You don't have to be Drake to realize that some friends are better than others. There are friends you know are only there for the party, and friends who actually listen when you whine about your life. There are friends you go out with for a beer, and friends you call when you're drunk and need a lift at 4am.

You jump in your car and notice that is feels like it is slipping out of gear or shifting in and out of neutral. What could the problem be? One problem may be that the transmission fluid and filter need to be changed.

For most people, the battery life on a DSLR is more than sufficient, but if you want to do a really long exposure or time-lapse, one charge might not last long enough to get the shot you want. You can always connect it to an extension cord to charge while you shoot, but that can be really annoying to work around.
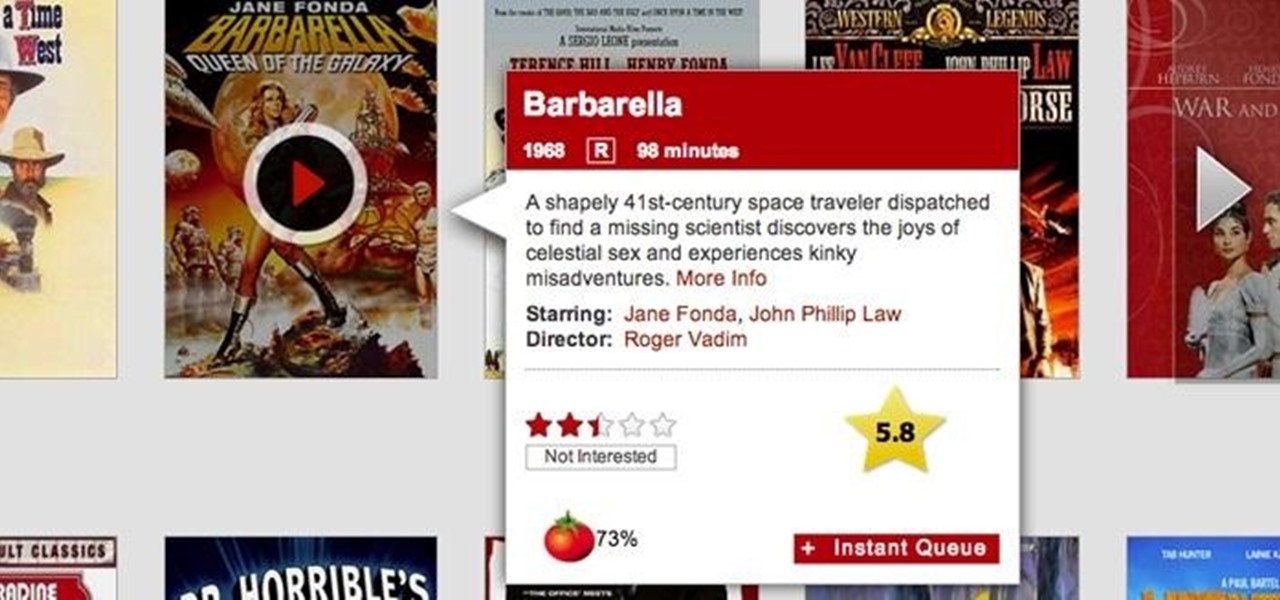
I like to call Netflix my quiet, digital friend. She's been there for me on many many occasions—from when I had to move home for a few months, to when the cable was down for days.

Streaming video has definitely changed how we watch movies and television shows, but with the constantly growing number of services out there, it can be hard to keep track of who's got what. Who's got Disney now? Starz? Netflix? Who knows. And when you add sites that let you rent or purchase titles, you could spend all evening trying to find something to watch. Here to simplify the process is a service called Can I Stream It?, which lets you search for your favorite movies and TV shows to fin...

For the most part, keyboard shortcuts are great. They save you some time and make it easier to do everything right from the push of a button. But like most things in life, there is always a caveat, and in this case, for me—it's a huge one.

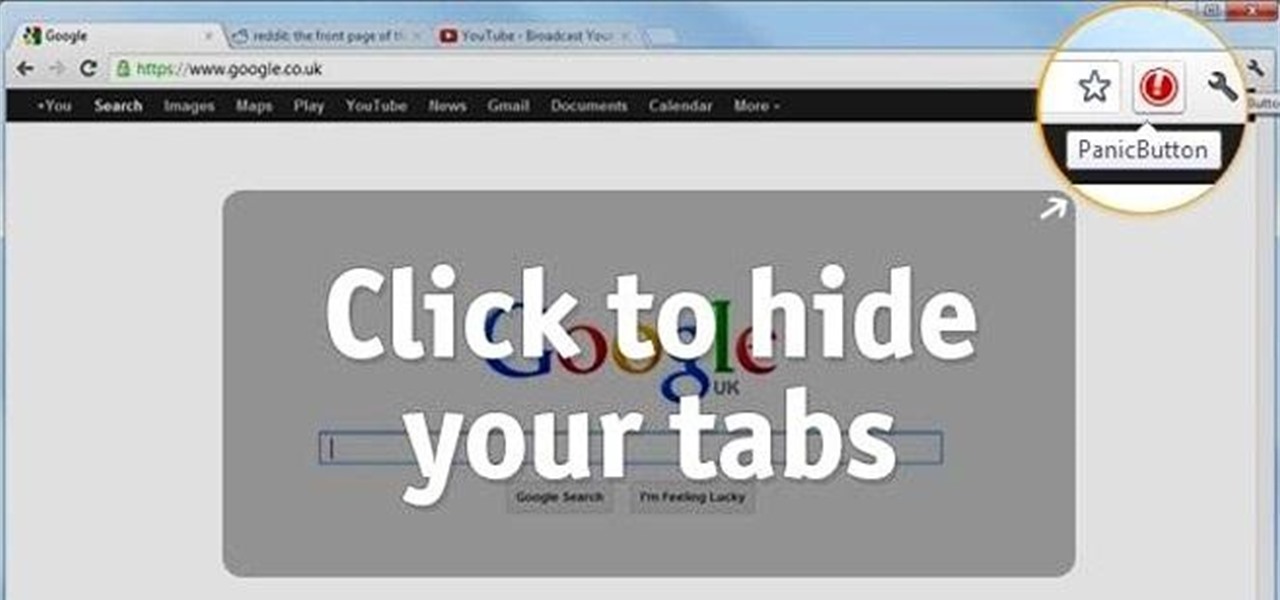
At some point or another, we've all been in that awful situation when someone walks up behind you while you're looking at something you don't want them to see. Whether you're tweeting during class, shopping for gifts online, or looking at something a little more NSFW, there are times when it would be nice to just click a button and have all your open tabs disappear.

The reason that Facebook is so popular is because it connects us to people that we could have never been connected to before. When people log on, they look for messages, comments, likes, and any other notifications that connect us to those people. These same notifications, though, distort our view of Facebook. We tend to appreciate statuses (I prefer stati) that have more likes. We're geared towards people that have more friends, so we tend to like pages that already have hundred of thousands...

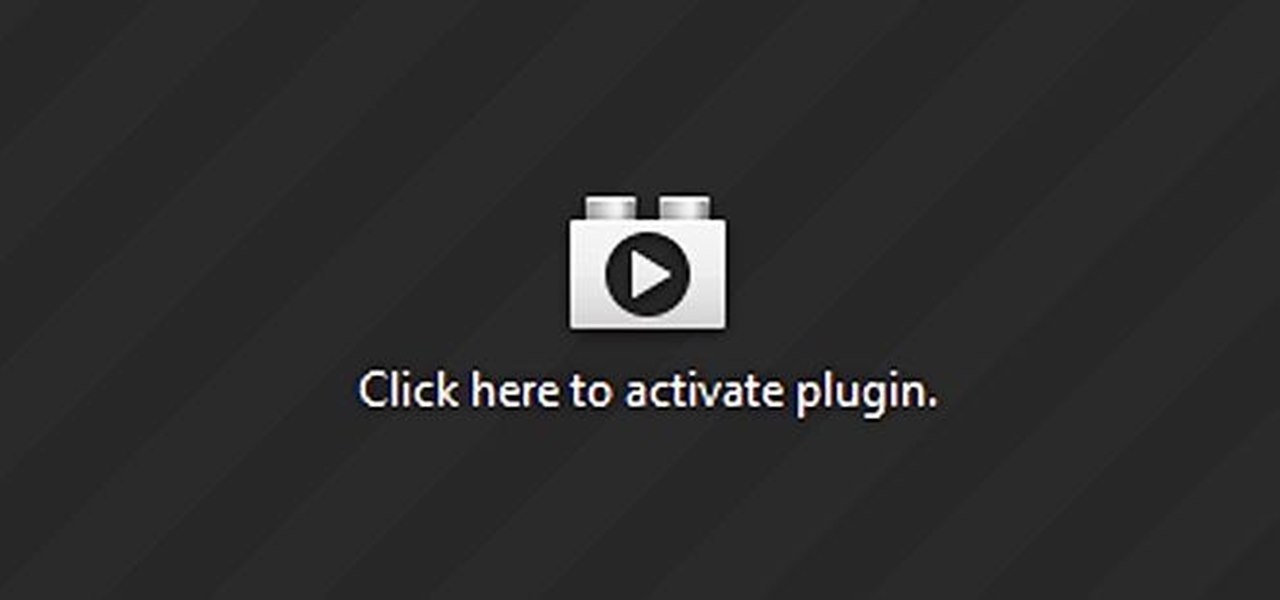
When you're at work or in class, there's nothing more annoying than sites that automatically play media. One minute you're happily distracting yourself, and the next, you're scrambling to hit pause while everyone stares at you. Not to mention now your boss knows you're slacking off.

The mighty Arduino microcontroller can be used to show children how robots work, it can be used to hack into hotel rooms, or it can be used to let you know when you've got a new job opportunity!

It's already August, which means school will be back in just a few short weeks. If you're getting ready to start or go back to college, that means you'll probably be dropping a few hundred bucks on textbooks. Here are some of the best places online to buy, sell and rent textbooks so that you can get back to more important things, like making your papers look longer than they really are and getting around your school's website blockers. Plus you can spend your money on more exciting things, li...

If you use Ubisoft's uPlay browser extension, you should probably get rid of it right now. An Information Security Engineer at Google discovered that the plugin has a hole in it that allows programs to be installed through uPlay, essentially letting anyone who feels so inclined to take over your computer. How the Exploit Works

Removing the gunk from a gutter but with proper methodically will ensure a clean job and keep you safe while doing activity on top of a ladder. Don’t let this chore get you down, with a little work you’ll have free flowing gutters all season.

In this video tutorial, viewers learn how to install and use Ad Block Plus in Mozilla Firefox. Begin by clicking on Tools and select Add-on. Then click on Get Add on and search for the extension in the search box. Now install the add on and restart the browser. Users will be able to selectively block out text ads or even just elements of web page that is not wanted to be seen. This video will benefit those viewers who use the Mozilla Firefox web browser, and would like to learn how to install...

If you are looking to improve your piano technique then this how to video is the place to start. You will learn how to strengthen your fourth and fifth fingers with this easy piano exercise. The fourth and fifth fingers are often the weakest fingers when playing piano. You must learn to strengthen then so you can play piano better. This exercise also improves the extension between the ring finger and the pinky finger. This is a great exercise for beginner to advanced students. With this tutor...

Movie star hair is all about combining healthy hair with haircare products that contain silicone chemicals. Learn about using hair extensions, curling irons and haircare products to get movie star hair in this free video on haircare from an experienced hairdresser.

A high jump layout technique practice, learn how to do the back somersault in this demonstrational video. This exercise trains special awareness and body shape for the Frosby flop. This essential training for good hip extension.

Make sure your electronics gear stays in order! And make sure your running wires are safe. Check out this video tutorial from the Good Idea Guys at Good Buy Guys to learn how to tape down a cable correctly. Keep those microphone cables, audio cables, and extension cords secure and safely underfoot. Tape Tex shows you how in "How to Tape Down a Cable". A great helpful tip for cable safety.

Check out this video tutorial to see how to remove and install a rear sway bar on a Honda Civic EP3 (SI or SIR). This may be the same on other vehicles.

To some, SCRABBLE is just a board game to play during family game night or during a casual get-together. Others think of SCRABBLE as a mere hobby. But with any activity, there will always be fanatics—the ones who would rather sell their soul than stop—the ones with a constant yearning for self-improvement—the merciless.

For the last three years, Apple has hosted its Worldwide Developers Conference at the San Jose Convention Center, but thanks to the COVID-19 pandemic, WWDC 2020 is now an online-only event. So what can you expect from the new virtual format and when and how can you watch the keynote and developer sessions?

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

In a surprise twist, Apple released iOS 12 public beta 8 to software testers on Thursday, Aug. 23, right alongside iOS 12 dev beta 10. The release comes as a bit of a shock, as the company released iOS 12 public beta 7 just three days earlier. The official build of iOS 12 now feels closer every day.

In our last ARKit tutorial, we learned how to measure the sizes of horizontal planes. It was a helpful entryway into the arena of determining spatial relationships with real world spaces versus virtual objects and experiences.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

I've been an iPhone user in the iOS ecosystem for years now after a brief stint in the Android realm. But, I'm also enthusiastic about varying forms of technology in general; I realize that iOS is far from perfect and that healthy market competition is beneficial for all. So, naturally being curious about other platforms, I decided to take Windows Phone for an extended trial run.

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

As one of the most powerful Android apps for connecting your phone or tablet to your other devices in various ways, Pushbullet had always been a fan—and Gadget Hacks—favorite.

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

So this is my methodology for this project of writing a rootkit. Please leave feedback on what is right/wrong. I tried to simplify concepts the best I could however...

In 1987, two brothers, Thomas and John Kroll, began work on an image editing software, which was eventually acquired in 1988 and released to the world in 1990 by Adobe. That software was Photoshop 1.0, initially exclusive for the Macintosh platform. Over the years, Photoshop became a great wizard of image editing and gained application rockstar status.

Like the majestic mountain structure it's named after, Apple's latest version of OS X, El Capitan, goes a little deeper to expand on the foundation laid by Yosemite. While the update may not be as monumental as some have hoped, it is an improvement and includes tons of useful new features you don't want to miss.

hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack.

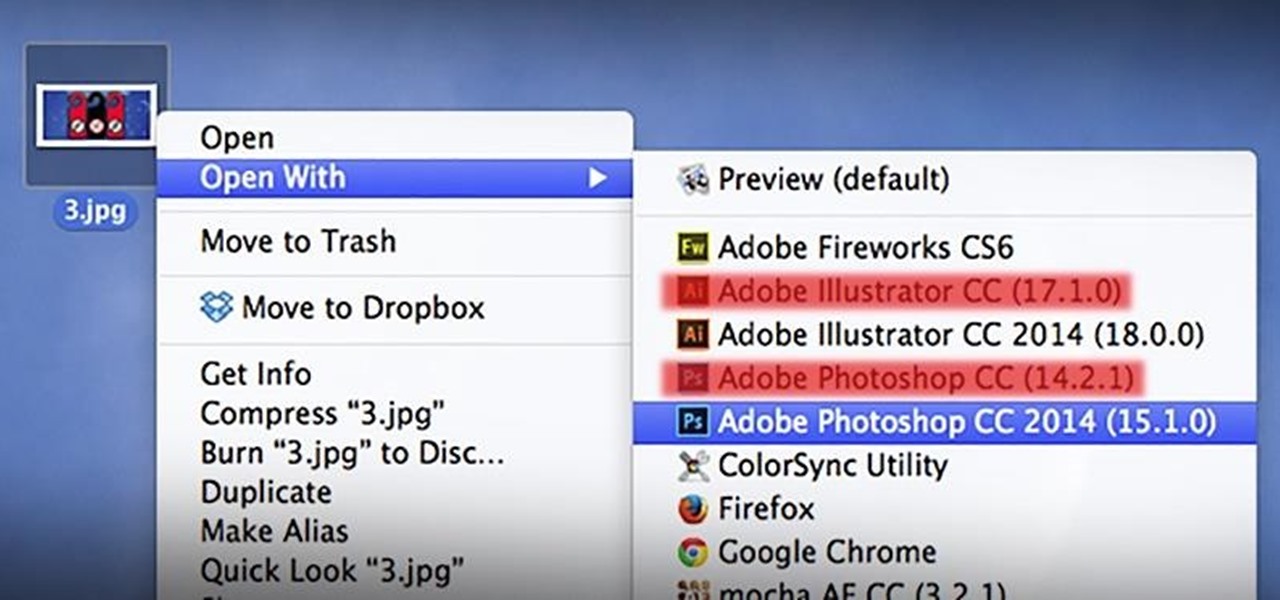
As a regular Mac OS X user, I have a love/hate relationship with the "Open With" contextual menu. Sometimes, it has just what I need. Other times, it's often packed with unnecessary or duplicate items, or missing the app I want to open the file up with the most.