The keyboard is one of the biggest weak points of iOS devices, in part due to the lack of an option to add a number row. Fortunately, there is a way to quickly switch between the numeric and alphabet layouts on your iPhone or iPad's keyboard.
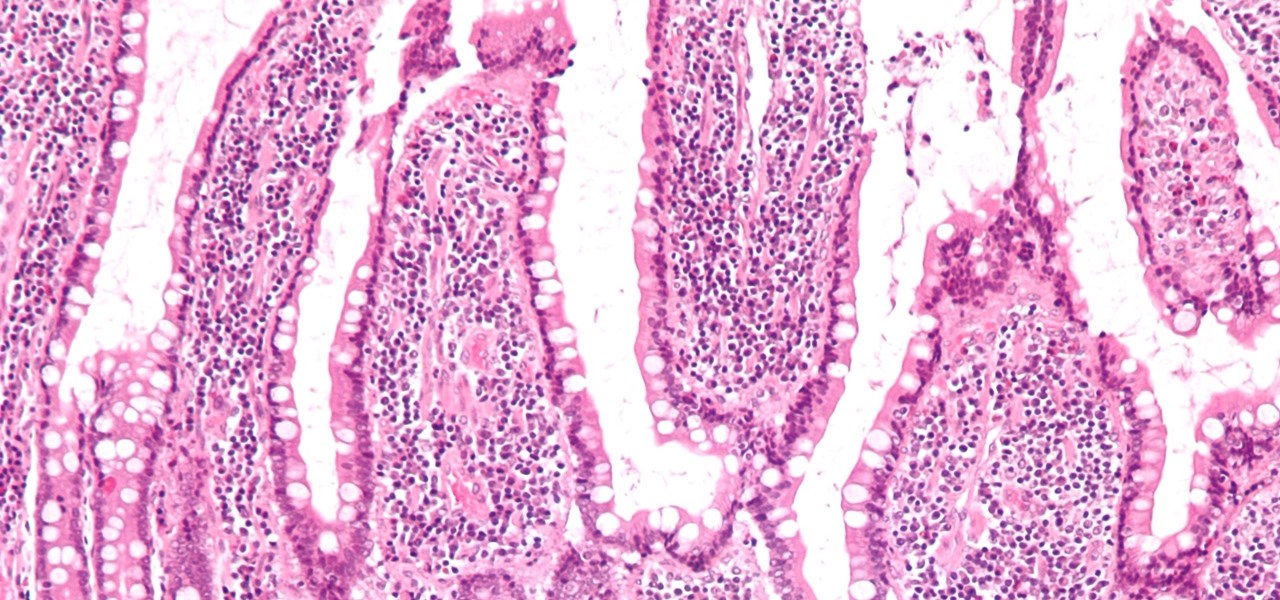
If the all the fingerlike projections in our gut were flattened out, its surface area would be 100 times bigger than our skin's. It's so large that the actions of just a small part of it can impact our health. A new research study has found that enterochromaffin cells in the intestinal lining alert the nervous system to signs of trouble in the gut — trouble that ranges from bacterial products to inflammatory food molecules.

A recently confirmed polio outbreak in Syria is connected to low levels of vaccination, worsened by conflict. It is the first confirmed incidence of polio in Syria since 2014. Before 2013, the last case of polio in Syria was in 1999.

Back in May 2017, Apple filed a patent application for a way to communicate with Siri by writing her questions and responses using iMessage. While that didn't make it into iOS, thankfully, something even better did — a way to ask Siri things with the keyboard directly in the Siri interface. This works in iOS 11 and later.

Could your fever, body aches, cough, and sore throat be the flu? Soon, finding out may not involve a trip to the doctor.

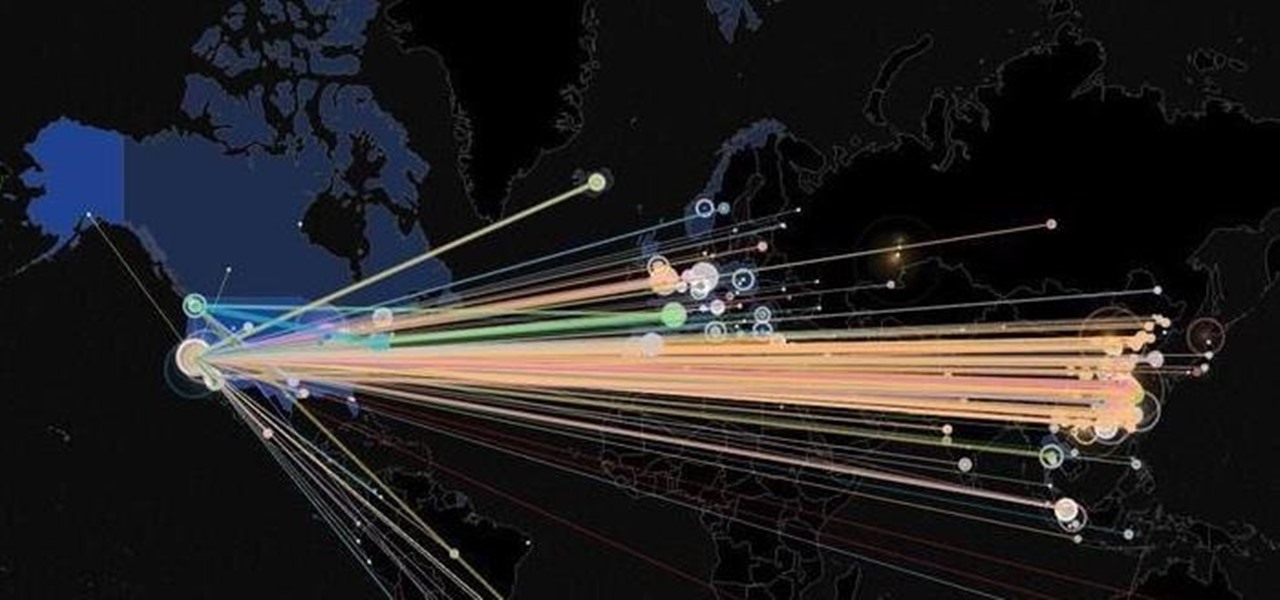
The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

The hatred is almost universal—by now, even late night TV hosts are bashing Apple's move to ditch the headphone jack in the iPhone 7. It's not like the disdain is baseless, either, because there are plenty of problems that come along with removing the iPhone's only analog sound output.

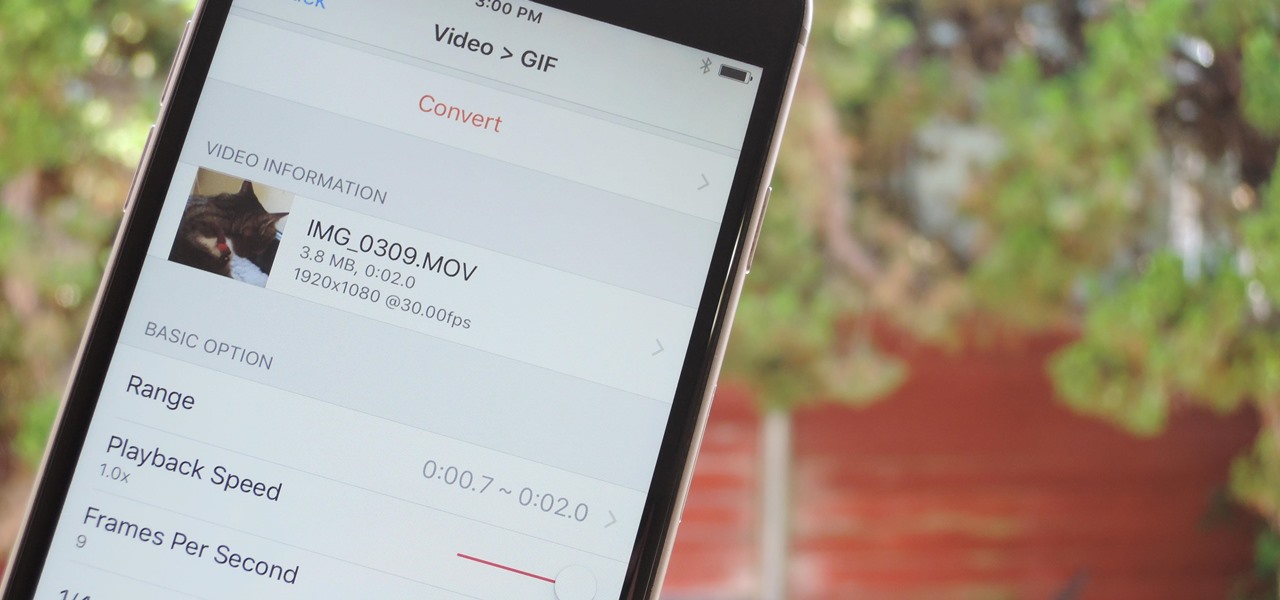
The internet has officially been taken over by GIFs—they're everybody's favorite method of communication these days, and nary a meme would exist without them. But even with the abundance of GIF-sharing websites, and even GIF keyboards, we're still a bit lacking in regard to creating GIFs on a mobile device.

These days, there are Android apps for every budget—forgive me if that sounds like a car commercial, but that's just the way things are in the age of the smartphone and tablet. You've got apps that require monthly subscriptions, paid apps that will run you a $30 one-time installation fee, and even games that start at 99 cents, but quickly skyrocket in price with in-app purchases.

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

Being able to customize the look and feel of your device is the main reason a lot of folks choose Android over iOS. And perhaps the single biggest way to visually overhaul your phone or tablet's UI is to apply an icon pack, which can liven up your home screen with bright colors or make things look a bit more classy with a sleek, minimalist style, for instance.

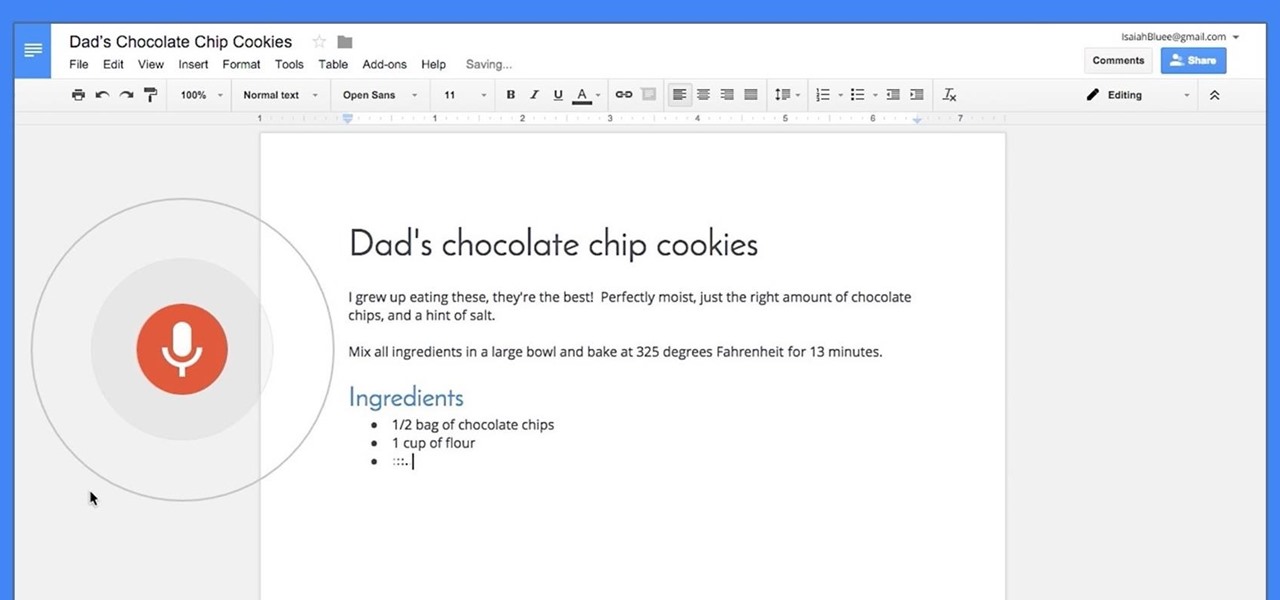
Google launched voice typing for Google Docs last Fall, and followed that up about six months later with voice commands that let you format and edit text as well. You can do things like select text, apply format settings like alignment and headings, and add and edit tables—all with your voice.

Google is rolling out an update for Google Drive that streamlines the online file storage/sharing app, and finally gives you access to the Trash folder that had only been available on the desktop version.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

Facebook just keeps coming up with more and more diversions to help you ignore your responsibilities. At least this diversion is a little more intellectual than most of the other things that can easily distract you on Facebook.

I mentioned in one of my earlier articles something about ghost hackers, and very shortly stated a thing or two of what they do.

Hello there Nullbytes, In my previous tutorial found here,

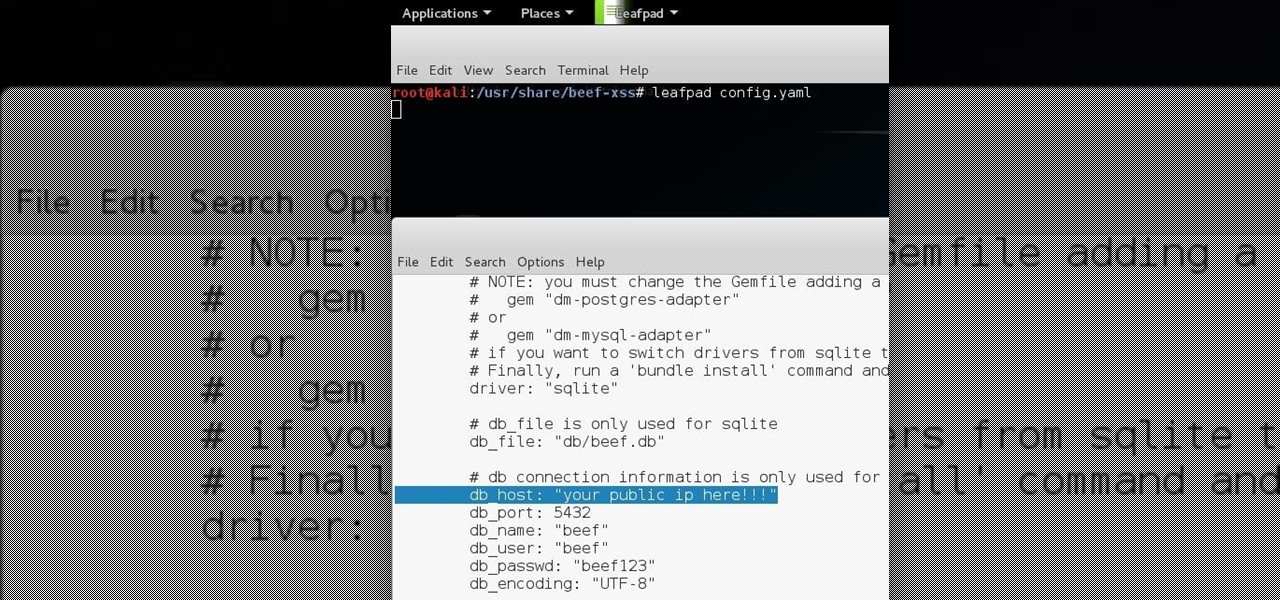
Hello all Just thought id share how ive managed to get beef working over the internet.

The notification light on phones and tablets is slowly disappearing. The once staple feature is now only found on a few devices, and a bevy of other notification systems have sought to fill the gap. The most popular of these systems is Ambient Display, which has grown in popularity with OEMs over the last couple of years; even Google's own Nexus line of phones have made the plunge.

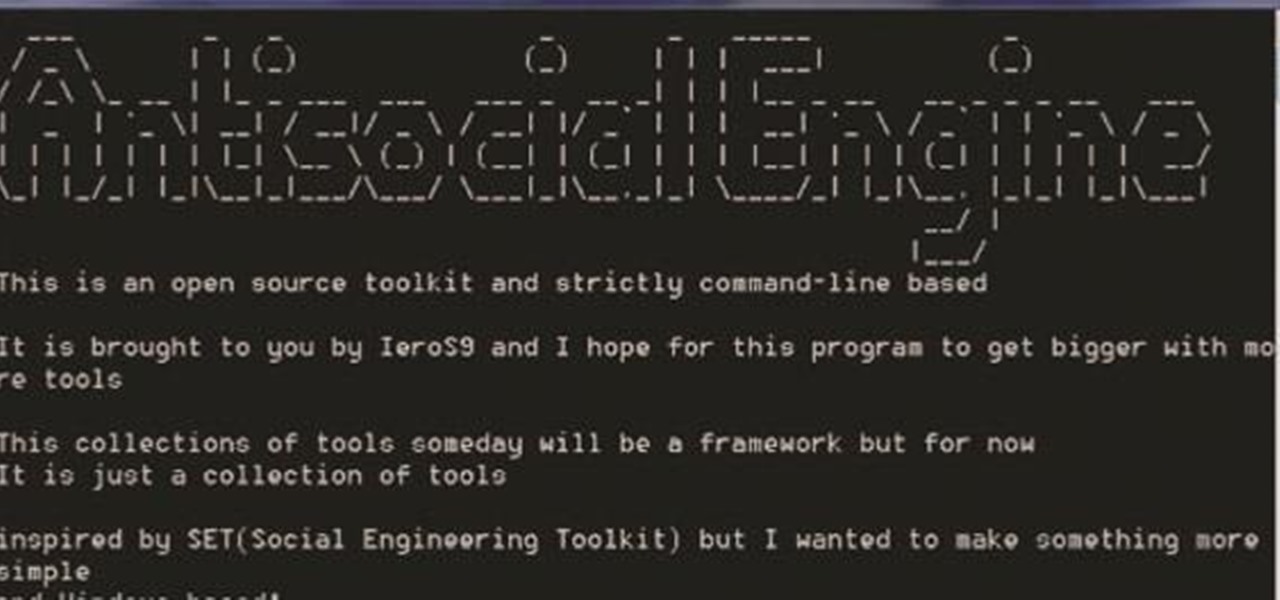
A.E Hi again this is my second post on nullbyte. The first one was on how to make a remote screenshot captor, now I will give you a presentation for a project of mine(I have named It Antisocial Engine) that It is not something extraordinary but will help many guys.

In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.

In python, or any scripting language for that matter, there are certain things that you will carry with you throughout your entire scripting career. Some of the most basic things that you will keep with you are output, variables, and their value types. We'll start by going over output, then cover variables and their types. So, let's get started!

You're at your friend's house. All you've heard about all day is his new laptop. He's got a brand new top-specced MacBook Pro, and he won't stop going on about it. It particularly annoys you as all you've got is a 4 year old cheap laptop, even if it is running Linux.

Since the release of Windows 8, Microsoft has been heavily encouraging users to use Windows with a Microsoft account. According to Microsoft, the main benefit of using a Microsoft account is the ability to sign in and sync your information across various Microsoft devices and services. Furthermore, you have access to a singular cloud storage solution which can contain documents, pictures, settings, and more on whatever system you're using with the Microsoft account.

One of Android's biggest strengths, when compared to other mobile operating systems is its open file structure. Google introduced a built-in file manager with Marshmallow that provides basic file management, but like with most apps on Android, there are alternatives. Third-party file managers are readily available, providing deeper access and control of all your files.

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

Hello, ladies and gents! Today I will be discussing the fun and excitement of backdoor on an OSX system.

In addition to sharing emojis and GIFs, most of us also probably share various types of links through email or text, whether it be for a Google Maps location, a bar or restaurant on Yelp, or an awesome song on Spotify.

Hi, my name is Alan, and I am not a script kiddy brat from Xbox Live asking you how to boot someone offline for being mean to me. I am an amateur white hat hacker hoping to learn and teach and this is my first tutorial.

Google I/O is like Christmas for Android enthusiasts. Every year, this conference showcases new and upcoming features for the world's leading mobile operating system, and this year's was no different. Shortly after announcing Android M, Google released a preview version of the upcoming firmware for Nexus devices.

On an Android device, you can download almost any file type into a neat and tidy "Downloads" folder, and those files can then be accessed with an appropriate app, shared via email, or transferred over to your computer. On an iPhone, there is no such folder, and saving files from Safari is almost impossible unless you're jailbroken.

Eating flowers is a time-honored culinary tradition, from nibbling on nasturtiums to grazing on candied violets. And why not? They look beautiful and lend a unique floral flavors to salads, desserts, and anything in between.

Now that we have our vulnerable server, it's time to start up BeEF. Getting Started

One of the many additions that appear on Android 5.0 Lollipop is a handy menu that lets users correct for or simulate different types of color blindness. While Google didn't flip the switch on this new feature until Lollipop was released, it turns out they had been working on it for quite some time.

OR rather How to make the Backdoor Persistent: Hello, my Cold and Merciless Hackers,

Welcome back, my novice hackers! In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn.

If I told you that people who use emojis in their conversations have more sex than plain-text users, would you believe me? According to a recent study launched by Match.com, men and women that use emojis have more sex than those who do not. If you were looking for an excuse to increase your emoji output, you may not find a better one than that. To make your emoji typing as smooth and seamless as possible, I'm going to show you how to create shortcuts in iOS 8 for all your favorite use cases. ...

Well Welcome Back My Fellow Hackers. What is Slowhttptest? You may be asking. Slowhttptest is a Application Layer Denial of Service attack aka an attack on HTTP. You can read more about it here and also download it if you don't have Kali Linux. slowhttptest - Application Layer DoS attack simulator - Google Project Hosting.

Video: . Marley Hair is Super Cute Curled so I decided to Curl it.

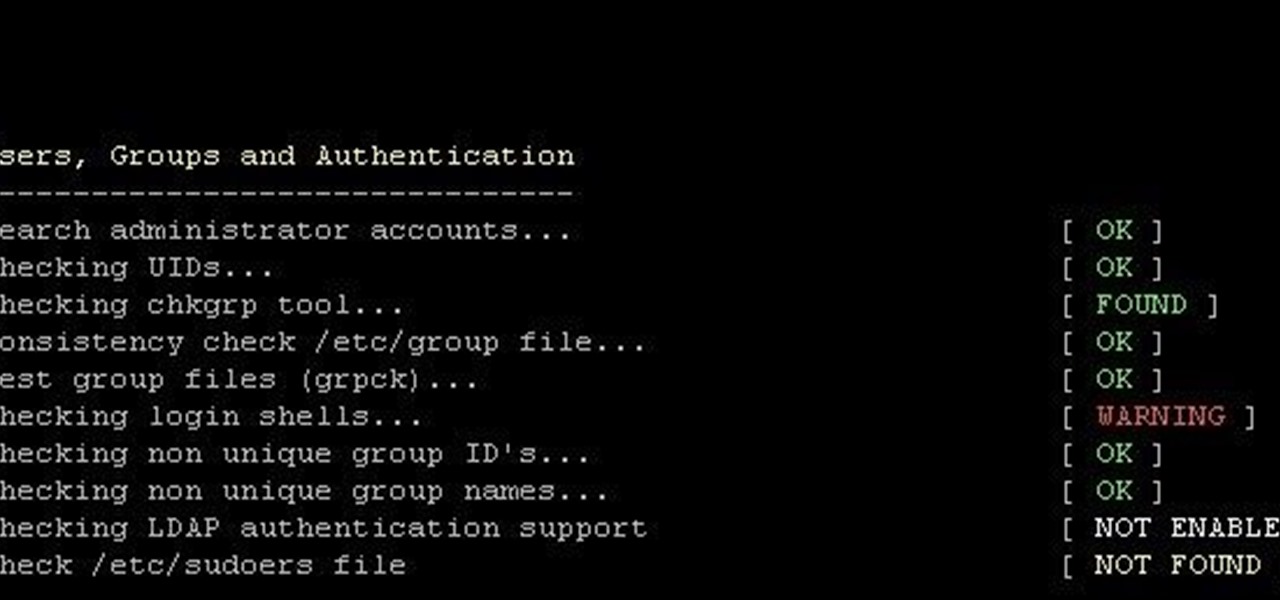
This is finding some of your vulnerability using Lynis. This tool Lynis is used on Unix and Linux type operating systems (sorry windows). So lets get started