
How To: Hack Any Account That Has Recovery via Phone Option Enabled (SMS) On Android:
Hello Elite Hackers! Welcome to my 3rd Post, which explains how to hack any account like G-mail, Facebook, etc.


Hello Elite Hackers! Welcome to my 3rd Post, which explains how to hack any account like G-mail, Facebook, etc.
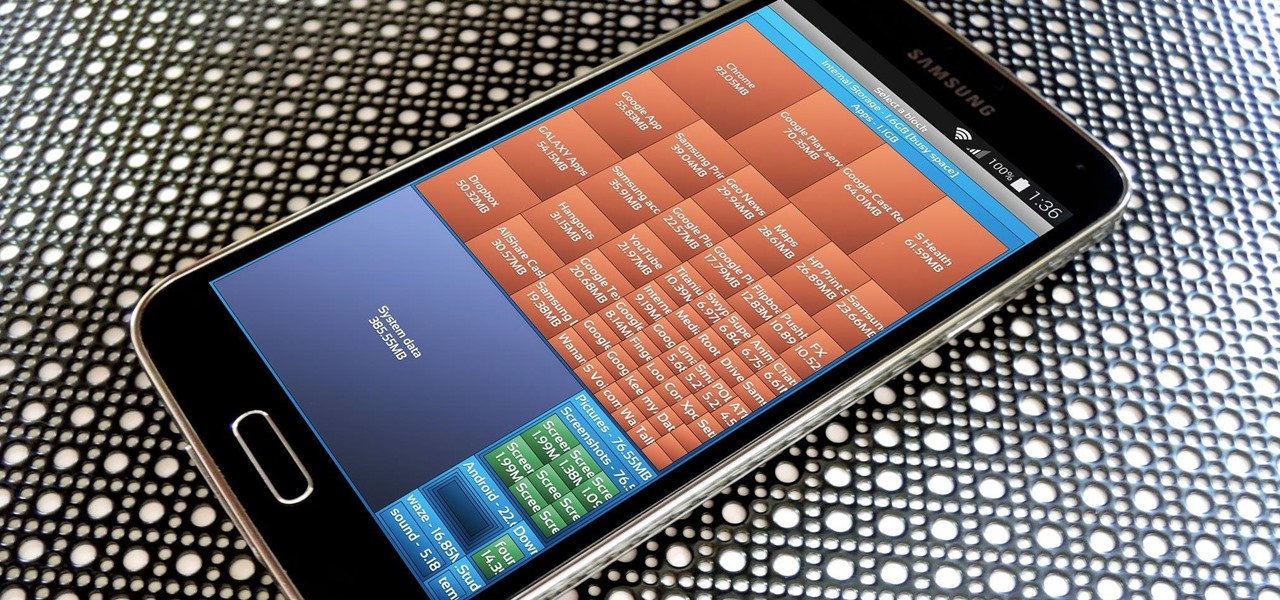
The more we use our smartphones, the more storage space becomes occupied—it's an inescapable fact. But as the data accumulates and chokes off our storage, it can become difficult to identify exactly which files are occupying the most space.

The Nexus 6 is one of the few devices on the market that sports a 1440p "QHD" display. This means that the amount of pixels displayed is higher than almost any other smartphone, which sounds great on the surface, but is not without its drawbacks.

If you're a fan of Thai food, I'm sure you're familiar with sticky rice. There is something so special about its chewy texture and sweet flavor. If you have a desire to make it in your own kitchen but don't have the proper tools such as a traditional bamboo basket or stackable steamer, there are several other methods that work just as well. Once you try these alternative methods, I'm sure you'll be "sticking" to them for a while. What Makes Sticky Rice So Sticky?

In the weeks before Apple officially released iOS 8, consumers were abuzz over rumors that a new feature would password-protect your photos and text messages from prying eyes. Unfortunately, this ended up being untrue, though we did cover some alternatives to protecting your important information using some built-in features and a third-party app. Now, there's a new iOS app that can do it all.
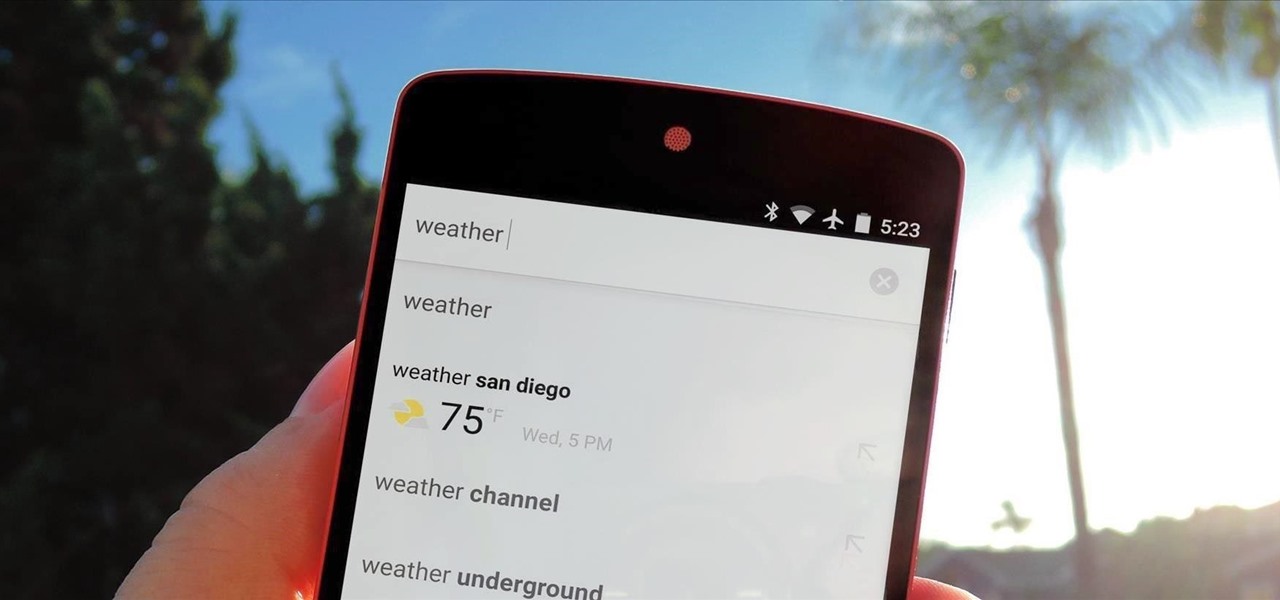
Google continues to be the most commonly-used search engine for a reason. While continuing to stay ahead of the pack with advanced semantic search functions, Google even introduced Knowledge Graph results that offer key information without ever having to click a search result.
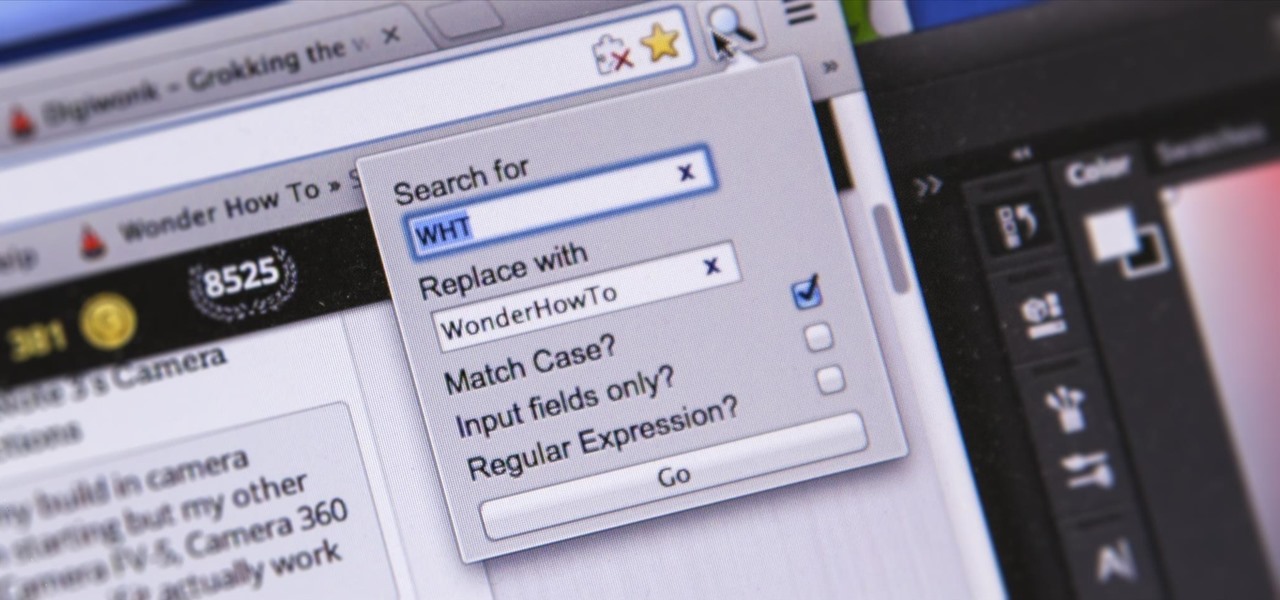
I'm sure you've been there—halfway through typing something out, you realize that one word you've been using more than any other has been misspelled. Perhaps it's a single word, acronym, or line of code that you find yourself typing quite often at work, but this one requires complicated hand gymnastics that you'd simply rather not perform over and over again.

Finding a unique wallpaper can be extremely difficult, and even the most dynamic wallpapers become exhausted and boring to look at after a while. Searching for new, interesting wallpapers can become a tedious task, so instead, let's just make our own instead.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.

It was a chilly but otherwise beautiful night at YouTube Spaces LA—food trucks, ping pong, a photo booth, and the chance to view film school projects created completely with Glass. About a year ago, the Glass Creative Partnership was formed to explore how Glass could be used in filmmaking, with partnerships spanning from the American Film Institute to CalArts and UCLA. On July 16, 2014, the products of that partnership were screened under the Southern California night sky. Three films were sh...

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"
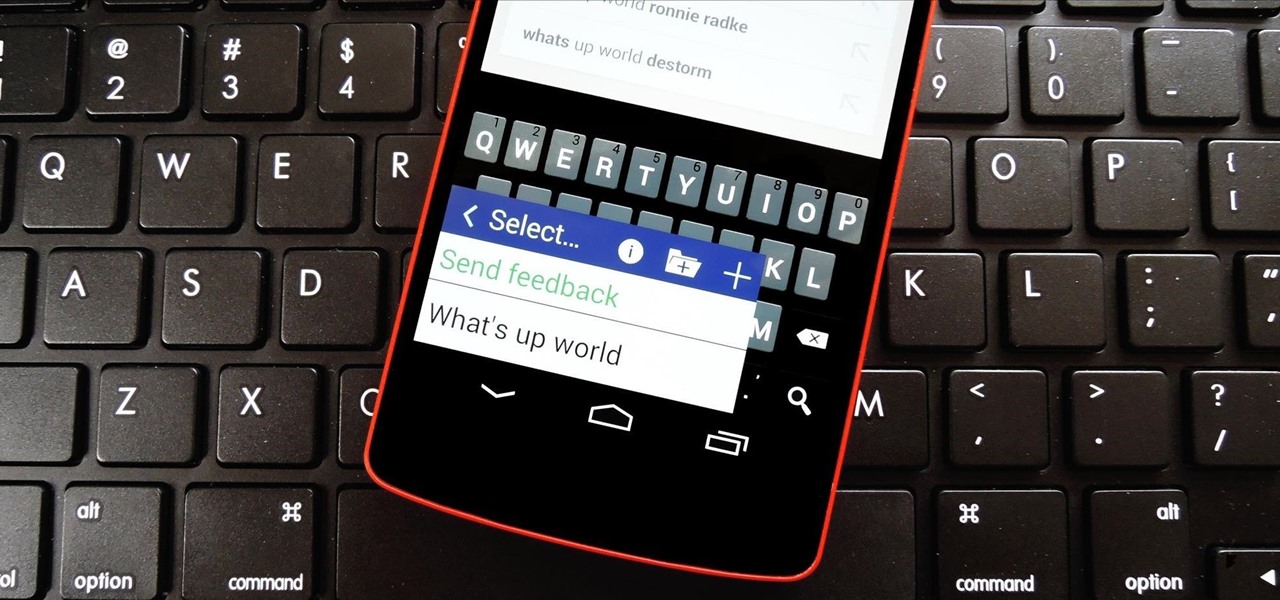
There are a lot of instances where we find ourselves typing virtually the same phrase that we've typed many times before. Whether it's the standard spousal reply of "I'll be home in a few", or a work-related phrase like "I'll have that to you by the end of the day", typing phrases like these can feel very redundant at times.
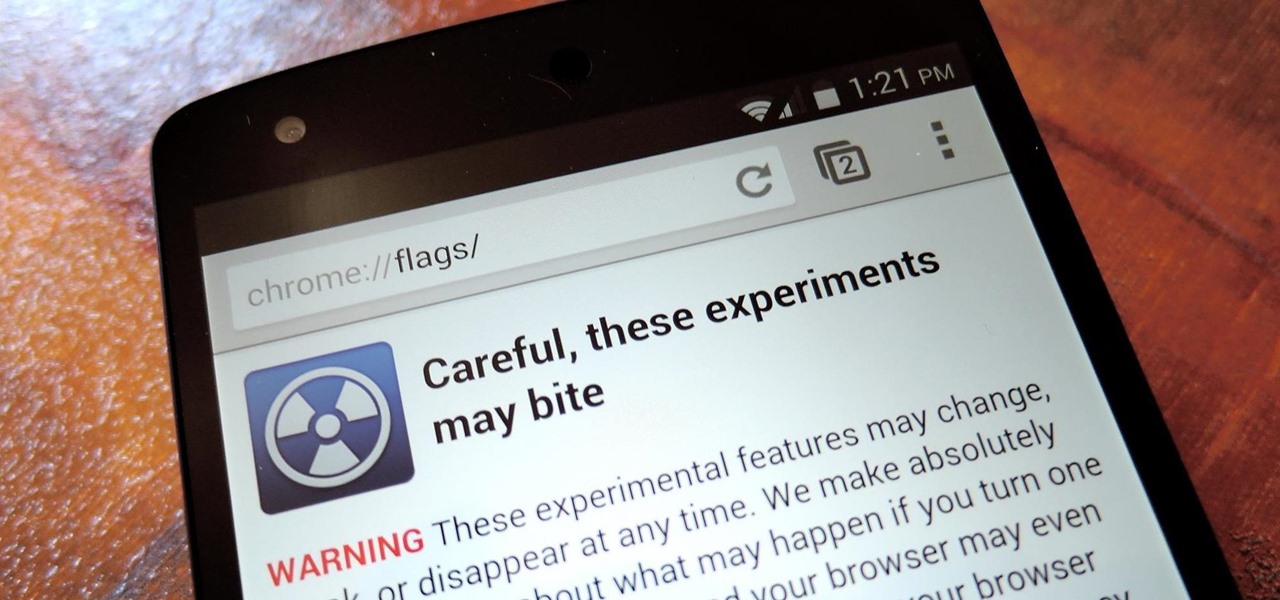
With the release of Jelly Bean, Chrome became the default web browser on Android. The wildly successful desktop browser was now fully entrenched in the world's largest mobile operating system.

The space on your phone is extremely valuable, so getting the most out of your screen real estate can help you out when multitasking or for just making your device feel bigger. One thing that is often overlooked when it comes to saving space on the screen is the keyboard.

Air New Zealand is looking for a spokesperson for the Antarctica: No Ordinary Place, No Ordinary Assignment project, a two-week adventure in Antarctica, where the chosen candidate will join National Geographic photographer Jason Edwards to document environmental issues and important research being conducted by research teams sponsored by Air New Zealand and Antarctica New Zealand.
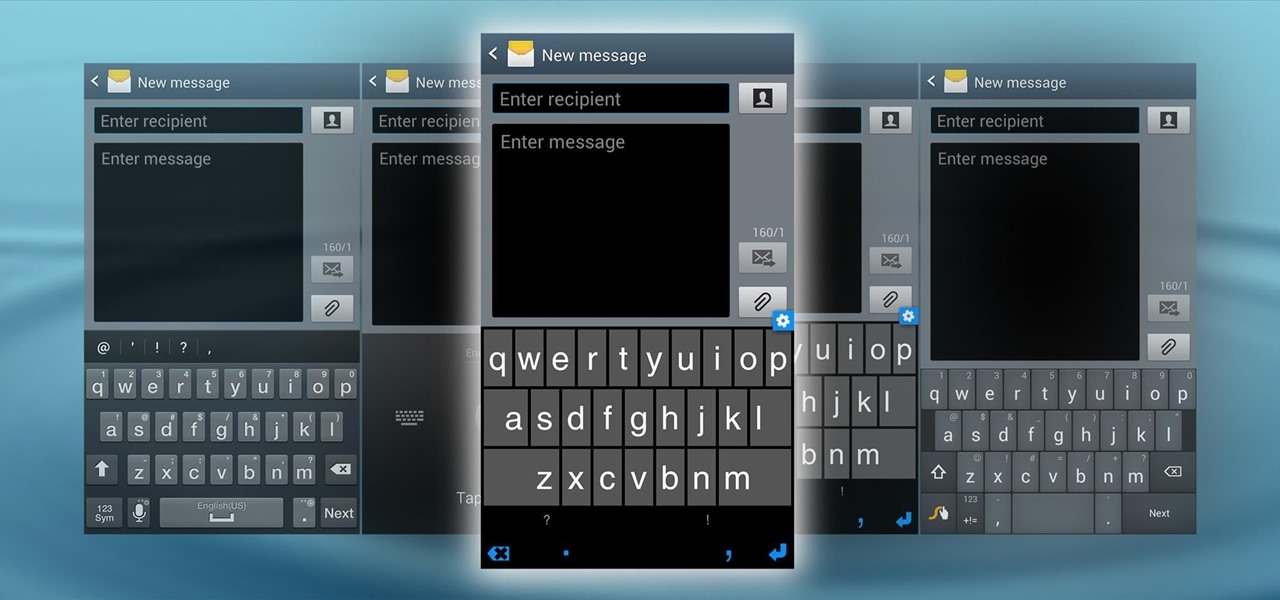
The absence of a physical keyboard is both a gift and a curse. When it was announced in 2007 that the first iPhone would have a touchscreen only, people literally lost their shit. Now, almost 7 years later, you'd be hard-pressed to find a smartphone that still has a physical keyboard.

Welcome, my neophyte hackers!

In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, creating files and directories, and finally, getting help. Let's open up BackTrack and getting started learning more Linux for the aspiring hacker.

Cinema is a matter of what's in the frame and what's out, according to director Martin Scorsese, who asserted that when describing his life's work. Getting the perfect shot can turn an otherwise ordinary scene into something great, both on and off screen.

Welcome back, my newbie hackers! We've already saved the world from nuclear annihilation and covered our tracks afterwards, but the world is still threatened by a malicious, megalomaniacal dictator with missiles and nuclear weapons.

Who doesn't hate Auto Correct? There's nothing worse than hitting 'Send' only to realize that your phone betrayed you by changing a word so that your message doesn't even mean the same thing anymore—especially when it's going to someone like your boss or parents.

Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"!

Time-lapse videos are a recent phenomenon to the mainstream audience—in movies, on television shows, and even in commercial ads. These sped-up and blurred images are a microcosm of many of our lives in which we're constantly in a hurry to get somewhere. We like everything fast: our work, our coffee, and our news.

There are several ways to send pictures to others on your smartphone—picture message, email, Bluetooth, and even by bumping phones together. Now there's an even more unique way to transfer pictures from one Apple device to another—with sound. Chirp for iPad, iPhone, and iPod touch

When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.

The simplest and most fun way of customizing your Converse sneakers to reflect your personality is to lace them all fancy-like. Whether you love pink laces or emo black ones, choose two of your favorite shoelace colors and check out this fashion DIY tutorial to learn how to tie your Converse shoe with two laces per shoe.

If you say Ke$ha at the MVAs you saw her new look: a dress made from a trash bag! Well, if you're looking to create something cool for less than $2, check out this video and see how to make Ke$sha's inspired garbage bag dress. You don't have to spend a million dollars to turn heads, in fact, you likey have all the materials you need right under your kitchen sink! For this project you'll need a trash bag, some scissors, some tape and a stapler. For your own flair, grab sparkles, streamers or w...
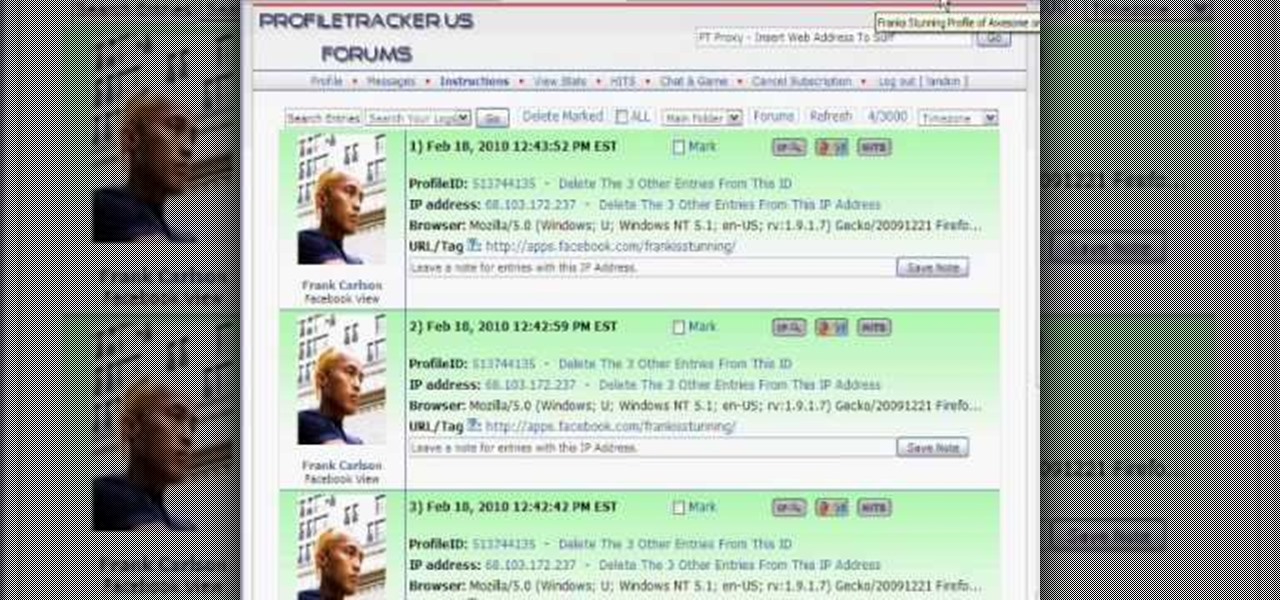
Want a way to monitor who is coming onto your Facebook profile? You can use a third party app, the FBspace Tracker, to enable your profile to secretly log who is viewing you. Even better, FBspace Tracker lets you set up your profile with custom HTML code. This video shows you where you can download the app, then how to install it and set up your Facebook profile through the app. Make your profile not only unique, but secure as well!

The holidays are upon us, guys and gals, which means it's time to start thinking about how you'll set your table to look inviting and beautiful for the festive season. While you can always go out and purchase a wilting pre-made floral centerpiece at your nearest supermarket, you yourself can often make a much better looking centerpiece at home.

Emilie Autumn is a fun, unique singer who dresses up like the hybrid of a doll and pin up girl. Slightly kooky yet adorable at the same time, the singer is truly one who doesn't care what others think of her personal style.

Leggings have the unique ability of covering you up (as long as we're not talking sub zero temperatures here) and keeping you warm and fashionable at the same time. They allow you to continue wearing certain fall dresses into fall. and look great in a pair of boots.

In this tutorial, we learn how to make a church door card. To start, you will need to take a piece of card stock and the template for the church door. After this, you will fold the template up using the paper, then cut it out. After this, write the message you want on the inside of the card. From here, you will decorate the front of the card and then tie a ribbon on the front. This will close the two doors and then when you upwind it, the person can see the inside. Make this unique and have f...

In this tutorial, we learn how to draw a skull with a Sharpie. First you will draw the eyes, make sure to draw lots of little lines around them then cross them to create depth. From here, draw the outline to the head and then the nose and the teeth. Make sure to add lines in around the head to show cracking and marks around the head. Use shading to create darker lines along the head and then add in additional details. Make this unique to you, it doesn't have to look one certain way. When fini...

In this video, we learn how to knit with color with Brandon Mably. Get inspiration from the world around you to get different colors and make out different patterns. Carry your colors around the item that you are knitting to make a nice pallet that you love. You can use inspiration from the outside, different states, stores, plants, and anything else that you love! Once you find something you want, get started knitting and find a way to knit that works for you. Use the color range that you ar...

In this video, we learn how to make a VW beetle cake with buttercream. First, you will need to apply the buttercream icing onto the top of your cake and the sides. After this, you will pile on the other cakes to this with more icing inside of each layer. Then, you will start to cut the cake and it into the shape of the car that you want to make. Use an outline so you can follow it while you are making it so you know exactly how it is formed. Next, you will add in the parts for the wheels, the...

In this tutorial, we learn how to draw Naruto 4-tails. First, draw the outline of the characters and the four tails. After this, draw in the rest of the outline in the final stages using a darker stroke of the pencil. Start to add in the details of the figure of the body and then add in the shading around the sides. Make sure you draw in the hands and the fingers as well as the facial features to make it look more realistic. Add in any more details that you would like to make it unique, then ...

In this tutorial, we learn how to draw a cartoon spray can. Start off by drawing a round circle for the eyes, then fill in the pupil and draw the eyebrow above it. After this, draw in the nose and then draw the other eye opposite to the first. From here, draw in the mouth and the goatee on the face. Then, draw in the top, which will be a rectangle with a half circle on top of it. From here, draw a hand on the right side pointing straight out, then draw a top to the spray can showing the spray...

In this tutorial, we learn how to add 3D effects and shading to graffiti letters. To start, you will draw a simple letter with a pencil. Then, take one point under the letter in the middle and draw a darker outline. Next, you will draw an outline around the first outline to make it look 3D. Next, you will shade in the area in the middle of the letter and anything that is in between the first letter and the second. After this, you will add in lines and additional detailing to make the letters ...