help you make it even easier. Watch this video for tips on getting guys to buy you drinks in a bar. If the guys are going to hit on you, might as well get some free drinks out of it.

There's an epidemic on the Internet, and the disease—Facebook. It's an addiction comparable to a hot cup of coffee in the morning or a soothing cigarette throughout the day—in worse case scenarios, a hit from the crack pipe. If you're on Facebook, you know what I'm talking about. You're addicted to finding out what's going on with your friends and addicted to telling those friends everything you're doing. You can't stop, even when you're at work.

Those of us who've taken the time to learn how to code are relatively well-suited for shakeups in the economy. Despite the recent and notable disruptions caused by the COVID-19 outbreak, demand for talented and trained programmers and developers is still high, and it will likely keep rising as companies in every industry adapt their business models to a more remote world.

The entire wireless industry is working overtime to convince the world that 5G, and the higher prices associated with the faster speeds it affords, will not only be worth it but will deliver never-before-seen wonders. But few companies have produced such a stunningly well-done sales job as Three, one of the leading wireless giants in the UK.

The HoloLens 2 hasn't even reached most of the market, but it's already a big-time TV star. Microsoft's augmented reality device made its primetime debut on FOX TV last night on an episode of the hospital drama The Resident.

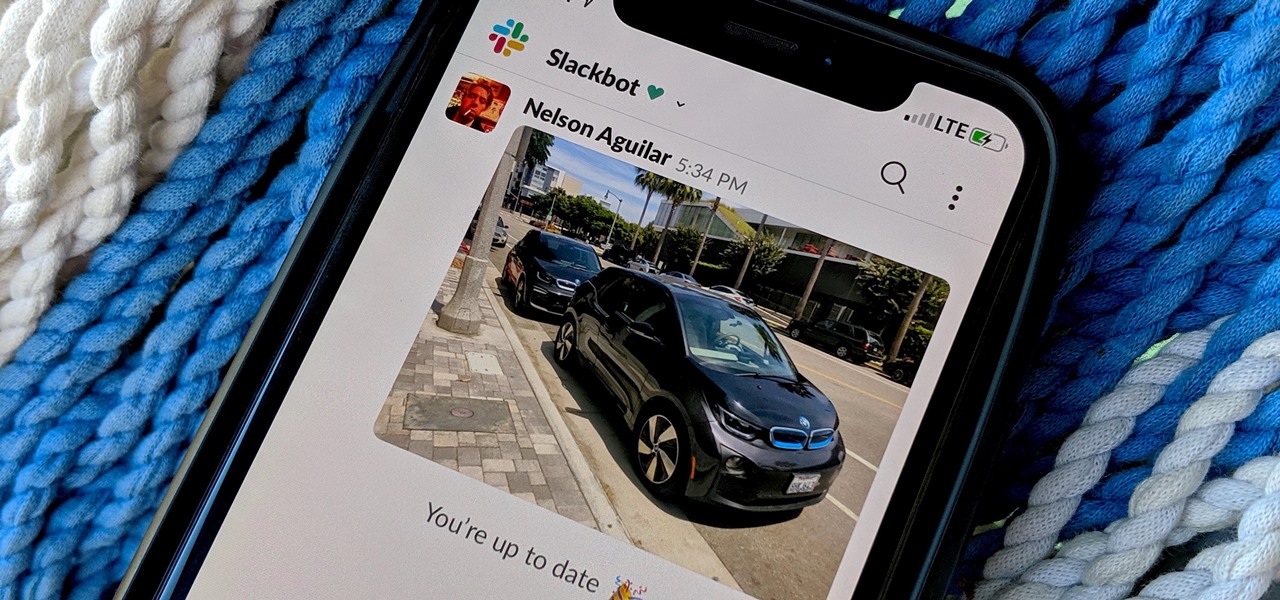
By default, Slack optimizes the images you upload and send to other users in your workspace. Although optimization lowers the resolution of the image, it does send quicker, which is better if your internet service is poor. However, you may want to send the highest-resolution image possible, so how do you stop Slack from sending only optimized and lower-quality photos?

One of the biggest advantages of the front-mounted ultrasonic fingerprint sensor found on the Galaxy S10 and S10+ is that you no longer have to physically pick up your device and reach around the back to unlock it. Instead, you simply place your finger on the screen for easier access and added convenience — at least on paper.

After entering the UK's version of bankruptcy last month, Blippar's assets are up for sale, and bidding ended today.

The Pixel 3 has an indisputably great camera, but a software update coming soon is going to make it even better. Google will be adding a "Night Sight" shooting mode that's so good with low-light situations that you'll have to see it to believe it.

Leading augmented reality headset makers Microsoft and Magic Leap are among the companies now vying for a military contract for battlefield heads-up displays.