Do you feel like you will go crazy if you see another website written in Comic Sans? You are not alone. In this tutorial, learn how to download free fonts online and install them on your computer for use in Photoshop. By using new fonts, you can guarantee that your graphics will look unique and polished.

You are typing along and you notice one of they keys on your keyboard isn't responding like it should. It is common to get a stuck key and you won't need to take your keyboard to fix this problem. You can do it right at home.

This video shows how to make a "Dreadhawk," which is a mohawk made of dreadlocks. This is a unique hairstyle that provides a very different look. The instructor begins by separating his front section of hair from the rest, and making a ponytail with it using a rubber band. He continues in this manner, making five more ponytails with sections of hair. You can then tie ponytails together, restricting their movement and keeping the Dreadhawk more intact. This hairstyle can also be done with regu...

In this video, the Flowergod demonstrates how to make an Asian inspired arrangement with bamboo and colorful flowers. He starts with a low pot filled with craft foam and adds some very large leaves to the bottom. He then puts a sparse branchy twig in the middle along with several tall bamboo canes. He adds purple flowers and more greenery at different levels, and a large red flower at the base. The video is speeded up so you can see every step in the process. This is a unique and beautiful ar...

Do you ever want you hair to appear short, but feel that cutting it is the only way? Well YouTips4U has found a unique and creative strategy to making your hair appear short without even having to cut it! It's a simple process and all you need is a ribbon of your choice. YouTips4U shows you a few different basic styles and tips you can use to make your hair look short and beautiful. So if you are looking for a short new look for your hair without the cut, this is the video for you.

Do you need a Venetian mask but can't afford to buy a fancy one? This tutorial teaches you how to make a Venetian style mask by yourself with some basic supplies you can buy from a craft store. You'll need a blank mask or some plaster strips, decorations (like ribbons, crystals, feathers etc.) and basic construction tools like X-acto knives, scissors, and glue. First, you need to lay out the materials, add the trim with hot glue and attach the feathers to the top of the mask. The feathers wil...

Jolene Sugarbaker of The Trailer Park Cooking Show has a crazy new recipe that she wants to share with everyone. It's called oatmeal raisin asparagus cookies. Sounds interesting? Jolene insists that they are delicious. Learn how to make these oatmeal raisin asparagus cookies by watching this episode. These cookies are filled with essential vitamins and nutrients that you can't get from just any cookie. Your guests will never be the wiser that these cookies even contain asparagus in them. Alth...

The ukulele is a beautiful and unique stringed instrument that is perfect for the traveling musician because it is so portable and relatively inexpensive. The ukelele is a version of a small guitar that originated in Hawaii. In this tutorial you will learn how to play Spanish piece on the ukulele. Once you get a hang of this beginner song you can impress your friends with this easy Spanish song on your uke.

The ukulele is a beautiful and unique stringed instrument that is perfect for the traveling musician because it is so portable and relatively inexpensive. The ukelele is a version of a small guitar that originated in Hawaii. In this tutorial you will learn how to play "Moani Ke Ala," an old Hawaiian song in the key of D. This song's progression is D A D D7 G D A A D A D (repeat)then a transistion chord for key change C, then key of F. The progression in the key of F is F C F F7 B flat F C C F...

The ukulele is a beautiful and unique stringed instrument that is perfect for the traveling musician because it is so portable and relatively inexpensive. The ukelele is a version of a small guitar that originated in Hawaii. In this tutorial you will learn how to play "Tricky Fingers," an old Hawaiian song in the key of F. The chord progression in this song is F E Eflat D F C F C and the bridge is A D G7 C. Once you get a hang of this beginner song you can impress your friends with this rendi...

The ukulele is a beautiful and unique stringed instrument that is perfect for the traveling musician because it is so portable and relatively inexpensive. The ukelele is a version of a small guitar that originated in Hawaii. In this tutorial you will learn how to play "Kauoha Mai The Keyhole Hula" by Martin Pahinui. The chord progression in this song is E7 A7 D E7 A7 D for the intro and D D7 G D E7 A7 D E7 A7 D for the verse. Once you get a hang of this song you can impress your friends with ...

The ukulele is a beautiful and unique stringed instrument that is perfect for the traveling musician because it is so portable and relatively inexpensive. The ukelele is a version of a small guitar that originated in Hawaii. In this tutorial you will learn how to play "C-A-T, Popoki Spells Cat," an old Hawaiian song in the key of A. The chord progression in this song is A B7 A E7 A B7 E7 A. Once you get a hang of this beginner song you can impress your friends with this rendition of "C-A-T, P...

The ukulele is a beautiful and unique stringed instrument that is perfect for the traveling musician because it is so portable and relatively inexpensive. The ukelele is a version of a small guitar that originated in Hawaii. In this tutorial you will learn the correct left hand fingering position when you're learning ukulele or for that matter and stringed instruments with frets. Once you get a hang of this technique you will be able to play some easy songs on the uke.

What is better than wearing makeup? Cool colors on your nails with funky designs. Watch this Beauty & Style how to video to learn how to apply nail polish in the shape of flowers with a blue and green striped background on acrylic nails. Everyone is sure to love this unique flower nail design. The nail enamels you will need for the fancy nail look are: blue, blue green, red, orange, white, yellow gold.

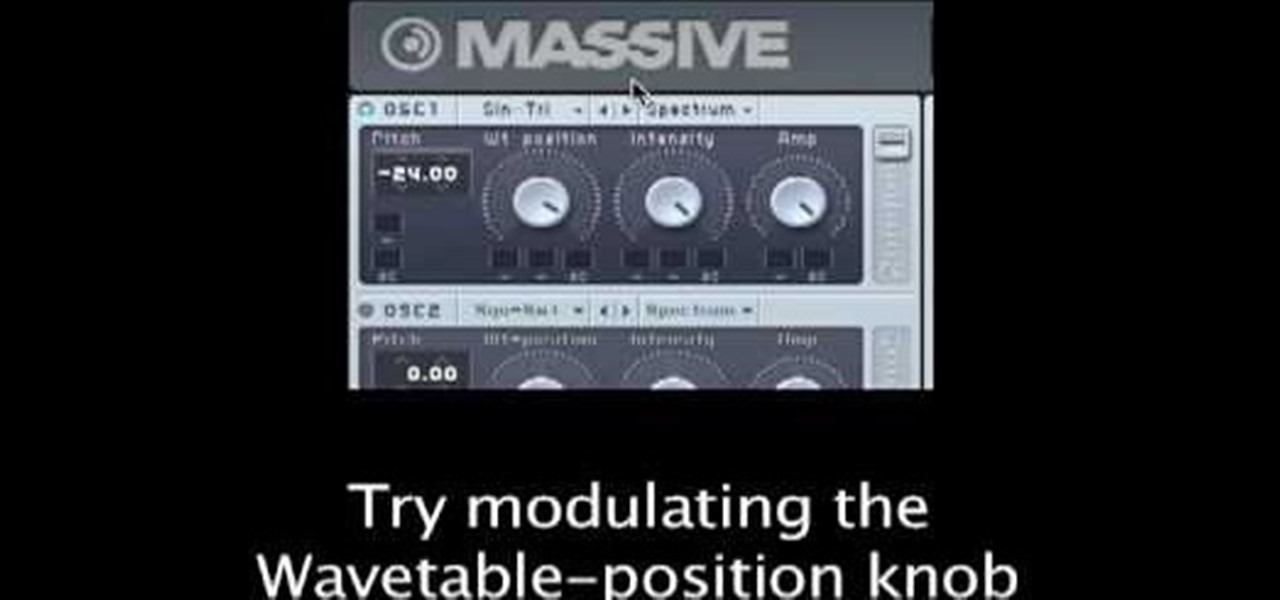
This tutorial demonstrates use of the Native Instruments' MASSIVE synthesizer, which shifted the paradigm for software synthesis development in late 2006. MASSIVE's fat, analog sound is unique to the soft-synth world, offering a wide scope of sound design possibilities. But underneath all that, it is an extremely simple-to-use, great-sounding engine that can provide some of the baddest bass tones you've ever heard. And remember: all patches discussed in the video are available through http://...

Follow these crochet guidelines to start a wavy shell pattern crochet blanket. This pattern is only a two row pattern. You can use three colors to make it appear unique and interesting. The beginning is the most difficult part, but once mastered, this crochet pattern is deceptively simple.

You love the video game Tetris and you love the puzzle Rubik's Cube, then what's stopping you from attacking the Tetris Cube?

Scrapbooking is all about using a variety of materials to create different effects. This idea just uses simple household masking tape and watercolor paints. Masking tape can be stuck onto a glass surface or anything else where it can be easily removed, and then painted with watercolor paints. The end result is a really great finish. Watch this video scrapbooking tutorial and learn how to use masking tape and watercolor paints to create a unique look for any scrapbooking project.

In this video series, learn how to dress different plus size body types. Our expert, Michele Varon, shows you the different types of plus size women. With her plus size models, you can see which body type you most closely resemble. Once you know, you can start to find flattering clothing for various occasions.

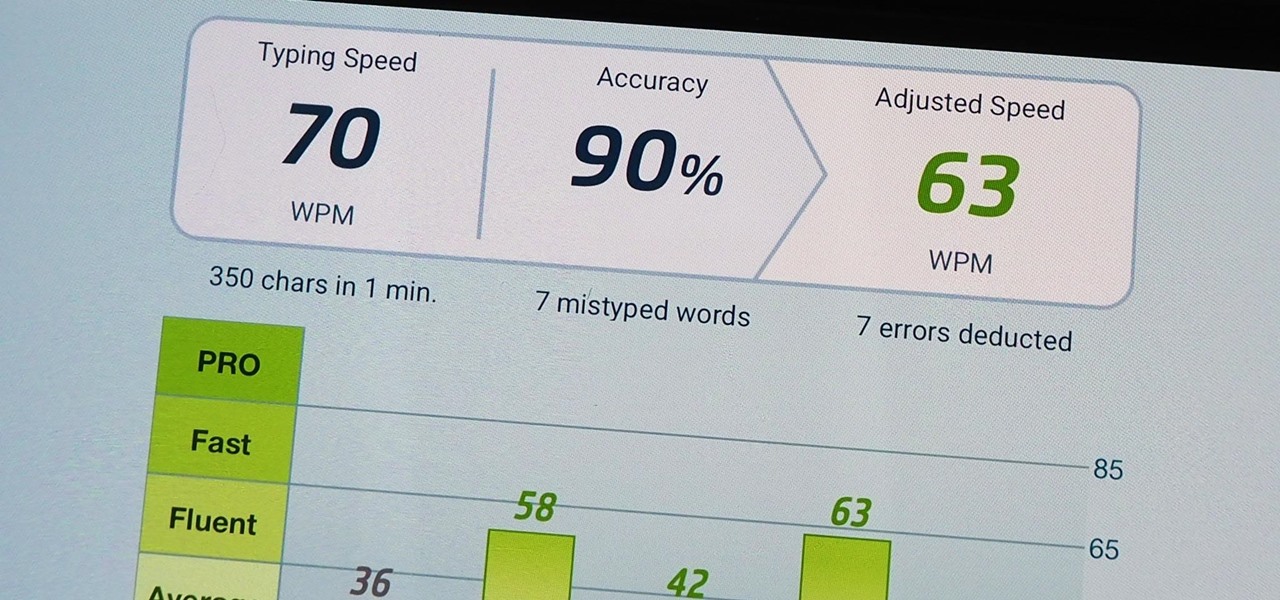
We use our smartphones every single day. They're a part of our daily routine, and as a result, we've gotten really good at using them — especially when it comes to typing very quickly. But just how fast can you type on your iPhone? Can you match your speed on a physical keyboard for your computer or tablet? You might just surprise yourself.

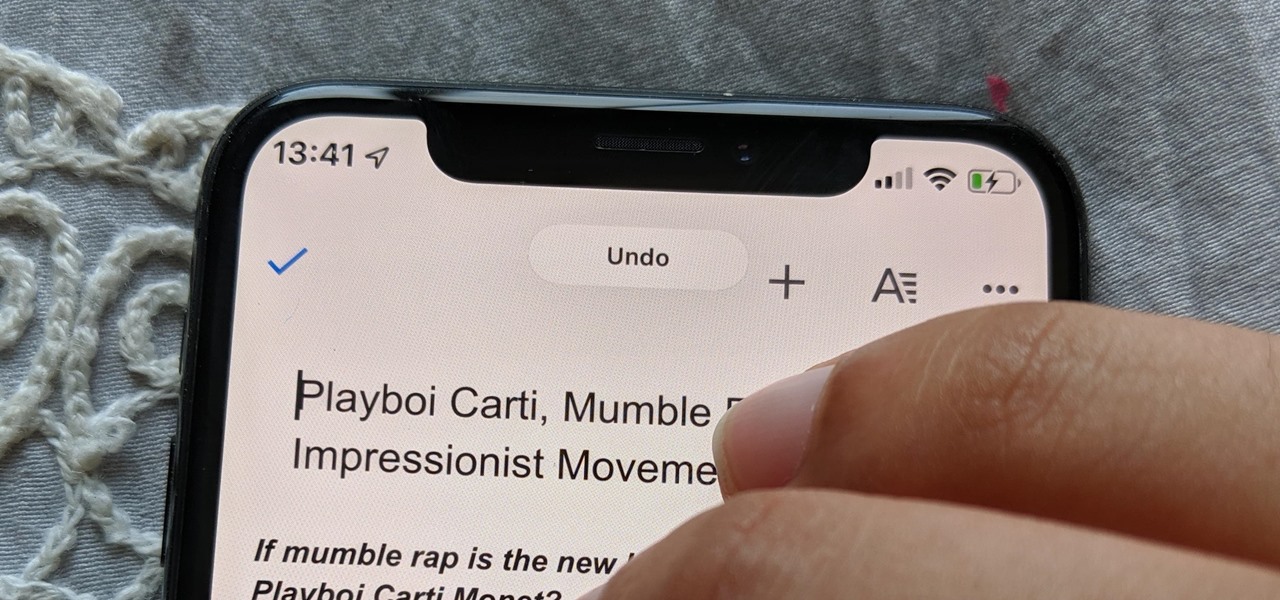
Between sending iMessages, jotting down notes, and crafting emails, you do a lot of typing on your iPhone. No doubt, you've been in the middle of an important task when everything comes to a screeching, obtrusive halt, where a rogue "Undo Typing" pop-up forces you to close it before continuing with your typing. Don't put up with the BS anymore — here's how to stop it.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can easily fingerprint any hashes to discover the right Hashcat mode to use to retrieve a password.

Shake to undo is now the worst way to take back what you just typed on your iPhone. Among the many changes in iOS 13, Apple has updated text gestures, including how you select a word, sentence, and paragraph, copy and paste text, and undo and redo what you type.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

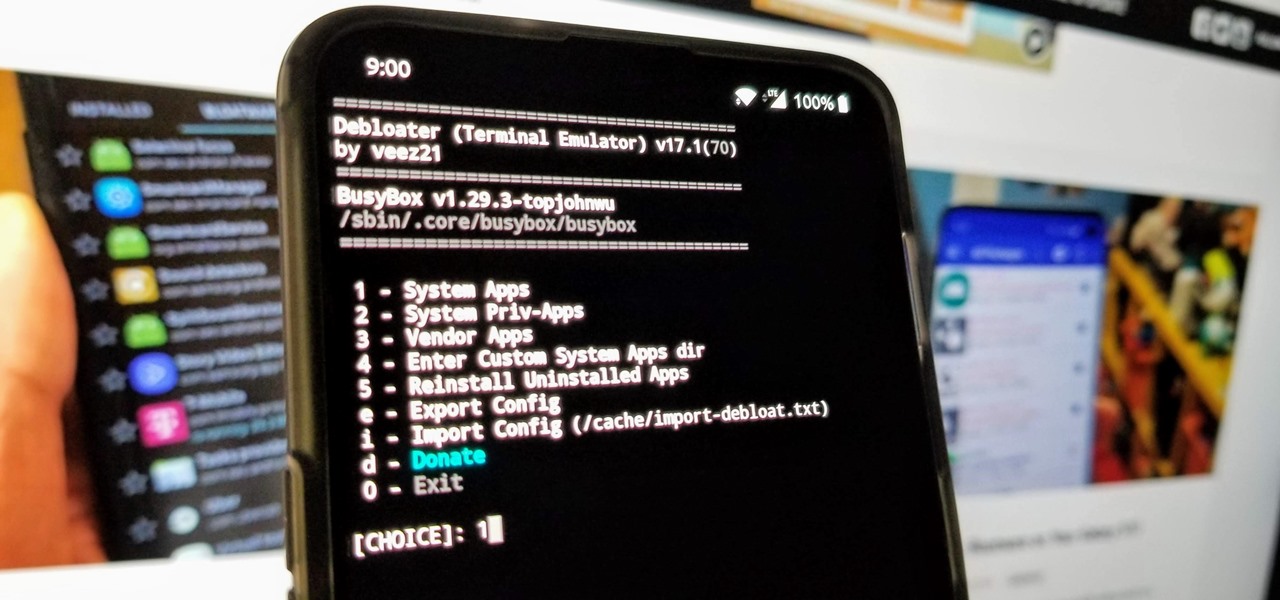
When you get a new phone, the last thing you want to deal with is a ton of preinstalled programs staring back at you. They not only clutter your home screen with apps you'll probably never use, but they're also wasting space on your internal storage and potentially draining battery. To truly uninstall them, you'll need root — but even then, it can be hard to pin down all the apps that should be removed.

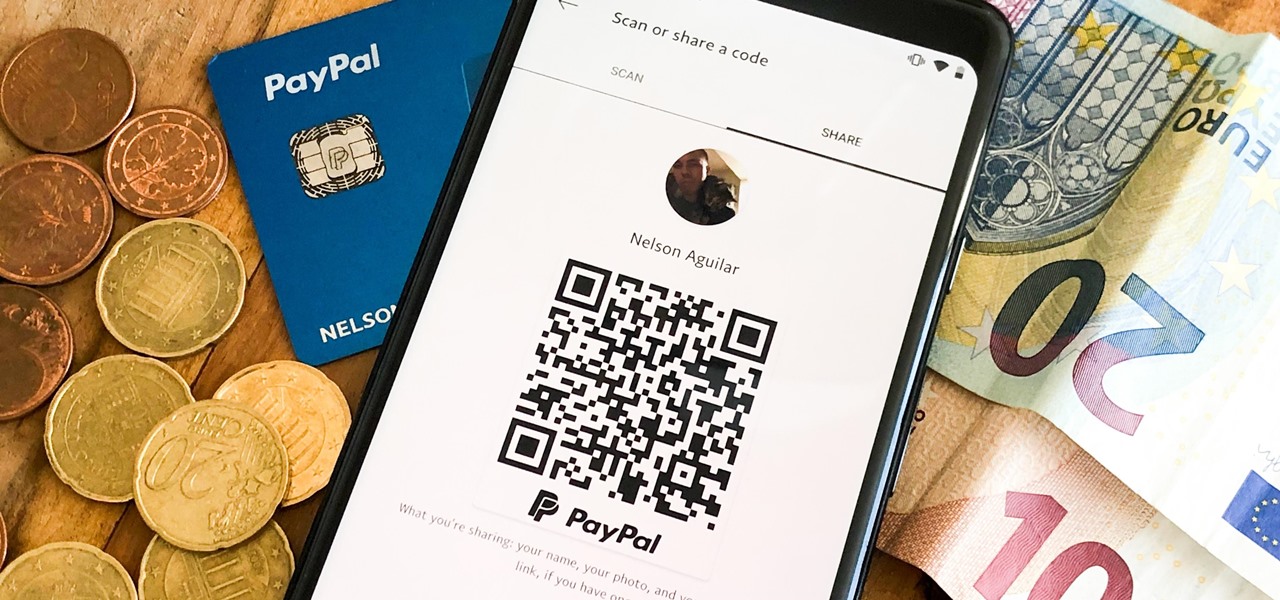
There are many ways to send and receive money on PayPal. You can use an email address, a phone number, or a PayPal.Me link, but if you're standing right next to the person you're trying to pay or get digital cash from, the easiest way, by far, is to use QR codes.

MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line. We'll use aliasing to set some simple commands for easy native packet capture on a macOS system.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

Whether it's for your company, your professional image, or just your personal account, making a poll on Instagram is a great way to reach out to followers, friends, family, and other users to measure their thoughts and opinions about any given topic. Instagram for Android and iOS makes it fun and simple to do so, offering the same tools to professional and personal users alike.

Your email inbox is a treasure trove of personal data. The people you contact, your writing style, which messages you flag as spam — all of this information and more can be used to paint a clear picture of you. Google knows this as well as anybody, so they use this data to constantly improve your experience in Gmail.

The first question people ask me when they come to my apartment is usually "What's your Wi-Fi password?" While I'm happy to give my friends free access to the internet, it's hard to walk each person through my secure password. Luckily, there's a way to create a QR code that will let people easily connect to a Wi-Fi network.

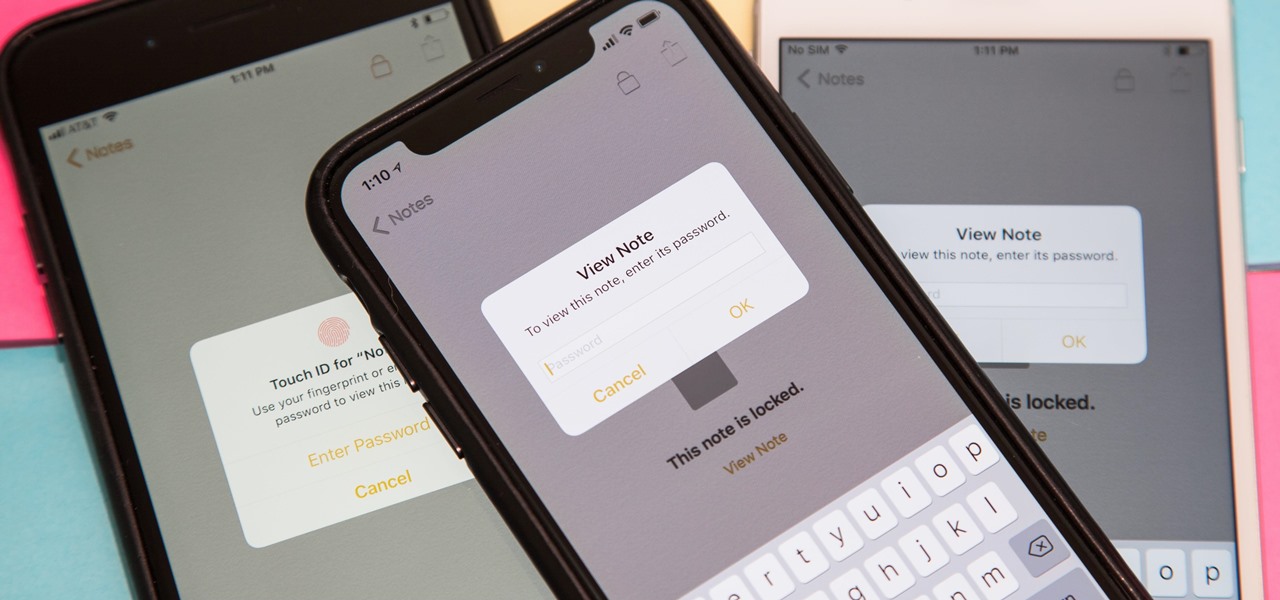
It's no secret that you can protect notes on your iPhone with a password, but one thing that most people don't know is that you can actually set unique passwords for each note instead of a blanket password for all of them. It's not obvious at all in the Notes app, but it's easy to do once you've got the hang of it.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

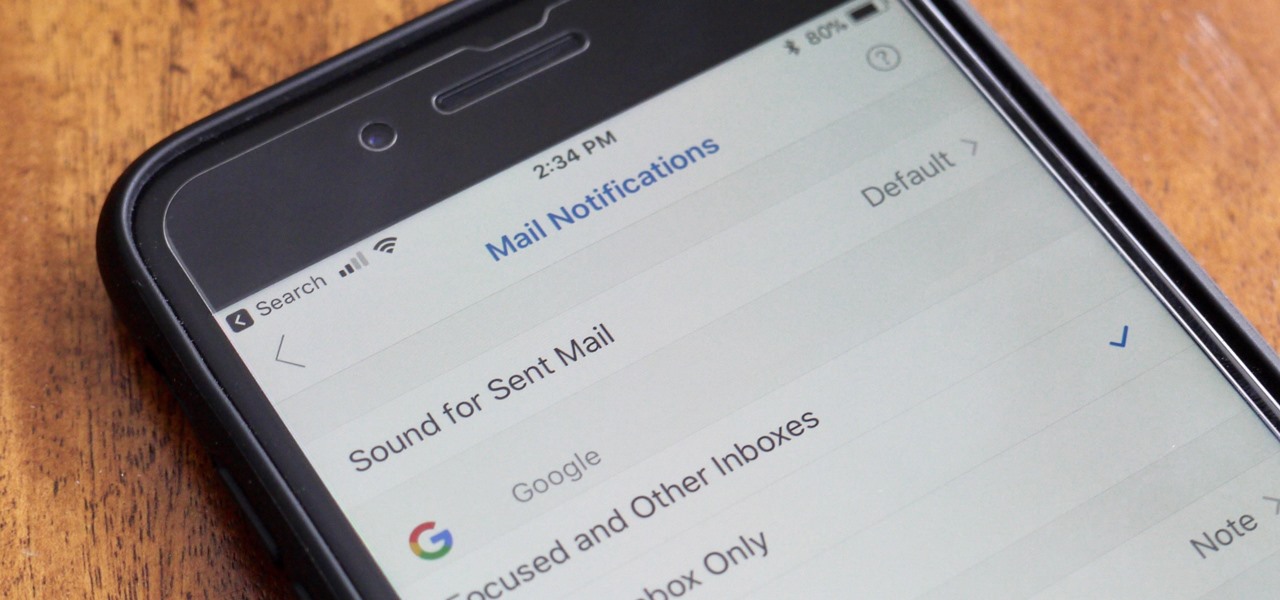
With email, one size does not typically fit all. You have multiple email accounts, each for different purposes and with varying levels of importance, so it only makes sense to customize the way your phone alerts you to each account's incoming emails. Luckily, Outlook allows you to do just that.

Whether you're new to Android or you just haven't kept up on the app scene lately, we hand-picked over one hundred essential apps that are all designed to improve your experience. From custom launchers and icon packs to weather apps and file explorers, there's something for everyone in this list.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

In its never-ending quest to innovate its flagships, Apple's newer iPhone models with Face ID do away with the iconic Home button present since the first iPhone back in 2007. That means screenshots, force-restarting, switching apps, Apple Pay, and the home screen all work differently on the iPhone X, XR, XS, XS Max, 11, 11 Pro, and 11 Pro Max. One of the more important aspects, Siri, is also slightly different.