Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

When you're actively using your phone, a certain amount of battery drain is to be expected. But, if your device is just sitting in your pocket draining its battery, that's when you need to take action.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.
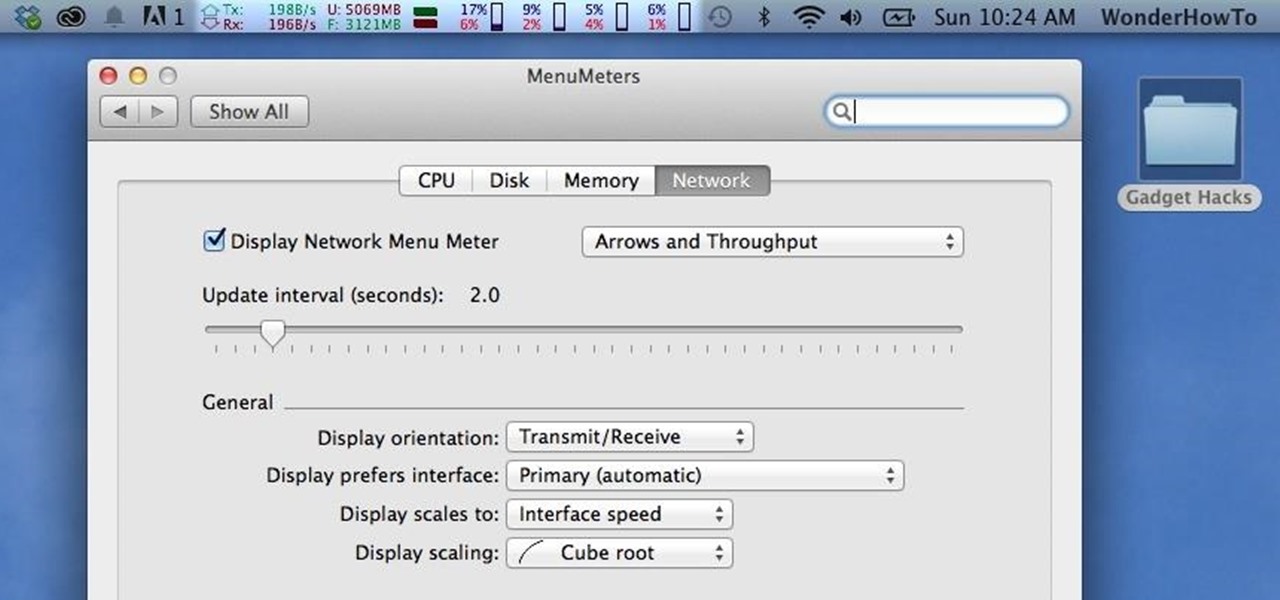
Like a car, your Mac needs to be monitored and cared for to keep it running as smoothly as possible. While your vehicle comes with a ton of gauges to keep track of your oil, temperature, and in some cases, even tire pressure, your Mac has no easy way to watch for low memory or high disk usage. Normally you would have to open up Activity Monitor to take a look at your usage stats, but now there is something better.

Voicemails are like chores for me. I have to listen to them, but never really feel like doing it. When I finally do, most of them get deleted right away, but every so often they'll be one I save and listen to over and over again, whether it's a cute birthday wish from grandma or a hilarious joke from my friend.

What if someone asks you to do a Nmap scan but you left your pc at home? What if a golden opportunity shows during a pentest but you were walking around the building, taking a break?

One of the best features of Android is the fact that it's open-source, giving developers the ability to use it on pretty much any device they can think of, like on a Windows PC using Andy. That's what drove the creators behind the Android-x86 project to port over the mobile OS to any computer running an Intel processor.

Go to a chain supermarket, and chances are you'll see one type of garlic—maybe two or three if you're lucky. However, there's a mouthwatering slew of Allium sativum out there, far beyond those papery white bulbs most of us encounter at the nearest Stop 'n' Shop.

Google Now is a quick and intuitive way to tailor your device to work for you and, unlike other personal assistants, provide you with up-to-date information based on search habits, emails, and the general all-knowingness of Google.

On a recent trip to Palm Springs, I found myself navigating with Google Maps and virtually exploring my destiniation using its built-in Street View feature. The thing is, using Street View can make keeping track of your exact location difficult as you zoom in, out, and about. It's a little discombobulating.

Twitter found a sweet spot with its 160-character limit, but Snapchat sports a social media low of 31 characters, forcing us to condense our ideas into a few short words when typing in picture captions because of their ephemeral nature. While this severely limited amount of words is Snapchat etiquette, I've got so much more to say than 31 characters!

In an attempt to keep things simple, Snapchat has a limited amount of editing features, made up of "smart" photo filters, drawing pens, and special text captions. If you want more editing capabilities, you'll be pleased to know there's a way, no thanks to Snapchat, but you will need to be rooted.

Puff and Po and the Empress's Treasures, is an inspiring indie game that stays fateful to the arcade single screen plat-former style and game-play.

A banner alert for notifications is like the Robin to our iPhone's Batman—they're taken for granted and don't really get the recognition they deserve. Yes, they can be disruptive at times, but just like Robin, they can be necessary for getting things done.

There are already a ton of glitches on Grand Theft Auto Online, and one of the newest ones to be uncovered lets you make millions in less than an hour, but you will need a million to get the job done. This glitch, revealed by YouTube user Caspahz below, lets you duplicate exotic cars that you already own so you can sell them for quick cash.

Mac laptops, especially the older PowerBooks, often can become very hot when doing processor intensive tasks like movie rendering, YouTube videos streaming, database lookups, or just gaming. Often just lifting the machine from the surface is enough to cool it down without the need of expensive hardware or software tuning.

Headphone cords are one of those things we all deal with because it beats the alternative (no music). But they can be so obnoxious—they're always getting caught on things, and they seem to be perpetually tangled. If you have ear buds, you can make a simple a cord container to keep them organized, but over-ear headphones are a little more tricky.

Welcome back, my budding hackers! I began this series on Linux basics because several of you have expressed befuddlement at working with BackTrack on Linux. As a hacker, there is no substitute for Linux skills.

Lots of us have already tried leopard nails and in this one I have added a new twist to the design to make it slightly more exciting for all of us who love this design pattern!

When we think of search it's usually in regards to the internet. But when you are using a smartphone, searching your device itself can be just as important and useful.

If you have a Mac running Mountain Lion, I'm sorry to tell you that all it takes to crash almost any app on it is eight little characters. This strange bug seems to only affect Mountain Lion and doesn't cause your computer any harm. Apparently, it even crashes the error reporter. On its own, the bug doesn't really pose a threat—just don't type it.

MAC addresses (not to be confused with Macs) are unique identifiers assigned to network devices in order to access the internet. Hotels use these Mac addresses in order to check if a registered patron has agreed to their terms and conditions, how much bandwidth is being consumed, and of course, whether they've paid or not.

As enjoyable as Facebook can be at times, it can also be a great distraction and even better deterrent of getting work done. A quick "Oh, let me check my notifications" can turn into hours and hours of Facebooking, and before you know it, you're already on your 7th Wikipedia page, all thanks to that status your friend posted. The reason I mention this is because Firefox's new 17.0 update includes many features, but the one that's been making the rounds online is the integration of Facebook Me...

As a technology writer, phone screenshots can pile up on your computer in no time. Testing out different apps, showing buggy software, and doing step-by-steps can lead to a plethora of mobile screenshots piling up on your computer's desktop. The problem with my screenshots is that they save as photo.png or photo.jpeg, as do many of my other photos. If I haven't finished a project or article, I tend to move them to different folders to save them for later. After a while, the screenshots begin ...

With the Samsung Galaxy S III being a hot commodity, it's no surprise that your friends might try unlocking your fancy password-protected phone. While some friends have good intentions when using your phone, there are those certain friends who get into the phone to do this... The worst scenario might be that you leave the phone around a group of friends, come back and find that all of your social media accounts have been hacked. When you yell out to your friends asking who did it, no one make...

Playing advanced games on your phone can be pretty frustrating sometimes. Touchscreen devices are great for everyday apps and games designed solely for them, but when it comes to games that require multiple actions in conjunction with directional movement, it gets ugly.

Hi, gang! Time for another hack using Metasploit. We have exploited Windows XP (a very insecure operating system) and we have exploited Ubuntu and installed Meterpreter on a Linux system exploiting the Samba service. Several of you have asked for a hack on more modern Windows systems, so here goes.

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:
(Series designed to help explore whether your ideal employment ideas should be formalized into a business venture or as an employee or volunteer value added problem solver).

In this video, we learn how to stretch your ears by taping. When you get to a certain size, taping is the only thing you can do, which is also very easy. To do this, you will need to have Teflon tape, which is a light and flimsy type of material that isn't sticky. You will need to wrap the tape around your plug until it's all the way around, not pulling it too tight so there isn't too much pressure. Do this several times, depending on how much you want to stretch it, then you will be done and...

In this video, we learn how to make silly putty from scratch. You will first need to take some flour and mix it with warm water in a small plastic container. After you mix this together and it turns into a putty type of shape, you will then add in some food coloring to the container as well. Add in some borax to this and continue to mix until it's completely finished mixing together. When done, you will be able to play with this and make other colors to mix together. This is a great project f...

this video first shows a type of modem that can be used to connect Xbox Live along with a router. It is shown that you must already have an internet provider and router for connecting more then one device into your modem. An Xbox live account is also required to gain access to Xbox Live. A DSL cable is then connect from the Xbox into the router which is then connect to your internet providers modem. You must then select connect in the Xbox Live access menu. After the Xbox has been connected y...

Call of Duty: Black Ops has a great Easter egg on the main menu which allows you shoot and kill tons of Nazi zombies! And it's really easy to find. Basically, from the main menu, look down at your restraints and start tapping LT and RT to break free. This will give you the "Just Ask Me Nicely" achievement. Next, go to the computer and type in DOA, which will unlock Dead Ops Arcade. When you start playing the game, you'll earn the "Insert Coin" achievement. That's it!

In this video, we learn how to understand music notation when reading sheet music. To help you read sheet music wherever you are, it's an easy process. You can learn how to read sheet music within just a few minutes and practice. You can be great at reading any type of sheet music so you can play with a band or just by yourself. Music notation is a big part of sheet music, so you must understand this before you can read sheet music by yourself. Once you get this, you will be able to play musi...

In this tutorial, we learn how to complement your skinny jeans outfit. The skinny jeans are a hot look right now in fashion and in the stores. With the skinny jeans, you can wear a top that is bigger or loose on you. Since the jeans are so tight, this will transition nicely with the different looks. Get a longer top as well, that at least hits your hips. A loose fit will work with this, especially if you have a larger body type. For the shoes, you can wear a slouch boot, because this will com...

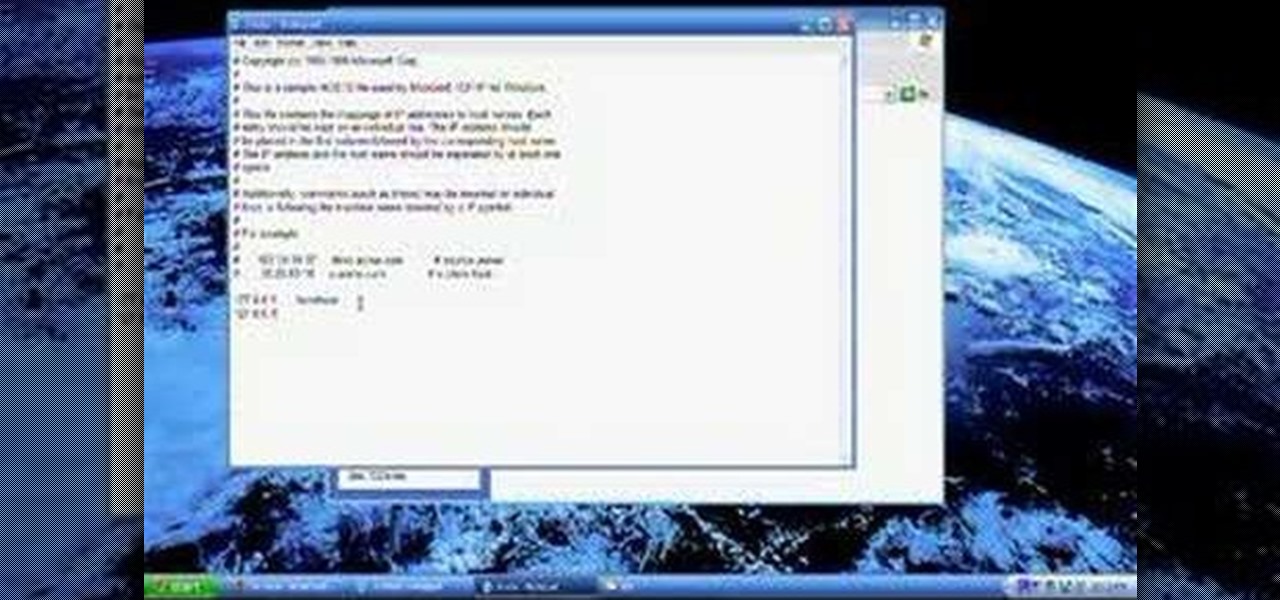
In this video, we learn how to block a website without software. First, open up 'my computer' and then double click on the local disk. After this, open up the 'windows' folder and then locate the 'system 32' folder, open this. Next, open the 'drivers' folder and then open the 'etc' folder. From here, double click 'host' file and then open it with a notepad. Now, after the last text type in "127.0.0.1 (website to block)". After this, save the file and then clean all the temporary internet file...

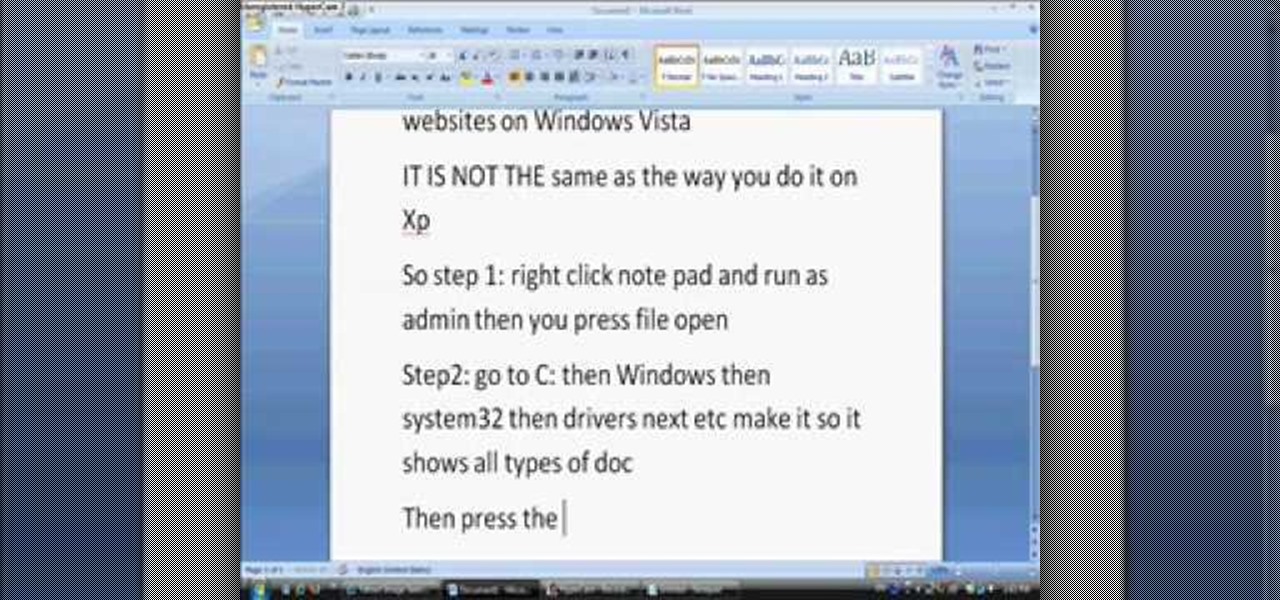
In this tutorial, we learn how to block websites on Windows Vista. First, you will right click on the notepad and then run as admin. From here, you will click "file open". Then, go to the C drive and open up windows. Then, you will go to the system and find the drivers, then click on the host file. From here, go to the second local host and press enter twice. Then, type in "127.0.0.1" and press tab. Then insert all the directories that you want to block. From here, you will be finished blocki...

In this video we learn how to make court-bouillon poached prawns and king crab legs. First, boil some pickling spice, wine, celery, and onions then let this simmer for an hour. After this simmers, you will grab your prawns and dump them inside of the pot. Let these boil until they have cooked, then take them out. After this, grab your crab legs and cook them with melted butter that has been seasoned with your favorite types of seasonings. Score the sides of the legs so the flavor can get thro...

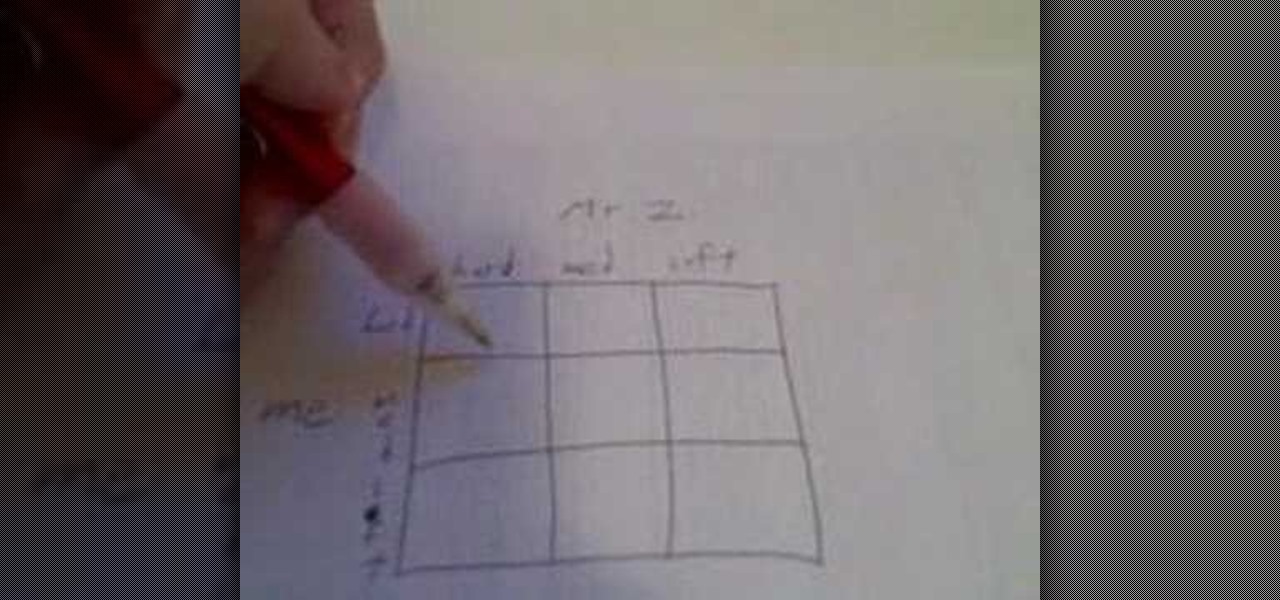
In this video, we learn how to negotiate a pay raise with game theory. You first need to take into account how much money you are getting an hour with how much you are worth. Make a chart with your boss on there and the other player is you. You will then see if you want to play soft, medium, or hardball with them to negotiate. Think about how your boss will respond to different types of negotiations. When you are finally confident in approaching your boss, you will get respect and get the pay...