Apple has released the 2nd beta of iOS 8, exactly fifteen days after the first version was unveiled at WWDC and subsequently released to developers. I've already shown you some of the new features of iOS 8, like location-based app alerts, randomized MAC addresses, hidden Safari tricks, and a slew of new things in the Messages app. But if you've had the chance the explore iOS 8, let's go through some of the changes that Apple has made to the latest iteration of its mobile operating system.

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography.

Ever since the much-lauded effects of the Mediterranean diet became widely known, people have been buying olive oil by the gallon. A diet that prevents heart disease, is based on fresh, seasonal foods, and includes a tasty as hell fat like olive oil? Duh—that's a no-brainer.

Welcome back, my aspiring hackers! Domain Name System (DNS) is one of those things we seldom think about unless it doesn't work. Then, it can be very frustrating when we attempt to navigate to a website and we get that frustrating error message.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

Welcome back, my budding hackers! In previous tutorials, we've looked at some of the basic commands and concepts for using Linux. Along the way, I realized that I've failed to provide you with some basic background material on the stdin, stdout, and stderror.

Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.

KitKats? Toast? Sorry if that headline made you hungry, but no I'm not talking about Nestlé's chocolatey wafer treat, nor the crunchy slices of bread you have with your eggs in the morning.

Welcome back, my tenderfoot hackers! I recently began a new series on digital forensics to help tenderfoot hackers from being detected and ultimately, incarcerated. In this installment of that series, we will look at recovering deleted files. This is important to hackers because you need to know that even when you delete files on your computer or on the victim's computer, a forensic investigator can usually recover them.

It's officially the holiday season, which means everyone will soon be traveling home to spend time with loved ones. And anyone who has any knowledge whatsoever of computers knows what else that means—family members left and right asking you to fix their various technical woes.

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

When it comes to the user interface, you're pretty much limited to the stock one that comes on your Samsung Galaxy Gear smartwatch—a carousel of large black and white icons representing the features and applications on the watch.

With the Samsung Galaxy Gear smartwatch only several weeks old, the extent as to what you can do with it is limited since there are only about 70 apps in the Gear Store right now, and a lot of those need the full app installed on your Samsung Galaxy Note 3 in order to function properly.

Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Most smartphone manufacturers focus on megapixels when it comes to cameras, but HTC took a different direction with the HTC One. Instead of trying to compete with the 13MP camera on the Samsung Galaxy S4, or the 20MP camera on the Sony Xperia Z1, or even the newer iPhone's 8MP, they decided on a simple 4MP camera. At first, you might think that 4MP is terrible, but not so fast. There are many advantages to your HTC One's camera that other phones just don't have.

Welcome back, my aspiring hackers! As mentioned several times in previous Linux tutorials, nearly everything in Linux is a file, and very often they are text files. For instance, all of the configuration files in Linux are text files. To reconfigure an application in Linux, we simply need to open the configuration file, change the text file, re-save, and then restart the application and our reconfiguration is applied.

If you're a Twitter user, it's a safe bet to assume that you've used a hashtag. On all social networking sites that have the capability, such as Instagram, Facebook, and Google+, the pound (#) symbol is used to mark and designate specific keywords or topics in order to make it effortless for users to connect with one another.

Welcome, my hacker novitiates! As part of my series on hacking Wi-Fi, I want to demonstrate another excellent piece of hacking software for cracking WPA2-PSK passwords. In my last post, we cracked WPA2 using aircrack-ng. In this tutorial, we'll use a piece of software developed by wireless security researcher Joshua Wright called cowpatty (often stylized as coWPAtty). This app simplifies and speeds up the dictionary/hybrid attack against WPA2 passwords, so let's get to it!

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

A spare key is one of those things that never seems like a huge deal until you need it. If you've ever lost your keys, had them stolen, or locked yourself out of your house or car, you know how difficult and embarrassing it can be trying to get your door open.

Welcome back, my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on all of us—all of the time. Don't get me wrong, I don't condone it, but I know the NSA.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

Welcome back, my neophyte hackers! Several of you have written me asking how to crack passwords. The answer, in part, depends upon whether you have physical access to the computer, what operating system you are running, and how strong the passwords are.

One of the most frustrating things on the Internet are sites that make you register just to view content. I'm not talking about paywalls—I mean the sites that make you give them personal information to look at free articles or forum threads. Most people are uncomfortable with this because a lot of these sites either spam you themselves, or sell your information to someone else who will.

Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.

Having trouble finding the right foundation for your makeup creations? The trick is, you need to know about them first, and know about your skin type, in order to get the perfect match. This video will help you decipher your foundation makeup issues and find the perfect one. Visit Hoppy's Makeup for more information.

Kai Shu is the most modern type of Chinese calligraphy. This video demonstrates how to draw some simple, unrelated characters with style, grace, and a brush. It goes on to show some more printed examples of this type of calligraphy. Work slowly, practice, and you can master this ancient painting art for yourself.

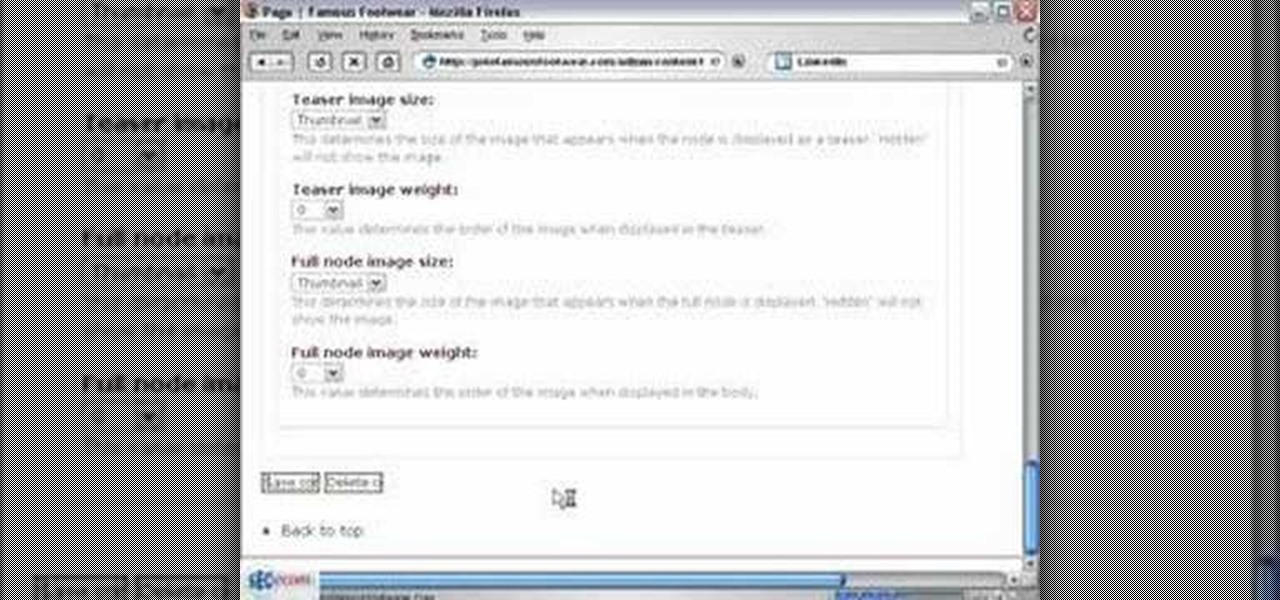
In this video you will see how to upload image content types on your Drupal CMS system

In these videos on raising farm animals, learn some of the basic facts about sheep. Our expert naturalist will discuss the major characteristics of this bovine species, including different types of sheep, types and colors of wool, eating habits and digestion (it is a ruminant animal), how to raise and handle a sheep, how to go about buying a sheep of your own, signs of disease, when to shear, how to tell a ewe and a ram apart, and how to breed sheep.

In this video from faintstarlite we learn how to jailbreak an iPhone 3GS step by step for beginners! Your iTunes needs to be running 3.0 and you must use a windows computer. Plug in your iPhone to your computer. Go to purplera1n.com and download the program. Your iPhone will now reboot and it will load up with the Purple Rain icon. Now click on the Freeze icon and install Cydia which then allows you to download programs on your iPhone. You will need this to download ultrasnow which unlocks yo...

In this how-to video from the TyingItAllTogether Channel, learn how to tie Clifford W. Ashley's flower knot. Ashley is the author and illustrator of a book he wrote about tying various types knots, including ones that he created himself. In his book, Ashley shows how to tie this knot, but does not show in his illustrations how to actually hold and tie the knot in one's hand. This video tutorial seeks to clarify those steps. You will need to begin with a piece of rope folding it in half to eff...

Have you ever seen one of those Snapple machines with the lever coin return? I will show you how to get free drinks or snacks out of this type of machine.

In this tutorial, we learn how to cook a deboned turkey in a small oven. First, take out the sack of guts and the turkey neck from the turkey and place in a large pot full of water. When finished, cut the turkey open with a sharp knife, then remove the breast plate and ribs. Then, remove all the bones and parts you can find on the inside of the turkey by cutting gently and pulling the good meat gently away. Once you have cut all of the bones out of the chicken, you can start to cook the turke...

Many of us often faces the electric problem and one of them is power plug problem. When it goes down you need to change it.

To solve a Rubik's cube, you will need to begin by keeping in mind the 7 steps. To learn about the cube itself, you will need to take it apart. The cube has 3 types of pieces. The center pieces do not move. They are actually fixed. Every piece is unique, and every piece has a unique place.