Hand tracking technology company Leap Motion has built a stunningly fluid augmented reality ping-pong game that not only showcases the capabilities of its open source Project North Star augmented reality headset, but also demonstrates how artificial intelligence can elevate immersive experiences.

If two hands are better than one, then two hand-tracking SDKs must be better than one as well. After uSens announced its Hand Tracking SDK at the Augmented World Expo in Santa Clara on Thursday, ManoMotion unveiled the latest version of its own SDK. Both technologies give apps the ability to track hand gestures with just a smartphone camera.

Microsoft's Monday keynote introduced the fourth generation of the company's Kinect sensor during Build 2018 in Seattle.

Scavenging for weapons and supplies in PUBG adds to the element of excitement and dread of the unknown. But this feeling can quickly turn into annoyance as you attempt to swap your weapon for a better one on the ground, only to automatically pick up the gun you just dropped again.

Just days after announcing the launch of two new mixed reality studio facilities, Microsoft is extending its mixed reality reach even further with the announcement that the HoloLens will now be offered in 29 new markets.

At the Augmented World Expo Europe press conference in Munich today, RE'FLEKT will unveil the addition of remote video calling to their RE'FLEKT One enterprise augmented reality platform, in addition to ARKit and ARCore apps that demonstrate the platform's capabilities.

When you have minor software issues like an app crashing, restarting your iPhone would usually fix it. But Apple doesn't provide an official "Restart" or "Reboot" option (unless you count this bold text hack), so we typically have to power our devices off and on in these scenarios. Thankfully, there's a great Cydia tweak that lets you "respring" your device, which is even faster than restarting.

Waymo just received approval on a patent for a push-button console that replaces not only a steering wheel in a car but the brake and gas pedals, too. This reflects Alphabet's driverless arm could remain true to its original mantra of developing cars that pilot themselves without human intervention.

Global design and technology services company Tata Elxsi says it has licensed its advanced autonomous vehicle middleware platform "AUTONOMAI" to a "leading automotive OEM."

At the 2017 Augmented World Expo (AWE) in Santa Clara today, smartglasses maker Epson introduced two new augmented reality headsets from its Moverio line of products.

Google loves to play games. That's just what they did when they went ahead and teased us with a few Android O hints after Reddit user Zitroney unlocked an Easter egg in a Google Creative Lab developer's app ShortStories.

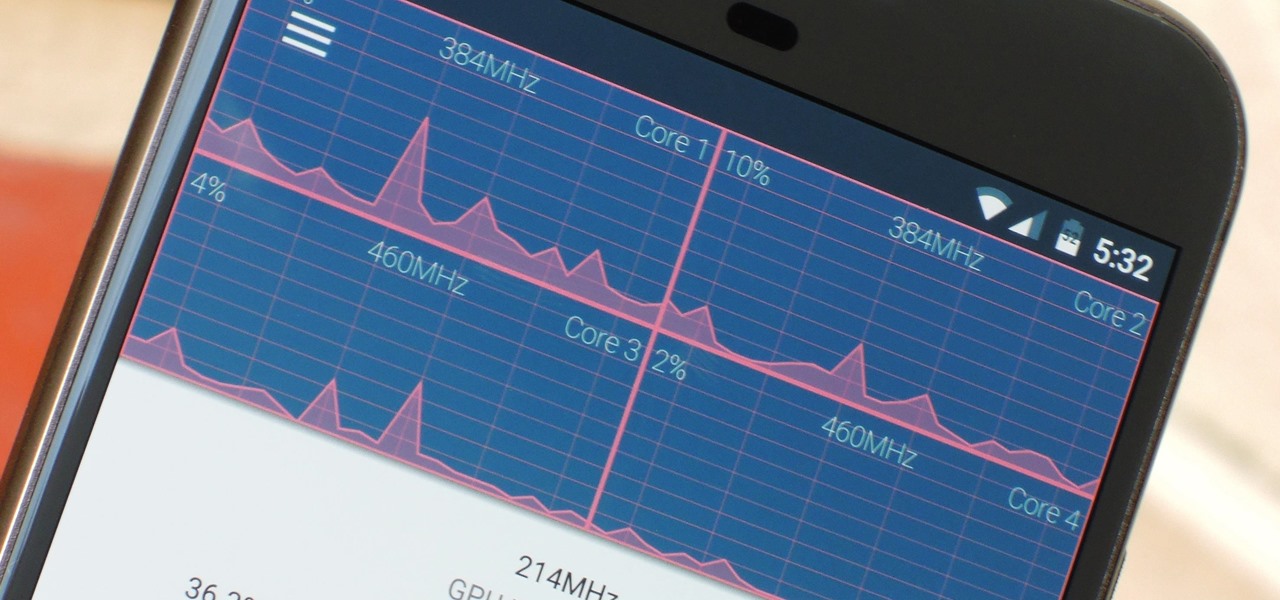
The Google Chrome browser does mostly everything well and integrates nicely with other Google services, but it's not exactly renowned for speed. With a rooted device and the aid of an app called Kernel Adiutor, however, you can make Chrome as nimble as some of the fastest browsers on the market.

While the numbers may not always seem to agree, the message remains the same: augmented reality is a growth segment. This week's edition of Market Reality starts with two new reports outlining the expected good fortunes for the industry and concludes with an example of a company capitalizing on their own growth.

Forget 3D movies. Warner Bros.' newest patent shows off designs for a mixed reality movie-going experience that will leave other theater-going experiences in the dust ... all in the comfort of your own home.

Unity 5.6 was just released on March 31, and it will be the last entry in the Unity 5 cycle. With all of the new features, it looks like Unity 5 is going out with a bang.

If you've ever built a piece of IKEA furniture, you're familiar with the confusion that some 2D instruction booklets can create. But neuroscience suggests that they're cognitively overloading, as our brains have to translate their basic flatness into physical reality and that's pretty hard to do. Fortunately, augmented reality has come to the rescue.

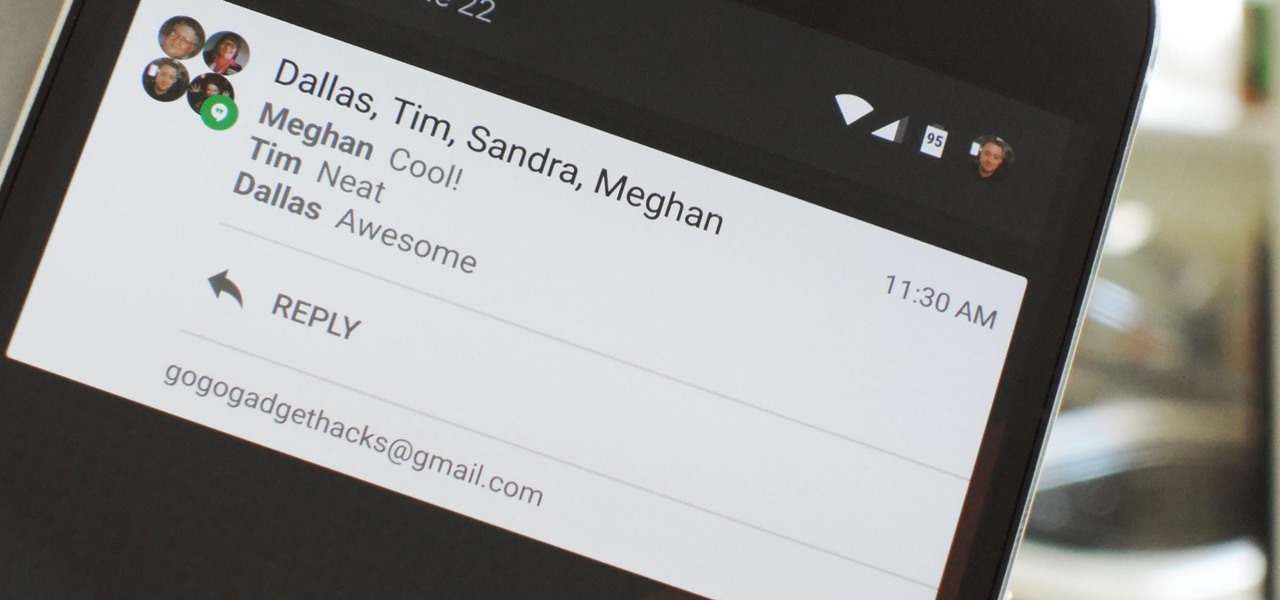
If you have any group chats going, you're surely familiar with this scenario: One person sends a picture, then, within 30 seconds or so, all other participants chime in with one-word responses like "Cute," or "Awesome." It's a social nicety, so you have to expect this behavior, but that doesn't make it any less annoying when your phone randomly beeps and vibrates ten times in a row because of it.

We're already glimpsing the future when we look at mixed reality through a headset, but is the real evolution of this technology something that will exist as part of our bodies? As intense as that may sound, TechCrunch's Jay Donovan offers compelling reasons why it's not such a crazy idea:

This is a familiar scenario: you light up the grill, get cooking, eat the fruits of your labor, then clean up every trace of your barbecuing once you're finished — except maybe the hot charcoal, which usually gets dumped right before the next cookout.

Apple's once flawless mobile operating system has seen its fair share of bugs recently. From Messages and Wi-Fi settings crashing to having your photos and contacts exposed, iOS has been standing on shaky ground for a while now.

Hello aspiring hackers, It's been a while since I wrote a tutorial, so I figured I might just share one of the tools that I have created to help the community grow.

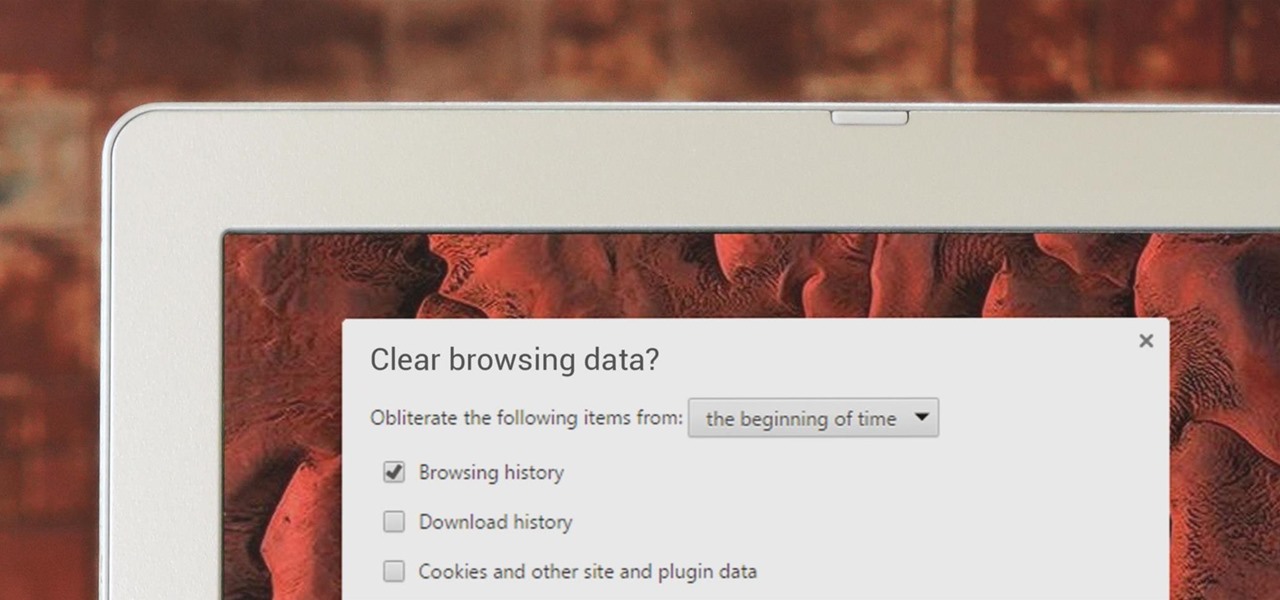
If you've been visiting websites of ill repute, or if you've been Christmas shopping and don't want to spoil the surprise, it would be a disastrous situation if anyone were to come across your browsing history. Visited sites, cookies, and cache can paint a very clear picture of your recent internet activity, and depending on the situation, you may only have a few seconds to delete your history before someone else barges in.

Your English teacher is a creep. The way he looks at your girlfriend, the way he always spends ages with the girls in the class going over their work but not the boys, just the way he is.

Hi Folks. This is my first post. I will teach how to create a server and client python reverse shell using sockets and python language. The script i'll post here is going to be very simple, and from here you'll have the possibility to adapt to your own purpose. For example, my original script can download files, upload files, make changes to registry, create user accounts and more. I'm sure you could do it on your own too.

You're smashing your keyboard to increase your screen brightness, yet it won't go any higher, but you know you've been able to set it higher before. Angered by this, you get up and move your laptop, only to suddenly notice that the display does in fact get a lot brighter.

Picture this scenario—you're using your phone in a dimly-lit room, then you move to an area with a lot more ambient light, and Auto Brightness kicks in within a few seconds to ramp up the backlight. That's the way it should be, right? But then you move back to the darker area, and your phone takes 30 seconds before it decides to dim back out. Pretty annoying, isn't it?

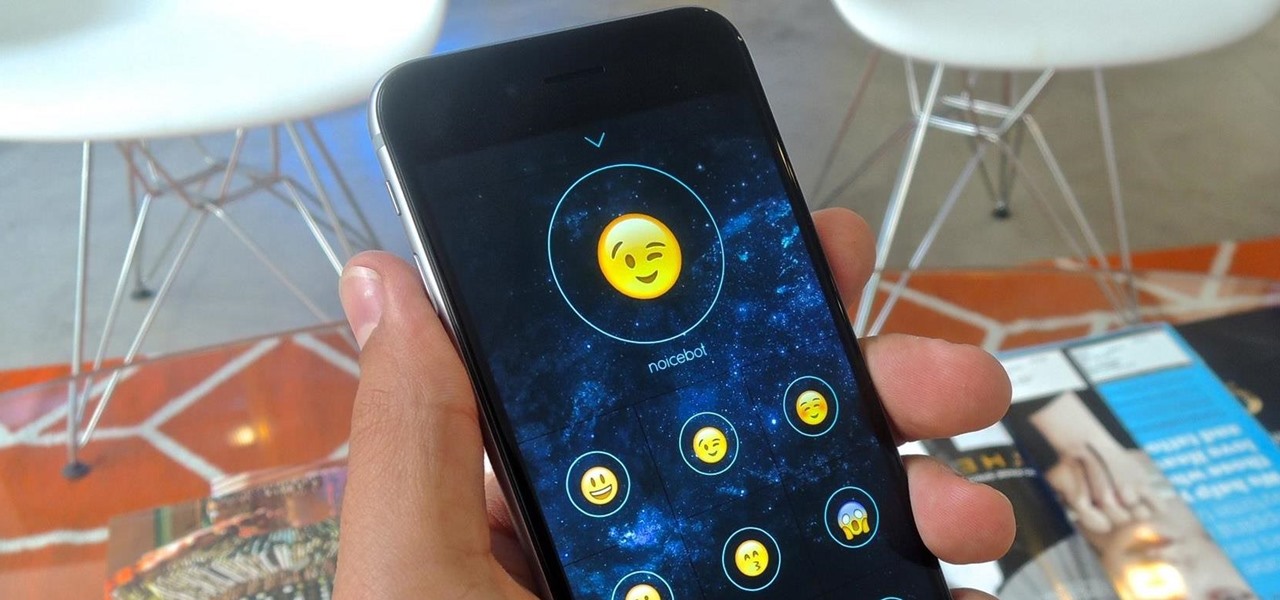
As messaging and texting have all but replaced the need to actually call someone, emojis have seemingly replaced our need to type out text. With a simple emoji, you can relay emotions like "I don't feel very well" or "I love you" quickly and easily, knowing that the other party will instantly know what you're feeling.

If you work at a large office or have a multi-story home, you're probably familiar with Wi-Fi range extenders. Since one hotspot isn't always enough to cover an entire area, Wi-Fi repeaters are generally set up in larger areas to capture and rebroadcast the original signal.

There are so many mods we can apply using a custom recovery. From themes to bug fixes and feature ports, a typical rooted user spends a decent chunk of time in TWRP Recovery.

Dianne Tice and Roy Baumeister gave a bunch of college students a questionnaire in which the students answered questions about their work habits. In a class which she taught, Tice also assigned a paper with a deadline which she said could be extended and observed which students availed themselves of the option to extend.

There is no better example of a risk-versus-reward scenario than jailbreaking your iPhone or rooting your Android phone. While both jailbreaking and rooting undoubtedly has its advantages, this possibility of something going wrong and you ending up with a 500-dollar doorstop is never too far out of mind.

The next time a light bulb burns out in your house, don't throw it out. Believe it or not, burned out light bulbs aren't entirely useless. Besides creating an extra task on your to-do list, they can be hollowed out and used for a variety of different things from home decorations to miniature indoor gardens.

Considering how often many of us fly on commercial airlines, the idea that a hacker could somehow interfere with the plane is a very scary thought. It doesn't help to learn that at Defcon, a researcher found that the Automatic Dependent Surveillance Broadcast (ADS-B), transmissions that planes use to communicate with airport towers are both unencrypted and unauthenticated.

Beat the Clock is a great wrestling drill. Learn from a wrestling coach how this drill can improve wrestling skills in this video tutorial.

The breaststroke is a great swimming stroke for beginners. Many swimmers prefer the breaststroke over other swimming strokes. Get expert tips and advice in this swimming video tutorial.

We've been so worried about volumetric scans possibly robbing celebrities and performers of their agency and right to control their image that, somewhere along the way, we forgot that scans may not always be necessary to produce passable holographic performances.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

Recently, iPhone users have been bragging that they can set Live Photos as their lock screen wallpaper. While this is a great way to spice up a boring lock screen, Android users shouldn't feel left out in the cold. The highly customizable and feature-rich OS has a few tricks up its sleeve too, and it's really easy to set any GIF as your Android's home screen and/or lock screen background.