A lot of things have been changing over at Microsoft recently. Not only did they acquire the ever-popular Android keyboard SwiftKey and give away Windows 10 for free, but they've started a Google X-like experimental division called Microsoft Garage, and they've actually released quite a few awesome Android apps.

Yes, I understand some people may consider this a repost. However, I have been searching for this answer for 3 weeks and after reading numerous reddit post, Kali Forums post and Null byte post I finally have gotten it to work for me. I would like to compile and share this information with you guys.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

ADB and Fastboot are probably the most essential tools for any Android aficionado. They can do everything from backing up your device to unlocking your bootloader with a few simple steps. This paves the way for many new tweaks and customizations that weren't possible before. The required platform works with the three most popular computer operating systems, too, which is good news for everyone.
For all of the flak that Windows 8 received from desktop users, it certainly had some interesting and unique features. For instance, the "Charms" bar allowed you to easily access several key menus by simply hovering your mouse pointer in the top- or bottom-right corner of the screen.
Make no bones about it—having an "undo" option is a freaking godsend. Whether you accidentally deleted an entire essay, screwed up the shading on a Photoshop job, or sent an email that wasn't quite ready, having the option to undo a click or button-press can definitely be a lifesaver.
Hello, Hackers/Viewers! My name is nullf0x, and I have 4 years of experience as a hacker. You might see everyday that one of your friends or acquaintances get a new virus in their computer. You might think, How cool would it be if I made a virus? or How cool would I be if i could remove viruses from others computers for money or free?

If you're a Mac user with an Android phone, some apps on your computer aren't very useful, such as Messages, which is meant to work and sync with iOS devices. But now, thanks to MDRS, LLC, using the Messages app on your Mac with an Android phone is now possible and easily achievable. Plus, we've got 50 promo codes to give away for a free year of service!

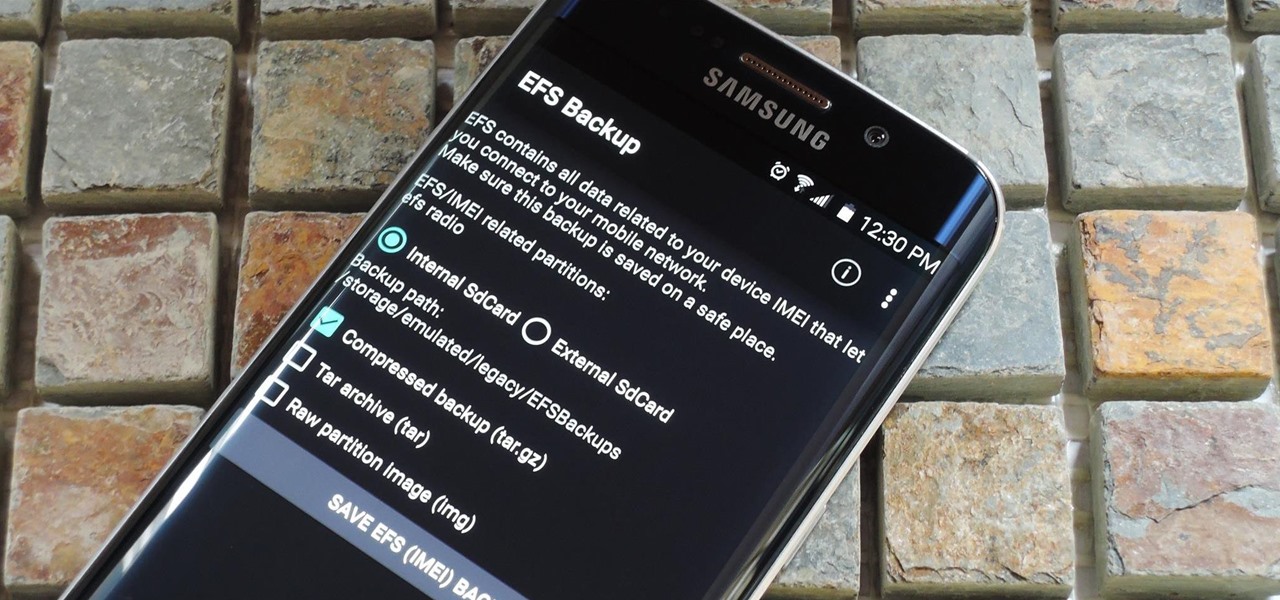
The EFS partition on modern Android phones houses the unique IMEI for your device, which is essentially an identification number that lets you connect to mobile networks. But sometimes, when you're flashing ROMs or restoring backups in custom recovery, the EFS partition can become corrupted, which will prevent your phone from connecting to any type of mobile network.

bObsweep Standard and Pethair are made to easily transition between a variety of floor types, so they function efficiently in most spaces.

Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.

Presented by Apartments.com When looking for a new apartment, it's hard not to notice the improvements (on large and small scale) needed prior to moving in. While your landlord may be taking care of new carpeting, cleaning the central air vents, and fresh paint on the walls, there may be some additional improvements on your list that you can take care of on your own. Here are five quick improvements you can check off your list before the big move.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Thanks to a couple of photoshopped images that made rounds across Twitter last year, iPhone users were duped into thinking that iOS 8 included a security feature that would lock individual apps. Of course, none of it ended up being true, but we covered other features and apps that could accomplish roughly the same thing.

One of the many unique features that sets Android apart from other mobile operating systems is its live wallpaper system. Instead of the same old boring static image, this system lets developers create apps that provide dynamic home screen wallpapers.

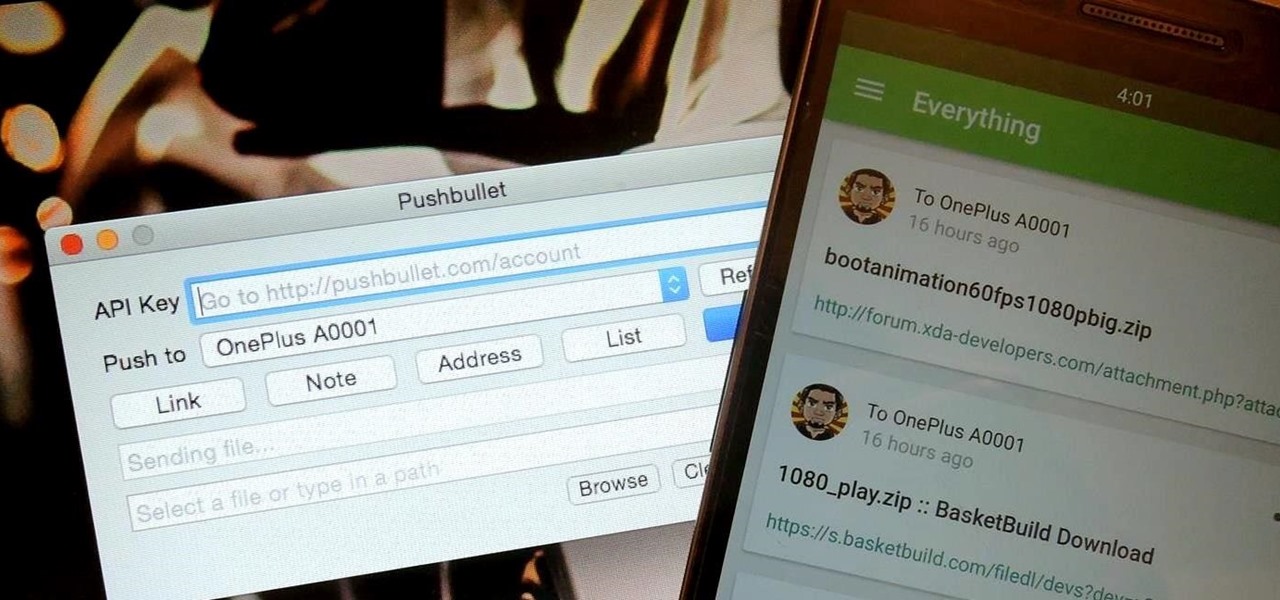
Before Continuity and Handoff were even announced, Pushbullet was already allowing users to quickly send notes, links, and photos between their devices with a few clicks.

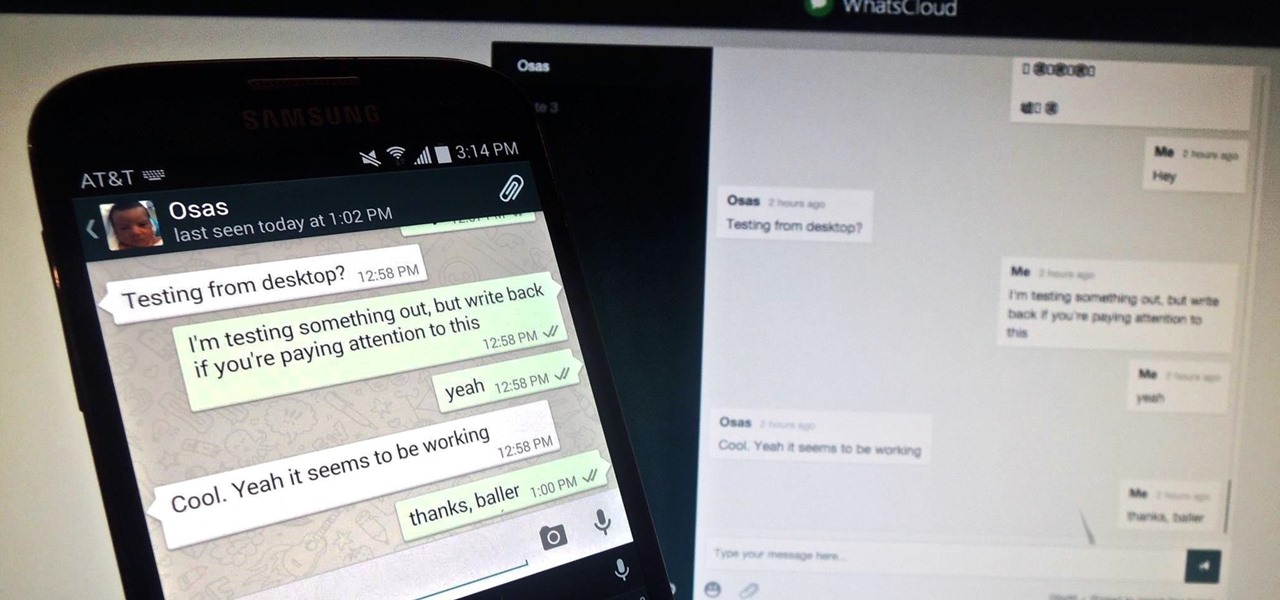
Pretty much my only gripe with computer-side messaging clients like Mighty Text is that they don't allow you to send and receive messages shared through WhatsApp, the popular third-party messaging application, which was purchased earlier this year for $19 billion by Facebook.

Third-party keyboards have been available for iPhone ever since iOS 8, but which ones are worth checking out? There have been many options over the years, and if you want keyboard features like swipe-typing and themes, you're going to have to put Apple's stock QuickType keyboard on the backburner and try out these top hits.

As soon as third-party keyboard compatibility was announced for iOS 8, Apple loyalists and the newly curious both looked to the popular Android third-party keyboard developer, SwiftKey, to see if they'd be offering their services to iOS.

Welcome back, my hacker apprentices! Last week, I started off my password cracking series with an introduction on the principles and technologies involved in the art of cracking passwords. In past guides, I showed some specific tools and techniques for cracking Windows, online, Wi-Fi, Linux, and even SNMP passwords. This series is intended to help you hone your skills in each of these areas and expand into some, as yet, untouched areas.

When Yahoo! purchased the home screen replacement app Aviate back in January, many were wondering if the internet giant intended to continue development of the launcher or if the transaction was just another acqui-hire.

These days, our smartphones carry some very sensitive data. From banking app passwords to personal photos, there are many things on your Nexus 5 that you might not want other people to have access to.

Introducing a unique way to share photos and videos among friends and family, Snapchat was the big hit of 2013 (despite its many flaws). Thanks to its ephemeral nature and lack of third-party sign-in integration, it quickly grew into a multibillion-dollar company in the span of just 12 months.

As precious as we like to think that all of the photographs on our smartphones are, they're really not. Every time I rummage through my extensive index of pictures, I quickly realize how many one-off pictures I have, which served their purpose a long time ago and are no longer important.

What kind of music do you like? It's a classic first date question that reveals so much about the person answering, but when it all comes down to it—everyone likes or listens to music. We may each have our own unique tastes and interests, but music is usually something almost anyone can get behind.

Writing longhand may boost learning and goal achievement, but that doesn't mean squat if you don't have pen and paper on you.

Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it.

THis video shows you what types of videos you can make, why you should make videos and exactly whant you need to get started.

I am a man who enjoys a good cup of crap. Not just any crap, but the kind that makes the Seattle coffee-snob inside of me feel all warm and happy as if the sun were out (which of course it isn't.) It's the kind of crap that has traveled through the intestinal tracts of a nocturnal marsupial, cutely called a Civet. It's the kind of fermented brew that everyone should lay their lips on at least once.

This video will show you how to use MCedit to create flat land in your Minecraft world. Are you the type for wide open spaces? Land lots of land under starry skies above? Watch this video to learn how to make flatland in Minecraft with MCedit.

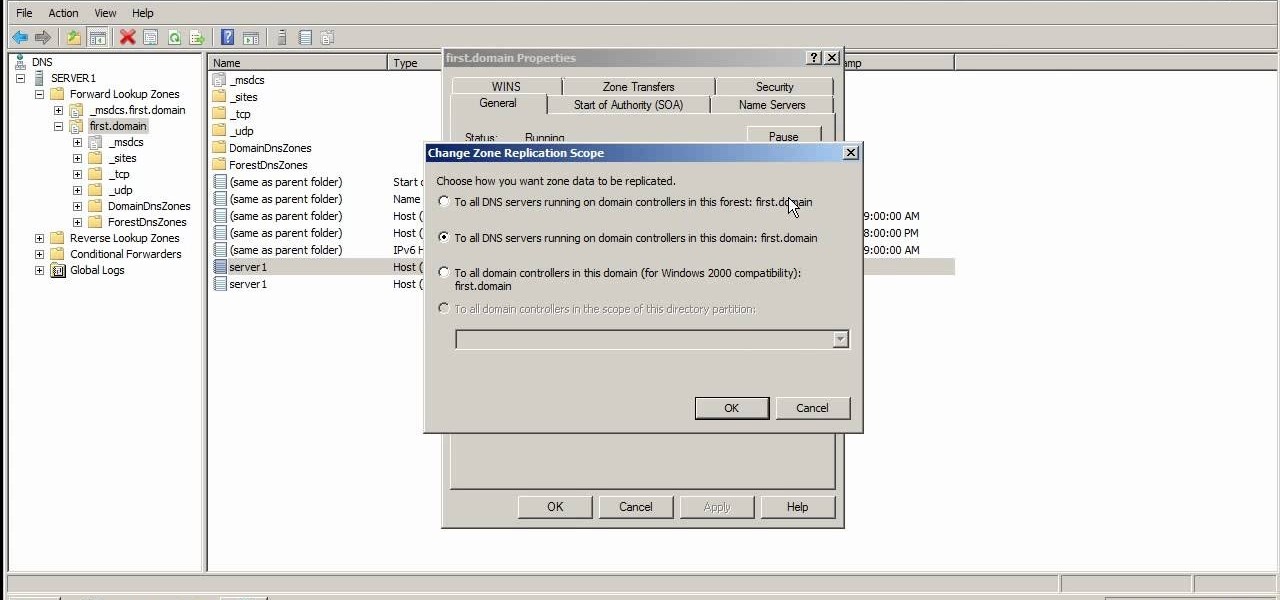
This video explains the different kinds of zones you will come across in Microsoft Windows Server 2008 DNS. The video has practical step by step instructions to managing these zones, as well as understanding their different functions and uses, and covers replication.

Fairy cakes are basically lovely little cupcakes adorned with pretty icing and "fairy dust" - AKA sprinkles - for a nice ethereal effect.

You may be just recovering from a hectic - and binge-filled - holiday season, but prom season is just around the corner. Make sure you look like the belle of the ball by creating this simple and romantic hairstyle.

This tutorial shows you how to determine what kind of skirt you have - straight or tapered . Then, depending on the type of skirt you have, you're shown how to alter the hem or shorten the length of your skirt.

This tutorial shows you how to do two basic macrame ties, which you can use to make keychains, bracelets, chokers and other types of jewelry. Add beads, charms and other decorations to your projects - macrame is cheap, easy and fun!

This is an easy tutorial that will go well with any Renaissance Faire outfit or similar costume. By using two different types of fabric, you can even make it reversible and increase the number of costumes you can wear it with.

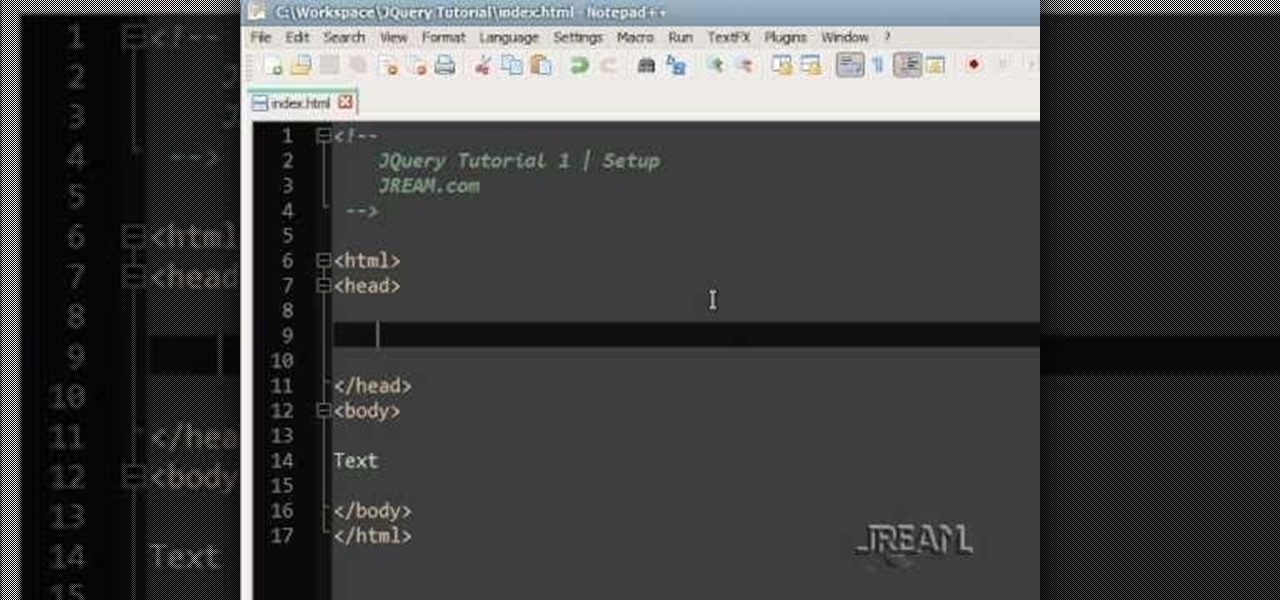
Learn to work with PDO in PHP with this informative video tutorial from JREAMdesign. The PDO extension is a consistent interface for accessing several types of databases in PHP and it has a ton of options. This knowledge is also required for Zend Certification.

There are so many choices at the craft stores when you go to buy some new stamps! Do you get wood or acrylic? How do you choose the best one? This video shows you everything you'll ever need to know when it comes to stamp types.

There are several different techniques you can use to transfer a pattern onto the fabric you want to embroider, depending on the color and type of the fabric you want to embellish. This video shows you three separate techniques, such as chalk pencils or tracing paper.

JQuery is a new type of JavaScript that you can use to write and design your own websites. This tutorial shows you how to download the JQuery software and set up a few basic items, like script tags. Now you're ready to start learning JQuery!