
How To: Crack MD5 Hashes with All of Kali Linux's Default Wordlists
Hello, multicolored-hat hackers!


Hello, multicolored-hat hackers!

Malware often disguises itself inside of seemingly non-malicious files, such as installer packages, where it can then gain root access to your computer to track activity or steal your information.

Do you have a major mosquito problem? Well, here's a solution used by the military to drastically cut down their numbers.

Managing files can be time consuming on your Mac, for the simple reason that keyboard shortcuts and right-clicks sometimes lack the effectiveness we need. But with a simple third-part app, you can expedite the process of sharing, moving, deleting, and overall managing files on your computer.
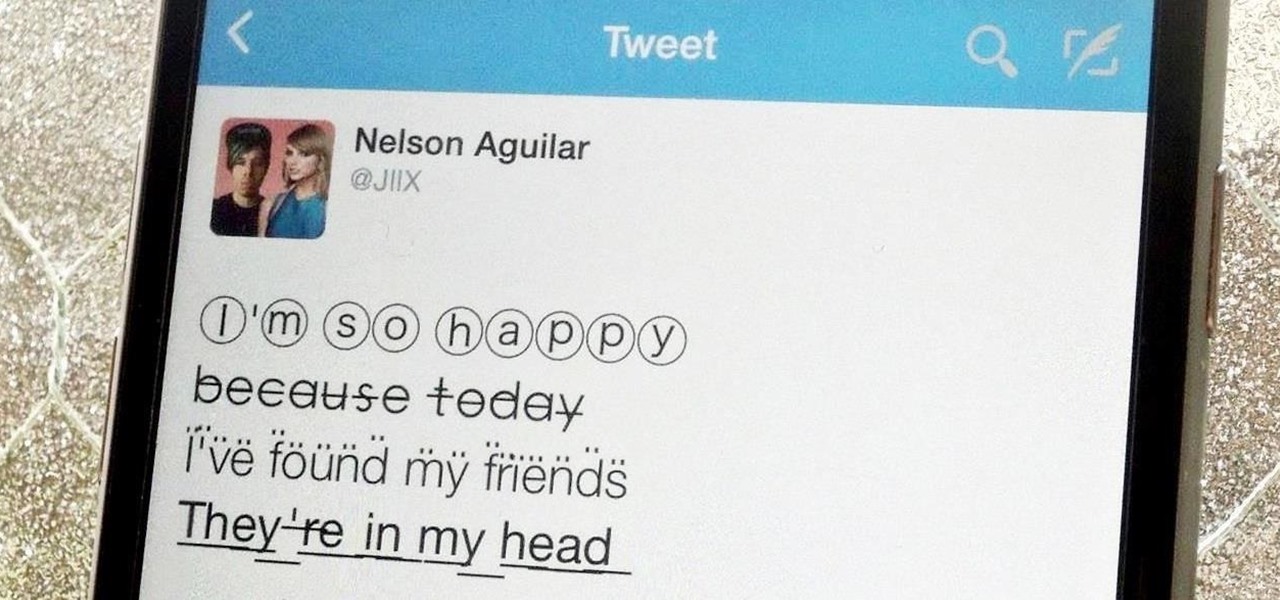
Aside from media, there's not a whole lot you can do in 140 characters to make your tweets stand out. You can use emojis, but they aren't exactly ground-breaking. However, now you can use Bedazzle, a Chrome extension from Gordon Zheng that'll allow you to add "rich text" to your tweets.
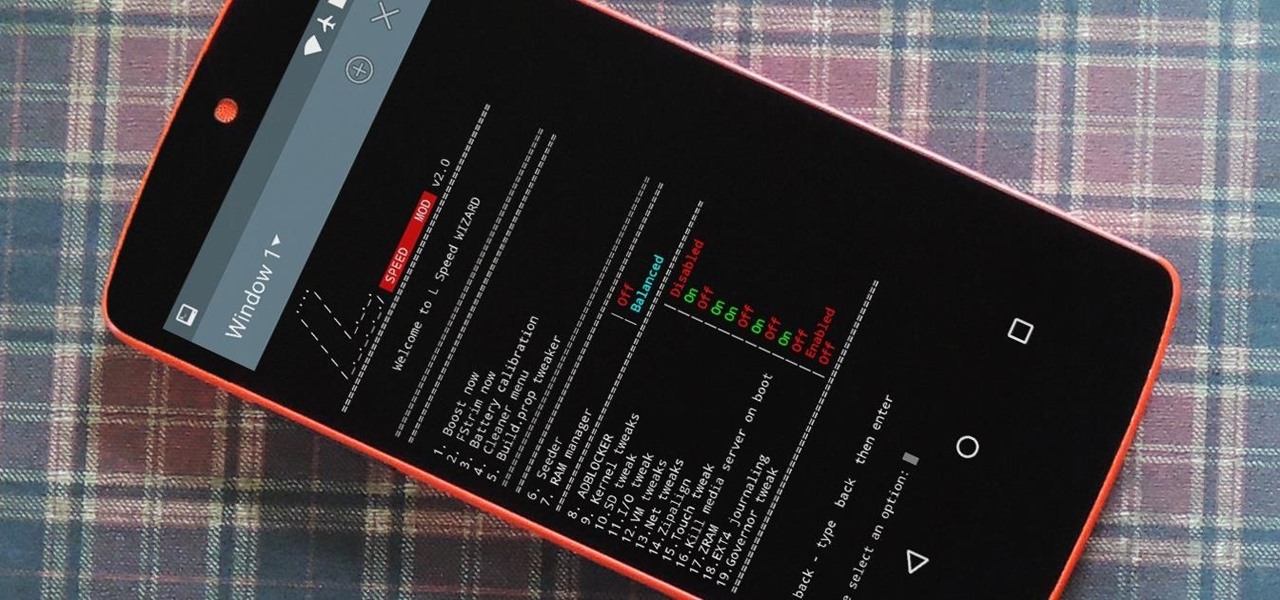
Performance boosters generally get a bad rap, but that doesn't mean they should all be dismissed—particularly when they're as well thought out as the latest work from developer Danijel Markov. After recognizing a few inefficiencies in the way Android handles memory management and other system-level functions, he created a flashable ZIP that will apply many fixes in one fell swoop.
Hi there, Crackers, Welcome to my 7th post (Part-1), this tutorial will explain about the basics of Batch Scripting.

Hi nullbytes! I've been recently reading the whole Linux Basics for the Aspiring Hacker series and felt like it was missing some stuff I know, so I felt like sharing it with anyone who might find it useful too.

Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.

Sit back grad some popcorn and learn how to remove the drain stopper, or plunger from your bathtub, so that you can replace it, or remove a hair clog.

UPDATE NOVEMBER 2015: The root process has changed for the Nexus Player now that the device is running Android 6.0 Marhsmallow. I've updated this article with detailed instructions on the new root process, but the video below still depicts the old process for Android Lollipop.

When streaming services like Spotify or Pandora compete for customers, the main differentiating factor is the size of their libraries. While these and comparable services usually run somewhere around $10 per month, a completely free alternative may actually have the most expansive library out there.

If you're a fan of Thai food, I'm sure you're familiar with sticky rice. There is something so special about its chewy texture and sweet flavor. If you have a desire to make it in your own kitchen but don't have the proper tools such as a traditional bamboo basket or stackable steamer, there are several other methods that work just as well. Once you try these alternative methods, I'm sure you'll be "sticking" to them for a while. What Makes Sticky Rice So Sticky?
A FGPA is chip that is programmable with the computer to create circuit. It is a totally different type of programmable board compared to an Arduino for example. The Arduino will follow lines of codes to generate the necessary outputs. A FPGA won't however read lines of code, but it is a circuit itself. When the chip is programmed, a series of AND-ports, OR-ports and many others ports are linked together. The FGPA will increase the speed and the possibilities of your designs! I assume that by...

Whether you choose to hang an authentic or artificial pine Christmas wreath on your door — or an entirely different type, like ones made of paper waste or even food — chances are you've spent a year or two struggling with how to keep your decor hanging. With one easy to apply, quick to remove trick, you can skip the shiny wreath holder and any further damage to your front door.

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.
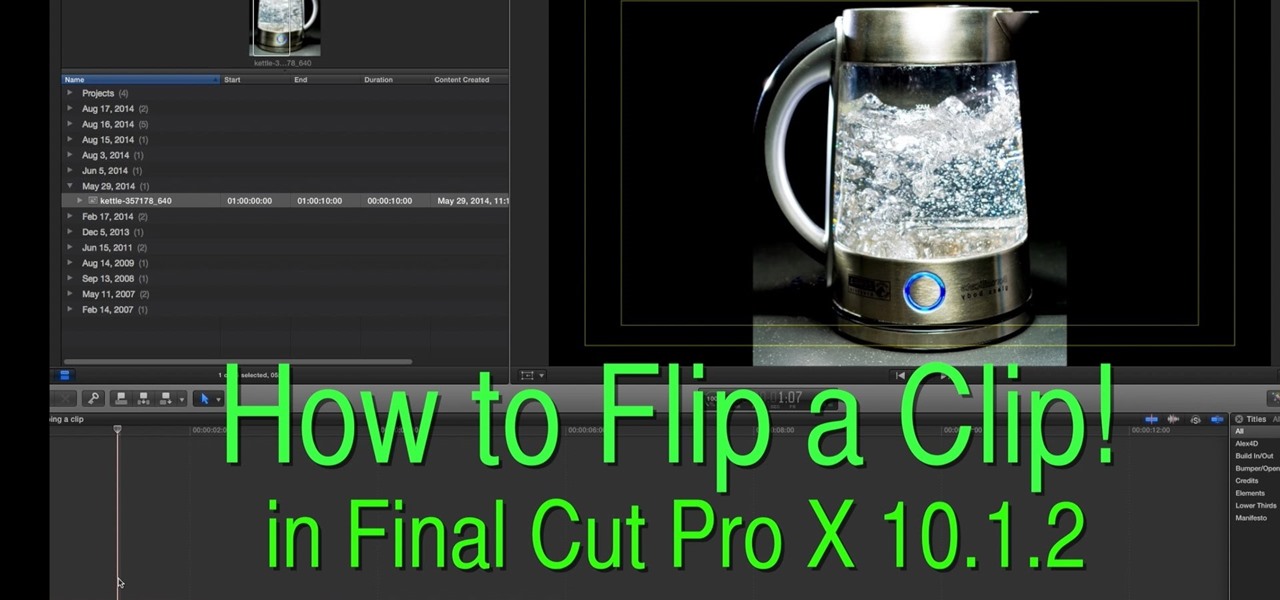
This is a great how to for all users in Final Cut Pro X 10.1.2 Video: .

Losing important data is the modern-day equivalent of misplacing your wallet or keys. We have tons of vital information stored in our digital worlds, and losing any of it can be devastating. But if you've accidentally deleted something important from your Android device, there's still hope.

Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.

There is finally a keyboard for smartwatches that would make James Bond proud, thanks to Minuum Keyboard.

Most variants of the Galaxy S5 come with the gesture-based Swype keyboard preinstalled. If you're into gesture typing, you probably already switched to this input method from the default Samsung keyboard (whose gesture service is nice, but it's no Swype).

Tequila is a hard liquor that's often been misunderstood. Produced from the agave plant, this aged spirit has complex flavors that bloom the longer it's aged and can rival the finest scotch.

To-do list and reminder apps are a dime a dozen on Google Play, so trying to find the right one for you could take hours as you sift through hundreds of similar apps and widgets. Well, search no more, as we've found one of the most well-designed and easy-to-use reminder apps out there.

Many of the beauty products you buy at drug and department stores are loaded with potentially toxic ingredients like parabens, while their active ingredients are made of things like glycolic, lactic, malic, and alpha hydroxy acids and retinoids, which are all derived from foods.

I'll freely admit that I'm a SwiftKey diehard. I've used the keyboard since its inception in 2010, and it was one of the first apps I ever paid for back in the days of my beloved Sprint Evo 4G. Since then, I've kept up with all its beta iterations, and have unabashedly installed it on various friend's devices.
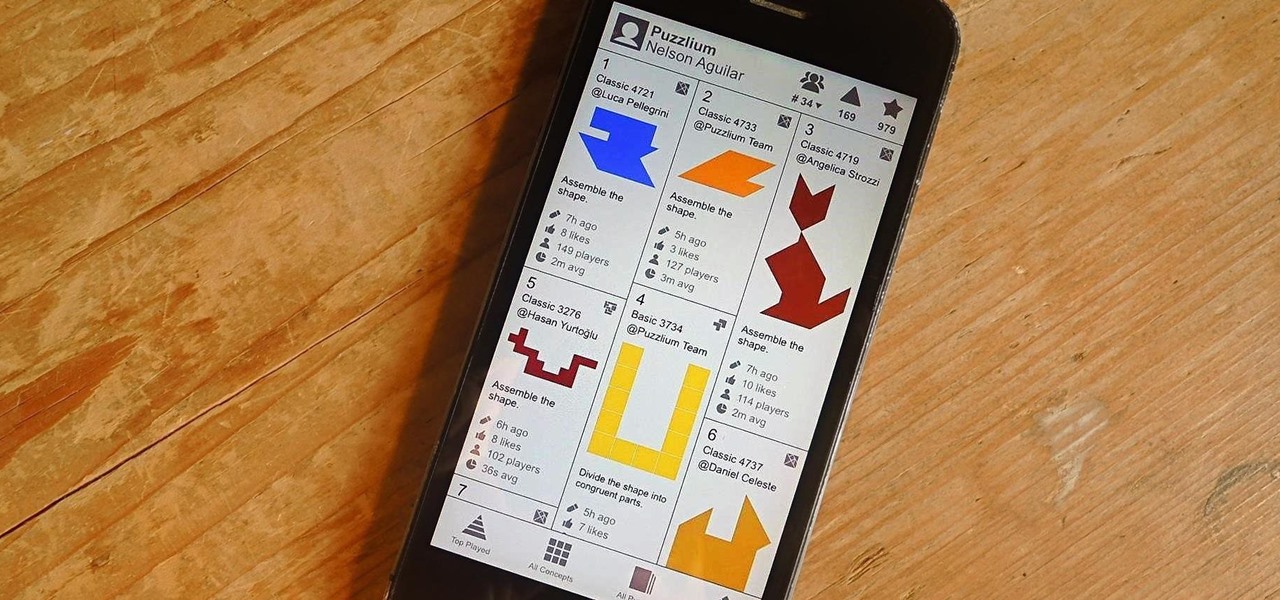
There is no shortage of games for your iPhone, and I'm sure you and your friends are probably sick to death of playing Candy Crush Saga by now. To spice things up, instead of waiting for cool new addicting games to come out, take control and make your own, then share them with your friends.

As with most OEMs, HTC would like you to think that you can do virtually anything with your new HTC One M8, but as a softModder, you know that isn't true. To actually unleash the full potential of that device, you need access to the whole system, not just the parts that HTC deems okay for you to mess with.

As Microsoft unveiled their new Windows Phone 8.1 software update yesterday, undoubtedly the most memorable takeaway was their showcase of Cortana. Competing directly against Apple's Siri and Google's Now, Cortana is Microsoft's entry into the digital voice assistant fray, and the official replacement to their search app.

Whether you've been fully converted or just want a little Apple with your Android, adding your iCloud email to your Galaxy Note 3 is a fairly simple task. Usually, Apple and Android don't play nice, but your iCloud address can be added to your stock email app just like any other email account.
What is Programming? Why need to learn? How to get started? Which language to choose? While surfing web, you must be encountering various softwares, games, etc. and might be thinking to make one, but don't know where to start. Here, I am starting series in Programming.
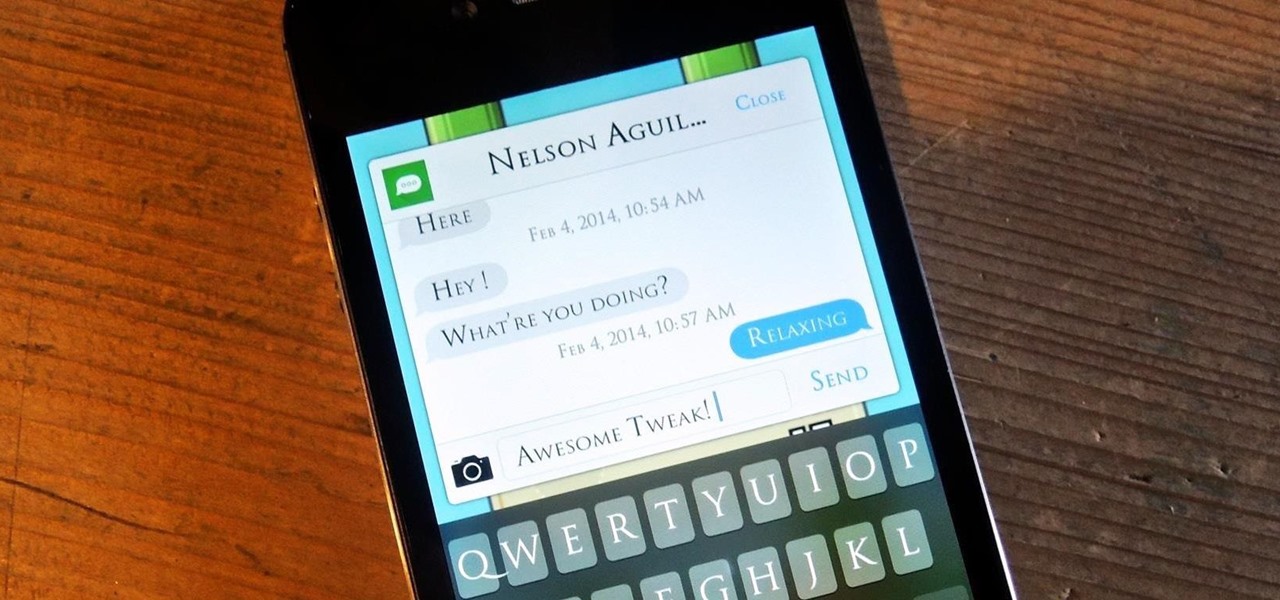
Texting can be difficult sometimes. When you're browsing the web or playing a game on your iPhone and need to respond to text message real quick, you have to exit your current app to do so. Not exactly efficient, especially if a quick "K" is all you need to say.
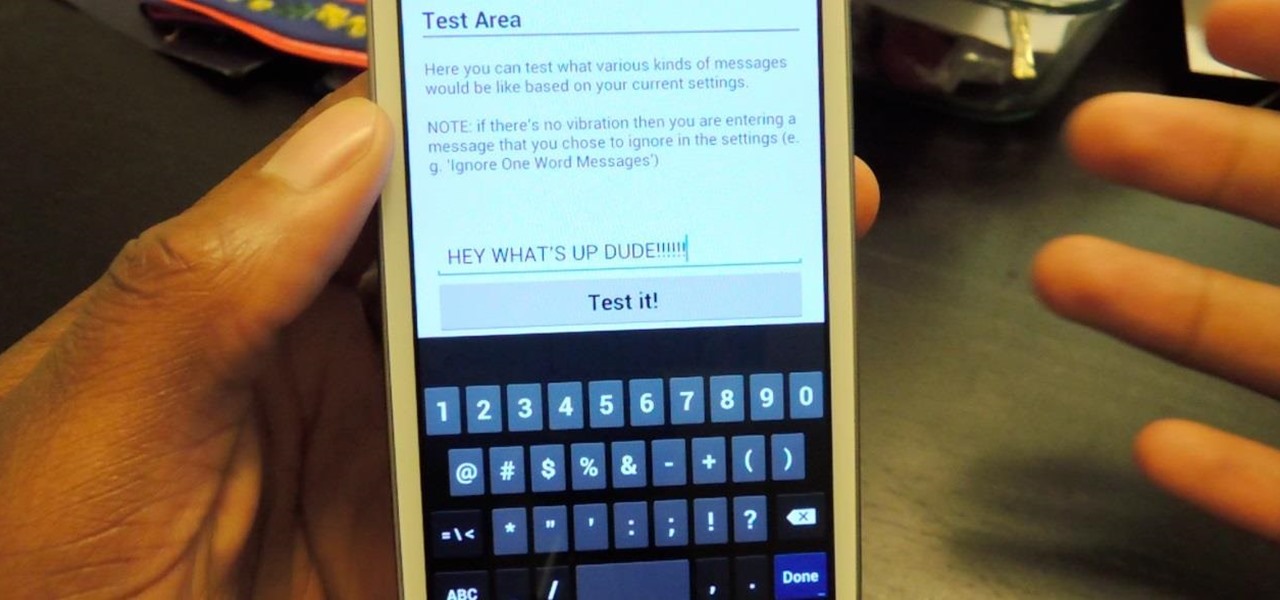
The constant stream of beeps and the buzzes coming from your Samsung Galaxy S3 can soon begin to fade into the background and remain forgotten. With smartphones vibrating for email alerts, Candy Crush notifications, phone calls, and text messages it can become difficult to tell which alert is which.

The holiday season wouldn't be the same without decorations. Ornaments and fancy lighting brightens up a neighborhood and helps spread the holiday cheer. While decorations and Christmas lights are fantastic, why not get a little more creative and some fun in the process?

Using fresh herbs can make a huge difference in almost any dish, but they're not always available everywhere. Depending on where you live, you can't always get them during the colder months. Personally, the problem I run into the most is not being able to use fresh herbs before they go bad.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.

Welcome back, my fledgling hackers! In the first part of my series on Wi-Fi hacking, we discussed the basic terms and technologies associated with Wi-Fi. Now that you have a firm grip on what Wi-Fi is exactly and how it works, we can start diving into more advance topics on how to hack Wi-Fi.

Welcome, my neophyte hackers!